Security Validation Platform
Quantify risk and consistently discover, validate and mitigate with real-world simulations.
Security Validation Powered
by Breach & Attack Simulation
Overcome the challenges of manual security assessments by consistently validating your security against the latest real-world threats with our security validation platform.
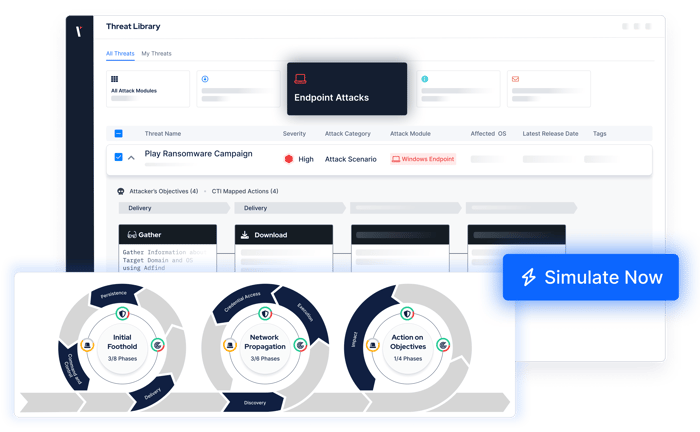
Simulate tactics and techniques across the cyber kill chain and address gaps swiftly and effectively with a cutting-edge BAS solution—no offensive security expertise required.
Mapping Picus Platform Products to
MITRE ATT&CK Tactics
Picus Platform empowers organizations to strengthen their defenses by comprehensively validating security controls against all tactics outlined in the MITRE ATT&CK® Framework. Picus products work in harmony to deliver unparalleled visibility into your organization’s security posture. Each product complements the others, enabling security teams to identify and remediate gaps across every stage of an attack lifecycle. Whether used individually or as an integrated suite, Picus products ensure that security controls across the stack are continuously optimized to counter evolving threats.
Picus Attack Surface Validation (ASV) |
Picus Security Control Validation (SCV) |
Picus Attack Path Validation (APV) |
Picus Cloud Security Validation (CSV) |
|||||||
Attack Surface Validation |
Endpoint Attacks |
Network Infiltration Attacks |
Web Application Attacks |
E-mail Infiltration Attacks (Phishing Attachment/
|
Data Exfiltration Attacks |
URL
|
Attack Path Validation |
Cloud Security Validation |
||
Vulnerability Exploitation |
Malware Download |
|||||||||
Reconnaissance |
✔ |
|||||||||
Resource Development |
✔ |
|||||||||
Initial Access |
✔ |
✔ |
✔ |
✔ |
✔ |
|||||
Execution |
✔ |
✔ |
✔ |
✔ |
||||||
Persistence |
✔ |
✔ |
✔ |
✔ |
||||||
Privilege Escalation |
✔ |
✔ |
✔ |
✔ |
||||||
Defense Evasion |
✔ |
✔ |
✔ |
✔ |
||||||
Credential Access |
✔ |
✔ |
✔ |
✔ |
||||||
Discovery |
✔ |
✔ |
✔ |
✔ |
✔ |
|||||
Lateral Movement |
✔ |
✔ |
✔ |
|||||||
Collection |
✔ |
✔ |
✔ |
|||||||
Command and Control |
✔ |
✔ |
✔ |
|||||||
Exfiltration |
✔ |
✔ |
✔ |
✔ |
||||||
Impact |
✔ |
✔ |
✔ |
|||||||
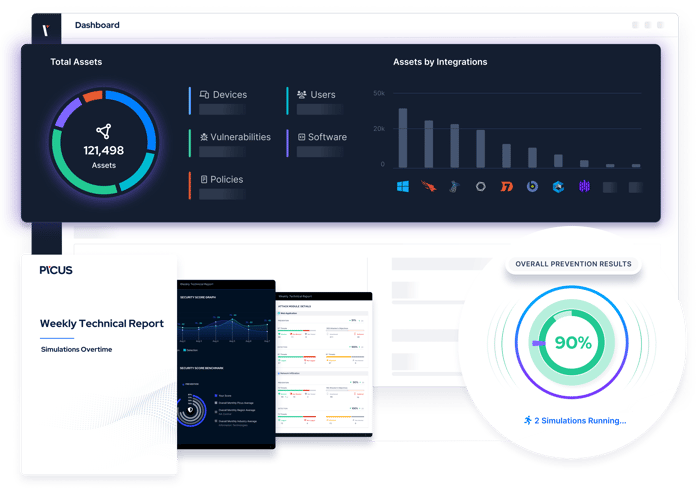
The Picus Security Validation Platform
Benefits of Security Validation
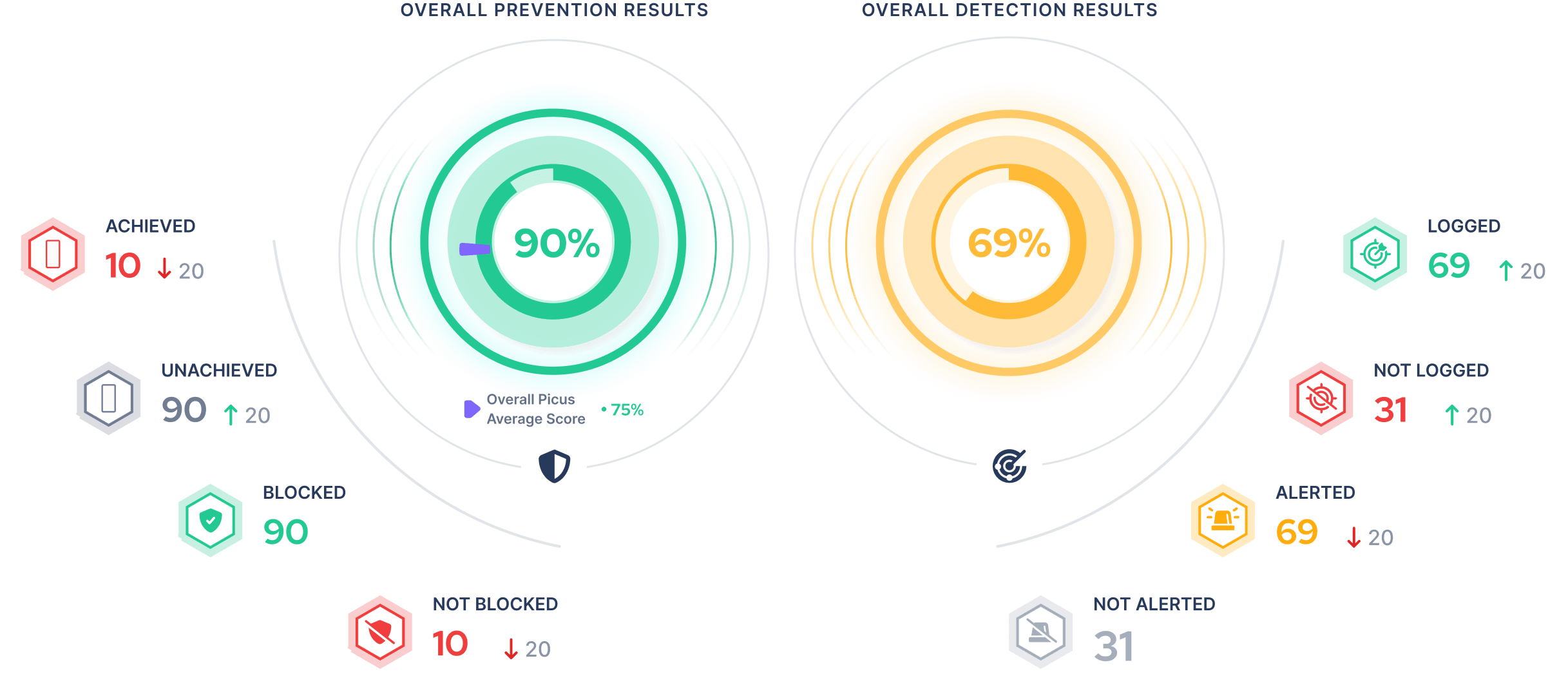
Consistently Discover, Validate, and Mitigate Exposures
Customer Stories
Best Choice for Attack Simulation
"With an expert support team, fully automated attacks, and detailed dashboards, the Picus platform is the best choice for breach and attack simulation."
Application Security and Vulnerability Management Manager, Financial Sector Organization
Companies should embrace automated continuous testing to protect against longstanding online threats.
Cybersecurity and Infrastructure Security Agency (CISA)

Quantify Your Cyber Risk
Get the insights you need to measure effectiveness, make critical decisions, and prove your security posture with automated security validation.
- Consistently assess your prevention and detection controls.
- Track security improvements in real-time.
- Share evidence with stakeholders.
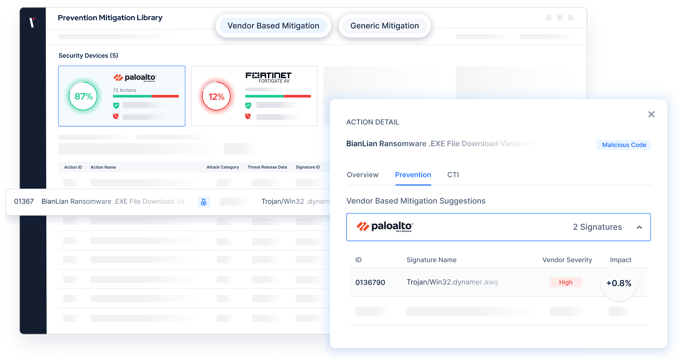
Reduce Threat Exposure
Get the visibility and context to focus on what matters most.
- Get broad and up-to-date visibility of your internal and external assets.
- Validate based on the latest cyber threat intelligence and vulnerabilities using automated BAS.
- Make prioritized security decisions.
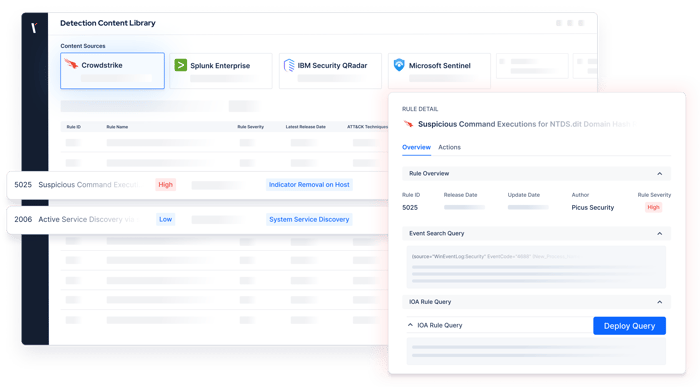
Maximize Impact with Actionable Insights
Identify security gaps, and address them swiftly and effectively.
- Quickly access mitigation suggestions to address policy gaps and misconfigurations.
- Use vendor-specific rules & signatures to optimize security controls.
- Get intelligent insights driven by AI.
Validate and Optimize Effectively
.png?width=680&height=395&name=AI%20smart%20assistant%20(5).png)
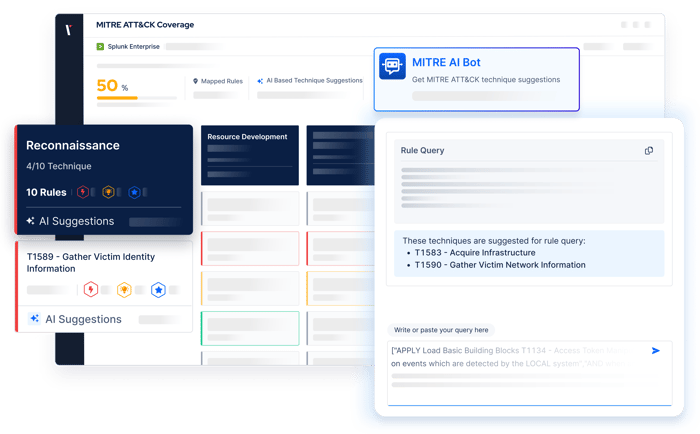
Keep Pace with The Latest Threats
Threats and TTPs
Simulated
Hours SLA for
Emerging
Threats
% Average Prevention
Score Increase in
3 Months
Validate Effectiveness Across Your Security Program
Validation
Enhance visibility of internal and external cyber assets and the security risks they pose.
Validation
Identify cloud misconfigurations and overly permissive identity and access management policies.
Validation
Measure and optimize the effectiveness of security controls with consistent and accurate attack simulations.
Validation
Eliminate high-risk attack paths that attackers could exploit to compromise users and assets.
Validation
.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.
Frequently Asked Questions
Security validation reduces cyber risk by verifying that an organization’s cyber security program is effective at defending its critical assets against the latest threats.
Without consistent validation, security teams can never be confident that security controls and processes are working as expected.
Due to the ever-changing threat landscape and IT infrastructure drift, security validation is a process that must be performed frequently.
Only by performing automated security validation can organizations obtain the insights they need to stay on top of their security posture and proactively identify and respond to risks sooner.
The Picus Security Validation Platform’s threat library is updated on a daily basis, ensuring security teams can simulate the latest threats. New emerging threats with actionable IOCs are added to the Picus Platform within 24 hours of disclosure.
The Picus Security Validation Platform is licensed as a yearly subscription, which includes access to its entire threat library and unlimited simulations. The platform is comprised of five individually licensed products that can be licensed based on the validation use cases most relevant to an organization.
The Picus platform is delivered as software-as-a-service (SaaS). In addition to the cloud-based deployment (available in multiple regions globally), it can also be deployed on-premises for organizations with strict regulatory requirements. For specific use cases, the Picus platform also supports fully air-gapped networks (environments w/o any connectivity to the outside world).
Yes. To meet the highest data protection and operational security standards, the Picus Platform is SOC 2 Type 2 compliant. Request a copy of our report here.
