
How often do you ask yourself “are we secure?”
Modern cyber security stacks are often complex, but hardly gap-free. Manually maintaining a broad range of technologies is arduous without a helping hand from automation. Security teams need innovative tools in identifying security gaps in relation with the changing adversarial context.
Metric Driven Security Hardening
The factors such as business continuity concerns, cost and time constraints, and skills shortages created a vacuum in the security industry in terms of establishing a viable, metric, and evidence-driven security hardening process. Most enterprises either rely on their technology investments, free emulation tools with limited scope, or make do with the insight provided by sporadic assessment or lab-based tests.
Complete Visibility on Cyber-attack Readiness
Picus Threat Emulation Module assesses the “readiness level” of network, web application, endpoint, and email security controls in production networks, either being in operation 24x7 or on-demand for red team practices. The emulation module can be configured over multiple attack vectors simultaneously and can process thousands of adversarial scenarios in Picus Threat Library across your whole defensive estate, cloud-based or on-premise, in a matter of hours.
Picus assessments are categorically safe, technology-agnostic, and require limited deployment effort.

Empowering Security Teams
Threat Emulation Module is the pivotal piece of the Picus Platform. It bridges your defensive capabilities with the largest available adversarial library and links the identified gaps with the Picus Mitigation Library for quick risk elimination.
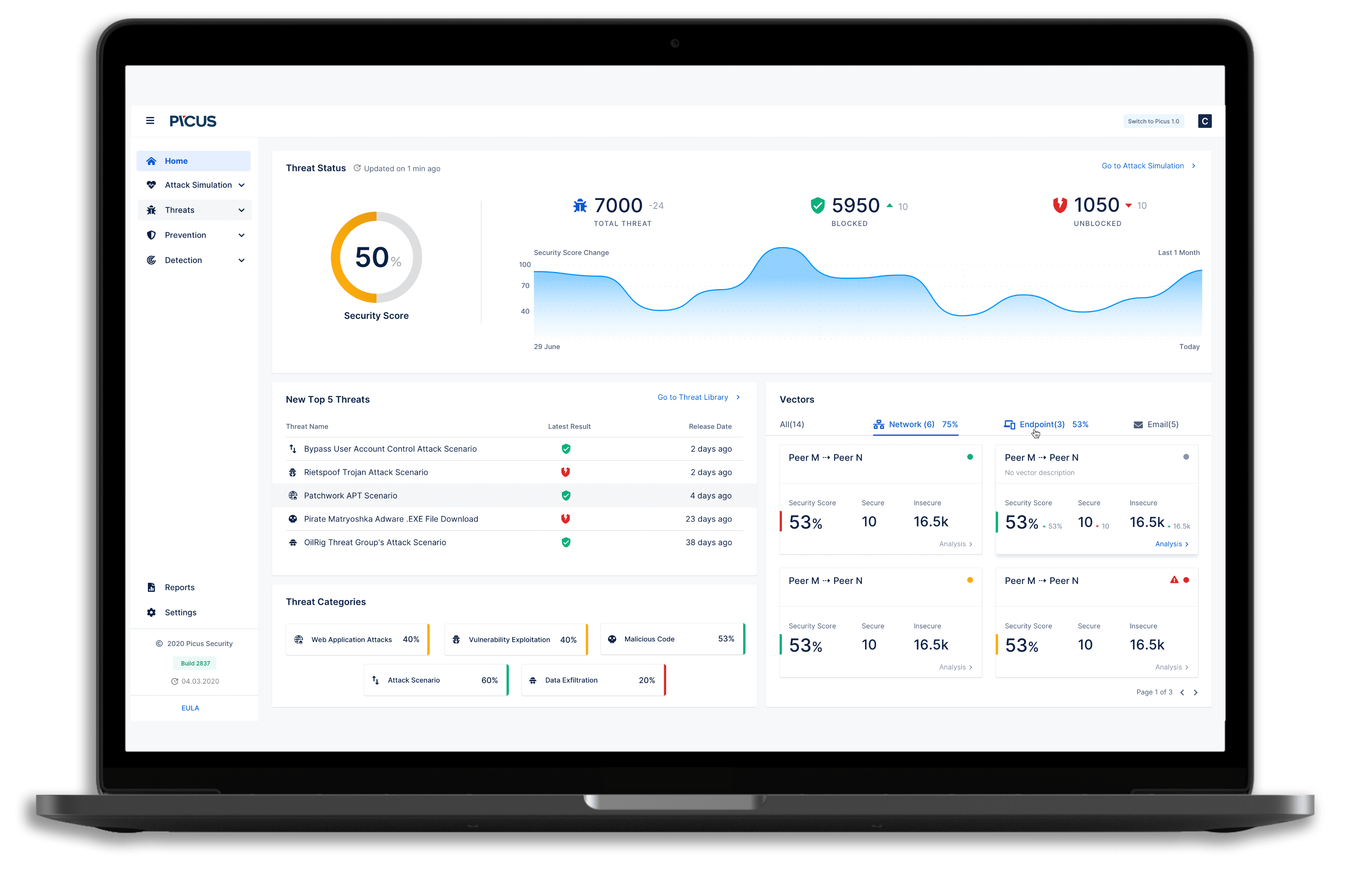


Emulation with the Best User Experience
Threat Emulation Module has an easy to use and functional user interface. Some key usability features are:
- Executive-level reporting
- Advanced notification features on sudden success rate drops
- Easy navigation among different attack vectors
- Advanced historical and vector-based comparisons
- Enriched threat or technique information visibility containing CVE, CWE, OWASP, cyber-kill chain, MITRE ATT&CK references, file hash information, targeted operating systems, targeted applications, and others.

