MITRE ATT&CK® Framework Beginners Guide
| February 13, 2026
This guide is designed for you to get a comprehensive understanding of the MITRE ATT&CK Framework and explore how you can utilize it for your organization.
1. Introduction
The famous criminologist Edmond Locard's 'Every contact leaves a trace' principle also applies to cybercrime. As with any crime, adversaries leave traces behind during cyberattacks, and each trace is referred to as an Indicator of Compromise (IoC). An IoC is evidence that a cyberattack has taken place.
Indicators of Compromise give valuable information about what has happened, prepare defenders for future attacks, and help prevent, detect, and respond to similar attacks. However, there are various types of indicators that do not have the same importance, with some being much more valuable than others. Therefore, the differences between indicators have led to the need for a classification system.
A well-known IOC classification, The Pyramid of Pain, was introduced in 2013 by cybersecurity expert David J Bianco. Bianco illustrated the value of each indicator type in this pyramid. He named the pyramid 'The Pyramid of Pain' due to the fact that each level is proportional to the pain both security professionals and adversaries feel.
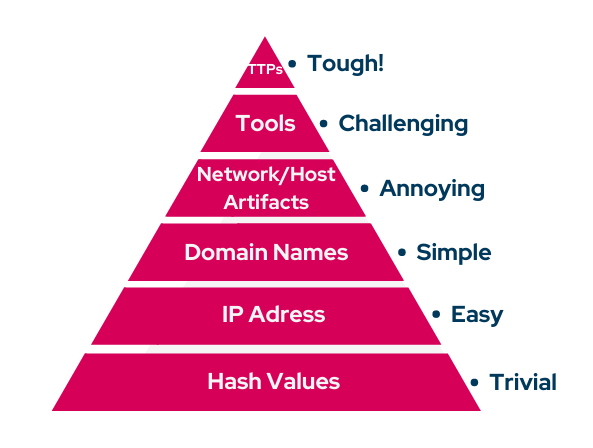
The Pyramid of Pain (David Bianco, 2013)
As we climb to the upper levels of the pyramid, it becomes increasingly difficult (painful) for security professionals to collect and apply indicators. However, it also becomes difficult for adversaries to replace them with new ones. For example, according to a security professional's point of view, it is easy to obtain and incorporate the hash values of malicious files into security controls, but it isn't easy to define and apply TTPs (Tactic, Technique, and Procedures) into security tools. From an adversary's perspective, changing the hash value of a malware file is very simple; however, it is challenging and costly to change TTPs. According to the defender's and adversary's perspectives, each indicator type is given in Appendix A.
Starting with the first antivirus software, we traditionally detect atomic IOCs, such as hash values, IP addresses, and domain names. However, we must also begin to detect adversary behavior, tactics, techniques, and procedures (TTPs), and tools used by adversaries. At least, we have to detect their artifacts in the network and hosts.
2. The MITRE ATT&CK Framework
The MITRE ATT&CK Framework systematically defines and organizes TTPs (tactics, techniques, and procedures). It is a globally accessible public knowledge base in accordance with real-world observations of adversary operations. It has become a common language between security teams to describe TTPs.
The other important aspect of MITRE ATT&CK is that it is a community-driven initiative; therefore, it is a compelling framework as the whole global security community can contribute to it.
- The ATT&CK Framework includes observed (known) adversary behavior, so it cannot be expected to consist of every adversary behavior.
2.1. ATT&CK Matrix for Enterprise
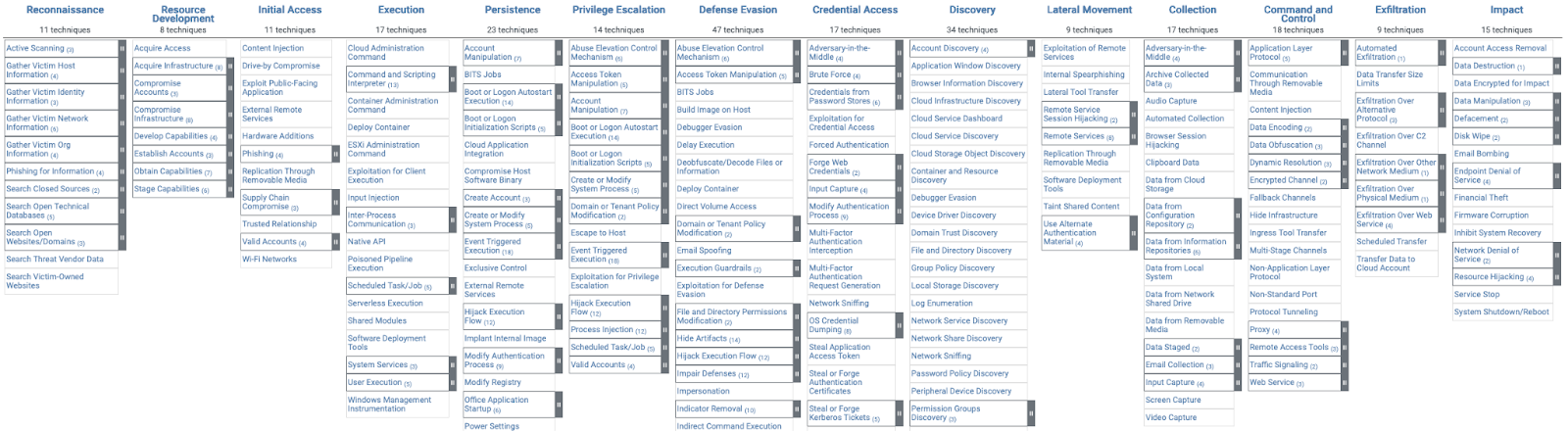
This is the MITRE ATT&CK Matrix for Enterprise. In this matrix, each column represents a tactic, the adversary's technical goals. To achieve these goals, in other words, tactics, adversaries use different methods, and these methods are called techniques. So, for example, for Initial Access, an attacker may send a spearphishing attachment or exploit a public-facing application, such as an Apache Server.
There are two other ATT&CK matrices: the Mobile and Industrial Control Systems (ICS) matrices.
MITRE ATT&CK is not static. For example, in the October 2025 v18 release, six new techniques and six new sub-techniques have been added to the Enterprise matrix, and 62 techniques and sub-techniques have been updated. So, the framework expands as new techniques and tactics are observed and existing (sub-)techniques are updated. In the latest release (v18), ATT&CK for Enterprise contains 14 tactics, 216 techniques, and 475 sub-techniques. MITRE ATT&CK also provides threat groups that are related to an intrusion activity and the software utilized by these threat groups. MITRE ATT&CK uses the term software to define malware, custom or commercial tools, open-source software, and OS utilities that adversaries use. Currently, ATT&CK includes 176 groups, 784 software, 55 campaigns, 44 mitigations, 691 detection strategies, 1739 analytics, and 106 Data Components.
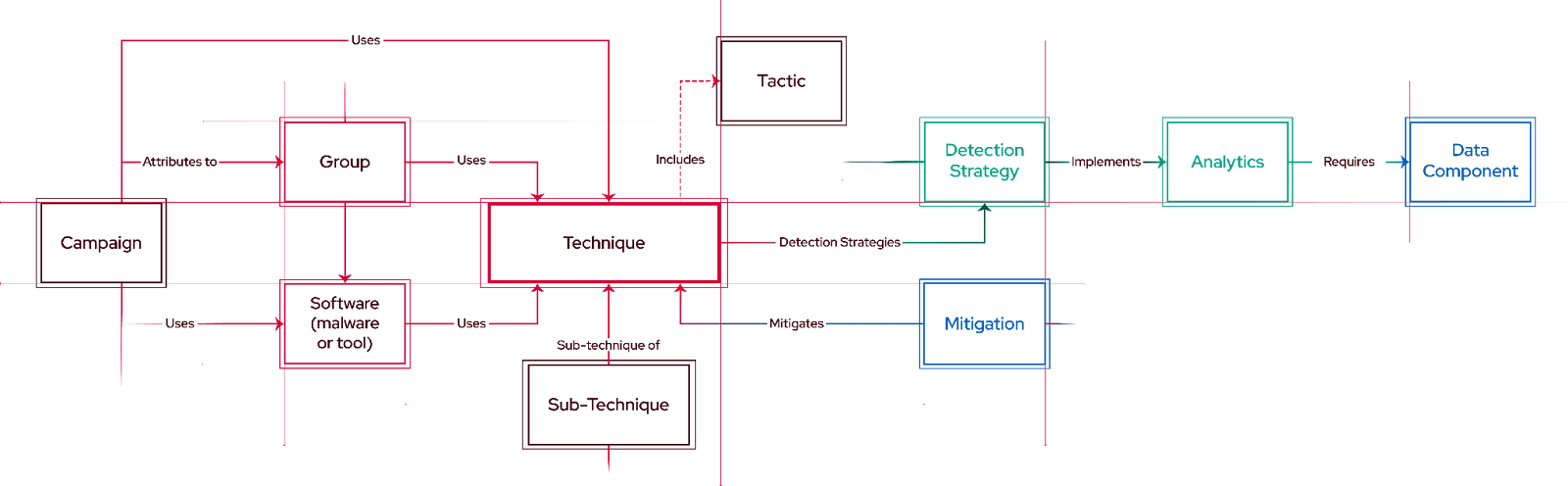
The above figure presents relationships between objects in the MITRE ATT&CK Framework. We explain these objects in the following sections.
2.2. Tactics
Tactics represent the "what" and "why" of an ATT&CK (sub-)technique and answer the following question: "What goals are adversaries trying to achieve?". So, they are the adversary's technical goals, the reason for performing an action, and what they are trying to achieve. For example, an adversary may want to achieve Credential Access in order to gain access to a target network. In addition, each tactic contains a list of techniques that have been observed being used in the wild by threat actors.
- The ATT&CK framework is not meant to be read in a linear fashion.
- An adversary does not have to progress through the tactics from left to right.
- An adversary does not have to employ all of the ATT&CK tactics.
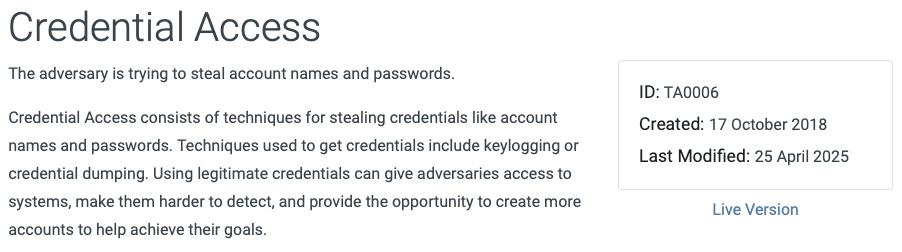
Each tactic has an ID. For example, the ID of the Credential Access tactic is TA0006. MITRE ATT&CK also provides a brief description of each tactic. The following table represents 14 tactics in the ATT&CK for Enterprise and their brief descriptions.
|
ID |
Tactic |
Goal (The adversary is trying to) |
|
TA0043 |
Reconnaissance |
Collect data to plan future malicious activities. |
|
TA0042 |
Resource Development |
Identify resources to support malicious operations |
|
TA0001 |
Initial Access |
Gain first access to your network |
|
TA0002 |
Execution |
Execute malicious code |
|
TA0003 |
Persistance |
Maintain their foothold |
|
TA0004 |
Privilege Escalation |
Get access to higher-level permissions |
|
TA0005 |
Defense Evasion |
Evade defenses to avoid being detected |
|
TA0006 |
Credential Access |
Acquire account names and passwords |
|
TA0007 |
Discovery |
Investigate your environment |
|
TA0008 |
Lateral Movement |
Move through your environment |
|
TA0009 |
Collection |
Collect data relevant to their goal |
|
TA0011 |
Command and Control |
Control compromised systems and communicate with them |
|
TA0010 |
Exfiltration |
Steal collected data |
|
TA0040 |
Impact |
Alter, corrupt, or destroy your systems and data |
- The MITRE ATT&CK for Mobile matrix includes 12 tactics similar to the Enterprise matrix, excluding "Reconnaissance" and "Resource Development" tactics.
- The MITRE ATT&CK for ICS (Industrial Control Systems) matrix consists of 12 tactics. It includes tactics of the Enterprise framework except "Reconnaissance", "Resource Development", "Credential Access", and "Exfiltration" tactics. But, the ICS matrix consists of "Inhibit Response Function" and "Impair Process Control" tactics in addition.
2.3. Techniques
Techniques describe "how" an adversary accomplishes a tactical goal through an action or a series of actions. For example, an attacker may utilize the OS Credential Dumping technique to achieve the Credential Access goal (tactic). So, a technique is a specific adversary behavior used to accomplish a goal.
- Adversaries use many techniques to achieve their overall mission.
- A technique can be used to achieve multiple goals. So, a technique can be categorized under multiple tactics. For example, the T1078 Valid Accounts technique is categorized under the following four tactics: Defense Evasion, Persistence, Privilege Escalation, and Initial Access.
MITRE ATT&CK provides the following information about each technique
- Metadata
- Description
- Sub-techniques
- Procedure examples
- Mitigations
- Detection Strategy
2.3.1. Metadata
This is the metadata section of the OS Credential Dumping technique, which includes:
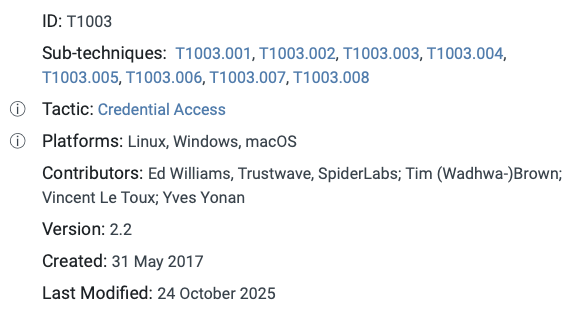
- ID: Unique identifier of the technique (T1003).
- Sub-techniques: IDs of sub-techniques of the technique. OS Credential Dumping technique includes eight sub-techniques identified by T1003.001, T1003.002, …, T1003.008. A sub-technique is a way to describe a specific implementation of a technique in more detail. Note that some techniques do not have sub-techniques, for example, the T1190 Exploit Public-Facing Application technique.
- Tactics: Name of the technique(s), in which the technique is categorized. For example, the tactic of the OS Credential Dumping technique is Credential Access, so adversaries use this technique to achieve Credential Access.
- Platforms: This part defines platforms affected by the technique. OS Credential Dumping affects Linux, Windows, and macOS. The MITRE ATT&CK Matrix for Enterprise includes the following platforms: Windows, macOS, Linux, ESXi, IaaS, SaaS, Identity Provider, Office Suite, Cloud (Azure, AWS, Google Cloud), Network Devices, and Containers.
Other metadata fields are Contributors (contributing persons or organizations), Version (the version number of the technique), Created(the first added date to ATT&CK), and Last Modified.
2.3.2. Description
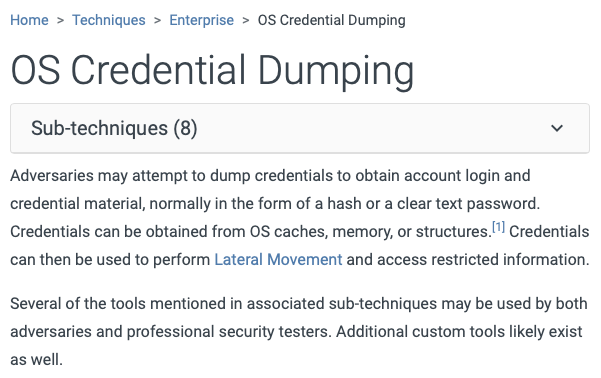
The first part of each technique or sub-technique provides a description. In some techniques, these definitions are written in great detail, while others are more concise.
2.3.3. Sub-techniques
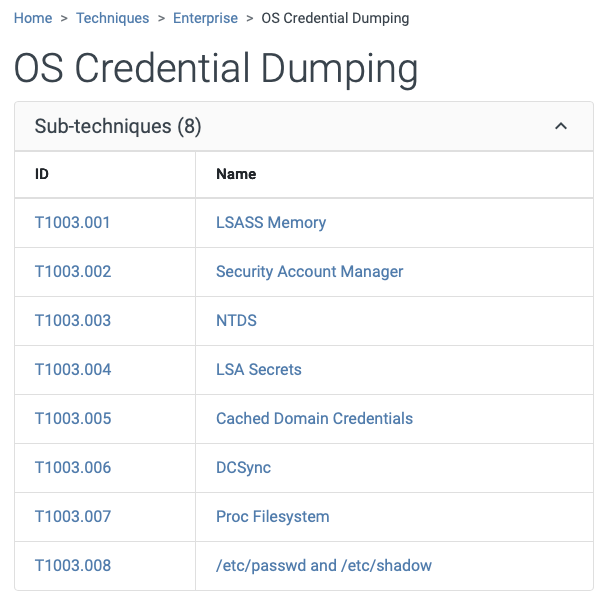
In this part, sub-techniques of the technique are listed. Of course, some techniques do not have sub-techniques.
2.3.4. Procedure Examples
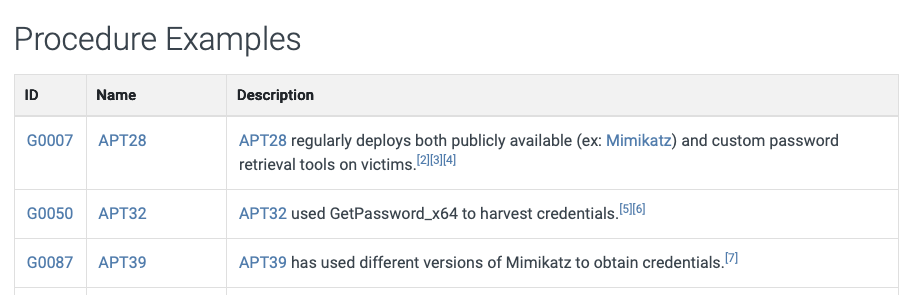
Procedures describe how a technique or sub-technique has been applied amidst specific adversary behavior. For example, "APT39 has used different versions of Mimikatz to obtain credentials." So, procedures define which threat actor implements the technique, how it applies, and what tool it uses. This information can be valuable for replicating an incident using adversary emulation, as well as specifics on how to detect that instance when it is in use. However, some procedure examples provided in the technique are too generic to define an adversary emulation practice.
2.3.5. Mitigations
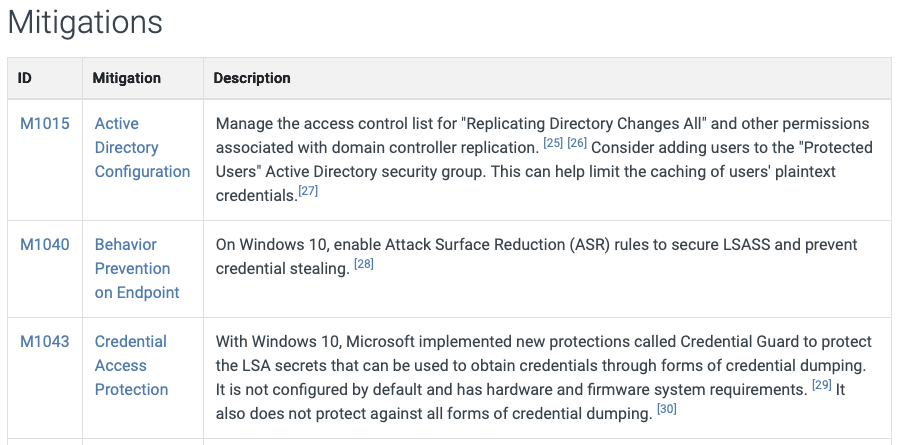
This section provides suggestions for common mitigations for the technique or sub-technique. As shown in the above image, some mitigation suggestions are very specific and easy to apply, but some are too generic. Currently, 44 different Mitigation measures are provided by MITRE ATT&CK for Enterprise.
2.3.6. Detection Strategy
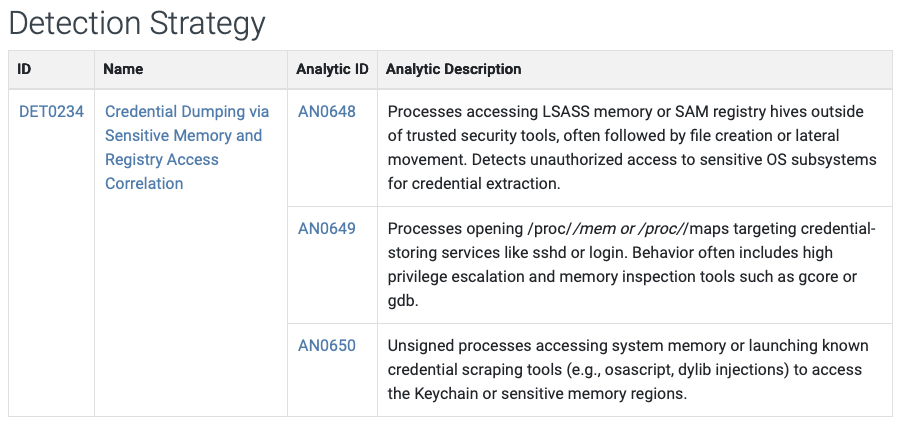
This part includes detection suggestions. Similar to mitigations, some detection suggestions are specific enough to develop detection rules, but some of them are too generic.
3. Groups
Groups are threat groups, activity groups, or threat actors related to an intrusion activity and are tracked by a common name in the security community. Currently, there are 176 groups in the MITRE ATT&CK Framework.
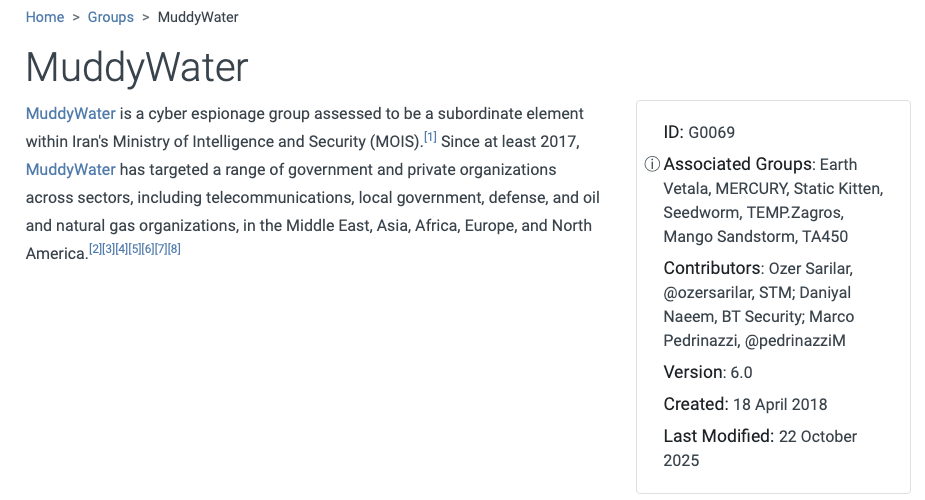
As seen in the screenshot, ATT&CK provides attribution of the group, targeted geographies, and targeted sectors. For example, the MuddyWater APT group is attributed to Iran, and it targets telecommunication, government, and oil companies in the Middle East, Europe, and North America.
Like other objects in the MITRE ATT&CK framework, each group has an ID. Moreover, ATT&CK also provides associated groups with the group, which are the same or very similar groups in threat intelligence reports.
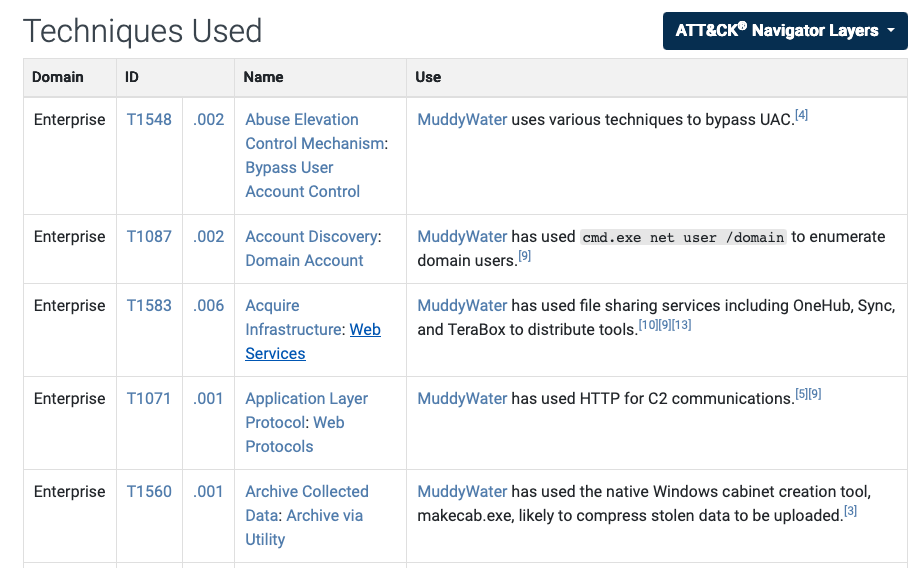
For each threat group, MITRE ATT&CK includes techniques used by the group and briefly describes how the group used these techniques. Furthermore, ATT&CK visualizes the techniques used by the group on the ATT&CK Navigator, as seen in the image below.
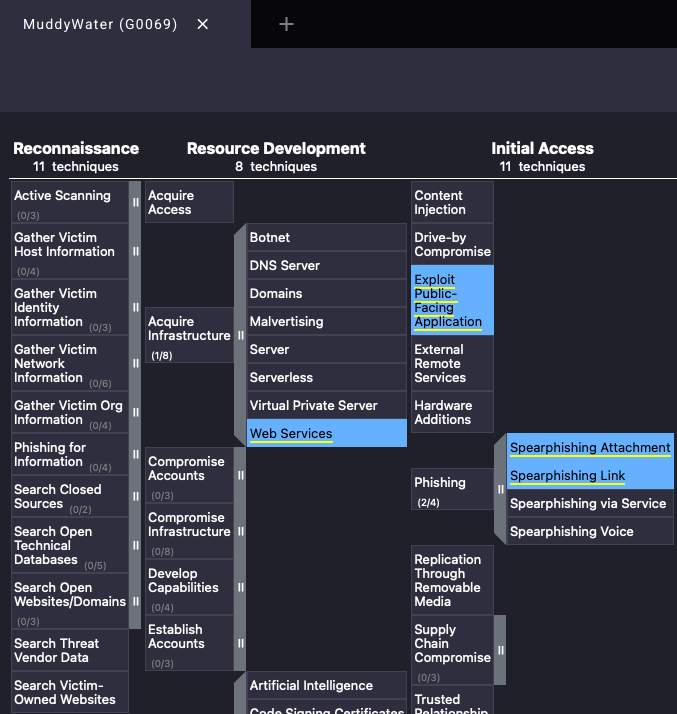
Aside from the ATT&CK techniques used by a threat group, the framework provides a list of Software used by the threat group, as shown in the image below. The software list for each threat group also includes the ATT&CK techniques used by the group.
4. Software
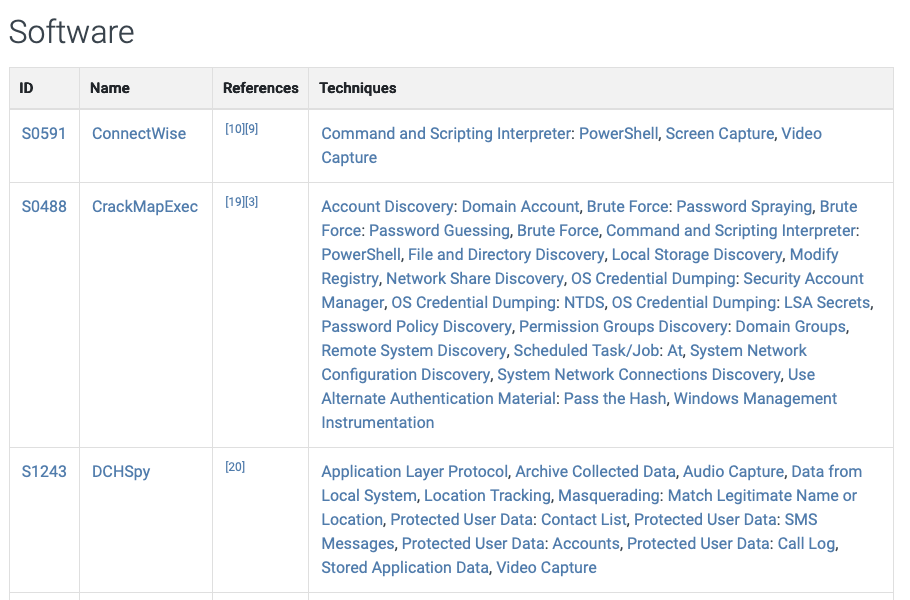
Software is categorized into malware and tools in the MITRE ATT&CK framework.
- Malware: Commercial, custom closed-source, or open-source software that is intended to be used for malicious purposes by adversaries falls under the malware category.
- Tools: Commercial, open-source, built-in, or publicly available software that could be utilized by a defender, penetration tester, red teamer, or attacker is included in the tools category. Tools can be software that isn't typically found on an enterprise system, such as Mimikatz, Metasploit, and Empire. Moreover, tools can be commonly available as part of an operating system or can be already installed on a system, such as certutil, netstat, and bitsadmin, which are also referred to as "living-of-the-land" tools. Emerging threat actors, such as the DarkSide ransomware group, heavily use these publicly available and living-of-the land tools.
5. Campaigns
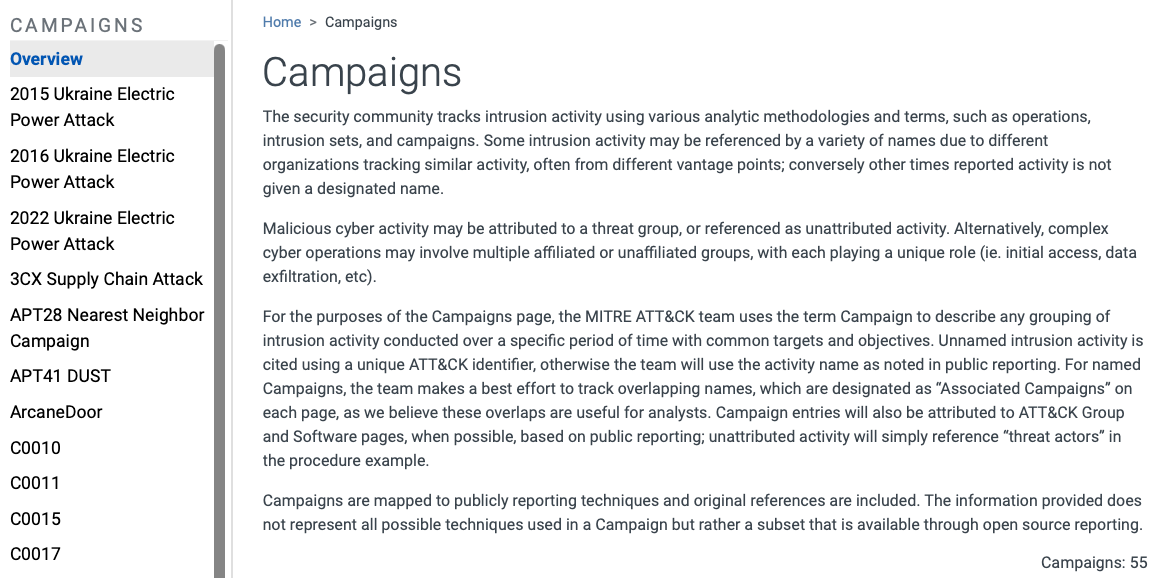
Campaigns in the MITRE ATT&CK Framework refer to specific operations or series of activities conducted by threat groups, often targeting particular organizations, sectors, or geographies. These campaigns are typically tracked by a common name or label and can span over time, showing how a group operates in different attack scenarios. As of now, there are 55 campaigns identified within the MITRE ATT&CK Framework.
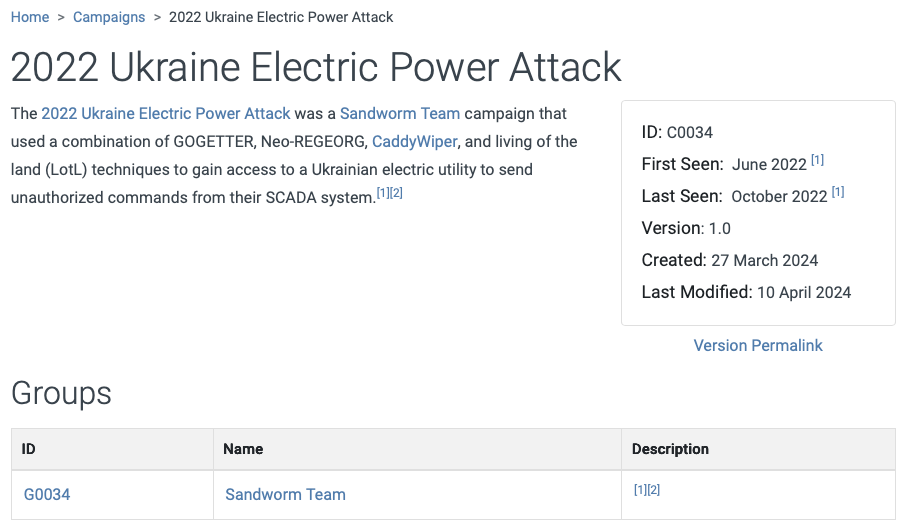
As shown in the screenshot, ATT&CK provides details about the campaign, including its associated threat group, targeted industries, and geographical focus. For example, the campaign "2022 Ukraine Electric Power Attack" is attributed to the Sandworm Team group, targeting the energy sector in Ukraine, and specifically aiming at critical infrastructure organizations. Each campaign in ATT&CK has its unique ID, providing the ability to track and link the campaign to related threat groups, techniques, and software used. This allows for a better understanding of how campaigns evolve over time and their associated tactics.
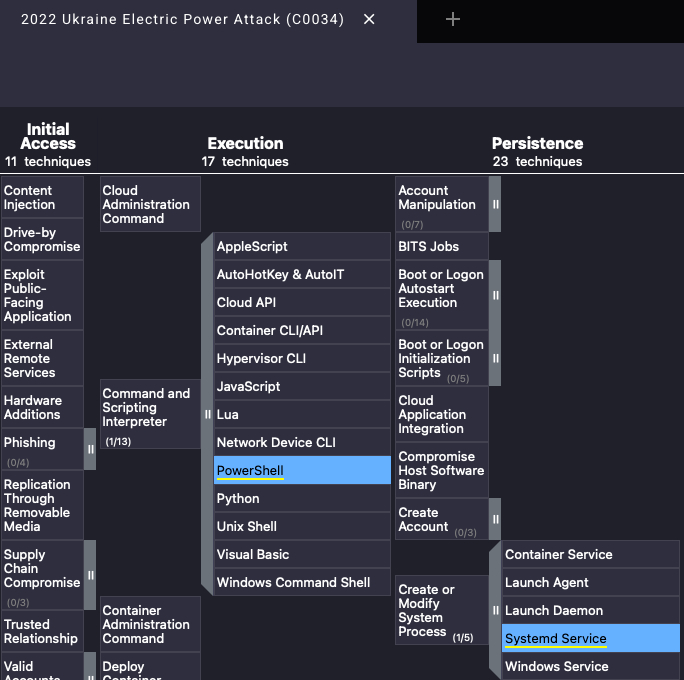
MITRE ATT&CK also includes detailed information on the techniques used during each campaign. For example, a campaign may use a combination of initial access methods like phishing or exploitation of public-facing applications. This data is visualized using the ATT&CK Navigator, where users can see the timeline and overlap of techniques used within the campaign. In addition to techniques, ATT&CK lists the software used by threat groups within specific campaigns, offering insight into the tools leveraged in the attack. The software section also links back to the techniques associated with it, providing a deeper understanding of how specific tools align with a threat group's tactics and objectives.
6. Operationalizing MITRE ATT&CK
The MITRE ATT&CK framework has become a common language between security teams. For example, threat Intelligence teams use MITRE ATT&CK to investigate techniques used by adversaries, red teams can use it for adversary emulation and security validation, blue teams utilize it to improve detection, and purple teams use MITRE for assessment and mitigation.
However, operationalizing MITRE ATT&CK requires skilled CTI, red, blue, and purple teams, as well as strong cooperation between these teams. To learn how to operationalize the MITRE ATT&CK framework, please enroll in our free "Operationalizing MITRE ATT&CK for SOCs" course in Purple Academy.
APPENDIX A - Type of Indicators
The following table describes each indicator type according to the defender's and adversary's perspectives.
|
Indicator Type |
Defender's Perspective |
Adversary's Perspective |
|
Hash Values |
Reliable indicators because the likelihood of two separate files having the same hash value is negligible. SHA 256, SHA1, or other hash algorithms can be used to provide unique references to individual samples of malware involved in an intrusion. |
It is straightforward to change the hash value of a malicious file; for example, adding a null byte to the end will yield a different hash value. So, it is worthless to track hash values as there are so many of them, and adversaries can easily change them. |
|
IP Addresses |
IP addresses used by adversaries are fundamental indicators. For most cyberattacks, adversaries need to connect to the target network, which requires an IP address. |
Adversaries can change IP addresses very quickly and frequently by utilizing anonymous proxy services, the Tor network, botnets, and proxy chains. |
|
Domain Names |
Domain names used by Command and Control (C2) servers are helpful indicators to detect malicious activities within the network of an organization. |
It is trivial to change domain addresses by utilizing DNS providers with lax registration requirements and dynamic DNS providers. Moreover, adversaries use domain generation algorithms (DGA) to generate many potential domain names for a malicious server, making it difficult to identify them. |
|
Network / Host Artifacts |
Network artifacts are pieces of the network activity that can help differentiate malicious network connections from legitimate ones. URI patterns, header values, and specific user-agent values are examples of network artifacts. Host artifacts are observables created by adversary behavior on target hosts, such as registry keys, dropped files, created directories, and services. |
When network or host artifacts of a cyberattack are identified, the adversary must go back to the weaponization phase of the cyber kill chain and change the configuration of their tools and recompile them. |
|
Tools |
Tools are software used by adversaries for malicious activities, such as Mimikatz credential dumper, Cobalt Strike, Empire, or other host-based utilities used by adversaries. |
If a tool used in cyberattacks was identified, the adversary must go back to the weaponization phase of the cyber kill chain and find or create a new tool. A new tool requires research and development effort. |
|
TTPs (Tactics, Techniques, and Procedures) |
TTPs are the most valuable indicators. TTPs reflect adversary behavior in all stages of a cyberattack, from reconnaissance through data exfiltration, e.g., dumping credentials from the LSASS memory. However, TTPs are also difficult to model and apply to security controls. |
When a TTP is identified, adversaries must find and implement a new behavior, which is the most time-consuming activity. Identifying, detecting, and responding to a TTP forces adversaries to change their behavior, requiring significant time and monetary investment. |




.png?width=353&height=200&name=rr25-Blog-7-data-from-local-system%20(1).png)

.png?width=353&height=200&name=rr25-Blog-5-Impair-Defenses-11%20(1).png)


