What is Common Vulnerability Scoring System (CVSS) ?
Are you struggling to navigate the complex world of cybersecurity? The Common Vulnerability Scoring System (CVSS) can be your guiding light. With its standardized methodology, CVSS enables you to assess, prioritize, and communicate the severity of software vulnerabilities effectively.
This blog explores the key components of CVSS, how it differs from other vulnerability scoring and assessment methodologies, and how you can use CVSS scores to fortify your organization's security stance. Don't let cyber threats catch you off guard - harness the power of CVSS and stay ahead of the game.
What Is CVSS? What Does CVSS Stand for?
CVSS stands for the Common Vulnerability Scoring System. It is a standardized framework used to classify and rate the severity of software vulnerabilities based on a set of measurable metrics. CVSS provides a consistent way to evaluate and prioritize security risks across different systems and organizations.
Who Developed the CVSS, and What Is Its Purpose?
The Common Vulnerability Scoring System (CVSS) was commissioned by the National Infrastructure Advisory Council (NIAC) to support the global Vulnerability Disclosure Framework and developed in collaboration with organizations such as in various IT vendors [1]. CVSS is now maintained and published by the Forum of Incident Response and Security Teams (FIRST) [2].
The purpose of CVSS is to provide a standardized, objective, and consistent framework for assessing the severity of security vulnerabilities. By assigning numerical scores to vulnerabilities, CVSS helps organizations understand the potential impact of these vulnerabilities on their systems and prioritize their response to security incidents. The scoring system takes into account factors such as exploitability, impact, and the affected component's environment, enabling organizations to make informed decisions when managing and mitigating security risks.
What Are the Main Components of the CVSS?
CVSS, or the Common Vulnerability Scoring System, is primarily organized into three core groups:
1. Base Metrics: These fundamental factors reflect the inherent characteristics of a vulnerability, not influenced by time or user environment.
2. Temporal Metrics: These elements assess vulnerability over time, including changes due to the availability of exploits and the effectiveness of remedies.
3. Environmental Metrics: These components account for the specific conditions of a user's environment, such as the potential impact on their operations.
In the following sections, we'll explore each of these components in more detail.
The Base Metric Group of CVSS
The base metrics in the Common Vulnerability Scoring System (CVSS) offer a comprehensive and technical evaluation of the severity of a given vulnerability, focusing on the inherent characteristics of the vulnerability itself.
CVSS Base Metrics have three sub-groupings [3]:
1. Exploitability Metrics
2. Impact Metrics, and
3. Scope.
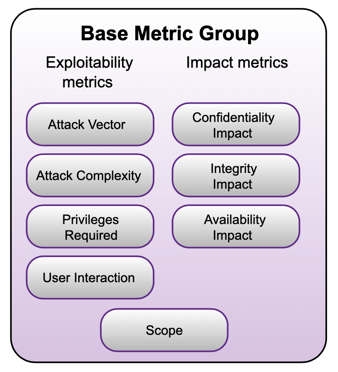
Figure 1. The Base Metric Group [3].
1. Exploitability Metrics
Exploitability metrics consists of four main sub metrics that determine how easily a vulnerability can be exploited and the conditions necessary for a successful attack. These metrics are given below.
-
Attack Vector (AV)
-
Attack Complexity (AC)
-
Privileges Required (PR)
-
User Interaction (UI)
Each sub metric is provided with a brief description.
-
Attack Vector (AV)
This metric evaluates the means by which an attacker can exploit the vulnerability, considering factors such as whether the attack can be executed remotely or requires physical access to the target system.
-
Attack Complexity (AC)
This metric quantifies the level of difficulty an attacker faces when attempting to exploit the vulnerability. It takes into account any requirements for the attacker to meet specific conditions, such as the need for social engineering or the presence of specific configurations on the target system.
-
Privileges Required (PR)
This metric assesses the level of privileges an attacker needs to have on the target system to successfully exploit the vulnerability, ranging from no privileges to high-level administrative privileges.
-
User Interaction (UI)
This metric measures whether or not an attacker needs to rely on a user's interaction with the system (e.g., clicking on a malicious link or opening a malicious file) to exploit the vulnerability.
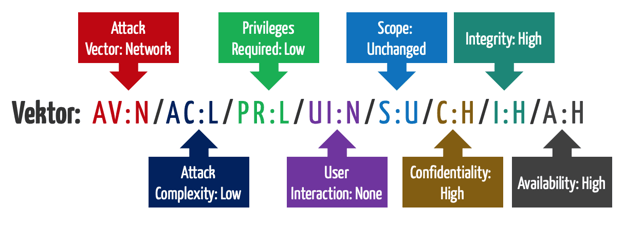
Figure 2. Metrics of the Base Metric Group Used in the Calculation of CVSS [4].
2. Impact Metrics
In CVSS, the impact metric consists of three main sub metrics that evaluate the potential consequences of a successful attack on the affected component.
-
Confidentiality Impact
-
Integrity Impact
-
Availability Impact
These metrics analyze the potential effects on the confidentiality, integrity, and availability of the data managed by the component. The Impact metrics consist of:
-
Confidentiality Impact (C)
This metric measures the impact of a successful attack on the confidentiality of the data managed by the affected component, ranging from no loss of confidentiality to a total loss.
-
Integrity Impact (I)
This metric gauges the impact of a successful attack on the integrity of the data managed by the affected component, evaluating the trustworthiness and veracity of the information after a successful exploit.
-
Availability Impact (A)
This metric assesses the impact of a successful attack on the availability of the affected component, determining how the vulnerability can disrupt the component's accessibility to authorized users and the resources it manages.
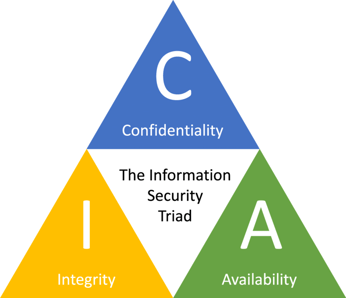
Figure 3. The Information Security Triad [5].
3. Scope
In addition to Exploitability and Impact metrics, CVSS also takes into account the Scope (S) metric, which captures whether a vulnerability in a component can impact resources in other components beyond its security scope, thus evaluating whether a vulnerability breaches security boundaries.
The Temporal Metric Group of CVSS
Temporal metrics in the Common Vulnerability Scoring System (CVSS) assess the current state of exploit techniques or code availability, the existence of any patches or workarounds, and the confidence in the description of a vulnerability.
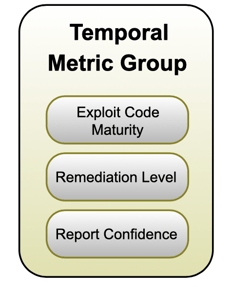
Figure 4. The Temporal Metric Group [3].
The Temporal metric consists of three main sub metrics.
-
Exploit Code Maturity (E),
-
Remediation Level (RL), and
-
Report Confidence (RC).
Below, you can find a description for each sub metric.
1. Exploit Code Maturity
Exploit Code Maturity measures the likelihood of a vulnerability being attacked, based on the current state of exploit techniques, exploit code availability, or active exploitation. The more easily a vulnerability can be exploited, the higher the vulnerability score. Values range from "High" when functional autonomous code exists or no exploit is required, to "Unproven" when no exploit code is available or an exploit is theoretical.
2. Remediation Level
Remediation Level reflects the availability and permanence of fixes for a vulnerability, an important factor for prioritization. The less official and permanent a fix, the higher the vulnerability score. Values range from "Unavailable" when no solution is available or it is impossible to apply, to "Official Fix" when a complete vendor solution, such as an official patch or upgrade, is available [3].
2. Report Confidence
Report Confidence measures the degree of confidence in the existence of the vulnerability and the credibility of the known technical details. The more a vulnerability is validated by the vendor or other reputable sources, the higher the score. Values range from "Confirmed" when detailed reports exist or functional reproduction is possible, to "Unknown" when there are reports of impacts indicating the presence of a vulnerability, but the cause is uncertain or the reports differ on the cause or impacts [3].
The Environmental Metric Group of CVSS
Environmental metrics in the Common Vulnerability Scoring System (CVSS) allow analysts to customize CVSS scores based on the importance of the affected IT asset to a user's organization.
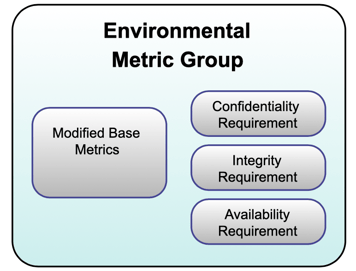
Figure 5. The Environmental Metric Group [3].
The Environmental Metric consists of two main sub metrics, which are given below.
- Security Requirements (CR, IR, AR)
- Confidentiality Requirement
- Integrity Requirement
- Availability Requirement
- Modified Base Metrics
Below, you will find a brief description for each sub metric.
1. Security Requirements
Security Requirements enable analysts to adjust CVSS scores depending on the importance of Confidentiality, Integrity, and Availability for the affected IT asset within the organization. Each security requirement has three possible values: Low, Medium, or High. The environmental score is affected by reweighting the corresponding Modified Base Impact metrics, such as Modified Confidentiality, Integrity, and Availability impact metrics, based on the selected security requirement.
2. Modified Base Metrics
Modified Base Metrics let analysts override individual base metrics based on specific characteristics of a user's environment. These metrics influence the Environmental Score by overriding Base metric values before applying the Environmental Security Requirements. Characteristics that affect Exploitability, Scope, or Impact can be reflected in the Modified Environmental Score. Each Modified Environmental metric has the same values as its corresponding Base metric, along with a "Not Defined" value.
How Does CVSS Differ From Other Vulnerability Scoring and Assessment Methodologies?
CVSS differentiates itself from other vulnerability scoring and assessment methodologies by offering a comprehensive, open framework that evaluates security vulnerabilities using well-defined metrics.
These metrics are divided into three groups: Base, Temporal, and Environmental.
Base metrics assess inherent vulnerability characteristics, while Temporal metrics focus on time-dependent aspects, and Environmental metrics consider the vulnerability's specific context within an organization. By combining these metrics, CVSS generates a numerical score, reflecting the risk level associated with a vulnerability.
This standardized and transparent approach allows organizations to effectively prioritize remediation efforts and make informed decisions about their security posture. CVSS promotes a shared understanding of vulnerability severity across systems, stakeholders, and cybersecurity professionals, enabling better communication and collaboration in addressing security threats. Its technical foundation makes it a valuable, adaptable tool for assessing and managing vulnerabilities across diverse environments.
What Are the Different Versions of CVSS, and What Are the Key Differences Between Them?
Since its inception, CVSS has undergone multiple revisions to address evolving cybersecurity needs and improve its accuracy and applicability. The key versions of CVSS include
-
CVSS v1,
-
CVSS v2, and
-
CVSS v3, with the latest version being CVSS v3.1.
CVSS v1 [6], the first iteration, provided a baseline for assessing vulnerabilities. However, it had limitations in terms of granularity and precision, leading to the development of CVSS v2.
CVSS v2 [7] introduced several enhancements, including refined metric definitions and better vulnerability classification. Despite these improvements, CVSS v2 still had some shortcomings in addressing the diverse range of vulnerabilities and their impacts on modern systems.
CVSS v3 [8] addressed the limitations of CVSS v2 by introducing significant changes to its metric groups, refining the scoring methodology, and offering a more accurate representation of vulnerability severity. Some key updates in CVSS v3 include the addition of new metrics, such as "User Interaction" and "Scope," as well as the separation of "Access Vector" into two distinct metrics: "Attack Vector" and "Attack Complexity."

Figure 6. The Latest CVSS Version, v3.1 [9].
CVSS v3.1, the latest version, builds on the foundation of CVSS v3 by introducing minor updates and clarifications to improve its usability and effectiveness [10]. The changes in CVSS v3.1 primarily focus on refining metric definitions and guidance [11], ensuring that the framework remains relevant and accurate in assessing contemporary cybersecurity threats.
How Is CVSS Score Calculated?
CVE Entries, or Common Vulnerabilities and Exposures, are scored using the CVSS (Common Vulnerability Scoring System). CVSS is an open framework that provides a standardized approach to assessing and rating the severity of software vulnerabilities. This system helps organizations prioritize vulnerability remediation efforts and better understand the potential impact of a vulnerability on their systems.
CVSS scores are calculated based on three metric groups:
-
Base
-
Temporal
-
Environmental
A CVSS score ranges from 0 to 10, with 0 indicating no impact and 10 indicating the highest possible severity.
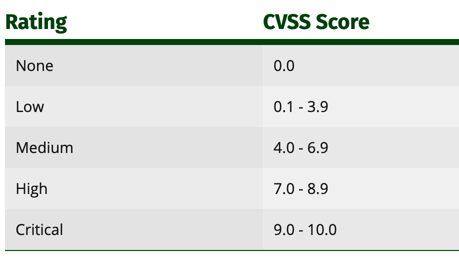
Figure 8. CVSS v3.0 Ratings [9].
The scores are usually represented in a vector format, which provides detailed information about the various metric values. Organizations can use these scores to prioritize remediation efforts and allocate resources to address the most critical vulnerabilities first.
How Is CVSS v3.1 Base Score Calculated?
The CVSS Base Score equation consists of two main components:
-
Impact, and
-
Exploitability
These two components are combined to calculate the overall Base Score. The higher the score, the more severe the vulnerability is considered to be. The Base Score ranges from 0 to 10, with 0 indicating no risk and 10 representing the highest level of severity.
-
Impact
This component reflects the consequences of a vulnerability on the affected system in terms of confidentiality, integrity, and availability. It considers how much damage can be done if the vulnerability is exploited.
-
Exploitability
This component assesses how easy it is for an attacker to exploit the vulnerability. It takes into account factors such as the method of attack, the complexity of the attack, the level of access required, and the degree of user interaction needed for a successful exploit.
CVSS v3.1 Base Score Equation
|
Base score is defined as, If (Impact sub-score <= 0) 0 else, Scope Unchanged Roundup(Minimum[(Impact + Exploitability), 10]) Scope Changed Roundup(Minimum[1.08 x (Impact + Exploitability), 10]) The Impact sub-score (ISC) is defined as follows: Scope Unchanged 6.42 x ISC{Base} Scope Unchanged 7.52 x [ISC{Base}- 0.029] - 3.25 x [ISC{Base} - 0.02]^15, where ISC{Base} = 1 - [(1 - Impact{Conf}) x (1 - Impact{Integ}) x(1 - Impact{Avail})] The Exploitability sub-score is given below. 8.22 x AttackVector x AttackComplexity x PrivilegeRequired x UserInteraction |
Equation 1. CVSS v3.1 Base Score Equations [12].
CVSS v3.1 Base Score Calculator
The National Institute of Standards and Technology (NIST) provides access to the Common Vulnerability Scoring System (CVSS) calculator, which is a framework that helps organizations assess the severity of software vulnerabilities. CVSS is an open, standardized system that calculates a score based on the characteristics of the vulnerability, taking into account factors related to both exploitability and impact.
To use the NIST CVSS calculator, follow these steps:
-
Visit the NIST's CVSS Calculator website:
-
Input the relevant sub-parameters under the Exploitability and Impact Metrics.
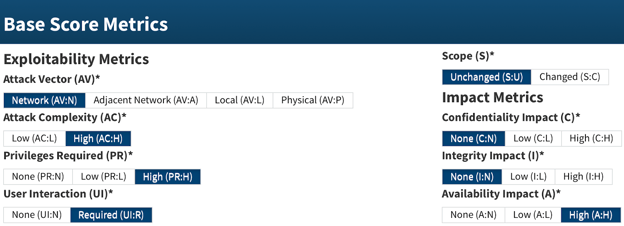
Figure 5. Base Metrics Parameters from NIST [12].
-
Once you have selected the sub-parameters, the calculator will generate a CVSS score ranging from 0 to 10, with 0 being the lowest severity and 10 being the highest. The score will be accompanied by a severity rating (None, Low, Medium, High, or Critical), providing a standardized assessment of the vulnerability's risk.
-
As you decide on the parameters or change some of your selections, you will see a dynamic score that is adaptive to your selections.
How Is CVSS v3.1 Temporal Score Calculated?
The Temporal score is a rating system that combines four different factors to provide an overall assessment of a vulnerability or risk. It takes into account the
- fundamental severity of the issue,
- the maturity of the exploit code,
- the availability and effectiveness of a solution to address the vulnerability, and
- the reliability of the information about the vulnerability.
By multiplying these factors together and rounding up the result, the Temporal score helps in understanding the current status and potential impact of a specific vulnerability or risk, considering not only its inherent properties but also external factors that may affect its exploitation and mitigation.
CVSS v3.1 Temporal Score Equation
The CVSS v3.1 Temporal Score Equation is a dynamic scoring method that evaluates the risk posed by a vulnerability while accounting for factors that change over time, such as exploit code maturity, remediation level, and report confidence. This equation provides a more nuanced understanding of vulnerabilities by considering the evolving nature of both threat information and response efforts.
|
Roundup(BaseScore x ExploitCodeMaturity x RemediationLevel x ReportConfidence) |
Equation 2. CVSS v3.1 Temporal Score Equation [12].
These metrics represent factors that change over time as vulnerability information and remediation efforts evolve.
How Is CVSS v3.1 Environmental Score Calculated?
Environmental Score Impact Metrics (ESIM) are quantitative measures designed to assess the potential impact of vulnerabilities on a given environment. These metrics take into account various factors, such as the modified impact subscore, exploitability, and scope, to provide a comprehensive understanding of the potential risk posed by a particular vulnerability.
The environmental score is calculated based on specific formulas, which vary depending on whether the modified scope is unchanged or changed. In both cases, the score incorporates elements like exploit code maturity, remediation level, and report confidence to ensure a well-rounded evaluation.
CVSS v3.1 Environmental Score Equation
|
The environmental score is defined as the following: If (Modified Impact Sub score <= 0) 0 else, If Modified Scope is Unchanged Round up(Round up (Minimum [ (M.Impact + M.Exploitability) ,10]) × Exploit Code Maturity × Remediation Level × Report Confidence)
If Modified Scope is Changed Round up(Round up (Minimum [1.08 × (M.Impact + M.Exploitability) ,10]) × Exploit Code Maturity × Remediation Level × Report Confidence) The formula for the modified Impact sub score is given below: If Modified Scope is Unchanged 6.42 × [𝐼𝑆𝐶𝑀𝑜𝑑𝑖𝑓𝑖𝑒𝑑]
If Modified Scope is Changed 7.52 × [𝐼𝑆𝐶𝑀𝑜𝑑𝑖𝑓𝑖𝑒𝑑 − 0.029]-3.25× [𝐼𝑆𝐶𝑀𝑜𝑑𝑖𝑓𝑖𝑒𝑑 × 0.9731 − 0.02] 13 Where, 𝐼𝑆𝐶𝑀𝑜𝑑𝑖𝑓𝑖𝑒𝑑 = 𝑀𝑖𝑛𝑖𝑚𝑢𝑚 [[1 − (1 − 𝑀. 𝐼𝐶𝑜𝑛𝑓 × 𝐶𝑅) × (1 − 𝑀. 𝐼𝐼𝑛𝑡𝑒𝑔 × 𝐼𝑅) × (1 − 𝑀. 𝐼𝐴𝑣𝑎𝑖𝑙 × 𝐴𝑅)], 0.915] The Modified Exploitability sub score is defined as 8.22 × 𝑀. 𝐴𝑡𝑡𝑎𝑐𝑘𝑉𝑒𝑐𝑡𝑜𝑟 × 𝑀. 𝐴𝑡𝑡𝑎𝑐𝑘𝐶𝑜𝑚𝑝𝑙𝑒𝑥𝑖𝑡𝑦 × 𝑀. 𝑃𝑟𝑖𝑣𝑖𝑙𝑒𝑔𝑒𝑅𝑒𝑞𝑢𝑖𝑟𝑒𝑑 × 𝑀. 𝑈𝑠𝑒𝑟𝐼𝑛𝑡𝑒𝑟𝑎𝑐𝑡𝑖𝑜n |
Equation 3. CVSS v3.1 Environmental Score Equation [12].
The modified impact subscore, a key component of the environmental score, is derived from various parameters, such as confidentiality, integrity, and availability. It also factors in the ISCModified value, which is a minimum function dependent on the interaction of multiple variables.
The modified exploitability subscore takes into account attack vector, attack complexity, privilege required, and user interaction to provide a comprehensive understanding of the vulnerability's exploitability. By combining these components, ESIM offers a robust framework for evaluating the potential impact of vulnerabilities on an environment.
How Can Organizations Use CVSS Scores to Prioritize Vulnerabilities and Risks?
Organizations can leverage CVSS scores to prioritize vulnerabilities and risks by evaluating the severity of identified software flaws and potential impacts on their systems. The comprehensive scoring system, which includes Base, Temporal, and Environmental metrics, allows organizations to assess each vulnerability in terms of its inherent properties, time-dependent factors, and specific impact on the organization's environment.
By using CVSS scores, organizations can systematically identify and prioritize high-severity vulnerabilities that require immediate attention and remediation, ensuring optimal allocation of resources and minimizing potential impacts. Furthermore, CVSS scores facilitate effective communication among security teams, IT professionals, and decision-makers, enabling a common understanding of the risk landscape and fostering a more efficient vulnerability management process.
What Tools and Technologies Are Commonly Used in Conjunction With CVSS Scoring?
Several tools and technologies can be employed in conjunction with CVSS scoring to enhance vulnerability management efforts.
-
Vulnerability scanners often incorporate CVSS scores into their reports, enabling organizations to prioritize remediation efforts based on the assessed severity of identified vulnerabilities.
-
Additionally, security information and event management (SIEM) solutions may utilize CVSS scores to correlate vulnerability information with security events and incidents.
-
Threat intelligence platforms can complement CVSS scores by providing contextual information on threat actors, real-world exploit activities, and emerging threats, helping organizations better understand the actual risk associated with a given vulnerability.
-
Furthermore, risk management tools and frameworks, like NIST's Risk Management Framework, can incorporate CVSS scores to inform risk assessments and mitigation strategies.
How Does CVSS Work With Other Cybersecurity Standards and Frameworks, Such As CVE and CWE?
CVSS complements other cybersecurity standards and frameworks by providing a quantitative and standardized method for assessing vulnerability severity. The Common Vulnerabilities and Exposures (CVE) system is a widely used catalog of known vulnerabilities, where each entry is assigned a unique identifier and a corresponding CVSS score to represent its severity. This integration allows organizations to quickly assess the risk associated with a specific CVE entry and prioritize remediation efforts accordingly.
Similarly, the Common Weakness Enumeration (CWE) is a community-driven catalog of software security weaknesses that provides a common language for discussing and understanding the causes of software vulnerabilities. By mapping CWE entries to CVSS scores, organizations can gain a better understanding of the potential severity of a weakness, enabling them to prioritize secure coding practices and security testing efforts. Overall, the integration of CVSS with other cybersecurity standards and frameworks, such as CVE and CWE, contributes to a more cohesive and effective approach to vulnerability management and risk mitigation.








