Picus Threat Library Is Updated for Jester Stealer Trojan Malware
Picus Labs has updated the Picus Threat Library with new attack simulations for Jester Stealer malware of the Jester threat group.
Jester Cyber Threat Group
Jester is a Russian-speaking emerging threat group that adopted the Malware-as-a-Service (MaaS) business model. Jester provides various malware such as botnet, stealer, clipper, and miner malware to cyber threat actors for a price. They also train and recruit new members to their group with paid courses. The threat group was first observed in July 2021, and they are constantly trying to expand their operations.
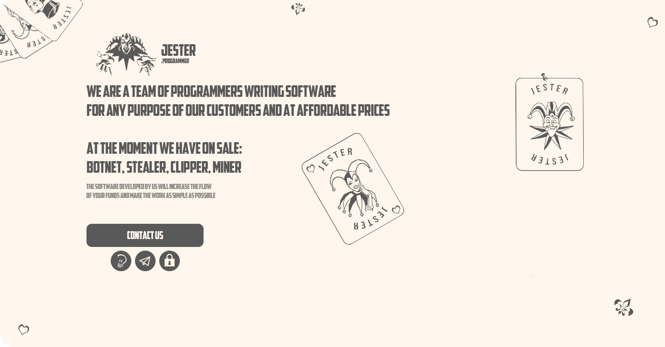
Figure 1: Jester Stealer Advertisement
Jester Stealer malware was recently discovered by Cyberint, and the malware is attributed to Jester [1].
Test your security controls against malware
What is the Jester Stealer Trojan?
Jester Stealer is a Trojan that gathers information from its victims. It mainly focuses on stealing credit cards and cryptocurrency wallets; however, data theft extends to personal information such as emails, passwords, FTP clients, and messengers apps like Telegram, Discord, and WhatsApp.
It is the flagship product of Jester threat group, and its business model is Malware-as-a-Service (MaaS). Jester threat group sells subscriptions to Jester Stealer from one month to lifetime. advertised and rented on the Dark Web.
The Jester threat group does not provide a delivery service; however, Phishing is frequently used to infect victims with Jester Stealer. Once it is executed, Jester Stealer connects to its C2 server using TOR. Later, it gathers confidential data and exfiltrates it in ZIP archives using TOR proxies. Unlike other stealer malware, Jester Stealer provides easy integration of TOR proxies and threat actors’ Telegram bot.
How Picus Helps Simulate Jester Stealer Malware?
Using the Picus Continuous Security Validation Platform, you can test your security controls against the Jester Stealer Trojan. We advise you to simulate Jester Stealer malware and determine whether your security controls can prevent them or not. Picus Threat Library includes the following threats to simulate Jester Stealer.
|
Threat Name |
|
Jester Infostealer .EXE File Download (3 variants) |
|
Jester Loader Malware .EXE File Download (3 variants) |
MITRE ATT&CK Techniques Used by Jester Stealer Malware
Initial Access
T1566.001 Phishing: Spearphishing Attachment
Execution
T1047 Windows Management Instrumentation
T1204 User Execution
Privilege Escalation
T1055 Process Injection
T1055.012 Process Injection: Process Hollowing
Defense Evasion
T1027.002 Obfuscated Files or Information: Software Packing
T1055 Process Injection
T1055.012 Process Injection: Process Hollowing
T1070.004 Indicator Removal on Host: File Deletion
T1112 Modify Registry
T1497 Virtualization/Sandbox Evasion
T1497.003 Virtualization/Sandbox Evasion: Time Based Evasion
T1553.002 Subvert Trust Controls: Code Signing
Credential Access
T1056.004 Input Capture: Credential API Hooking
Discovery
T1010 Application Window Discovery
T1012 Query Registry
T1120 Peripheral Device Discovery
T1033 System Owner/User Discovery
T1082 System Information Discovery
T1497 Virtualization/Sandbox Evasion
T1497.003 Virtualization/Sandbox Evasion: Time Based Evasion
T1518.001 Security Software Discovery
Lateral Movement
T1021.001 Remote Services: Remote Desktop Protocol
Collection
T1056.004 Input Capture: Credential API Hooking
T1113 Screen Capture
Command and Control (C2)
T1008 Fallback Channels
T1090.003 Proxy: Multi-hop Proxy
T1102 Web Service
T1105 Ingress Tool Transfer
T1571 Non-Standard Port
Exfiltration
T1041 Exfiltration over C2 Channel
Impact
T1486 Data Encrypted for Impact
Indicators of Compromise (IOCs)
|
MD5 |
SHA-1 |
SHA-256 |
|
9f4639a96ca5f604ad6df57c1ad9b549 |
02f9a9ffb68c2f2b9f382d7616e5d331c83421cb |
6c696dfabef6726c984759bbd8ea68c048bf2a8efd056597bcbe0b179c3a9d89 |
|
351606274af408607e77ed663bd7a041 |
8d106045e41005976bad85381e4e173522c1c538 |
63c6a046117b72d93b4e7080112efeef75a56c70fc739337a0e58a24bc9b483c |
|
17311685b626728febd2b02b10bef166 |
44220969370c56ffa1dd54c1c3252ccfde8a50d2 |
010207d4463874eabd3808b12355e24acab67ff55c93c075625c2a05e481fd31 |
|
87cc59d6197172dbdb2c95ac2f5e48d9 |
622c52806bdd7efd89ce77c27822ac9969900fdb |
6dd7f4652faa45c4e124cdeb6582262b8572f5ed8bd7fbdb2967ee5dce01d8e0 |
|
2d8ebe016b08ce37b916c8ce5889970b |
0af319908e3694a61beb6c46b6d1348953fe802f |
cdbed3a79d37d581fc5be268df61e13aaafa5c88a001f4e8b298d77c4b37ae13 |
|
b7061d79323a4795c17c4ddda7e46da4 |
c529ceec64e01721078de2d710dc15d694918266 |
3168f18432106cfaf21f48598c1b26b1026de7a0bac69ae548c79dec67be7853 |
Reference
[1] “How About a Magic Trick? A New Jester In Court,” Cyberint, 25-Jan-2022. [Online]. Available: https://cyberint.com/blog/research/jester-stealer/.








