log vALIDATION
WITH ATTACK SIMULATION
Picus Security Control Validation Platform, built on Picus BAS technology with an extensive library of threats, can easily integrate into your infrastructure and help you automatically identify logging gaps and areas of improvement.
Threat-Centric Validation
Given the complexity of the log management function, SOC practitioners have to deal with all combinations of failure involving malfunctioning log sources, invalid log format or temporary service disruption, while adapting the scope of log collection to the changing adversarial landscape. A threat-centric validation process allows SOC teams to proactively and consciously address these challenges by identifying:
-
Links between logging gaps and attack techniques
-
Problems with originating or shipping logs
-
Challenges in identifying log sources and level of verbose
Enhanced Logging for Better Visibility
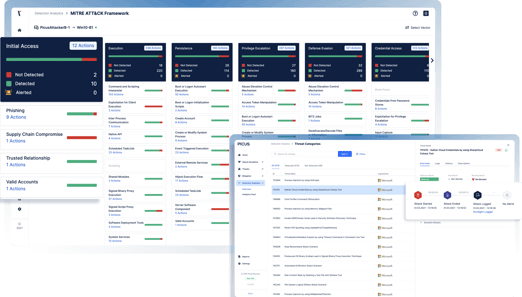
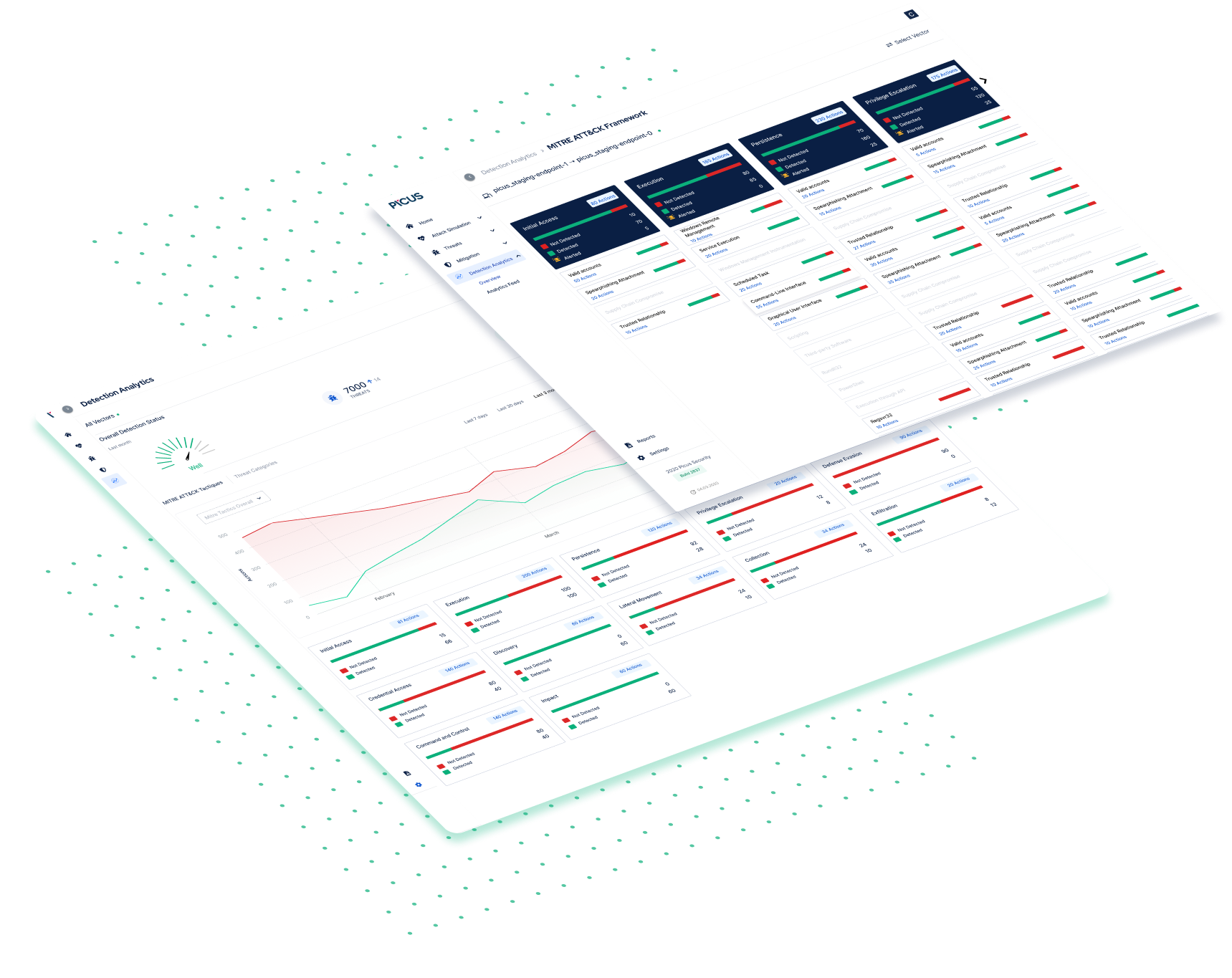
Starting from scoring attack vectors and revealing critical weak links, Picus is able to break down vector scores into individual contributions from each security control. The Detection Analytics module shows:
-
Which security controls detected the attack
-
Whether the attack is blocked
-
Start and end time of each single attack scenario
-
Log delivery status and time
-
If the attack has been alerted.
Security scores of each solution will be calculated as a percentage of the full mitigation potential, given by the available policy set provided by its vendor on the date of operation. Scores on each attack vector will be shown per attack category (i.e. web application) , sub category (i.e. cross scripting), kill chain stage and MITRE ATT&CK mapping for endpoint scenarios.
It is highly recommended to carefully design attack vectors and perform an initial validation of the prevention layer to identify weak links in the first stages of the Picus deployment. Then, mobilize your security operation teams for root cause analysis, run an assessment with Picus Detection Analytics and identify not blocked and not logged attacks.
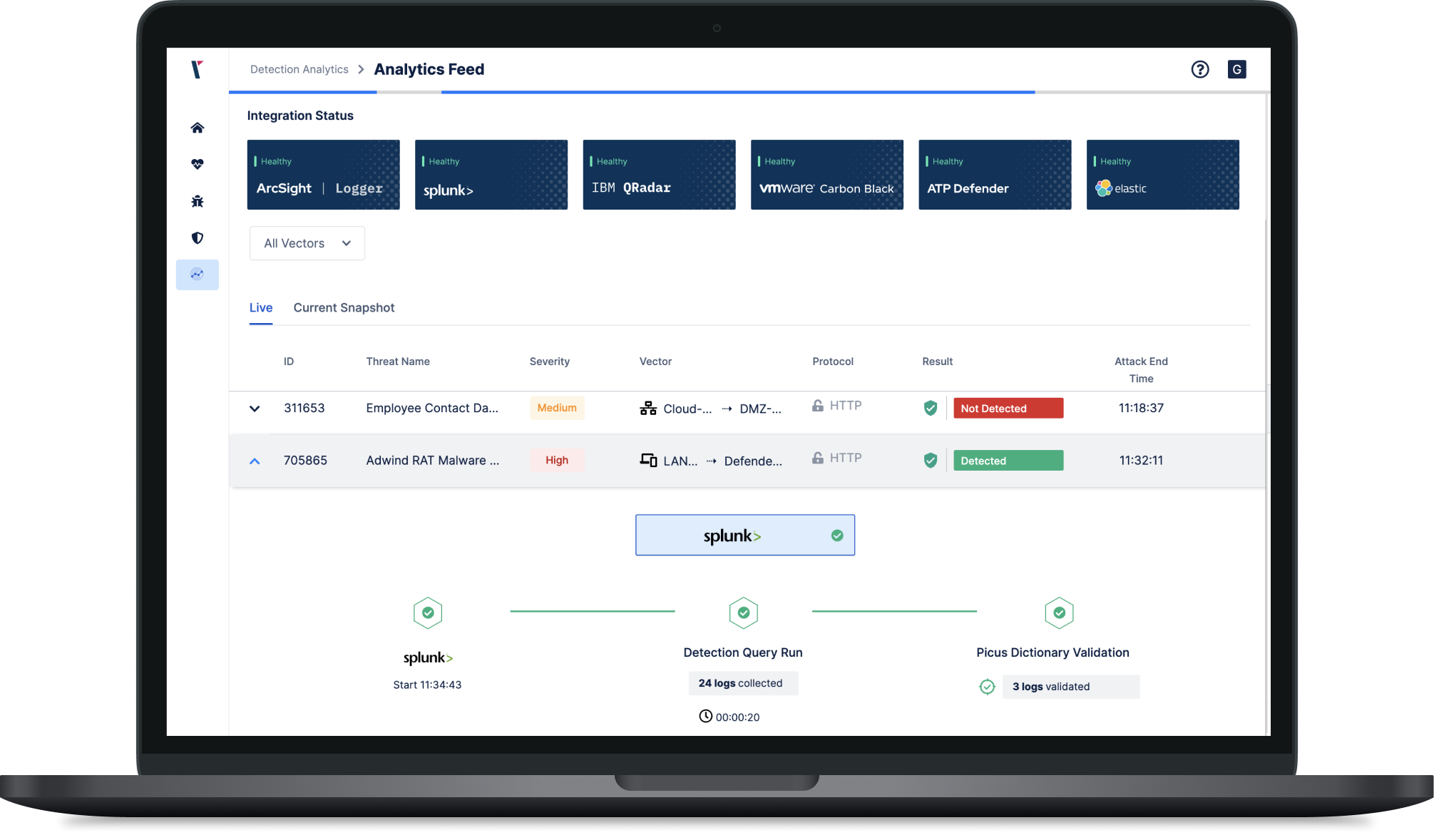
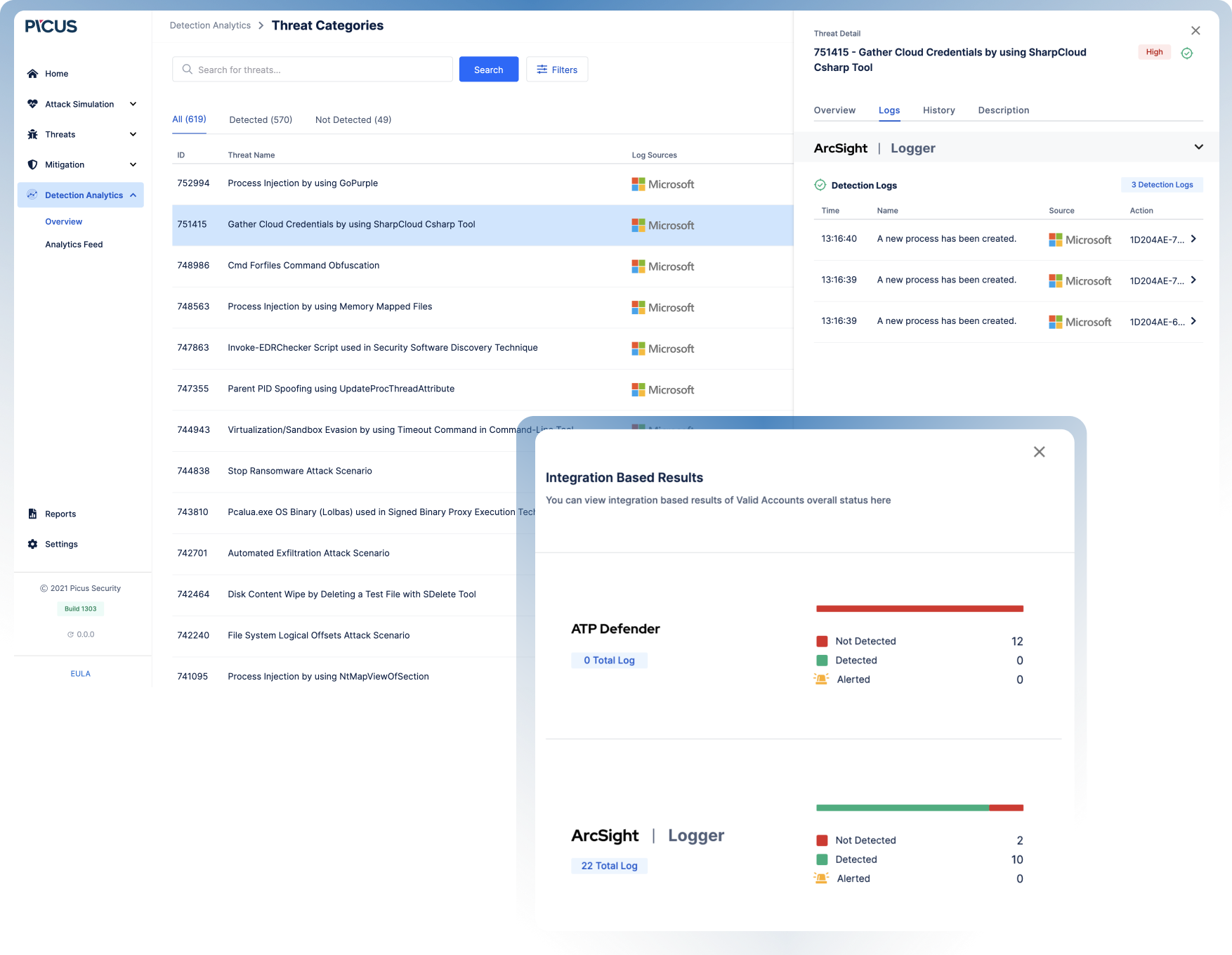
Identify the Missing Logs
Starting from threat emulation outcomes, Picus Detection Analytics drives log validation with actionable data. Picus reveals the journey of a threat with an end to end view of attack status (including start, end time), log status and delivery timeline, and alert and prevention status. Threats can be searched using advanced filtering criteria (severity, log source, alert status etc.). Picus will be effective in highlighting several problem scenarios including;
-
Attacks missed by the existing preventative controls
-
Attacks detected by the preventative infrastructure but missed by the SIEM
-
Log delivery issues
-
Incomplete or malformed logs.
Utilising the Picus Security Validation Platform, SOC teams may run a broad and fast root cause analysis identifying blocked but not logged threats, detected but not logged threats and significant time delays in the first phase after deploying Picus.
Log Validation with
Attack Simulation
Picus Security Control Validation Platform with the extensive library of threats, can easily integrate to your infrastructure and help you automatically identify logging gaps and areas of improvement.
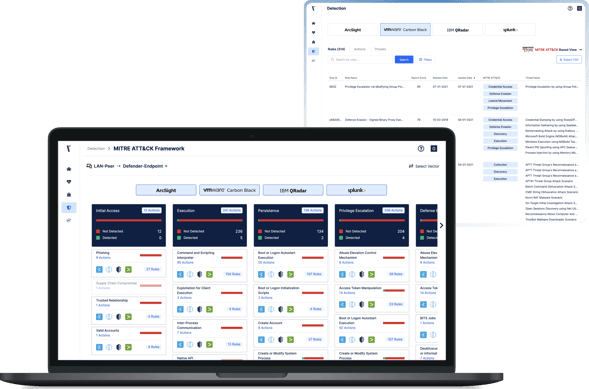
Optimize Endpoint Logging by Leveraging Threats
Picus Detection Analytics shows vendor-specific detection rules for SIEM and EDR platforms by TTPs. Filtering options allow users to narrow down the content based on severity, log source, MITRE ATT&CK tactic or technique release date.
Each detection rule is presented alongside log sources and policy requirements that need to be enabled on endpoints.
While testing for a sizable sample of tactics and techniques as displayed in the MITRE ATT&CK view, users should prioritize and address “not logged” (not detected) threats and attack actions in order to improve coverage quickly. In the long run, by developing a process around attack simulations that endpoints detected or missed, SOC engineers can establish a log baseline for endpoint segments and make decisions on which logs can be turned off to avoid overloading the SIEM infrastructure.