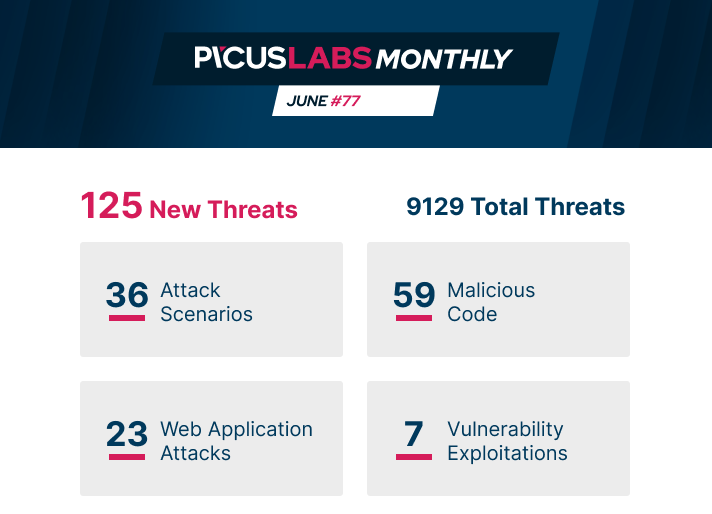
PICUS LABS MONTHLY #June 2020
JUNE'S THREAT: MAZE |
Customized Cobalt Strike BeaconsAlthough Cobalt Strike is a penetration testing product, it has become popular amongst targeted threat actors. A Cobalt Strike Beacon has various functions, including, but not limited to command execution, key logging, file transfer, SOCKS proxying, privilege escalation, mimikatz, port scanning, and lateral movement. You can test the effectiveness of your security controls against Cobalt Strike Beacons with '748618 Cobalt Strike Beacon used in Military Themed Campaign' in Picus Threat Library. |
JUNE'S THREAT ACTORS |
Ke3chang
Cycldek
Tor2Mine
Our world-class red team analyzed 500.000 TTPs to identify the top 10 most common ATT&CK techniques. Download Now: The Red Report: Your Handbook to Utilize MITRE ATT&CK Framework |
ATTACK SCENARIOS |
APT39 Threat GroupPicus Threat ID: 840562ACTIONS 1. Create a scheduled task using schtasks Technique: T1053 Scheduled Task Tactic: Execution, Persistence, Privilege Escalation
2. Display list of applications and services using "tasklist /v" Technique: T1049 Process Discovery Tactic: Discovery
3. Pass the Hash via PsExec Tool Technique: T1075 Pass the Hash Tactic: Lateral Movement ... 8. File Exfiltration Over DNS Technique: T1048 Exfiltration over Alternate Protocol Tactic: Exfiltration Netwire RATPicus Threat ID: 506809
ACTIONS 1. Create a new Registry Key for Autorun Technique: T1060 Registry Run Keys / Startup Folder Tactic: Persistence
2. Process Injection into Notepad via Process Hollowing Technique: T1093 Process Hollowing Tactic: Defense Evasion 3. Collect User Keystrokes into a File Technique: T1056 Iput Capture Tactic: Credential Access ... 17. File Exfiltration Over HTTP Port 80 Technique: T1048 Exfiltration over Alternate Protocol Tactic: Exfiltration
Atomic AttacksProcess Injection by using NtMapViewOfSection Function
ETW Logging Bypass with Environment Variable Spoofing
Mimikatz Execution with Evasion by using BetterSafetyKatz
|
MALICIOUS CODE |
|
Copperhedge Backdoor
Gh0st RAT
Kingminer Botnet
|
WEB APPLICATION ATTACKS |
|
Cisco UCS Director Cloupia Script Directory Traversal
Node JS Server Side Template Injection (SSTI)
LimeSurvey Stored XSS
|
VULNERABILITY EXPLOITATIONS |
|
Firefox DACL Sandbox Escape
SMBleed Microsoft SMB Server Denial of Service
Microsoft Windows OLE RPC Marshalling Buffer Overflow
 |
SIGMA RULES |
|
WiFi Credential Dumping via Network Shell
Process Injection via Frida Framework
Suspicious Conhost.exe Process Execution
|








