What is CVE (Common Vulnerabilities and Exposures) ?
Navigating the complex landscape of cybersecurity requires constant vigilance and a deep understanding of the tools at your disposal. One such indispensable tool for cybersecurity professionals is the Common Vulnerabilities and Exposures (CVE) system. As a comprehensive, standardized database of known security threats, CVE empowers organizations to identify, track, and address vulnerabilities effectively. Are you maximizing the potential of CVE to fortify your organization's security stance? Delve into the details of CVE and learn practical strategies for leveraging its benefits to stay ahead in the ever-evolving world of cybersecurity.
What Is a CVE? What Does CVE Stand for?
Common Vulnerabilities and Exposures (CVE) is an industry-standard list of publicly known information-security vulnerabilities and exposures. Each CVE entry is assigned a unique identifier (ID), allowing organizations to accurately assess and manage their security posture by identifying, categorizing, and addressing specific vulnerabilities.
By establishing a consistent approach to indexing and documenting vulnerabilities, CVEs serve as a trusted source of information for academic researchers, vendors, and end-users. This helps in the discovery and mitigation of software weaknesses across multiple platforms and operating systems, fostering enhanced cybersecurity measures across a wide range of products and services.
What is Vulnerability?
A vulnerability is a specific weakness or flaw within a software, hardware, or network system that can be exploited by an attacker to compromise its security. Vulnerabilities may arise from a range of sources, including but not limited to
-
Human Error
-
Design Flaws
-
Configuration Issues
-
Third-party Components
-
Unpatched Software
-
Zero-day Vulnerabilities
a. Human Error
Mistakes made by developers during the coding process can lead to vulnerabilities, such as buffer overflows, null pointer dereferences, or race conditions. These errors may allow attackers to execute arbitrary code, cause a denial of service, or access sensitive data.
b. Design Flaws
Inadequate design or architecture of a system can result in security weaknesses. For example, a system that lacks proper authentication, authorization, or encryption mechanisms may be vulnerable to attacks.
c. Configuration Issues
Misconfigured systems or services can lead to vulnerabilities, such as open ports, weak encryption settings, or default passwords. These issues may provide an attacker with unauthorized access or the ability to intercept sensitive data.
d. Third-party Components
Vulnerabilities may be present in third-party libraries, plugins, or frameworks used within an application or system. These vulnerabilities can be exploited by an attacker to compromise the entire system.
e. Unpatched or Unsupported Software
Outdated software versions may contain known vulnerabilities that have already been fixed in newer releases. Failing to apply security patches in a timely manner can leave systems exposed to attacks.
f. Zero-day Vulnerabilities
These are previously unknown vulnerabilities that are discovered and exploited by attackers before the vendor or developer becomes aware of them and releases a patch.
Identifying and mitigating vulnerabilities is a critical aspect of maintaining a strong cybersecurity posture. This involves continuous vulnerability scanning, assessment, and timely patch management to minimize the risk of potential exploitation by malicious actors.
What is an Exposure?
An exposure is a situation where a system, application, or network is unintentionally accessible or visible to potential attackers, increasing the risk of unauthorized access or security breaches. Exposures can arise from various factors such as misconfigurations, design flaws, or human error. They do not necessarily involve an inherent weakness or vulnerability within the system but rather represent conditions that make a system more susceptible to attacks or unauthorized access.
Exposures can lead to significant data breaches, including unauthorized access to personally identifiable information (PII) or other sensitive data. Both accidental exposures and sophisticated cyber attacks can result in severe security incidents, emphasizing the importance of comprehensive risk management and proactive security measures.
What Is the Purpose of the CVE System in Cybersecurity?
The CVE system serves seven critical purposes in cybersecurity, making it an invaluable resource for security professionals, researchers, and organizations. Some of the key purposes include:
1. Standardization of Vulnerabilities
2. Centralized Repository
3. Vulnerability Tracking
4. Vulnerability Assessment and Management
5. Risk Assessment
6. Coordination and Collaboration
7. Awareness and Education
Below, each aspect is accompanied by a brief explanation
a. Standardization of Vulnerabilities
The CVE system assigns a unique identifier (CVE-ID) to each vulnerability, providing a standardized way of referencing security flaws in software and hardware systems. This helps vendors, organizations, end-users, security experts, and researchers communicate more effectively about vulnerabilities and their corresponding mitigation strategies.
b. Centralized Repository
The CVE system acts as a centralized repository of known cybersecurity vulnerabilities, making it easy for security professionals to access information on identified flaws, their impact, affected products, and remediation steps.
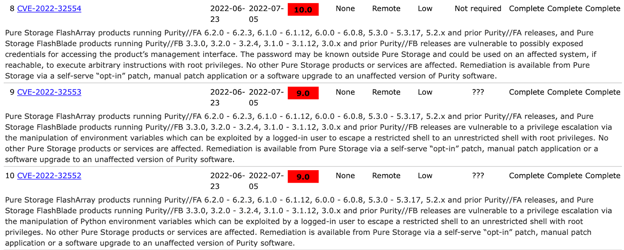
Figure 1. CVE List [2].
c. Vulnerability Tracking
By providing a consistent naming scheme and a centralized database, the CVE system simplifies the process of tracking vulnerabilities over time. This helps organizations monitor their security posture and prioritize patching and mitigation efforts.
d. Vulnerability Assessment and Management
The CVE system supports vulnerability assessment and management by providing a foundation for security tools, such as vulnerability scanners and intrusion detection systems, to identify and analyze known vulnerabilities in software and hardware systems.
e. Risk Assessment
The CVE system, along with associated scoring systems like the Common Vulnerability Scoring System (CVSS), helps organizations assess the risk posed by specific vulnerabilities. This enables them to prioritize their resources and focus on addressing the most critical vulnerabilities first.
f. Coordination and Collaboration
The CVE system encourages coordination and collaboration among vendors, security researchers, and organizations. By creating a public, shared resource for vulnerability information, the CVE system helps stakeholders work together to improve overall cybersecurity.
g. Awareness and Education
By maintaining an up-to-date record of known vulnerabilities, the CVE system raises awareness about security issues and helps educate organizations, professionals, and users about potential threats and best practices for maintaining secure systems.
How Does CVE Help Organizations Identify and Manage Security Vulnerabilities?
CVEs play a foundational role in the process of identifying and managing security vulnerabilities. The use of CVE identifiers helps streamline the coordination of remediation efforts. When security incidents occur, security analysts can quickly and accurately communicate the nature of the vulnerability and the severity, allowing for timely mitigation.
CVEs also provide context for incident response teams to find information more quickly and conduct a rapid response to a breach. Moreover, organizations can use CVE information on software and hardware to assess whether those products are compatible with their existing IT infrastructure and are secure and compliant with industry standards.
What Is the Structure of a CVE Identifier?
A CVE Identifier is a unique identifier assigned to publicly known cybersecurity vulnerabilities. It is a standardized method of naming these vulnerabilities to make it easier for security researchers, vendors, and organizations to communicate and share information about them.
A CVE Identifier consists of three parts:
-
CVE: The acronym itself, which stands for "Common Vulnerabilities and Exposures."
-
YEAR: A four-digit year, representing the year the CVE was assigned or when the vulnerability was made public.
-
NUMBER: A series of digits, typically four to six, that uniquely identifies the specific vulnerability within the given year.

Figure 1. CVE-2023-23397 Vulnerability.
How Are CVE Identifiers Assigned to Vulnerabilities?
CVE Numbering Authorities (CNAs) are integral to the cybersecurity landscape, as they are responsible for assigning and cataloging Common Vulnerabilities and Exposures (CVE) identifiers [3]. These standardized identifiers facilitate the tracking and communication of security vulnerabilities.
a. Who Are CNAs?
CNAs include IT vendors and other tech companies. Currently, there are 238 CNAs across 36 countries, collaborating within a standardized system to efficiently identify and address security vulnerabilities in their respective domains [3]. The full list of CVE numbering authorities can be found here.
They collaborate within a standardized system to efficiently identify and address security vulnerabilities in their respective domains.
b. What Is Root CNA?
The MITRE Corporation, a not-for-profit organization that operates federally funded research and development centers in the United States, serves as the editor and primary CNA for the CVE program. In this role, MITRE oversees the program's policies, procedures, and infrastructure, ensuring the CVE list is consistently maintained and updated.
While other CNAs assign CVE identifiers to vulnerabilities within their own domain, MITRE is also authorized to issue CVEs directly. This highlights MITRE's central position in the CVE program and emphasizes their commitment to maintaining a reliable and efficient system for addressing security vulnerabilities.
How Are New Vulnerabilities Added to the CVE Database?
The process of adding new vulnerabilities to the CVE database is both thorough and systematic, ensuring that each entry is accurately documented, verifiable, and has a tangible impact on public security. The Community Mapping Project gathers information on vulnerabilities from reliable sources, then generates and validates corresponding CVE Identifiers. Following this, a team of experienced experts at MITRE Corporation rigorously evaluates each vulnerability.
This comprehensive approach guarantees that every vulnerability in the CVE database is assigned a unique identifier, and that each entry is accurately described and scored based on the potential severity of its impact on software users.
What Is the Process for Reporting a Potential Vulnerability to the CVE System?
When new vulnerabilities are discovered, they are added to the CVE database through a systematic process.
Here's an overview of how that process works:
1. Vulnerability Discovery: A researcher, security expert, or organization discovers a new vulnerability in a software or hardware system. This could be through manual analysis, automated tools, bug bounties, or other methods.
2. Contacting the Vendor/Project: If possible, it is recommended to contact the vendor or project responsible for the affected software or hardware system to report the vulnerability. This allows the vendor to assess and address the issue and may provide additional information for the CVE entry.
3. Check for a CVE Numbering Authority (CNA): Determine if the affected vendor or project has a designated CNA responsible for assigning CVE-IDs. A list of CNAs can be found on the CVE website. If a CNA is available, report the vulnerability to them. They will assess the submission and, if appropriate, assign a CVE-ID and document the vulnerability.
4.Request a CVE-ID: If the vendor or project does not have a CNA or if you cannot identify one, you can request a CVE-ID directly from the CVE Program. To do this, you need to fill out the web form available on the CVE website. Provide as much information as possible about the vulnerability, including its impact, affected products, and any available remediation steps.
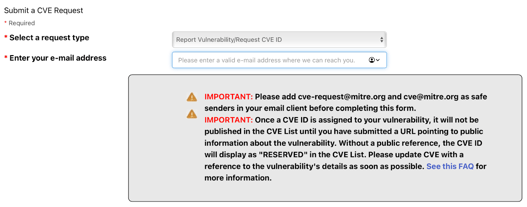
Figure 2. CVE ID Requesting Web Form [4].
5. Analysis and Assignment: After submitting the vulnerability report, the CVE Program or CNA will review the submission. Note that they may request additional information or clarification.
If the submission is accepted, the CVE Program or a CNA will analyze the vulnerability and assign a unique CVE Identifier (CVE-ID) to it. The CVE-ID follows the format "CVE-YYYY-NNNNN", where "YYYY" is the year and "NNNNN" is a unique number.
6. Documentation: The vulnerability's details, such as its impact, affected products, and remediation steps, are documented in the CVE database entry. The entry also includes references to other resources, like security advisories or technical reports.
7. Publication: The CVE entry is published on the CVE database, making it accessible to the public. It may be marked as "RESERVED" initially, meaning that details are withheld until the affected vendor has had time to address the issue.
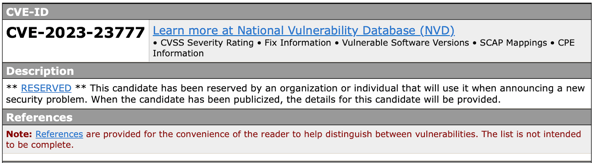
Figure 3. Example of a Reserved CVE [5].
8. Updates and Maintenance: As new information becomes available, the CVE entry may be updated to reflect changes in the vulnerability's status, such as whether a patch has been released or if new affected products are identified.
The CVE database serves as an essential resource for security professionals, researchers, and organizations, helping them stay informed about known vulnerabilities and take appropriate steps to secure their systems.
How Are CVE Entries Scored?
CVE entries are scored using the Common Vulnerability Scoring System (CVSS), which provides a standardized method for assessing the severity of security vulnerabilities. CVSS scores range from 0 to 10, with 10 representing the highest severity. The scoring system considers several factors to rate the impact and exploitability of a vulnerability.
In the following sections, we will delve deeper into CVSS and its three metrics that comprise the system
What Is the CVSS (Common Vulnerability Scoring System)?
CVE Entries, or Common Vulnerabilities and Exposures, are scored using the CVSS (Common Vulnerability Scoring System). CVSS is an open framework that provides a standardized approach to assessing and rating the severity of software vulnerabilities. This system helps organizations prioritize vulnerability remediation efforts and better understand the potential impact of a vulnerability on their systems.
CVSS scores are calculated based on three metric groups:
-
Base
-
Temporal
-
Environmental
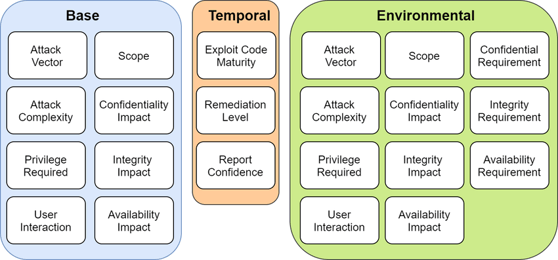
Figure 4. Base, Temporal and Environmental Management with CVE [6].
Base Metrics
These metrics represent the intrinsic characteristics of a vulnerability that are constant over time and across different environments.
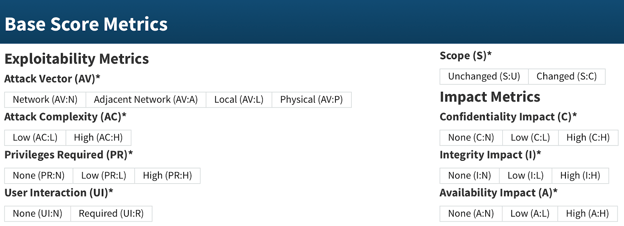
Figure 5. Base Metrics Parameters from NIST [7].
Attack Vector (AV): This metric reflects the means by which an attacker can exploit a vulnerability (e.g., local, adjacent network, network).
Attack Complexity (AC): This metric measures the conditions that must be met for an attacker to exploit the vulnerability (e.g., low, high).
Privileges Required (PR): This metric indicates the level of privileges an attacker must possess to exploit the vulnerability (e.g., none, low, high).
User Interaction (UI): This metric determines if user involvement is needed for a successful exploit (e.g., none, required).
Scope (S): This metric denotes whether a vulnerability can affect resources beyond its security scope (e.g., unchanged, changed).
Confidentiality Impact (C): This metric measures the impact on the confidentiality of the affected system's data (e.g., none, low, high).
Integrity Impact (I): This metric measures the impact on the integrity of the affected system's data (e.g., none, low, high).
Availability Impact (A): This metric measures the impact on the availability of the affected system's resources (e.g., none, low, high).
Temporal Metrics
These metrics represent factors that change over time as vulnerability information and remediation efforts evolve.
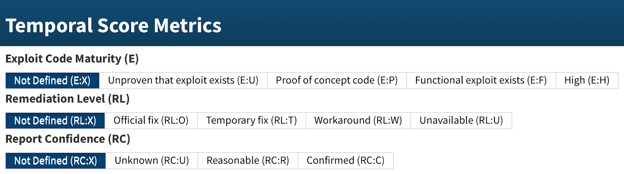
Figure 6. Temporal Metrics Parameters from NIST [7].
Exploit Code Maturity (E): This metric measures the likelihood of an exploit being available (e.g., not defined, high, functional, Proof-of-Concept (PoC), unproven).
Remediation Level (RL): This metric reflects the availability of a fix or workaround for the vulnerability (e.g., not defined, official fix, temporary fix, workaround, unavailable).
Report Confidence (RC): This metric measures the level of confidence in the existence of the vulnerability and its details (e.g., not defined, confirmed, reasonable, unknown).
Environmental Score Impact Metrics
These metrics account for the potential impact of a vulnerability on a specific organization, considering the unique characteristics of its environment.
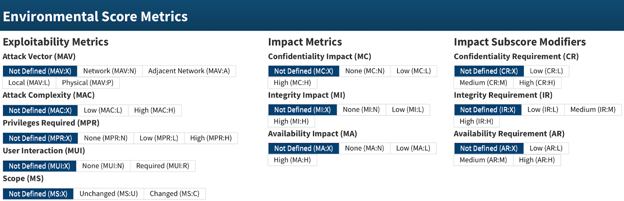
Figure 7. Environmental Score Impact Metrics Parameters from NIST [7].
Confidentiality Requirement (CR): This metric reflects the importance of confidentiality to the organization (e.g., not defined, low, medium, high).
Integrity Requirement (IR): This metric reflects the importance of integrity to the organization (e.g., not defined, low, medium, high).
Availability Requirement (AR): This metric reflects the importance of availability to the organization (e.g., not defined, low, medium, high).
A CVSS score ranges from 0 to 10, with 0 indicating no impact and 10 indicating the highest possible severity.
|
Rating |
CVSS Score |
|
None |
0.0 |
|
Low |
0.1 - 3.9 |
|
Medium |
4.0 - 6.9 |
|
High |
7.0 - 8.9 |
|
Critical |
9.0 - 10.0 |
The scores are usually represented in a vector format, which provides detailed information about the various metric values. Organizations can use these scores to prioritize remediation efforts and allocate resources to address the most critical vulnerabilities first.
For more detailed information, visit our blog on CVSS here.
How Can Organizations Use CVE Information to Assess the Severity of Vulnerabilities?
Organizations can effectively use CVE information to assess the severity of vulnerabilities by staying up-to-date with trusted databases such as the NIST National Vulnerability Database and MITRE's CVE database. Identifying relevant vulnerabilities and employing CVSS scores allows organizations to prioritize their patching and mitigation efforts based on the severity of the identified issues. Further prioritization should involve considering the attack vector, evaluating the potential impact on the confidentiality, integrity, and availability (CIA) triad, and assessing the exploitability of each vulnerability. By developing and implementing comprehensive remediation plans to address these vulnerabilities, organizations can ensure they are proactively responding to potential threats.
Continuous monitoring and reassessment of the severity of both new and existing vulnerabilities is crucial in maintaining a robust security posture and staying ahead of emerging risks in the ever-evolving cybersecurity landscape.
What Is the Difference Between a CVE and a CWE?
CVE (Common Vulnerabilities and Exposures) and CWE (Common Weakness Enumeration) work in tandem to enhance software security by addressing distinct yet interconnected aspects of vulnerabilities and weaknesses. CVE's role is to pinpoint specific vulnerabilities, offering unique identifiers that allow security practitioners to accurately track and manage these issues in various systems and applications. Meanwhile, CWE delves deeper into the root causes of these vulnerabilities, encompassing coding errors, design flaws, and implementation oversights, which facilitates the identification of recurring patterns and trends in software weaknesses.
By combining CVE's precise vulnerability tracking with CWE's comprehensive understanding of the underlying issues, developers and security professionals can implement more effective mitigation strategies and cultivate secure coding practices. Together, CVE and CWE create a holistic and contextual approach to understanding and managing software security risks, fostering improved communication and collaboration within the industry.
CVE vs. CWE Comparison Table
|
Aspect |
CVE (Common Vulnerabilities and Exposures) |
CWE (Common Weakness Enumeration) |
|
Purpose |
Identifying and naming specific vulnerabilities |
Classifying and describing types of weaknesses |
|
Focus |
Specific vulnerabilities in software or systems |
Underlying weaknesses that lead to vulnerabilities |
|
Identification |
Unique identifiers and description for individual vulnerabilities, e.g. CVE-2023-22921 Zyxel NBG-418N v2 firmware Cross-Site Scripting vulnerability |
Unique identifiers and description for weakness categories, e.g. Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') |
|
Usage |
Tracking, managing, and mitigating known vulnerabilities |
Understanding, prioritizing, and addressing common software weaknesses |
|
Role |
Facilitates communication and consistency in vulnerability management |
Provides a common framework and language for discussing software weaknesses |
In summary, CVE is focused on identifying and naming specific vulnerabilities, while CWE is focused on classifying and describing the types of weaknesses that can lead to those vulnerabilities. Both standards play a crucial role in secure software development and vulnerability management.
How Can Organizations Keep Track of CVEs Relevant to Their Systems and Applications?
Organizations can keep track of CVEs relevant to their systems and applications by maintaining an up-to-date inventory of hardware and software assets, subscribing to vulnerability notification services like NIST's National Vulnerability Database (NVD) and MITRE's CVE database, and implementing a vulnerability management solution to automatically detect vulnerabilities.
By filtering CVEs based on their inventory and customizing notifications for relevant vulnerabilities, organizations can stay informed about potential risks. Assigning a dedicated team or individual to manage CVEs and establishing a patch management process will ensure timely remediation efforts. Regularly reviewing and updating the inventory and list of relevant CVEs will help organizations adapt to changes in their systems and applications, maintaining a robust security posture in the face of emerging vulnerabilities.
Conclusion
In conclusion, a detailed understanding of CVE is essential for organizations looking to improve their cybersecurity process. CVE provides a standardized identifier system, allowing the industry to improve transparency and consistency in the management of potential security threats. With CVE, businesses can respond quickly and effectively to potential security incidents and limit the impact of those incidents on their systems. CWE complements CVE by tracking programming errors that lead to cybersecurity threats, providing developers valuable guidance on improving the security of their products. CVE and CWE, combined with industry-standard metrics like CVSS, provide businesses with the tools, information, and context to make informed investment decisions about potential cybersecurity solutions.








