What Is MITRE ATT&CK?
As cybersecurity professionals face an ever-growing range of sophisticated cyber threats, staying ahead of attackers has become increasingly challenging. The MITRE ATT&CK Framework has emerged as a vital resource for security experts to stay up-to-date with the latest tactics and techniques used by adversaries.
In this blog, we'll delve into the MITRE ATT&CK framework's various components, providing valuable insights for cybersecurity professionals seeking to fortify their organizations' defenses and stay one step ahead of the attackers.
What Does MITRE ATT&CK Stand for?
MITRE ATT&CK stands for MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK).
MITRE ATT&CK is a knowledge base that tracks cyber adversary tactics and techniques based on real-world observations. It helps organizations understand attacker behavior, improve detection strategies, and strengthen their cybersecurity defenses.
Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) is a component of the MITRE ATT&CK framework, which provides a structured approach to classifying and understanding cyber threats.
-
"Tactics" represent the objectives or goals of an attacker.
-
"Techniques" are the methods used to achieve those objectives.
-
"Common Knowledge" refers to the shared understanding and accumulated expertise within the cybersecurity community regarding adversary behavior, which forms the basis of the framework's knowledge base.
What Is MITRE ATT&CK?
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a comprehensive, globally accessible knowledge base and framework that systematically categorizes cyber adversary tactics, techniques, and procedures (TTPs) [1]. It enables organizations to better understand, assess, and defend against cyber threats across the entire attack lifecycle. The framework provides a common taxonomy and language for cybersecurity professionals, fostering improved communication and collaboration among defenders, threat hunters, and red teams.
Who Is MITRE?
Established in 1958, MITRE is a non-profit organization that operates Federally Funded Research and Development Centers (FFRDCs) [2] to support the U.S. government in various domains, including scientific research, development, and systems engineering [3]. In the realm of cybersecurity, MITRE is renowned for its efforts in identifying, comprehending, and mitigating software and hardware vulnerabilities.
In 1999, MITRE initiated its work on classifying software vulnerabilities by launching the Common Vulnerabilities and Exposures (CVE) List [4]. This list facilitated tracking of known vulnerabilities and exposures in software and hardware systems. Building upon these efforts, MITRE introduced the Common Weakness Enumeration (CWE) List in 2006 [5], which aimed to provide an exhaustive classification of software and hardware vulnerabilities. To this day, MITRE collaborates with the security community to maintain and enhance the CWE List.
In addition to the CVE and CWE Lists [6], MITRE is also recognized for initiatives like the MITRE ATT&CK framework. This globally-accessible, continuously updated knowledge base comprises adversarial tactics, techniques, and procedures employed by advanced persistent threats and other cyber threat actors. By offering a comprehensive understanding of cyber threats, the framework empowers organizations to respond to them more effectively and efficiently.
What Is the Purpose of the MITRE ATT&CK Framework?
The primary goal of MITRE ATT&CK Framework is to help organizations improve their cybersecurity posture by providing them with a comprehensive view of potential adversary tactics, techniques, and procedures (TTPs). ATT&CK also helps organizations to identify gaps in their security posture and prioritize their defenses against the most significant threats.
What Are the Main Components of ATT&CK as an Attack Framework?
The ATT&CK framework is a comprehensive knowledge base of tactics, techniques, and procedures (TTPs) used by attackers to carry out cyberattacks. It covers a wide range of cyber threats and is designed to help organizations improve their defenses by identifying and understanding the various techniques that attackers use.
There are seven main components of ATT&CK as an attack framework.
-
Tactics
-
Techniques
-
Data Sources
-
Mitigations
-
Groups
-
Software
-
Campaigns
How Many Tactics in MITRE ATT&CK?
MITRE ATT&CK Tactics are a set of high-level objectives that cyber attackers aim to achieve in their operations, such as gaining access, executing malicious code, or exfiltrating sensitive data.
The MITRE ATT&CK framework (currently v13 [7]) identifies a total of 14 tactics that encompass the various stages of a cyber attack. The following is an improved list of these tactics along with the attackers' objectives.
|
MITRE ATT&CK Tactics |
Attacker Objective |
|
1. Reconnaissance |
Gathering information to plan and strategize future operations |
|
2. Resource Development |
Establishing resources required to support and execute operations |
|
3. Initial Access |
Getting the initial access to a target network |
|
4. Execution |
Executing malicious code to compromise the target or achieve specific objectives |
|
5. Persistence |
Ensuring continued access to the compromised system, maintaining a foothold |
|
6. Privilege Escalation |
Obtaining higher-level permissions to access sensitive resources and systems |
|
7. Defense Evasion |
Employing tactics to avoid detection by security controls |
|
8. Credential Access |
Acquiring account names, passwords, and alternative authentication information |
|
9. Discovery |
Identifying and understanding the target environment to facilitate further exploitation |
|
10. Lateral Movement |
Navigating within the target environment to access additional resources or systems |
|
11. Collection |
Gathering data relevant to the attacker's objectives and goals |
|
12. Command and Control |
Establishing communication with compromised systems to remotely control them |
|
13. Exfiltration |
Extracting sensitive data from the target environment for unauthorized use |
|
14. Impact |
Manipulating, disrupting, or destroying target systems and data to cause harm or achieve specific objectives |
How Many MITRE ATT&CK Techniques Are There?
These are the specific methods that attackers use to achieve their objectives. The framework currently (v13) includes 227 techniques across the 14 tactics [8].
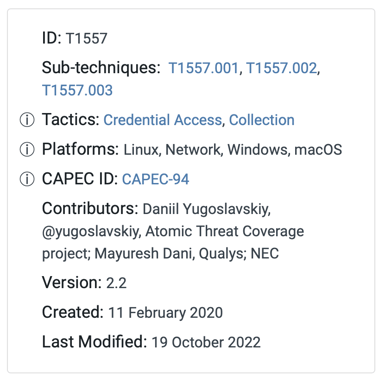
Figure 1. ID Metacard for the Adversary-in-the-Middle Technique From the MITRE ATT&CK Framework.
For example, in Figure 1 provided above, the Adversary-in-the-Middle technique is illustrated, assigned the ID number T1557. This specific technique encompasses three sub-techniques: T1557.001, T1557.002, and T1557.003. The Adversary-in-the-Middle technique falls under two distinct tactics – Credential Access and Collection.
From the information card, it is possible to identify the contributors, version number, creation date, and most recent modification date.
Other Main Components of MITRE ATT&CK
The six other components of MITRE ATT&CK are given below.
MITRE ATT&CK Data Sources
These are the data sources that can be utilized for detecting or investigating the specific implementation of attack techniques. The framework recognizes various data sources, including network logs, endpoint logs, and process monitoring.
In ATT&CK v13, 41 data sources are available.
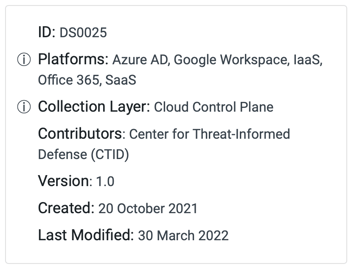
Figure 2. ID Metacard for the Cloud Service (DS0025) Data Source MITRE ATT&CK Framework.
The provided ID card in Figure 2 is a metadata card for a cloud services dataset, offering an overview of its details, platforms, data collection layer, contributors, and version history.
MITRE ATT&CK Mitigations
These are the countermeasures that can be used to prevent or mitigate the impact of specific techniques. The framework identifies a variety of mitigations, such as software updates, access controls, and network segmentation.
MITRE ATT&CK Groups
These are the threat actors or groups that are known to use specific techniques. The framework includes information on a number of groups, including nation-state actors and cybercriminal organizations.
MITRE ATT&CK Software
These are the specific tools and malware that are associated with specific techniques. The framework includes information on a variety of software, such as remote access trojans (RATs) and command-and-control (C2) servers.
MITRE ATT&CK Campaigns
In ATT&CK, a campaign refers to an organized and sustained series of cyber attack or intrusion activity by a specific threat actor or group, characterized by a common objective or set of objectives. These campaigns are often named and tracked, and are grouped together based on their associated tactics, techniques, and procedures, as well as their attribution to a particular threat actor or group.
For instance, "C0010" is an example of a named campaign in the MITRE ATT&CK Framework. It is a cyber espionage campaign conducted by "UNC3890," a threat group believed to conduct operations in support of Iranian interests. The campaign targeted various sectors and organizations in Israel, including shipping, government, aviation, energy, and healthcare.
What Are the Different Types of Matrices Within the MITRE ATTACK Framework?
There are three main ATTACK matrices within the MITRE ATTACK framework:
-
Enterprise Matrix,
-
Mobile Matrix, and
-
ICS Matrix
Enterprise ATT&CK Matrix
The Enterprise ATT&CK Matrix is the most comprehensive and covers the tactics, techniques, and procedures (TTPs) for various platforms such as Windows, macOS, Linux, Azure AD, Office 365, Google Workspace, SaaS, IaaS, networks, and containers.

Figure 3. Four Tactics and their corresponding Techniques from Enterprise ATT&CK Matrix.
The MITRE ATT&CK Enterprise matrix consists of seven matrices.
-
PRE
-
Windows
-
macOS
-
Linux
-
Cloud
-
Network
-
Containers
PRE Matrix
"Pre-Attack" tactics and techniques that adversaries use to prepare for cyberattacks. It covers aspects such as reconnaissance and resource development, helping organizations better understand and defend against early-stage threat activities.
Each technique under the PRE Matrix given below with their corresponding techniques, Reconnaissance and Resource Development.
-
Reconnaissance
Adversaries engage in Reconnaissance to collect information on targets, aiding in planning and executing future operations and informing subsequent attack phases.
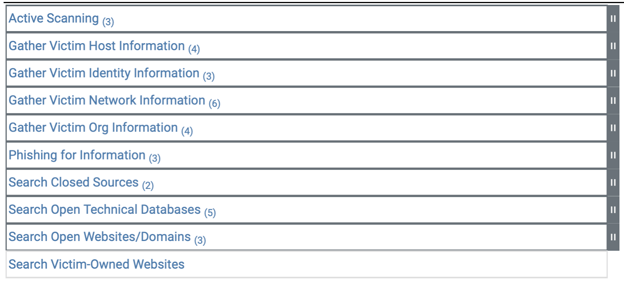
Figure 4. Reconnaissance Under the PRE Matrix.
-
Resource Development
Resource Development encompasses tactics where adversaries obtain or create resources, such as infrastructure, accounts, or capabilities, to support their targeting efforts and facilitate various stages of the cyber attack lifecycle.

Figure 5. Resource Development Under the PRE Matrix.
Windows, macOS and Linux Matrices
The Windows, macOS, and Linux Matrices are comprehensive cybersecurity frameworks focusing on identifying and categorizing tactics, techniques, and procedures (TTPs) specifically targeting each respective operating system. These matrices help security professionals better understand, detect, and defend against potential cyber threats in Windows, macOS, and Linux-based environments.
Cloud Matrix
The Cloud Matrix is a cybersecurity framework outlining tactics and techniques for cloud-based threats. It covers platforms like Azure AD, Office 365, Google Workspace, SaaS, and IaaS, helping security professionals protect cloud environments.
Network Matrix
The Network Matrix is a cybersecurity framework detailing tactics and techniques targeting network infrastructure devices. It assists security professionals in understanding and defending against threats to the Network platform.
Containers Matrix
The Containers Matrix is a specialized cybersecurity framework that addresses attacker tactics and techniques targeting container technologies, such as Docker and Kubernetes. It provides security professionals with insights and cybersecurity strategies to safeguard container-based environments from potential cyber threats and vulnerabilities.
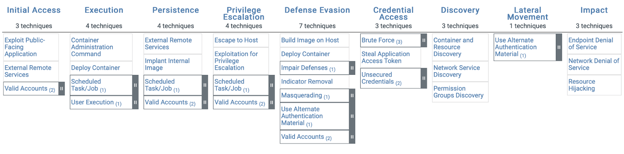
Figure 6. Containers Matrix from the MITRE ATT&CK Framework.
MITRE ATT&CK Mobile
The Mobile ATT&CK Matrix is a framework that outlines the various methods and techniques used by attackers to compromise mobile devices, such as smartphones and tablets, running on iOS and Android platforms.
Additionally, it covers the tactics and methods employed by attackers when they do not have direct access to the targeted mobile device.
The ICS ATT&CK Matrix is a framework that focuses on the techniques and tactics used by attackers to compromise industrial control systems, which are used to manage critical infrastructure such as power grids, factories, and mills.
It is similar to the Enterprise ATT&CK Matrix but tailored specifically for the unique security concerns of ICS environments.
How to Use MITRE ATT&CK to Improve an Organization’s Cybersecurity Posture?
The MITRE ATT&CK framework helps cybersecurity professionals to enhance an organization's security posture.
Structured Approach to Threats
The framework provides a structured way to understand and analyze the tactics, techniques, and procedures (TTPs) used by attackers, enabling organizations to better comprehend their potential adversaries.
Threat Intelligence
Mapping known TTPs to the framework helps organizations identify the types of attacks they are likely to face and develop targeted defenses against those threats.
Incident Response
During an incident, the framework helps identify the stage of the attack, the TTPs used, and the potential impact, enabling incident responders to make informed decisions about containment and remediation.
Breach and Attack Simulation
Organizations can leverage Breach and Attack Simulation (BAS) tools to simulate cyberattack campaigns and map their Tactics, Techniques, and Procedures (TTPs) to the framework. This allows them to identify gaps in their defenses, prioritize areas for improvement, and test the effectiveness of their security tools.
Improved SOC Effectiveness
The framework enhances the capabilities of a Security Operations Center (SOC) by allowing analysts to more easily identify and prioritize alerts, leading to faster and more efficient incident response.
How Does the MITRE ATT&CK Framework Differ From Other Cybersecurity Frameworks and Methodologies?
In this section, we will compare the MITRE ATT&CK Framework against the existing frameworks Cyber Kill Chain and NIST Cybersecurity Framework.
Cyber Kill Chain:
-
Provides a general overview of the attack process, which is valuable for grasping the basic concepts
-
Linear structure may not capture the complexity of modern cyberattacks, limiting the ability to address more sophisticated threats
-
Focuses primarily on perimeter security, potentially overlooking the importance of defense-in-depth strategies
-
Central axiom (breaking any phase of the kill chain stops the attack) may not be sufficient for comprehensive risk-driven cybersecurity approaches
NIST Cybersecurity Framework:
-
Establishes broad guidelines for managing cybersecurity risks, helping organizations build a solid foundation
-
Lacks the detailed focus on attacker TTPs found in MITRE ATT&CK, which can be essential for proactive defense and threat anticipation
-
Organized around five core functions, offering a high-level view of organizational cybersecurity needs
-
Often used to create or assess cybersecurity programs, but may not provide granular insights for specific defensive measures against complex threats
MITRE ATT&CK Framework:
-
Delivers in-depth understanding of real-world attacker behavior, allowing organizations to anticipate and adapt to evolving threats
-
Hierarchical structure enables easy navigation and identification of relationships between attacker methodologies
-
Offers actionable insights for threat hunting, red teaming, and cyber threat intelligence enrichment, fostering a proactive cybersecurity posture
-
Facilitates communication between stakeholders by providing a comprehensive set of terminology and definitions, enhancing collaboration and knowledge sharing
In conclusion, the MITRE ATT&CK framework offers a comprehensive, in-depth understanding of real-world attacker behavior, fostering a proactive cybersecurity posture. While the Cyber Kill Chain and NIST Cybersecurity Framework provide valuable insights, the ATT&CK framework's focus on TTPs and actionable intelligence makes it particularly suited for addressing sophisticated threats and enhancing threat anticipation.
How Do Organizations Use the MITRE ATT&CK Framework to Identify and Prioritize Threats and Vulnerabilities?
Organizations use the MITRE ATT&CK framework to identify and prioritize threats and vulnerabilities by mapping their existing security controls against the known adversary tactics and procedures. This mapping helps organizations to identify potential gaps in their defenses and allocate resources accordingly.
What Is MITRE ATT&CK Navigator?
MITRE ATT&CK Navigator is a web-based visualization tool designed to help users explore and annotate the MITRE ATT&CK matrices, which contain tactics, techniques, and procedures used by cyber adversaries. The Navigator provides a simple, generic interface for users to create custom layers or views of the ATT&CK knowledge base, highlighting specific platforms, adversary behaviors, or defensive coverage.

Figure 7. Creating a custom layer for APT39 [9].
These custom layers can be created interactively within the Navigator or generated programmatically and then visualized using the tool. The primary goal of the ATT&CK Navigator is to make it easy for cybersecurity professionals to understand and apply the ATT&CK framework by offering a visual representation of the matrix and facilitating the identification of attack patterns, mitigation strategies, and gaps in defenses.
How to Access ATT&CK Navigator
Users can access the MITRE ATT&CK Navigator through its GitHub repository here.
From there, they have the option to use a hosted version of the tool by visiting this website or download the source code to run it locally on their own machines.
By accessing the hosted version or running it locally, users can explore the ATT&CK matrix, create custom layers, and visualize their findings, helping them understand attack patterns and improve their cyber defense strategies. The open-source nature of the tool also allows for community-driven enhancements, ensuring the Navigator remains up-to-date and relevant for cybersecurity professionals.
How to Use ATT&CK Navigator?
To begin using the Navigator, access it either through the GitHub repository or the hosted version available online. Start by creating a new layer and selecting the appropriate domain (e.g., Enterprise) to focus on the relevant data.
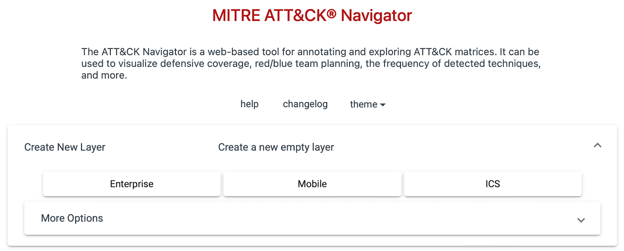
Figure 9. Creating a New Layer in MITRE ATT&CK Navigator
Upon clicking on the “Enterprise”, you will see the following layer.
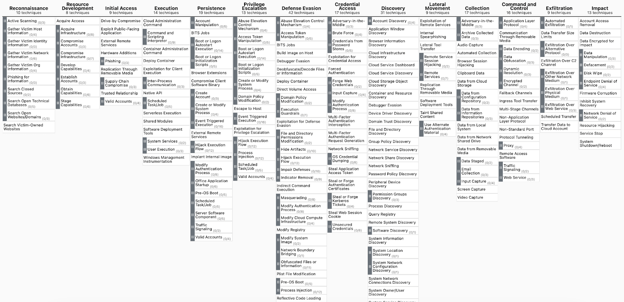
Figure 10. Creating a New Layer in MITRE ATT&CK Navigator
As there is too much information covered, you may need to narrow down your search. For instance, if you only want to see attack techniques related to credential dumping, you can narrow down your search like in Figure 11.
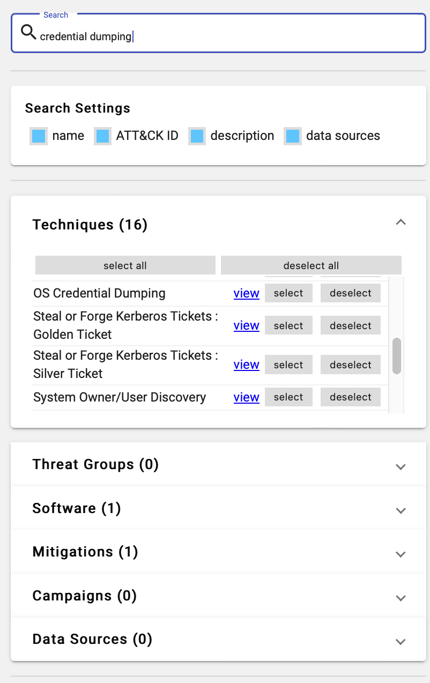
Figure 11. Searching for Particular Tactics and Techniques in
Once you find the relevant techniques, select them to add to your layer, which will then be displayed in the main window.
You can create multiple layers to compare and prioritize different threat actors or attack techniques. For better organization and readability, customize each layer by adding a name and description. Assign scores to each layer to help prioritize and differentiate between them. For example, you can assign a score of 1 to one threat actor and 2 to another.
To compare and analyze overlapping techniques between layers, create a new layer that combines the data from the other layers. Click on the 'Create Layer from other layers' function, and reference the layers you wish to combine. Enter the layer identifiers in the 'Score Expression' field, and you'll be taken to the new combined layer screen.
Next, click on the 'color setup' button and set the 'high value' to the sum of the individual layer scores (e.g., 3, if you have two layers with scores of 1 and 2). This will highlight overlapping techniques, making it easier to identify commonalities and prioritize mitigation efforts.
Lastly, export the analyzed data in various formats, such as JSON, SVG, or Excel, to easily share and present your findings with your team. By following these steps, you can effectively use the MITRE ATT&CK Navigator to make informed decisions regarding your organization's cybersecurity posture.
How Can Organizations Use the MITRE ATT&CK Framework to Assess Their Security Posture and Identify Gaps?
Organizations can use the MITRE ATT&CK framework to assess their security posture and identify gaps by mapping their existing security controls against the known adversary tactics and procedures. This process helps identify potential gaps in their defenses and allows them to proactively take steps to improve their security posture.
How Can Organizations Effectively Map Their Security Controls to the MITRE ATT&CK Framework?
MITRE D3fend Matrix:
Organizations can effectively map their security controls to the MITRE ATT&CK framework by following a rigorous, well-documented process that includes identifying their assets, identifying potential adversary tactics and techniques, mapping their security controls against the known tactics and techniques, and analyzing the results to identify any potential gaps within their defenses.
MITRE ATT&CK Certification
In this section, we provide free training options and certification programs to gain comprehensive understanding of the MITRE ATT&CK Framework.
MITRE ATT&CK Defender
The MITRE ATT&CK Defender Certification Program (MADCP) is a training and credentialing initiative for cybersecurity professionals, emphasizing threat-informed defense and real-world skills.

Figure 9. MITRE ATT&CK Defender Certification Program (MADCP).
It offers on-demand and live courses, assessments, and certification to help individuals effectively apply the MITRE ATT&CK knowledge base in their work environment.
Picus Purple Academy Courses
Picus provides a comprehensive range of cybersecurity courses aimed at enhancing learners' advanced skills. These courses include the Command and Scripting Interpreter, Process Injection, PowerShell, Credential Dumping, and many other MITRE ATT&CK techniques. These courses are all part of the renowned “The MITRE ATT&CK Framework” Learning Path offered in the Purple Academy.
In addition to this Learning Path, Picus provides the Operationalizing MITRE ATT&CK for SOCs course as part of its Proactive Security Operations Center (SOC) Learning Path.
Furthermore, all courses included in the Purple Academy are offered free of charge and come with verifiable certification upon completion.
MITRE ATT&CK Evaluations
MITRE ATT&CK Evaluations are a series of assessments conducted by the MITRE Corporation to measure the effectiveness of cybersecurity products and solutions in detecting and responding to advanced persistent threats (APTs). These evaluations provide a standardized and transparent way for organizations to compare the capabilities of various cybersecurity products and make informed decisions when choosing a solution.
For example, in the MITRE ATT&CK, vendors were tested on their ability to detect tactics and techniques used by Wizard Spider and Sandworm APT groups, a sophisticated nation-state adversary known for their stealthy approach [10].

Figure #. MITRE Engenuity ATT&CK Evaluations - Enterprise [10].
The evaluation aimed to demonstrate how well each tested solution could detect and respond to these APT groups’ tactics across the entire kill chain, providing valuable insights for organizations looking to strengthen their cybersecurity posture.
Conclusion
The MITRE ATT&CK framework is a powerful tool that can help organizations improve their cybersecurity posture by providing a comprehensive view of the potential adversary tactics, techniques, and procedures. However, organizations should be aware of the challenges they may face when adopting the framework and should take steps to ensure that they have sufficient expertise, resources, and technical knowledge to use it effectively. By adopting the MITRE ATT&CK framework, organizations can prioritize their defenses against the most significant threats and improve their overall cybersecurity posture.

-3.png?width=353&height=200&name=image%20(79)-3.png)





.png?width=353&height=200&name=what-is-exposure-assessment-blog-preview%20(1).png)
