What Is a Red Team?
As our world becomes increasingly digitized, the importance of cybersecurity continues to grow. With new threats emerging every day, organizations must be diligent in their efforts to protect their systems, processes, and personnel. One way to proactively address potential vulnerabilities is through the use of a Red Team.
Composed of expert cybersecurity professionals, a Red Team simulates real-world attacks to identify weaknesses in an organization's security posture. By exposing vulnerabilities, organizations can strengthen their defenses and prevent potential cyber-attacks. In this way, a Red Team serves as an essential tool in the ongoing battle against cybercrime.
What Is a Red Team?
A Red Team is a group of authorized offensive security professionals who carry out real-world attack simulations that mimic the tactics, techniques, and procedures (TTPs) used by sophisticated adversaries to identify the potential attack paths that an attacker can take to compromise an organization's network and systems. The goal of the Red Team is to provide a comprehensive evaluation of an organization's security posture by identifying weaknesses and vulnerabilities that may have gone unnoticed by other security personnel and controls.
The Red Team conducts goal-oriented and driven assessments using a variety of techniques, such as social engineering, physical security testing, and ethical hacking to mimic the tactics, techniques, and procedures (TTPs) that are used by sophisticated real-world adversaries. By combining these techniques, red teamers identify potential attack paths which, at first glance, do not appear to be connected to one another, but actually allow the attacker to achieve their objectives.
What is Red Teaming?
Red Teaming is an exercise or a process that involves conducting adversarial simulations, vulnerability assessments, and penetration tests to evaluate an organization's security posture. Red Teaming exercises can be carried out by an internal Red Team or by an external group of experts who are contracted to perform the assessment.
The purpose of Red Teaming is to identify and assess potential risks and vulnerabilities in an organization's security infrastructure, policies, and procedures. By mimicking the tactics, techniques and procedures (TTPs) used by real-world sophisticated adversaries, red teamers can identify potential attack paths that attackers can take to reach their objectives.
Red Teaming exercises can provide valuable insights into an organization's security controls and help organizations improve their security measures, close potential gaps, and better defend against potential threats.
In addition to identifying vulnerabilities, Red Teaming exercises can also help to:
-
Test Incident Response and Security Awareness Training: By simulating real-world attack scenarios, organizations can evaluate the effectiveness of their incident response plans and security awareness training programs.
-
Develop a Deeper Understanding of the Threat Landscape: Red Teaming exercises can help organizations to better understand the evolving tactics, techniques, and procedures used by cybercriminals and other threat actors.
-
Improve Communication and Collaboration Between Security Teams: Red Teaming exercises can foster better communication and collaboration between different security teams within an organization, leading to more effective and efficient security operations.
-
Validate Security Investments: Red Teaming exercises can help organizations to determine whether their security investments are providing the expected level of protection and to identify areas where additional investment may be needed.
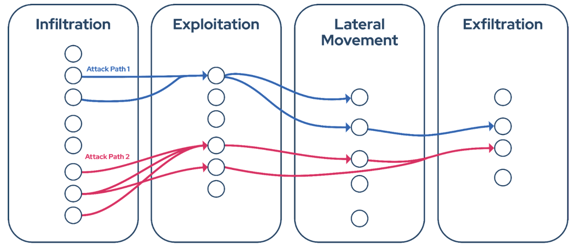
Figure 1. Red Teamers chaining different attack vectors to find stealthy attack paths [1].
This helps organizations to better understand how their systems and networks can be exploited, providing them with an opportunity to strengthen their defenses before a real attack occurs. By identifying potential risks and vulnerabilities that may not be immediately apparent, Red Teaming enables organizations to stay one step ahead of potential attackers and reduce the risk of a costly cybersecurity breach.
What Are the Essential Skills Required to Be an Effective Red Team Member?
To be an effective Red Team member, one must possess a diverse set of technical skills. Here, we provide six main skills required to be an effective red team member.
-
Proficiency in Operating Systems
-
Malware Analysis and Reverse Engineering
-
Knowledge in Network Protocols
-
Programming Skills
-
Knowledge in Penetration Testing Tools
-
Understanding Security Controls
-
Social Engineering Skills
Each skill is given with a brief explanation.
Proficiency in Operating Systems
Proficiency in operating systems, such as Windows, macOS, Linux, and Android, is a critical skill for Red Teamers. They should have a thorough understanding of these operating systems, including their underlying architectures, functionalities, and security mechanisms. Additionally, they should have a strong understanding of the commonly abused built-in tools and third-party frameworks that advanced persistent threats (APTs) use.
Along with proficiency in operating systems, a Red Team member should have a good understanding of virtualization technologies such as VMware, VirtualBox, and Hyper-V, and cloud computing platforms such as AWS, Azure, and Google Cloud Platform. This knowledge is essential to assess the security of these platforms and identify any vulnerabilities that can be exploited by adversaries.
Malware Analysis and Reverse Engineering
To perform effective red teaming, a Red Team member should also have experience in memory analysis, malware analysis, and reverse engineering of binaries to identify and exploit vulnerabilities in operating systems.
This requires knowledge of various debugging tools such as IDA Pro, OllyDbg, and WinDbg, as well as familiarity with different file formats such as PE, ELF, and Mach-O. Possessing these skills and knowledge enables a Red Team member to effectively simulate real-world attacks and identify weaknesses in an organization's defenses.
Knowledge in Network Protocols
Red teamers use network protocols to identify potential vulnerabilities and weaknesses in an organization's network infrastructure.
For example, they may analyze the traffic between devices on a network using protocols such as TCP, UDP, or IP to identify potential weaknesses in communication security. They may also look at DNS records to identify potential misconfigurations or vulnerabilities in an organization's domain name resolution. Additionally, understanding protocols like HTTP/HTTPS can help red teamers identify vulnerabilities in web applications, while knowledge of SSH and VPN protocols can enable them to identify and exploit weaknesses in remote access infrastructure.
Ultimately, understanding and analyzing network protocols is essential for red teamers to effectively identify and exploit vulnerabilities in an organization's network infrastructure.
Programming Skills
Red Team members must possess advanced programming skills to develop custom tools and exploits that can bypass security measures and evade detection. This requires proficiency in programming languages such as Python, Ruby, C/C++, and Bash, which are necessary to create custom tools and payloads to exploit vulnerabilities.
Knowledge in Penetration Testing Tools
Proficiency in advanced security tools is crucial for Red Teamers to effectively assess an organization's security posture. Familiarity with tools such as Burp Suite, Cobalt Strike, Mimikatz, PowerShell, and Empire Framework is necessary for executing sophisticated cyberattacks.
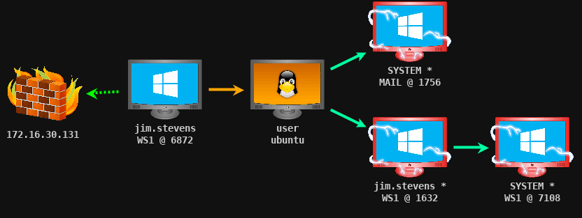
Figure 2. Pivoting with Cobalt Strike in an Organization Network [2].
Additionally, expertise in Wireshark for network analysis, Nmap for port scanning, and Kali Linux as a versatile penetration testing platform is essential. Red Teamers must also be familiar with leveraging social engineering tools like the Social-Engineer Toolkit (SET) to exploit human-related vulnerabilities.
Building competence in these diverse tools allows Red Teams to conduct comprehensive security assessments, identify weaknesses, and help organizations strengthen their defenses against real-world cyber threats.
Understanding Security Controls
Furthermore, an in-depth understanding of security controls is essential for Red Teamers to efficiently assess and bypass an organization's defenses.
Proficiency in firewalls, intrusion detection and prevention systems (IDS and IPS), endpoint security solutions, and virtual private networks (VPNs) enables them to analyze and exploit potential weaknesses. Knowledge of secure configurations, encryption technologies, and access control mechanisms is also vital to comprehensively test an organization's resilience against cyber threats. By comprehending these security controls, Red Teamers can better simulate real-world attacks, helping organizations identify vulnerabilities and optimize their security measures.
Social Engineering Skills
Finally, expertise in social engineering techniques is critical for testing an organization's human element of security, such as phishing attacks, pretexting, baiting, and tailgating.
By possessing all these skills, a Red Team member can effectively simulate realistic attacks against an organization's defenses and help identify vulnerabilities, thereby improving the organization's overall security posture.
What Are the Key Responsibilities of a Red Team Member?
There are four key responsibilities of a Red Team member.
-
Simulating Real-World Attacks,
-
Reporting,
-
Collaborating with Other Team (Blue and Purple), and
-
Continuous Cyber Threat Intelligence (CTI).
Below, we provided a brief overview of each responsibility.
Simulating Real-World Attacks
A Red Team member is responsible for simulating real-world attacks on an organization's security infrastructure to identify weaknesses and vulnerabilities that could be exploited by attackers. This involves conducting thorough assessments of the organization's systems, networks, and applications using a variety of techniques, including penetration testing, social engineering, and vulnerability scanning.
Reporting
Once vulnerabilities and critical attach paths are identified, a Red Team member is responsible for documenting their findings in a clear and comprehensive manner, including recommendations for improving the organization's defenses. This documentation is critical for helping the organization understand the potential impact of the vulnerabilities and prioritize their remediation efforts.
Collaboration with other Teams
Red Team members must also work closely with other security personnel, such as Blue Teams and Purple Teams, to ensure that their findings are integrated into the organization's overall security strategy. This collaboration helps to ensure that the organization is taking a comprehensive approach to security, and that vulnerabilities are addressed in a timely and effective manner.
Moreover, Red Team members must possess a strong understanding of the organization's business objectives and risk tolerance. This knowledge ensures that their assessments and recommendations are aligned with the organization's overarching goals, providing a tailored and effective approach to cybersecurity.
Continuous Cyber Threat Intelligence (CTI)
Cyber Threat Intelligence (CTI) is a crucial component for Red Teams to stay ahead in the cybersecurity landscape. It involves gathering, analyzing, and applying information about potential threats, adversaries, and their tactics, techniques, and procedures (TTPs). By utilizing CTI, Red Teams can enhance their capabilities and better understand the risks and attack vectors that may impact their organization.
Some key aspects of CTI for Red Teams include:
-
Information Sharing
-
Integrating of Intelligence Sources
-
Threat Actor Profiling
-
Indicator of Compromise (IoC) Analysis
-
Adapting to Evolving Threats
Each key aspect is provided with a brief explanation.
Information Sharing
Red Team members should actively participate in information sharing platforms and communities, such as ISACs (Information Sharing and Analysis Centers) and threat intelligence feeds. By exchanging knowledge with peers and industry experts, they can gain insights into emerging threats and stay current with global trends.
-
Integration of Intelligence Sources
Red Teams should leverage multiple sources of intelligence, including open-source intelligence (OSINT), commercial threat feeds, and internal data generated from security monitoring and incident response efforts. By integrating these diverse sources, Red Teams can develop a more comprehensive understanding of the threat landscape.
-
Threat Actor Profiling
Understanding the motivations, capabilities, and TTPs of threat actors enables Red Teams to anticipate potential attack scenarios and prioritize defensive measures. By profiling adversaries, they can tailor their security assessments and recommendations to address specific risks.
-
Indicator of Compromise (IOC) Analysis
Red Teams should analyze and correlate IOCs, such as IP addresses, domains, file hashes, and patterns of behavior associated with known threats. This analysis allows them to detect and mitigate attacks at an early stage, reducing the potential impact on the organization.
-
Adapting to Evolving Threats
Red Team members must be prepared to adapt their strategies and techniques based on the changing threat landscape. This requires continuous learning and the ability to think like an attacker, anticipating new attack vectors and developing innovative ways to test and strengthen their organization's defenses.
By incorporating these CTI-related activities into their daily operations, Red Team members can more effectively identify vulnerabilities, understand the threats facing their organization, and contribute to a robust cybersecurity posture.
What Are the Benefits of Having a Red Team for an Organization?
There are seven main benefits of having a Red Team in our organization.
-
Identifying Vulnerabilities
-
Testing the Effectiveness of Security Controls
-
Staying Up-to-Date with Latest Attack Techniques
-
Validating Security Investments
-
Increasing Awareness
-
Regulatory Compliance
-
Risk Management
In the below, we provide a brief explanation for each benefit.
Identifying Vulnerabilities
Red Teams play a critical role in proactively identifying weaknesses in an organization's defense systems by simulating real-world cyber attack. This often involves a comprehensive approach, testing everything from the physical security of servers, the robustness of network infrastructure, to the resilience of software applications against a variety of attack vectors. Thus, red teaming exercise helps organizations to identify vulnerabilities within their security before an actual attacker can exploit them.
Testing the Effectiveness of Security Controls
Red teaming exercises can be used to test the effectiveness of an organization's existing security controls. By simulating real-world tactics, techniques, and procedures (TTPs) used by sophisticated adversaries, organizations have a chance to see how well their security controls react to a potential attack. For instance, in a red teaming engagement, an ethical hacker may begin with a low-level user account with limited privileges and manage to pivot to another domain, where they compromise an admin-level account. If existing EDR or IPS solutions fail to detect this attack, it indicates that the organization's security controls may be operating in default mode.
Staying Up-to-Date with Latest Attack Techniques
Threat landscapes continuously evolve. By having a Red Team that stays up-to-date with the latest attack techniques or advancements in areas like zero-day exploits, advanced persistent threats (APTs) attack campaigns, and sophisticated social engineering tactics, an organization can better protect itself against new and emerging threats.
Additionally, understanding the nuances of emerging security vulnerabilities in new technologies, such as cloud infrastructures, IoT devices can be instrumental in shaping effective defensive strategies.
Validating Security Investments
Organizations often allocate substantial resources to fortify their security infrastructure. A Red Team plays a critical role in validating these substantial investments. By probing and testing the defenses under conditions that mimic real-world scenarios, they can assess the effectiveness of the security measures in place. This not only assures that the funds are well-spent but also aids in identifying areas that may need further strengthening or modification.
Increasing Awareness
The findings from Red Team activities serve as potent awareness tools for the wider workforce. These results provide tangible examples of potential attack vectors, highlighting the intricacies of cyber threats. By communicating these findings, organizations can reinforce the importance of strict adherence to security policies and procedures. This can lead to a more informed, vigilant staff, thereby enhancing the overall security culture within the organization.
Regulatory Compliance
In several industries, regular Red Teaming exercises are not merely beneficial but mandatory to comply with industry standards and regulations. These rigorous assessments help ensure that the organization is abiding by the prescribed guidelines, thereby avoiding potential penalties and reputational damage. Moreover, they demonstrate the organization's commitment to maintaining a robust security posture.
Risk Management
Red Teaming can play a vital role in an organization's risk management strategy. By uncovering vulnerabilities and potential entry points for attackers, it provides a clear view of the areas of highest risk. This empowers the organization to manage risk more effectively, enabling them to prioritize their efforts and resources towards addressing the most critical vulnerabilities. In turn, this proactive approach can significantly reduce the likelihood of successful cyberattacks.
How Does a Red Team Differ From a Blue Team?
Red Team and Blue Team play distinct roles in cybersecurity exercises, each contributing to the improvement of an organization's security posture. The table below highlights the key differences between the two teams:
|
Red Team (Offensive) |
Blue Team (Defensive) |
|
Simulates cyberattacks to exploit vulnerabilities |
Detects, assesses, and responds to simulated attacks |
|
Assumes the mindset of a sophisticated adversary |
Focuses on proactive defense and incident response |
|
Employs penetration testing and social engineering |
Utilizes security tools, protocols, and systems |
|
Imitates real-world attack techniques |
Analyzes network activity and configures security tools |
|
Seeks to remain undetected while infiltrating |
Prioritizes and mitigates the most dangerous threats |
|
Gains experience with threat actor TTPs |
Stays up-to-date with the latest cybersecurity trends |
What Is the Difference Between a Red Team Assessment and a Penetration Test?
Penetration Testing and Red Team assessments are two distinct methods used to evaluate an organization's cybersecurity posture. While both aim to strengthen security, they have different objectives, methodologies, and outcomes. The following table provides a comparison of key aspects to help you understand their differences:
Comparison Table for Penetration Testing and Red Team
|
Aspect |
Penetration Testing |
Red Team |
|
Objective |
Identify and exploit vulnerabilities in systems |
Achieve specific objectives by simulating real-world attacks |
|
Scope |
Focused on IT infrastructure, applications, networks |
Comprehensive security evaluation, including people and processes |
|
Duration |
Shorter, ranging from days to a few weeks |
Longer, spanning several weeks to months |
|
Methodology |
In-depth technical analysis, vulnerability-centric |
Blended approach, using technical, social, and physical tactics |
|
Technical Expertise |
Deep knowledge of tools, exploit techniques, and systems |
Broad expertise in cyber-attack tactics, tools, and procedures |
|
Threat Modeling |
Based on known vulnerabilities and attack vectors |
Adapts to evolving threats and simulates advanced adversaries |
|
Collaboration & Stealth |
Limited collaboration with internal teams, less stealthy |
Stealthy, often working without the knowledge of internal teams |
|
Outcome |
Identification, assessment, and remediation of vulnerabilities |
Test detection, response, security culture, and overall resilience |
|
Real-time Adaptation |
Limited, follows a pre-defined scope |
Adapts tactics and techniques as the assessment progresses |
|
Cost |
Generally more cost-effective |
Higher cost due to extended duration, scope, and required expertise |
What Is the Difference Between a Red Team Assessment and Security Control Validation?
Red teaming is a manual process where a group of security experts, acting as adversaries, attempt to breach an organization's defenses.
In contrast, SCV uses automated and continuous simulations of real-world attack scenarios to validate the performance of security controls. While red teaming provides valuable insights into an organization's security posture, it is often time-consuming and resource-intensive. SCV, on the other hand, offers a scalable and efficient alternative that can be performed regularly without straining resources.
|
Security Control Validation (SCV) |
Red Teaming |
|
|
Testing Method |
Utilizes automated, continuous testing methods |
Involves manual, scenario-based testing |
|
Testing Frequency |
Carried out continuously and on-demand |
Conducted periodically, typically annually or biannually |
|
Security Control Focus |
Primarily verifies effectiveness of existing security controls |
Aims at penetrating defenses to evaluate resilience |
|
Real-World Attack Scenarios |
Simulates known attack scenarios for testing |
Uses real-world attack scenarios to assess defenses |
|
Speed & Efficiency |
High speed and efficiency due to automation |
Lower speed and efficiency due to manual, in-depth testing |
|
Resource Intensity |
Requires fewer resources due to automation |
Requires significant resources due to manual testing |
|
Scope |
Covers both prevention and detection layers |
Broad, covering the entire organization |
|
Actionable Recommendations |
Provides specific recommendations to improve controls |
Offers limited, often strategic, recommendations |
|
Integration with Security Frameworks |
Integrated with frameworks such as MITRE ATT&CK and Cyber Kill Chain |
Limited integration with specific security frameworks |
|
Quantifiable Metrics |
Offers quantifiable metrics for evaluation |
Provides limited quantifiable metrics, more qualitative analysis |
|
Non-Disruptive Testing |
Non-disruptive due to automated, controlled testing |
May cause disruptions due to real-world attack simulations |
How Does a Red Team Engage With Other Security Teams, Like the Blue Team and Purple Team?
Red Teams play a vital role in the security ecosystem of an organization, often engaging closely with other internal security teams such as the Blue Team and the Purple Team.
The Blue Team typically represents the defensive side of cybersecurity within an organization. When engaged with the Blue Team, the Red Team's role is to simulate cyber-attacks to test the effectiveness of the Blue Team's defensive measures. This adversarial interaction helps to identify weaknesses in the organization's defenses, providing valuable feedback to the Blue Team.
A Purple Team, on the other hand, is a blend of both Red and Blue Teams. This integrated team functions to facilitate maximum knowledge transfer and collaboration between offensive and defensive security roles. In a Purple Team setup, the Red Team brings their offensive strategies and insights to the table, and the Blue Team shares their defensive tactics and experiences. The purpose of this engagement is to collaboratively identify gaps in the organization's security posture and to devise strategies to address them.
By working together in these ways, these teams can help build a more robust and resilient security framework within the organization. Through continuous learning, refinement, and adjustment of strategies based on the other's input, the security posture of the organization can be significantly enhanced.
What Are Some Common Red Team Methodologies and Frameworks?
The most common Red Team methodologies and frameworks include:
-
The Open Source Security Testing Methodology Manual (OSSTMM)
-
The Penetration Testing Execution Standard (PTES)
-
The MITRE ATT&CK Framework
Each framework is provided with a brief description.
Open Source Security Testing Methodology Manual (OSSTMM)
This comprehensive methodology focuses on evaluating various aspects of an organization's security, including network infrastructure, web applications, wireless systems, and human assets. OSSTMM provides a systematic approach to assess security controls and identify gaps or vulnerabilities in an organization's defenses.
Penetration Testing Execution Standard (PTES)
PTES is a framework that aims to provide a clear, consistent, and repeatable process for conducting penetration tests. It focuses on understanding the objectives of an attacker and testing against those objectives. PTES comprises seven stages: pre-engagement interactions, intelligence gathering, threat modeling, vulnerability analysis, exploitation, post-exploitation, and reporting.
MITRE ATT&CK Framework
This knowledge base of adversary tactics, techniques, and procedures (TTPs) is built on real-world observations and experiences. The MITRE ATT&CK framework helps organizations understand how attackers operate and develop effective prevention, detection, and response strategies. It covers a wide range of attack vectors and platforms, enabling organizations to tailor their defenses to specific threats and attack methods.
These frameworks and methodologies provide a solid foundation for Red Teams to evaluate and improve an organization's cybersecurity defenses while understanding and emulating real-world attacker behaviors.
What Types of Targets or Systems Do Red Teams Typically Assess?
Red Teams typically assess a wide range of targets or systems within an organization to identify potential vulnerabilities and weaknesses. Some common targets and systems that Red Teams evaluate include:
-
Network Infrastructure
-
Web Applications
-
Mobile Applications
-
Wireless Networks
-
Cloud Infrastructure and Services
-
Endpoint Security
-
Physical Security
-
Human Assets
Each of these targets are provided with a brief description below.
Network Infrastructure
Red Teams assess the security of an organization's network components, such as routers, switches, firewalls, and intrusion detection/prevention systems. They look for misconfigurations, unpatched vulnerabilities, and other weaknesses that could be exploited by attackers.
Web Applications
Red Teams test web applications for vulnerabilities like SQL injection, cross-site scripting, broken authentication, insecure data storage, and other common web application security flaws.
Mobile Applications
Red Teams assess mobile applications on various platforms (e.g., iOS, Android) to identify security vulnerabilities related to data storage, communication, authentication, authorization, and more.
Wireless Networks
Red Teams evaluate the security of wireless networks, looking for weak encryption, default or easily guessable credentials, rogue access points, and other vulnerabilities that could allow unauthorized access or data interception.
Cloud Infrastructure and Services
Red Teams assess the security of cloud environments, including Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), and Software-as-a-Service (SaaS) offerings, to identify misconfigurations, insecure access controls, and other vulnerabilities.
Endpoint Security
Red Teams test the security of various endpoints, such as workstations, servers, and mobile devices, to identify weaknesses related to operating systems, applications, and security controls.
Physical Security
Red Teams evaluate an organization's physical security measures, such as access control systems, security cameras, and alarm systems, to identify potential vulnerabilities that could allow unauthorized access to facilities or sensitive information.
Human Assets
Red Teams often use social engineering techniques to assess the susceptibility of employees to scams, phishing attacks, and other manipulative tactics that could lead to unauthorized access, data breaches, or other security incidents.
By assessing these various targets and systems, Red Teams can help organizations identify vulnerabilities and weaknesses in their security posture, prioritize remediation efforts, and improve overall cybersecurity resilience.








