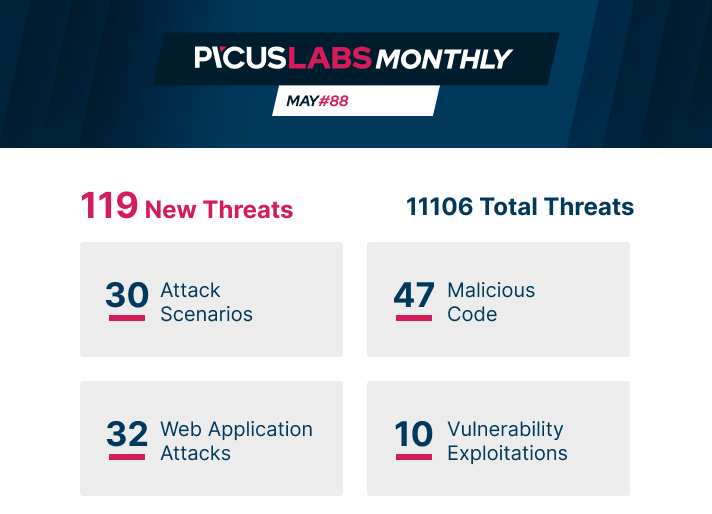
PICUS LABS MONTHLY #May 2021
MAY'S THREAT: DARKSIDE RANSOMWARE GROUP |
A Rising Ransomware Threat Group: DarkSideThe Darkside ransomware group established several high-profile breaches, including the US-based Colonial Pipeline Company incident in May 2021. They have established the Ransomware as a Service (RaaS) model and expanded their operations with the participation of other threat actors. In addition to encrypting files and demanding ransom, the Darkside threat actors exfiltrate data and threaten the victim by releasing the exfiltrated data, known as the double-extortion tactic.
You can test the effectiveness of your security controls against the Darkside ransomware campaigns with the "655212 Darkside Ransomware Attack Scenario" in Picus Threat Library. You can also validate your defenses against Darkside malware samples with threats 312355, 424348, 727882, 551628, 269817, 588030, 507789, 230239, 675517, 247255, 429456, 591155, 304959, 204994, 506926, and 166962 in Picus Threat Library.
|
MAY'S THREAT ACTORS |
UNC2447
APT29
|
ATTACK SCENARIOS |
APT / Malware ScenariosDarkSide Ransomware Scenario Picus Threat ID: 655212
ACTIONS:
1. Gather System Language via Powershell
PortDoor Backdoor Scenario Picus Threat ID: 571886
ACTIONS:
1. Copy a File "winlog.wll" in MS Word Startup Folder for Persistence ATT&CK Technique: T1547 Boot or Logon Autostart Execution ATT&CK Tactic: Persistence, Privilege Escalation
2. Execute Backdoored WLL using rundll32.exe ATT&CK Technique: T1218 Signed Binary Proxy Execution ATT&CK Tactics: Defense Evasion
3.Displays the current date and time variables using "net time" ATT&CK Technique: T1124 System Time Discovery ATT&CK Tactic: Discovery ...
9. Encrypt a file "253774.csv" using AES ATT&CK Technique: T1560 Archive Collected Data ATT&CK Tactic: Collection
Atomic AttacksCredential Dumping Stored Credentials with SeTrustedCredmanAccessPrivilege
Credential Dumping from Protected Processes via PPLDump
Process Injection by using DoppelGate Technique
Our world-class red team analyzed 500.000 TTPs to identify the top 10 most common ATT&CK techniques. Download Now: The Red Report: Your Handbook to Utilize MITRE ATT&CK Framework |
MALICIOUS CODE |
|
DarkSide Ransomware
UNC2447 - Sombrat, Fivehands, Hellokitty, Deathransom, Warprism, Beacon, Foxgrabber
APT29 - CobaltStrike Beacon
|
WEB APPLICATION ATTACKS |
|
HTTP Protocol Stack Remote Code Execution Vulnerability Variant-1
Microsoft Exchange Server Remote Code Execution Vulnerability
Apache OfBiz Deserialization to RCE Vulnerability
|
VULNERABILITY EXPLOITATIONS |
|
Ubuntu OverlayFS Privilege Escalation .ELF File Download Variant-1
ExifTool ANT Perl Injection Vulnerability Variant-1
GitLab Remote Code Execution .RMD File Download Variant-1
 |
SIGMA RULES |
|
Suspicious XSL Script Processing via WMI Execution
Computer Information Discovery via WMIC Tool
Sophos Antivirus Service Stop via Taskkill Tool
|








