Picus Launches Attack Surface Management and AI-driven Threat Profiling, Helping Organizations Minimize Threat Exposure
Today’s approach to risk management is similar to trying to assemble a puzzle with pieces from different sets. Security teams and organizations often only examine certain aspects of security in isolation - whether it is vulnerabilities, threat intelligence, asset inventory, or security validation data - and fail to connect the pieces together. Without a unified view, achieving relevant and significant risk prioritization is not possible.
That’s why we’ve built Picus Attack Surface Validation.
To effectively address critical vulnerabilities, misconfigurations, and security gaps, it's crucial that we blend an organization's unique context, its threat profile, with both attack surface and threat intelligence.
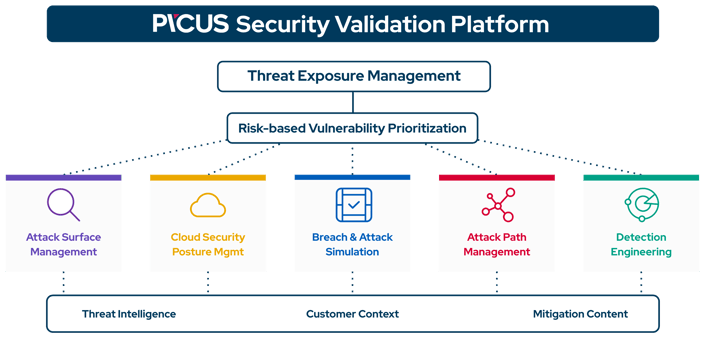
Introducing Attack Surface Validation
Attack Surface Validation (ASV) is a dedicated module for attack surface management, part of the Picus Security Validation Platform. ASV manages and automates the discovery, classification, and risk assessment of an organization's internal and external cyber assets. It aggregates and normalizes asset and vulnerability data from a diverse range of sources, enhancing visibility and supplying insights to prioritize the security of users, hosts, applications, and assets.
ASV helps customers looking to solve these use cases:
-
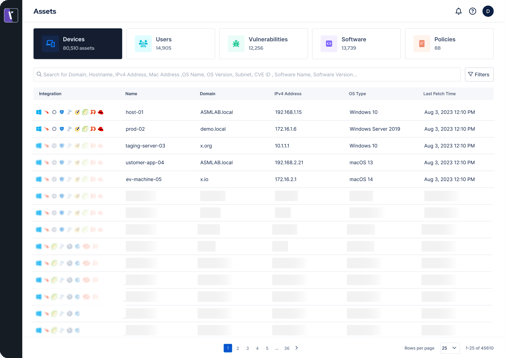
Obtain a unified view of asset inventory - Get all digital assets within a single view, including devices, users, software, policies, and vulnerabilities. We give you the confidence to evaluate your organization's attack surface accurately, spotting potential security gaps and make informed protective measures for digital assets and data.
-
Improve endpoint security hygiene - Identify and manage endpoint security agents that may be absent, non-operational, unregistered, or not complying with prescribed security policies.
-
Discover and prioritize vulnerabilities - Pinpoint vulnerabilities across all assets, including devices, software, users, and policies. Comprehensive visibility allows you to prioritize and respond to these issues in the most strategic, impactful manner for your organization.
How Does Attack Surface Validation Work?
ASV uncovers cyber assets and provides insights for better protection, reducing risk and improving your organization's overall security posture. Get continuous real-time monitoring, allowing you to keep pace with IT changes and new emerging threats. Consolidate, organize, and manage various asset types such as devices, users, vulnerabilities, and policies etc. within your organization with ASV’s asset library. Search with advanced filter options, including asset type, severity level, and data ranges, enables you to quickly and accurately locate assets.
Watch the 2-minute demo video to see the full benefits of Picus Attack Surface Validation
Integrations With Security and IT Tools
ASV integrates with the most popular and commonly used security and IT tools to provide a unified view of internal and external assets.
The Picus integration agent seamlessly connects to AVS with the following technologies:
-
Microsoft Active Directory - Track and understand asset user and device behavior, permissions and logging location to identify security risks.
-
Crowdstrike EDR - Easily see and map all your Crowdstrike endpoint agents and devices protected. Continuously and actively monitor changes with agents, devices, and registration status.
-
Tenable - Visualize vulnerabilities discovered across all assets, prioritize and respond to the most critical first.
ASV + Picus Security Validation Platform = Minimize Threat Exposure
It has become impossible to address all looming threats and patch all vulnerabilities and security gaps. To effectively minimize threat exposure and business risk, security teams have to put their focus on the issues with the biggest impact. Learn more in this blog how our newly launched AI-driven threat profiling capability helps you to identify the threats most relevant to you.
Combining consistent and accurate attack simulations, unified visibility of internal and external cyber assets, and AI-driven threat intelligence, the Picus platform now delivers an even more comprehensive view for organizations to effectively support a Continuous Threat Exposure Management (CTEM) program.
Picus Attack Surface Validation is available today. Schedule a demo to learn more or to get started!