The Ransomware Attack Lifecycle from the Defender’s Perspective
Defense against ransomware attacks is challenging yet possible if you understand the attacker’s mindset and implement a threat-centric defense approach.
The previous blogs on our ransomware blog series explained:
- the recent ransomware trends,
- the MITRE ATT&CK T1486 Data Encrypted for Impact technique and
- the MITRE ATT&CK T1490 Inhibit System Recovery technique,as the most prevalent ATT&CK techniques used in ransomware campaigns.
This blog post describes the ransomware attack lifecycle from the defender's perspective. We examined dozens of ransomware attacks, such as Kronos, Colonial Pipeline, and Kaseya ransomware attacks, and other attack campaigns of ransomware threat actors, such as Conti, DarkSide, REvil, and Ryuk, to develop this model.
Although ransomware threat actors constantly embrace new attack techniques, their attack lifecycle from the defender's perspective does not change often. If we can model the ransomware attack lifecycle, we can accurately identify possible defensive actions.
In the following blogs of these ransomware attack series, we will explain how to prevent and detect ransomware attacks in each phase.
Test your readiness against ransomware attacks now
Challenges in Ransomware Prevention and Detection
Let’s start with identifying the challenges in preventing and detecting ransomware attacks.
1. The first challenge is keeping up with the ever-changing ransomware threat landscape. Ransomware attacks are constantly changing and evolving. It frequently incorporates new vulnerabilities to exploit, new attack methods to utilize, and new defense evasion techniques to bypass prevention and detection by security controls. Security professionals need to keep up with these changes and stay up-to-date against these new threats so that they can defend their organizations.
2. The second challenge is the rising Ransomware-as-a-Service (RaaS) business model. RaaS enables threat actors with less technical skills to run ransomware campaigns to various targets. Ransomware Threat actors are not necessarily technically proficient like Advanced Persistent Threat groups anymore. As a result, the number of attackers increases significantly.
3. Another challenge is the changing work culture worldwide, shifting towards Work from Home and Bring-Your-Own-Device (BYOD) practices. These changes effectively create a larger attack surface for organizations and new challenges for security professionals that might require non-traditional defensive approaches.
4. The last challenge we want to mention in this blog is low user awareness. User awareness is critical because ransomware groups use various tactics to trick users for an initial foothold to the target network. Whether they are an employee, business partner, or customer, users should be aware of the new techniques of ransomware threat actors.
Ransomware Attack Lifecycle from the Defender’s Perspective
How can we overcome these challenges? How should we detect and prevent ransomware attacks? In order to answer these questions, we built a four-phase approach from the defender's perspective.
Tactics and techniques used by ransomware operators might change over time. However, the overall ransomware attack lifecycle remains relatively the same from the defender's perspective. The ransomware attack lifecycle can be divided into four phases:
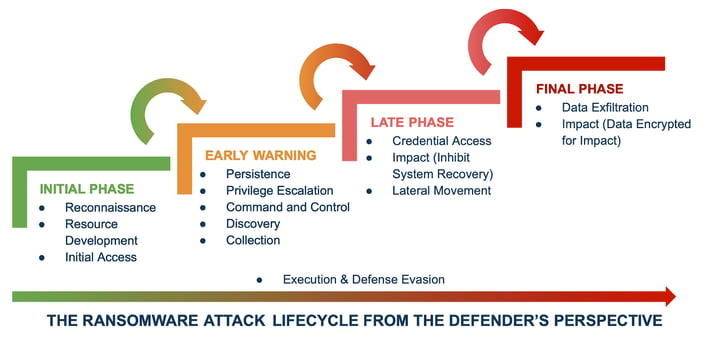
Phase 1 - Initial Phase
The first phase is the Initial Phase, where ransomware threat actors gather information on their target and gain access to the target network. This phase corresponds to Reconnaissance, Resource Development, Initial Access tactics of the MITRE ATT&CK framework.
One of the most used techniques in the Initial Phase is the MITRE ATT&CK T1190 Exploit Public Facing Application technique. Ransomware groups exploit vulnerabilities found in Internet-facing applications or devices to access the target network. These applications may be a web server, mail server, VPN server, monitoring software, or other Internet-facing utilities such as Windows Print Spooler.
Adversaries also trick users in the target system into executing their ransomware, as in the MITRE ATT&CK T1566 Phishing technique. According to ZDNet, threat actors used phishing emails in 42% of ransomware attack campaigns for initial access to their target system.
Spearphishing Attachment is a sub-technique of Phishing, which utilizes a malicious file attached to the email. Another sub-technique is Spearphishing Link. This sub-technique uses links to download malware contained in emails rather than attaching malicious files to the email itself to bypass email security controls.
Numerous file types, including Microsoft Office documents, PDFs, archived data, disk images, and executables, are utilized in spearphishing link/attachment emails. When the attachment or linked file is opened and potential defenses are bypassed, the adversary's payload exploits a vulnerability or operates directly on the user's system.
In the next blog, we will explain the prevention and detection of ransomware attacks in the Initial Phase.
Phase 2 - Early Warning Phase
After getting initial access, ransomware operators move to the Early Warning phase, where they establish persistence, discover the system, gather sensitive data, and improve their capabilities in the target’s network. Ransomware threat actors generally use MITRE ATT&CK techniques under the Persistence, Privilege Escalation, Command and Control, Discovery, and Collection tactics at this phase.
In this phase, ransomware threat actors gather detailed information about their target and adapt their attack methodology accordingly. They also try to gain higher-level permissions on their target if they get initial access to the target system with an unprivileged account. Moreover, adversaries collect data relevant to their goals in this phase. The next objective following data collection is often to exfiltrate the data in the following phases. If the ransomware utilizes multi-stage payloads to evade defenses as in the recent attack campaigns, adversaries may transfer additional payloads from an external system in this phase.
Techniques used in the Early Warning phase usually abuse built-in system utilities and may appear as legitimate actions in the log data. Therefore, preventing and detecting these techniques require proper log collection and validation for reducing false-positive alerts.
Phase 3 - Late Phase
In the Late Phase, ransomware operators disable the defense and recovery capabilities of the victim. Credential Access, Impact, and Lateral Movement tactics are commonly used to prepare the victim for the full impact of the ransomware.
Adversaries use the techniques in the Credential Access tactic to steal credentials such as account names and passwords. Then, they use valid credentials to access applications and sensitive information and move other systems. Credential dumping, brute force attacks, keylogging, and stealing Kerberos tickets are techniques used for credential access.
Adversaries use the techniques in the Impact tactic to damage or interrupt the target system and block their operational capabilities. Denial of Service attacks, Disk Wiping, and Data Encrypted for Impact are some of the widely used techniques classified under the Impact tactic of the MITRE ATTACK framework. In the Late Phase of the ransomware attack lifecycle, adversaries use the Inhibit System Recovery technique to damage the recovery capabilities of the victim so that the victim cannot restore its system to health and has to pay the ransom. Although it is not the ultimate goal of ransomware attacks, this technique dramatically improves the attack's impact.
In the Late Phase, the Lateral Movement tactic covers techniques used by adversaries to gain access to and control remote systems on a network. A ransomware attack lifecycle frequently involves pivoting through multiple systems. Many ransomware attacks have been recorded in recent months in which malware infects a host and then laterally moves to other hosts and internal servers, compromising the entire organization. Adversaries may choose to utilize their own remote access tools for Lateral Movement or use valid credentials with native network and operating system tools, which may be more stealthy.
Phase 4 - Final Phase
At last, in the Final Phase, ransomware performs its primary objectives. The ultimate purpose of the ransomware threat actors is to extort money from the victim by blocking the victim's access to its resources. To that end, in nearly all ransomware attacks, adversaries encrypt files in the target system. Then, ransomware threat actors demand money from the victim for the encryption key. Widespread use of data encryption makes Data Encrypted for Impact the signature ransomware technique. According to the Red Report, Data Encrypted for Impact was the third most used adversary technique in 2021.
However, widespread ransomware attacks caused organizations to invest in better backup solutions for their systems to avoid the harmful effects of the ransom and the ransom payment. As a result, ransomware threat actors added data exfiltration techniques to their arsenal to extort victims for ransom over stolen confidential data. Recent ransomware trends show that a large percentage of ransomware attacks also steal confidential data before encryption. So, Impact and Exfiltration are frequently used tactics in the Final Phase.
In addition to the MITRE ATTACK techniques used in the early and late phases of the ransomware attack lifecycle, there are techniques under Execution and Defense Evasion tactics used by attackers in all phases. Therefore, we didn't place these two tactics under any specific phase.
Conclusion
In this blog, "The Ransomware Attack Lifecycle from the Defender's Perspective", which is developed by Picus, is explained. This attack lifecycle consists of four phases, the Initial Phase, Early Warning Phase, Late Phase, and Final Phase.
We recommend that the necessary mechanisms be established to detect ransomware at all of these four phases and, if possible, to prevent it. Because as ransomware attacks became more sophisticated, the security measures that we would only take at a specific phase became inadequate. For example, measures to prevent ransomware from simply infecting the system or encrypting data are no longer sufficient due to the ever-evolving defense evasion techniques of ransomware and other malware attacks. Note that, even in the final phase, it is possible to prevent and limit the impact of ransomware attacks with proper mechanisms.
In the next blogs, we will explain how to detect and prevent ransomware attacks in each phase of the attack lifecycle with real-world attacks used by ransomware threat actors and detection rules utilized by detection engineers.
Get your certificate now: Ransomware Attacks: Basics, TTPs, and Countermeasures Course








