FEBRUARY'S THREAT: CLOP RANSOMWARE
|
The New Kid on the Block: the Clop Ransomware
Clop is ransomware that uses the .clop extension after having encrypted the victim's files. Another unique characteristic belonging with Clop is in the string: Dont Worry C0P included into the ransom notes. It is a variant of CryptoMix ransomware, but it additionally attempts to disable Windows Defender and to remove the Microsoft Security Essentials in order to avoid userspace detection.
You can validate your defenses against Ryuk malware samples with threats 789990, 536388, 864037, 752292 in Picus Threat Library.
|
FEBRUARY'S THREAT ACTORS
|
UNC2456
- Picus Threat ID: 231391, 574050, 532705, 360493, 265593
- Aliases: Seedworm, TEMP.Zagros
- Target Regions: Europe, Middle East, North America
- Target Industries: Telecommunication, Government, Oil
- Malware: Covicli Backdoor, PowGoop Loader, SSF.MX Backdoor
Hidden Cobra
- Picus Threat ID: 253176, 825496
- Aliases: Lazarus, APT38
- Target Regions: Europe, Middle East, North America, Asia
- Target Industries: Telecommunication, Finance, Government, Military
- Malware: AppleJeus Trojan, Foundre Trojan, Kupay Dropper
For more information on Hidden Cobra Advanced Persistent Threat (APT) Group, here is the blog post you can read:
Gamaredon
- Picus Threat ID: 680904, 312114, 408602, 232031
- Target Regions: Europe, Middle East, North America, Africa
- Target Industries: Telecommunication, Finance, Government
|
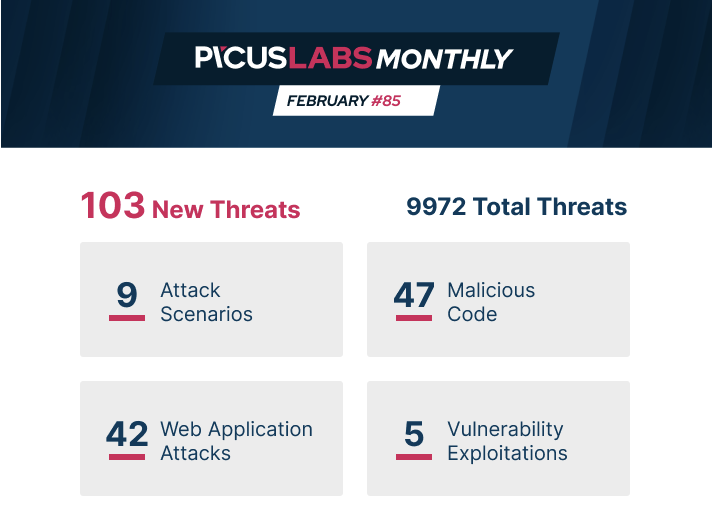
ATTACK SCENARIOS
|
Atomic Attacks
Disable Windows Defender for Endpoint by using Firewall Rules
- Picus Threat ID: 641385
- ATT&CK Technique: T1562.001 Impair Defenses: Disable or Modify Tools
- ATT&CK Tactic: Defense Evasion
Bypass User Access Control via ComputerDefaults.exe
- Picus Threat ID: 233800
- ATT&CK Technique: T1548.002 Abuse Elevation Control Mechanism: Bypass User Account Control
- ATT&CK Tactics: Privilege Escalation, Defense Evasion
Credential Dumping by using Custom MiniDumpWriteDump
- Picus Threat ID: 648954
- ATT&CK Technique: T1003.001 OS Credential Dumping: LSASS Memory
- ATT&CK Tactic: Credential Access
Our world-class red team analyzed 500.000 TTPs to identify the top 10 most common ATT&CK techniques.
|
MALICIOUS CODE
|
|
Clop Ransomware
- Picus Threat ID: 789990, 536388, 864037, 752292
- Signature ATT&CK Technique: T1083 File and Directory Discovery
- Target Regions: ALL
- Target Industries: ALL
Hancitor Malware Downloader
- Picus Threat ID: 692429, 475346, 484979, 789118, 641668
- Signature ATT&CK Technique: T1486 Data Encrypted for Impact
- Target Regions: ALL
- Target Industries: ALL
DEWMODE Dropper used by UNC2546 Threat Group
- Picus Threat ID: 769020, 706012
- Signature ATT&CK Technique: T1082 System Information Discovery
- Target Regions: ALL
- Target Industries: ALL
|
WEB APPLICATION ATTACKS
|
|
Atlassian Confluence Remote Code Execution via Macro Preview Feature
- Picus Threat ID: 726719
- OWASP Top 10: A1 - Injection
- CVSS 3 Base Score: 9.8 Critical
- CVE: CVE-2019-3396
- Affected Product: Atlassian Confluence
SAP Solution Manager Remote Code Execution Vulnerability Variant-1
- Picus Threat ID: 770413
- OWASP Top 10: A1 - Injection
- CVSS 3 Base Score: 9.8 Critical
- CVE: CVE-2020-6207
- Affected Product: SAP Solution Manager
Cisco ASA and Firepower Arbitrary File Deletion
- Picus Threat ID: 842421
- OWASP Top 10: A5 - Broken Access Control
- CVSS 3 Base Score: 9.1 Critical
- CVE: CVE-2020-3187
- Affected Product: Cisco ASA and Firepower
Adobe Magento Commerce Cross-Site Scripting (XSS) Vulnerability
- Picus Threat ID: 546452
- OWASP Top 10: A7 - Cross-Site Scripting (XSS)
- CVSS 3 Base Score: 4.8 Medium
- CVE: CVE-2021-21029
- Affected Product: Magento Commerce
|
VULNERABILITY EXPLOITATIONS
|
|
Google Chrome V8 Out of Bounds Read Vulnerability
- Picus Threat ID: 421523
- CVE: CVE-2020-16041
- CVSS 3 Base Score: 8.1 High
- Affected Product: Google Chrome V8 Engine
Python PyCArg_repr Buffer Overflow Vulnerability
- Picus Threat ID: 832392
- CVE: CVE-2021-3177
- CVSS 3 Base Score: 9.8
- High Affected Product: Python 3.X
Windows Kernel CSRSS Denial of Service Vulnerability
- Picus Threat ID: 716228
- CVE: CVE-2020-16938
- CVSS 3 Base Score: 5.5 Medium
- Affected Product: Windows Kernel
|
SIGMA RULES
|
|
Privilege Escalation via Modifying Group Policy Objects
- Picus Sigma ID: 6932
- Technique: T1068 Exploitation for Privilege Escalation
- Tactic: Credential Access, Defense Evasion, Lateral Movement, Privilege Escalation
System Information Discovery by Gathering OS Build Number Information via WMIC Tool
- Picus Sigma ID: 5889
- Technique: T1082 System Information Discovery
- Tactic: Discovery
Windows Defender Disable via Firewall Rules
- Picus Sigma ID: 6964
- Technique: T1562 Impair Defenses
- Tactic: Defense Evasion
|