Picus Breach and Attack Simulation
Simulate attacks to measure and optimize the performance of your security controls.
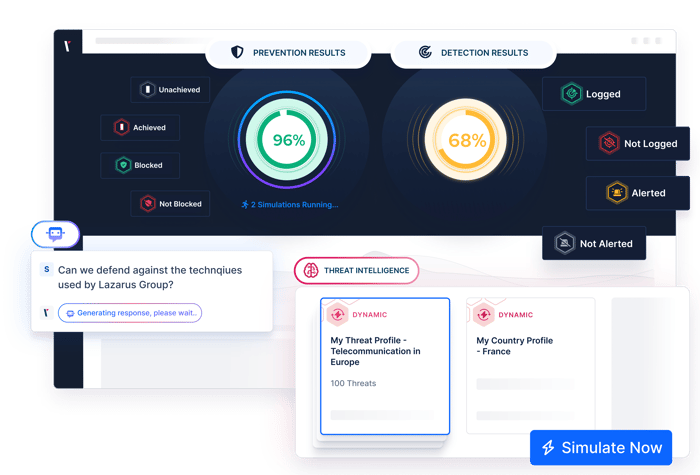
Breach and Attack Simulation for Cyber Resilience
Breach and Attack Simulation (BAS) is a continuous and automated method for testing your defenses by safely simulating and emulating real cyberattacks in a controlled environment. It uncovers blind spots, misconfigurations, policy gaps, and silent failures that traditional tools often miss.
Reasons to Validate Your Controls:
-
Configure settings to your environment
-
Improve efficacy over time
-
Reduce the risk of IT drift
BAS helps verify whether your security technologies are doing what they’re supposed to do. It shows if firewalls block malicious traffic, if EDRs detect threats, and if SIEMs generate timely alerts. It doesn't guess, it measures.
One of the most practical uses of BAS is validating security controls. This process, called Security Control Validation (SCV), focuses on confirming that your prevention and detection layers are working as intended. BAS powers SCV by running real attack scenarios and collecting measurable evidence of control effectiveness. That’s why the next section focuses exclusively on this critical use case.
Security Control Validation
Picus Breach and Attack Simulation validates security controls and strengthens defenses by stress-testing your implemented solutions to identify gaps that adversaries could exploit. The platform not only uncovers vulnerabilities across a variety of security measures but also provides both vendor-specific and neutral mitigation suggestions that are ready to implement. This eliminates the need for manual research and rule validation, saving time and effort.
Emerging Threats Testing
24-Hour SLA for Threats with Proof-of-Concept Exploitation, CISA Alerts, Active Threat Actor and APT Group Campaigns, and Ongoing Malware Campaigns.
Network Security Testing
Realistic Network Traffic for APT Groups, Ransomware Download Threats, Malware Loaders, Infostealers, Remote Access Tools (RATs), Trojans, Backdoors, and more.
Endpoint Security Testing
Ransomware & Malware Campaigns, Full Attack Killchain Coverage, APT & Threat Group Campaigns, Linux, macOS, and Windows Threats, DLL Side-Loading Attacks, Rootkits, Testing EDR, XDR, IDS, and AV Solutions.
Email
Gateway
Security
Malicious Links, Malicious Attachments, Executable Malicious Code, Rootkits, Cryptominer Threats, Botnets, Malware Droppers, and Loaders.
Data Loss Prevention (DLP) Testing
File Formats (e.g., PDF, XLS(X), DOC(X), and more), Country-Specific, PII, PCI, Critical OS Data, Source Code Exfiltration, and more.
URL
Filtering
Testing
Outbound HTTP Requests to Malicious URLs, Social Media URL Filtering, Dating & Travel Site URL Filtering, Malicious Command-and-Control, Malware, and Ransomware Site URL Testing.
Web App Firewall Security
OWASP Top 10 Attacks, XSS Evasion Attacks, XXE, SQL & PostgreSQL Injections, Command Injection, File Inclusion, Path Traversal, SSRF, CMS Attacks, HTTP Server Smuggling, Webshells, WAF Vendor Vulnerability Exploitation.
Micro Emulation Plans
Launch a ready-to-run micro-emulation plan for any MITRE ATT&CK technique you select.
Detection Analytics
Analyzes SIEM and EDR logs to identify gaps between expected and available events, pinpointing undetected, unlogged, and non-alerted attacks in real time.
BAS in Action: Validate, Detect, Mitigate
See how Picus BAS identifies security gaps, tests your defenses against real-world threats, and helps you quickly fix security vulnerabilities.
Benefits of BAS for Security Control Validation
Understanding Breach and Attack Simulation
Breach and attack simulation (BAS) is an automated and continuous method that allows organizations to simulate real-world cyberattacks in order to test and validate their security posture. It helps identify gaps in detection and response by safely emulating and simulating attacker behavior across networks, endpoints, and cloud environments.
Similar to other adversarial exposure validation tools , like automated penetration testing and red teaming, BAS tests enhance exposure management programs by reducing the number of exposures that need attention. This enables security teams to effectively prioritize the most critical risks. By factoring in the effectiveness of implemented compensating controls, BAS tools reveal the true business impact of cyber risks, streamlining remediation efforts and reducing the operational burden on security teams.
The objective of BAS tools is to deliver the most realistic exposure validation experience, and here is why: these solutions work by mimicking the tactics, techniques, and procedures used by real cybercriminals to validate identified exposures in the presence of an organization’s defensive measures (making no exceptions whatsoever). What does this mean? It means that BAS tools assess whether an exposure can actually be exploited by an adversary. In other words, BAS technologies provide data-driven insights into the feasibility of an exposure being exploited within an organization’s unique environment.
Thus, the reliability of the data output by BAS lies in its consideration of the effectiveness of an organization’s security measures. Let us explain this with a solid example.
Assume that your exposure assessment platform outputs a software vulnerability, say CVE-2024-38063, with a high CVSS score of 9.8 (critical). However, despite this possibly devastating score, the conditions necessary for a successful attack may not be present, or the NGFW implemented by the security team may block the attack at its initial stage. Consequently, the exposure doesn’t present as critical a risk as it might appear on paper (a.k.a theoretical, refer to Figure 1 below).
Therefore, BAS solutions validate the actual risk an exposure poses to business operations, helping security teams allocate remediation resources realistically to address the risks that truly matter.
An effective BAS solution with a high return on investment (ROI) should offer a diverse range of attack vectors, enabling organizations to emulate and simulate advanced adversarial behaviors observed in the wild, providing the most comprehensive and realistic adversarial exposure validation experience.
Expected attack vectors run by a BAS assessment include, but are not limited to:
-
Malware and ransomware download attacks
-
Atomic attacks (e.g., credential dumping scenarios)
-
Attack scenarios for APTs and threat groups
-
Data exfiltration attacks
-
Web application and email infiltration attacks
-
Vulnerability exploitation attacks
These attack vectors are expected to be continuously updated by analyzing commonly used attack patterns, emerging threat alerts, and active threat groups or malware campaigns that may target specific regions or sectors.
In addition, to enhance user convenience and deliver a smoother experience, BAS vendors can offer ready-to-run attack templates. These templates can be curated to include, for example, all emerging threats from the past year or highly impactful threats associated with recent exploitation activities, such as attacks by threat actors exploiting CVEs listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog.
In addition, by regularly encouraging users to simulate attacks from publicized and active threat groups, BAS creates an environment for continuous, proactive exposure validation. For example, by running simulations that mimic the advanced attack techniques of a specific threat group, such as Midnight Blizzard, organizations can validate exposures that might be exploited in a potential kill chain, examining them in a structured, chained manner.
BAS solutions play a crucial role in the exposure management lifecycle because they continuously and automatically validate cyber risks while factoring in the effectiveness of the organization’s implemented security controls.
These platforms test and validate the performance of security controls, including but not limited to:
-
Next-Generation Firewalls (NGFW)
-
Intrusion Detection Systems (IDS)
-
Intrusion Prevention Systems (IPS)
-
Anti-virus and Anti-malware Software
-
Endpoint Detection and Response (EDR)
-
Extended Detection and Response (XDR)
-
Data Leakage Prevention (DLP)
-
Security Information and Event Management (SIEM) solutions
-
Email Gateways
By simulating real-world attack scenarios, BAS platforms evaluate these controls' capabilities in detecting, preventing, and mitigating threats. They collect data on the progression of simulated attacks, offering insights into potential risks and identifying gaps in the organization's security posture.
BAS is an important adversarial exposure validation tool that enables organizations to proactively assess their security posture and identify exposures before they can be exploited by cybercriminals. By simulating real-world attack scenarios, BAS provides valuable insights into the effectiveness of security controls and highlights areas for improvement.
In the context of exposure management, BAS solutions enable organizations to:
-
Prioritize the most critical exposures within the unique context of the organization’s IT environment
-
Streamline remediation efforts by filtering out exposures that do not present any real risk (refer to Figure 1).
-
Minimize the likelihood of successful cyberattacks by staying ahead of sophisticated adversary behaviors
As the cyber threat landscape continues to evolve, BAS has become a crucial component of a comprehensive cybersecurity strategy, ensuring that organizations maintain a robust defense against potential breaches.
There are three main benefits of a BAS solution.
Continuous Validation of Cyber Risk Factoring Security Control Effectiveness
BAS solutions offer substantial advantages over traditional security practices such as manual penetration testing and red teaming. Traditional methods, while effective, are often constrained by the need for skilled professionals, limited scope, resource demands, and variability in outcomes. Additionally, they are typically conducted only once or twice a year due to high costs and potential disruption to organizational networks and resources. This limited frequency prevents them from effectively validating newly emerging exposures between engagements.
As attack surfaces continue to expand and become increasingly dynamic, the continuous assessments provided by BAS solutions are essential. BAS delivers automated, ongoing stress testing on an organization’s security controls against the latest and most sophisticated adversarial behaviors, offering a more adaptive and resilient approach to managing today’s complex security landscape.
Better Mobilization of Remediation Efforts with BAS
One of the benefits of BAS tools, as highlighted earlier, is their ability to reduce the sheer number of exposures, filtering them into a manageable set for the security team to address. Although Exposure Assessment Platforms (EAPs) can identify hundreds or even thousands of exposures, it is impractical for any security team, regardless of size, to tackle every single issue. Additionally, being required to address each identified exposure can significantly disrupt business operations, as patching and remediation efforts take time and can put operations on hold.
To address this, BAS solutions validate identified exposures to determine which ones are feasible for an adversary to exploit within an organization’s IT environment. This approach effectively bridges the prioritization gap left by legacy scoring systems like CVSS and EPSS. While these systems are useful for indicating the maximum potential impact of, for example, a CVE, adversarial exposure validation tools like BAS reveal the true impact of a specific exposure within the organization.
In other words, BAS helps security teams understand whether an attempted attack leveraging a particular CVE can be blocked immediately, partially, or, if not, at least logged and alerted as expected. This technique assesses the effectiveness of existing security defenses, sparing the team from addressing theoretical risks with no practical threat to the organization.
As a result, BAS provides a smaller, prioritized subset of exposures for remediation, enabling more efficient resource allocation.
Actionable Results and Mitigation Suggestion for Smooth Remediation
One of the most critical benefits of BAS solutions is the actionable, ready-to-apply mitigation suggestions they offer. BAS tools excel not only in validating which exposures need remediation but also in delivering mitigation recommendations that are researched and tailored for a variety of security control vendors.
This is essential because, in many cases, remediating vulnerabilities can take several days or weeks and may disrupt business operations. To address this challenge, BAS tools provide immediate mitigation suggestions that can be applied to security controls, giving security teams valuable time to fully remediate the exposure while minimizing disruptions.
BAS testing is designed to be safe and non-intrusive, allowing organizations to evaluate their security posture without compromising sensitive data or disrupting daily operations. These simulations are conducted in controlled environments, minimizing unintended consequences on other systems.
BAS solutions comply with regulatory frameworks and offer customizable testing parameters, enabling security professionals to tailor simulations to their specific environments and risk tolerance. Importantly, BAS does not require intrusive network scanning or firewall exceptions, ensuring that existing security infrastructures remain intact during testing. This approach provides a reliable and secure method for assessing and validating an organization's security controls.
When evaluating a BAS solution, you need to consider the following criteria.
Up-to-date Against Current and Emerging Threats:
An effective BAS solution must remain updated to address both current and emerging threats. As the cyber threat landscape continually evolves, the threat library in BAS should be consistently refreshed to keep pace with new techniques, vulnerabilities, and attack campaigns.
Threat Simulation Across the Full Attack Lifecycle:
An effective BAS solution should simulate a range of cyber threat techniques spanning the entire attack lifecycle. This includes:
-
Pre-Compromise Attacks: Email-based threats, malware downloads, vulnerability exploitations, and web application attacks.
-
Post-Compromise Attacks: Endpoint-specific attacks, data exfiltration, and lateral movement within the network.
-
Attack Campaigns: Scenarios based on malware tactics and campaigns led by known threat groups.
This approach enables a deeper understanding of potential adversary actions at each attack stage.
Pricing in Choosing the Right BAS Vendor
When evaluating BAS solutions, pricing varies significantly among vendors, influenced by factors such as features, deployment models, and organizational needs. For instance, some vendors offer comprehensive packages that reflect their extensive capabilities, while others provide more accessible entry points, making them cost-effective options for organizations seeking robust BAS functionalities. Therefore, organizations should assess their specific requirements and budget constraints to select a BAS solution that offers the best value for their investment.
Validation of Enterprise Security Controls:
Organizations deploy a wide range of security controls across diverse networks and locations. A robust BAS solution should thoroughly evaluate the entire security infrastructure and integrate smoothly with various prevention and detection technologies.
Continuous and Automated Simulation:
BAS delivers ongoing, automated cyber attack simulations to efficiently identify misconfigurations in security controls and monitor configuration changes. This process operates without manual intervention, consistently assessing the status of various security controls.
Threat Customization:
Every organization faces a unique cyber threat landscape, necessitating tailored threat prioritization. BAS should provide threat profiling to assist SOC teams in identifying and prioritizing relevant risks. Additionally, it should allow custom attack simulations and campaigns, enabling security teams to simulate their specific threat landscape and accurately assess their security posture.
Direct and Actionable Mitigation Insights:
Threat simulations reveal gaps in security controls, and a BAS solution should provide actionable mitigation guidance for these gaps, including emerging threats and zero-day vulnerabilities (when a public PoC is available). This empowers SOC teams to quickly craft tailored mitigation strategies.
Real-Time and Customized Reporting:
BAS solutions should generate assessment reports suitable for various stakeholders, including executives, SOC teams, and auditors. These reports should present real-time metrics, such as overall security score, detection rate, log collection, detection, and prevention.
Mapping to MITRE ATT&CK and Other Frameworks
A robust BAS solution should support industry frameworks like MITRE ATT&CK, mapping threat simulations to standardized methodologies. This alignment helps organizations identify security gaps, benchmark against industry best practices, and prioritize remediation based on the most relevant threats.
Ease of Use and Ease of Deployment
A BAS solution should be easy to deploy and use to ensure seamless integration with an organization's existing security infrastructure. The solution should have a user-friendly interface and provide clear instructions for deployment, configuration, and maintenance. Additionally, it should offer flexible deployment options, such as on-premises, cloud-based, or hybrid, to accommodate different organizational needs and network architectures. An easy-to-use and easy-to-deploy solution will encourage adoption and help organizations maximize the benefits of a BAS solution.
At Picus, we offer a cutting-edge Breach and Attack Simulation (BAS) solution designed to continuously assess and strengthen an organization's security posture. Leveraging our pioneering BAS technology, our Security Control Validation (SCV) module both simulates and emulates real-world cyber threats to evaluate the effectiveness of security controls, identify vulnerabilities, and provide both vendor neutral and specific actionable mitigation insights.
This proactive approach ensures that defenses remain robust and adaptable to evolving threats. Integrated with frameworks like MITRE ATT&CK, the platform delivers comprehensive threat coverage, while its intuitive interface and detailed reporting streamline the security validation process, making it both efficient and accessible.
What Does Gartner Say About Picus Security?
Gartner has recognized Picus Security as a 2024 Customers' Choice in the Breach and Attack Simulation Tools category. This prestigious distinction highlights Picus's dedication to delivering innovative and high-quality BAS solutions, tailored to meet the needs of organizations aiming to enhance their cybersecurity resilience.
Read all Gartner reviews about Picus Security's Breach and Attack Simulation solutions.
Why Security Controls Require Validation
Ever-evolving attacks and daily changes across IT environments mean that the configuration of security controls needs to be constantly reviewed and updated. Firewalls, SIEM, and EDR solutions are not ready to work out of the box and must be tuned regularly to perform effectively.
With security control validation, consistently identify policy gaps that impact the effectiveness of your controls and get action mitigations to reduce the time and effort it takes to optimize them.
Automated Validation Is Essential
While occasional penetration testing and red teaming assessments may provide some insights to help you test the effectiveness of your security controls, the pace of new threats means that a more proactive approach is needed.
Powered by Breach and Attack Simulation, the Picus Security Validation Platform simulates attacks automatically and consistently. Measure security control effectiveness at any moment and benefit from actionable insights to optimize your prevention and detection capabilities.
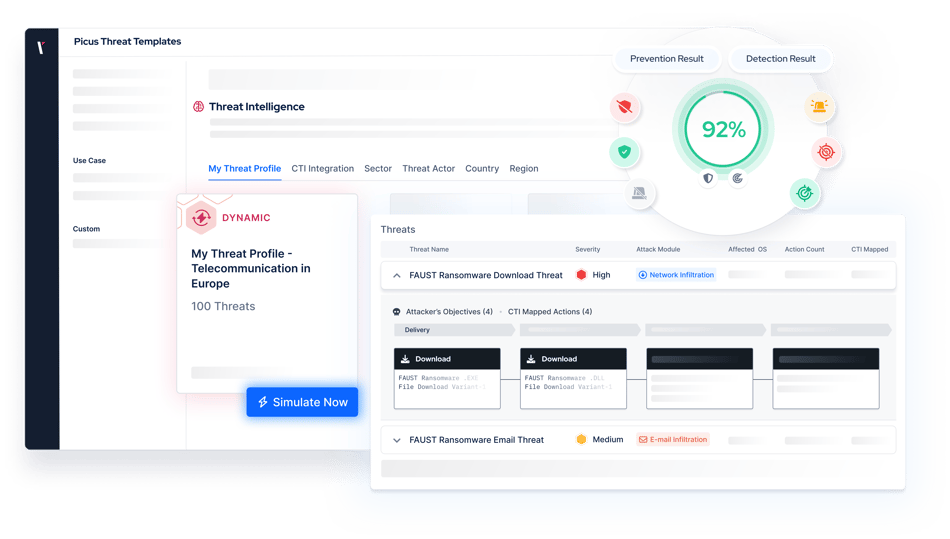
How Picus BAS Solution Helps You Validate Security Controls
Ensure that your controls remain effective with Breach and Attack Simulation.
By simulating thousands of threats and attack techniques, Picus provides assurance that your prevention and detection controls are working as you need them to.
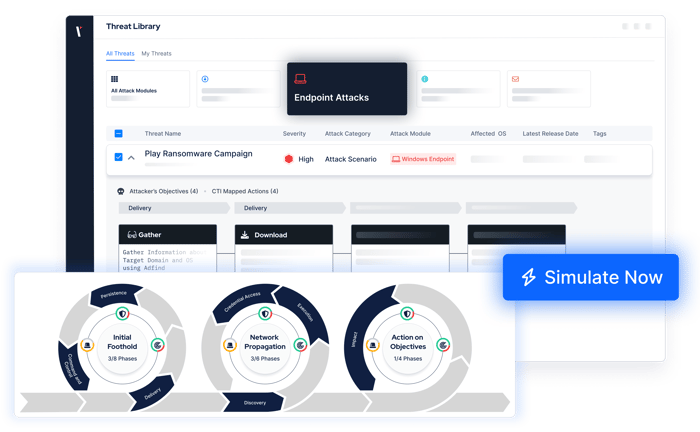
INTEGRATIONS
Unlock Your Security Stack’s Full Power
Picus seamlessly integrates with leading security solutions, including Microsoft, Palo Alto Networks, CrowdStrike, Splunk, AWS, Cisco, Check Point, IBM Security, SentinelOne, Fortinet, F5, Trend Micro, Trellix, Imperva, VMware Carbon Black, RSA, Securonix, and Exabeam.
With these integrations, Picus enables your team to:- Identify what your NGFWs, WAFs, EDRs, and SIEMs are missing
- Fine-tune controls using vendor-specific and agnostic mitigation guidance

Awarded By The Industry
Customer's Choice
2024 Gartner® Peer Insights™ Voice of the Customer for Breach and Attack Simulation
Cyber Security Excellence Awards
2024 Cybersecurity Excellence Awards – Most Innovative Cybersecurity Company
Customer Reviews
Picus is very good attack simulation tool in overall. It shows all security vulnerabilities and guides..
Sr. Information Security & Risk Officer
The implementation was very fast, the platform is easy to integrate and results quite intuitive to be analyzed.
CIO
It is easy to use and implement the product. It is a really useful tool to find out your security tool vulnerabilities..
Cyber Security Manage
A very successful platform where we can test the accuracy of our security investments and see their scores.
Manager, IT Security and Risk Management
Picus is one of the best BAS solution on the market today. The threat database it is constantly updated..
ICT Security Engineer
Picus completes the task it is required to do near perfect as a BAS solution. Threat database is up to date & updated frequently after a new malware or campaign, also the database is large..
Consultant Security Engineer
There is a very nice team from which I can get quick support. The application provides us with great convenience and confidence in our work.
Information Security Specialist
To test our systems with the real-time attack product is helping us to improve our security maturity. At the same time, the real time attacks are updating with the zero-day vulnerabilities..
Senior Vulnerability Management Engineer
With the help of this product we can perform continuosly endpoint attack via latest tactics and techniques which are used by threat actors..
Manager, IT Security and Risk Management
.. It is possible to customise the campaign or schedule the assessment periodically, to test protection measure implemented on network, endpoint and email.
ICT Security Engineer
Picus is such a great product for organizations that are looking to have constant checks and validation on their security posture in the organization.
Cybersecuirty Pre-sales Engineer.
Picus is a real safety measurement tool. Ever since we took Picus into our inventory, Security has helped significantly to increase our maturity level.
Cyber Defense Senior Specialist
It strengthened our security perspective and allowed us to follow trend attacks. We can test zeroday malicious threats very early because Picus could add them their attack database quickly.
Security Specialist
Other Use Cases
How the Picus Platform helps you address your cybersecurity challenges.
Automated Penetration
Testing
Stay on top of exposures while alleviating manual testing requirements.
Adversarial Exposure
Validation
Improve decision making with a holistic view of your security posture.
Latest Breach And Attack Simulation Resources









.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.
Frequently Asked Questions about Breach and Attack Simulation (BAS)
Breach and Attack Simulation (BAS) is an automated security testing method that safely emulates and simulates real-world cyberattacks to assess an organization’s defenses. It continuously replicates adversarial tactics, techniques, and procedures (TTPs), executing full attack kill chains to identify security gaps. BAS detects misconfigurations and inefficiencies in security controls, stress-testing them to evaluate their response to both known and emerging threats—without disrupting operations. It also provides vendor-specific and neutral mitigation strategies, including pre-tested prevention and detection signatures. This proactive approach strengthens security resilience and improves overall cyber defense strategies.
Yes, attack simulation is safe when performed using a reputable BAS tool. Unlike real cyberattacks, BAS solutions execute non-destructive simulations that do not compromise an organization’s systems or data. These tools operate in controlled environments, ensuring that attack scenarios do not disrupt business operations.
The level of safety depends on the tested environment and the BAS vendor’s approach. For example, some vendors conduct agentless simulations on WAF solutions, directly attacking the WAF. This increases the risk of denial-of-service conditions and can lead to unstable or inaccurate simulation results. In contrast, Picus BAS uses agent-based simulations on WAFs to ensure business continuity and provide more accurate assessments of WAF effectiveness.
BAS tools execute full attack kill chains safely within an organization’s IT environment, simulating adversaries across networks, endpoints, web applications, and email. They run diverse attack scenarios, including network infiltration, endpoint compromise, web exploitation, email attacks, data exfiltration, and URL filtering bypass. These scenarios use various attack vectors such as malware execution, ransomware downloads, atomic attacks (e.g., credential dumping, process injection, token theft), vulnerability exploitation, and APT simulations. By continuously testing security controls, BAS tools provide precise insights and mitigation strategies, helping organizations optimize defenses, improve detection and response, and proactively address vulnerabilities without disrupting operations.
Red teaming relies on human experts to simulate sophisticated adversaries, testing an organization’s ability to detect and respond to real-world attacks. While it provides valuable insights, red teaming is resource-intensive, costly, and offers only a point-in-time assessment, covering a limited scope within a short timeframe.
BAS, in contrast, delivers continuous, automated security validation. It systematically evaluates a broad range of security controls, ensuring defenses remain effective against evolving threats. BAS is more cost-effective and scalable, whereas red teaming requires specialized professionals and is conducted periodically. Ideally, both approaches should complement each other for comprehensive cybersecurity validation.
BAS and penetration testing (pentesting) both assess security defenses but differ in execution. BAS is automated and continuous, safely simulating real-world attacks to evaluate security effectiveness without impacting systems. Pentesting, on the other hand, is manual and periodic, performed by ethical hackers who actively identify and exploit system, network, and application vulnerabilities. Unlike BAS, pentesting is resource-intensive, puts significant stress on the network, and is not designed to be stealthy—its goal is to expose weaknesses through direct exploitation. While BAS provides ongoing validation, pentesting delivers deep, hands-on assessments. Both approaches complement each other for comprehensive security testing.
Traditional security assessments—such as red teaming, penetration testing, and vulnerability scanning—offer point-in-time evaluations that may quickly become outdated as threats evolve. These methods often require significant manual effort and only provide a snapshot of an organization’s security posture at a given moment.
BAS, in contrast, is automated and continuous, systematically testing security controls against the latest attack techniques. It provides ongoing validation, ensuring defenses remain effective against emerging threats. Unlike traditional assessments, BAS helps organizations detect gaps in real time and adapt their security posture proactively rather than reactively. Ideally, both approaches should be used together for comprehensive security assurance.
Vulnerability scanning detects and catalogs security weaknesses by comparing system configurations against known vulnerabilities, but it does not simulate real-world attacks or assess exploitability. It generates a static list of vulnerabilities with severity scores based on legacy metrics, often ignoring security controls already in place. For example, a scanner may flag a critical vulnerability without considering that a WAF or other defenses render it unexploitable, creating a false sense of urgency and adding unnecessary workload for security teams.
BAS, on the other hand, actively emulates adversary tactics, testing whether vulnerabilities can be exploited and whether security controls function as intended. Unlike vulnerability scanners, which lack business context, BAS provides actionable insights, real-time validation of security effectiveness, and continuous assessments. This approach gives organizations a more accurate understanding of real-world risks, ensuring security teams focus on threats that truly matter.
BAS tools evaluate security effectiveness by executing real-world attack scenarios and measuring how well security controls detect, prevent, and respond. Instead of theoretical assessments, BAS provides concrete prevention and detection scoring rates, highlighting where security solutions fail to react as intended. It identifies weaknesses across prevention, detection, and response layers, mapping results to frameworks like MITRE ATT&CK. Reports reveal attack success rates, prevention failures, and detection gaps, allowing teams to optimize configurations. Continuous testing helps security teams track progress, refine security controls, and apply vendor-specific mitigation strategies to strengthen defenses before actual threats exploit vulnerabilities.
Picus BAS enhances an organization’s security posture by continuously simulating real-world adversary tactics, techniques, and procedures (TTPs) to validate and optimize defensive controls. It executes comprehensive attack simulations, spanning network infiltration, endpoint compromise, web application exploitation, email infiltration, data exfiltration, and URL filtering bypass attempts. By testing security solutions—including but not limited to NGFWs, WAFs, IPS/IDS, XDR, EDR, EPP, AV, email/web gateways, DLP, and SIEM—Picus identifies misconfigurations, detection gaps, and ineffective controls. Leveraging an up-to-date threat library and MITRE ATT&CK mapping, it provides vendor-specific mitigation recommendations, enabling security teams to proactively strengthen defenses and reduce risk exposure.
BAS solutions are valuable for organizations of all sizes—from large enterprises to mid-sized companies with limited cybersecurity teams. For instance, enterprises, financial institutions, healthcare providers, and government agencies employ BAS to continuously validate their security controls across complex, dynamically changing IT environments. These organizations are frequently targeted by APT campaigns, making BAS an essential tool for providing data-driven visibility into the readiness of their defenses against emerging attacks.
Mid-sized organizations, which often face resource constraints, benefit significantly from BAS by automating attack simulations, reducing manual testing efforts, and identifying security gaps. Additionally, BAS offers vendor-specific mitigation recommendations, thereby easing the burden of routine security validation.
Organizations that handle sensitive data also leverage BAS to proactively test their defenses, strengthen security controls, and ensure compliance with regulations like GDPR, HIPAA, and PCI-DSS.
Yes. BAS tools are expected to integrate with a wide range of security solutions by interfacing with network security tools like NGFW, WAF, EG, and SWG to assess perimeter defenses and traffic filtering. They also collaborate with threat detection and intrusion monitoring systems such as IDS and IPS to ensure accurate identification and response to malicious activities. Additionally, they evaluate endpoint security tools—including EDR, XDR, AV, and EPP—to detect and contain threats, while integrating with SecOps platforms like SIEM and SOAR to validate that alerts, logs, and automated responses function as expected. Finally, they support data protection efforts alongside DLP and EASM solutions, providing comprehensive validation across security domains.
Implementing and managing a robust BAS program requires a strategic, multi-layered approach. Start by selecting a tool that simulates a comprehensive range of attack vectors—mirroring real-world adversary tactics across network, endpoint, application, and data layers—and maintains an up-to-date threat library for both known and emerging risks. Continuous, automated simulations should validate your preventive and detective security controls while also allowing for customized threat scenarios tailored to your organization’s unique environment. Effective programs provide actionable, vendor-based mitigation recommendations and real-time, customizable reporting that maps results to frameworks like MITRE ATT&CK. Finally, ensure the solution is easy to use and deploy, integrating seamlessly with existing security operations.
Yes, the Picus Platform supports on-premises, hybrid, and cloud environments.
Picus BAS (Security Control Validation - SCV) offers partial compatibility with cloud environments, depending on the deployment model. It effectively assesses security controls in Infrastructure-as-a-Service (IaaS) environments, where organizations utilize cloud-based infrastructure (e.g., virtual machines) from providers like AWS, Azure, or Google Cloud. SCV can simulate cloud-specific threats, such as misconfigured access controls, API exploitation, and data exfiltration, to evaluate security effectiveness.
For Platform-as-a-Service (PaaS) deployments, organizations should use Cloud Security Validation (CSV) instead of SCV.
Picus BAS simulates real-world cyber threats across network, endpoint, web application, email, data loss prevention (DLP), and URL filtering security to validate defenses.
For network security, it tests APT traffic, ransomware downloads, malware loaders, RATs, trojans, and backdoors. In endpoint security, it executes ransomware, DLL side-loading, rootkits, and APT group campaigns across Windows, Linux, and macOS, evaluating EDR, XDR, IDS, and AV solutions.
For web security, it targets OWASP Top 10 threats like XSS, SQLi, SSRF, and webshells, while email security tests malicious links, malware attachments, and botnets. DLP assessments focus on PII, PCI, and source code leaks, while URL filtering tests block phishing and malicious sites.
Picus BAS also includes emerging threats testing, integrating CISA alerts, APT campaigns, and MITRE ATT&CK-based micro emulations.
BAS tool pricing can be customized to meet an organization’s unique requirements, allowing for solutions that are tailored based on the features chosen. For instance, companies concentrating on ransomware preparedness may opt for a package specifically designed to evaluate their defenses against such threats. Similarly, enterprises aiming to strengthen endpoint security might add prevention and mitigation modules, or even extend their capabilities with detection analytics for SIEM or EDR systems. This adaptable pricing model ensures that organizations invest only in the features most relevant to their security priorities and operational needs, resulting in a scalable and efficient solution.

