PICUS LABS MONTHLY #April 2021
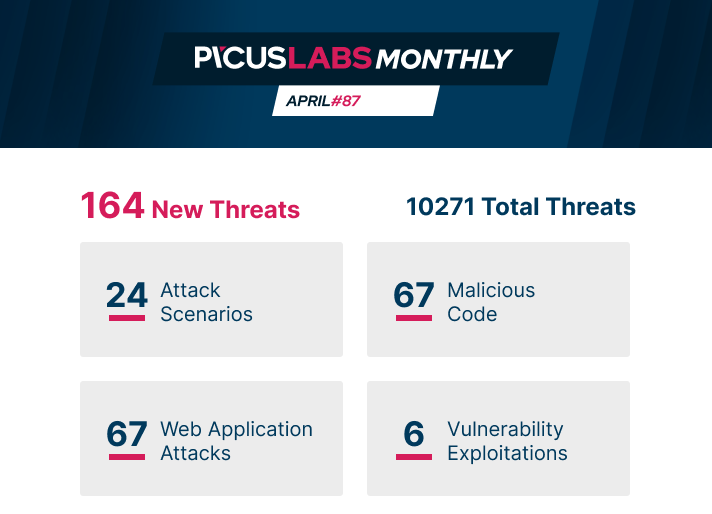
APRIL'S THREAT: FIN7 THREAT GROUP |
A Financially-Motivated Threat Group: FIN7FIN7 is a financially motivated threat group that has targeted victims in USA, UK, EU and Australia. It has primarily targeted finance. retail, restaurant, and hospitality sectors since mid-2015 by using point-of-sale malware. Some resources state that FIN7 is sometimes referred to as Carbanak, Anunak, but others claim that they are two separate groups using the same Carbanak malware and are therefore tracked separately.
You can test the effectiveness of your security controls against the FIN7group campaigns with '370387 FIN7 Group Attack Scenario" and 708444 "Information Gathering by using custom JScript used by FIN7 Group" in Picus Threat Library. You can also validate your defenses against FIN7 group samples with threats 709341, 382205, 789625, 490237, 447047, 756048, 498916, 224682, 573801, 704552, 269222, 502462, 346346, 107949, 219132, 926233, 793453, 601202, 512322, 691212, 692311, 159622, 205953, 197044, 102942, 704354, 904564, 705922, 803452, 703415, 169394, 207923, 234134 in Picus Threat Library. |
APRIL'S THREAT ACTORS |
FIN7
LazyScripter
APT28
|
ATTACK SCENARIOS |
APT / MalwareFIN7 Group APT Scenario Picus Threat ID: 370387
ACTIONS:
1. Execute JScript to Profile Target System ATT&CK Technique: T1059 Command and Scripting Interpreter ATT&CK Tactic: Execution
2. Execute Command by using FacefodUninstaller DLL Search Order Hijacking ATT&CK Technique: T1574 Hijack Execution Flow ATT&CK Tactics: Persistence, Privilege Escalation, Defense Evasion
3. Execute Shellcode by Reading a Registry Key ATT&CK Technique: T1055 Process Injection ATT&CK Tactic: Defense Evasion, Privilege Escalation. .. 10. Execute Keylogger by using Reflective DLL ATT&CK Technique: T1056 Input Capture ATT&CK Tactic: Collection, Credential Access
LazyScripter Threat Group Attack Scenario Picus Threat ID: 370387
ACTIONS:
1. Bypass User Access Control via Kocktopus Loader ATT&CK Technique: T1548 Abuse Elevation Control Mechanism
2. Disable Windows Defender via Koctopus Loader ATT&CK Technique: T1562 Impair Defenses
3. Execute Octopus Loader using Mshta.exe ATT&CK Technique: T1218 Signed Binary Proxy Execution 7.Execute Koadic Implant using Rundll32.exe (LazyScripter APT)
Sodinokibi Ransomware Scenario
ATT&CK Technique:T1566 Initial Access
2. Create a new Registry Key for RunOnce ATT&CK Technique: T1112 Modify Registry
3. Reflective DLL Injection via Invoke-ReflectivePEInjection ATT&CK Technique: T1055 Process Injection 9. Exfiltrate Collected Data via Image from the Victim over the HTTP Port 80 ATT&CK Technique: T1048 Exfiltration Over Alternative Protocol
Atomic AttacksPersistence with XSL Templates
Source Code Obfuscation via RosFuscator
Mimikatz Execution by using Shellcode compiled with sRDI
Our world-class red team analyzed 500.000 TTPs to identify the top 10 most common ATT&CK techniques. Download Now: The Red Report: Your Handbook to Utilize MITRE ATT&CK Framework |
MALICIOUS CODE |
|
APT28 - Delphocy Dropper
Clop Ransomware
Cring Ransomware
|
WEB APPLICATION ATTACKS |
|
VMware vCenter - ESXi - Cloud Foundation Remote Code Execution Vulnerability
SonicWall Email Security Post-Authentication Arbitrary File Read Vulnerability
WordPress XML External Entity Injection (XXE) Vulnerability Variant
|
VULNERABILITY EXPLOITATIONS |
|
Windows Service Elevation of Privilege via Symlink
Google Chrome V8 SimplifiedLowering Heap Corruption Vulnerability
Google Chrome Escape Sandbox via Devtools_page |
SIGMA RULES |
|
System Information Discovery by Gathering OS Information via WMIC Tool
Gathering Credential Access via Windows Security Login Prompt
IExplorer Data Deletion via Inet.cpl
|









