MARCH'S THREAT: HAFNIUM THREAT GROUP
The Rise of State-Sponsored Threat Groups HAFNIUM is a state-sponsored group that primarily targets entities in the United States across many industry sectors, including infectious disease researchers, law firms, higher education institutions, defense contractors, policy think tanks, and NGOs.
You can test the effectiveness of your security controls against the HAFNIUM threat group with '719575 HAFNIUM Threat Group Exchange Server Post-Exploitation Scenario" in Picus Threat Library. You can also validate your defenses against malware samples used by HAFNIUM with Picus ThreatID 3719270 and webshell samples with Picus ThreatIDs 510920 and 349535 in Picus Threat Library.
In this article HAFNIUM threat actor to understand their attack methods and the impact of this breach.
MARCH'S THREAT ACTORS
HAFNIUM
Picus Threat ID: 719575, 3719270, 349535, 510920 Target Regions: North America Target Industries: Government, Education, Healthcare
MuddyWater
Picus Threat ID: 396146, 843253, 752295 Aliases: Seedworm, TEMP.Zagros Target Regions: Europe, Middle East, North America Target Industries: Government, Education, Healthcare Malware: PassDump, RemoteUtilities trojan dropper , RemoteUtilities trojan
Picus Labs has updated the Picus Threat Library Earth Vetala Campaign of MuddyWater APT Group Mustang Panda
Picus Threat ID: 680904, 312114, 408602, 232031
Aliases: Bronze President, TEMP.Hex, HoneyMyte, and Red Lich
Target Regions: Asia, Europe, and North America
Target Industries: Telecom., aviation, government, NGOs, and think tanks.
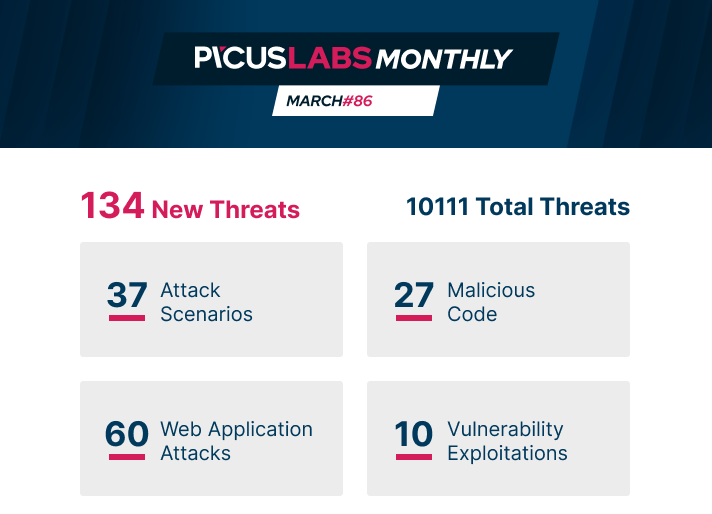
Our world-class red team analyzed 500.000 TTPs to identify the top 10 most common ATT&CK techniques.
ATTACK SCENARIOS
Atomic Attacks Windows Kernel Win32k Elevation of Privilege Scenario
Picus Threat ID: 671282 CVE: CVE-2021-1732 ATT&CK Technique: T1134 Access Token Manipulation ATT&CK Tactics: Defense Evasion, Privilege Escalation
Shellcode Execution via EnumChildWindows Callback Function
Picus Threat ID: 222204 ATT&CK Technique: T1055 Process Injection ATT&CK Tactic: Defense Evasion, Privilege Escalation
webinar, we dig down into T1055 Process Injection as the no. 1 technique in the Picus 10 Critical MITRE ATT&CK Techniques list.
Credential Dumping via RtlReportSilentProcessExit API Call
Picus Threat ID: 611239 ATT&CK Technique: T1003 OS Credential Dumping ATT&CK Tactic: Credential Access
For more information on MITRE ATT&CK T1003 Credential Dumping, here is the blog post you can read: MITRE ATT&CK T1003 Credential Dumping
MALICIOUS CODE
HAFNIUM
Picus Threat ID: 372862, 260828, 701507 Signature ATT&CK Technique: T1486 Data Encrypted for Impact Target Regions: ALL Target Industries: Logistics, Entertainment, Real Estate, Media
HelloKitty Ransomware
Picus Threat ID: 282623 Signature ATT&CK Technique: T1486 Data Encrypted for Impact Target Regions: ALL Target Industries: ALL
DEWMODE Dropper used by UNC2546 Threat Group
Picus Threat ID: 728133, 238722, 208936 Target Regions: North America Target Industries: Telecommunication
WEB APPLICATION ATTACKS
Microsoft Exchange Server Unauthorized SSRF Vulnerability Variant-1
Picus Threat ID: 520680 CVSS 3 Base Score: 9.8 Critical CVE: CVE-2021-26855 Affected Product: Microsoft Exchange
VMware View Planner Remote Code Execution Vulnerability Variant-1
Picus Threat ID: 395919 OWASP Top 10: A1 - Injection CVSS 3 Base Score: 9.8 Critical CVE: CVE-2021-21978 Affected Product: VMware
GitLab Path Traversal Vulnerability
Picus Threat ID: 673135 OWASP Top 10: A5 - Broken Access Control CVSS 3 Base Score: 5.5 Medium CVE: CVE-2020-10977 Affected Product: GitLab
VULNERABILITY EXPLOITATIONS
Microsoft Appx Deployment Service Elevation of Privilege Vulnerability
Picus Threat ID: 619884 CVE: CVE-2019-0841 CVSS 3 Base Score: 7.8 High Affected Product: Windows Appx Deployment Service
Win32k Denial of Service Vulnerability .EXE File Download Variant-5
Picus Threat ID: 859973 CVE: CVE-2021-1732 CVSS 3.1 Base Score: 7.8 High Affected Product: Win32k Graphics Service
Windows Installer Service Privilege Escalation Vulnerability
Picus Threat ID: 740070 CVE: CVE-2021-1727 CVSS 3.1 Base Score: 7.8 High Affected Product: Windows Installer Service
SIGMA RULES
Credential Dumping From Keepass Database
Picus Sigma ID: 3985 Technique: T1055.005 Process Injection: Thread Local Storage Tactic: Defense Evasion, Privilege Escalation
Our research has found that Process Injection was the most prevalent MITRE ATT&CK technique used by adversaries in their malware. For more information on MITRE ATT&CK T1055 Process Injection blog post Data Collection with 7z.exe via Commandline
Picus Sigma ID: 5178 Technique: T1560.001 Archive Collected Data: Archive via Utility Tactic: Collection
Credential Dumping via Procdump
Picus Sigma ID: 3929 Technique: T1003.001 OS Credential Dumping: LSASS Memory Tactic: Credential Access