What Is Continuous Threat Exposure Management (CTEM)?
What Is Continuous Threat Exposure Management (CTEM)?
Continuous Threat Exposure Management (CTEM) is a cybersecurity process that leverages attack simulations to identify and mitigate threats to an organization’s networks and systems. This allows organizations to test their security posture and identify vulnerabilities before they are exploited by real attackers.
Gartner, in their Predicts 2023 report [1], emphasizes the importance for organizations to shift from simply addressing threats to proactively managing their threat exposure. In response to this ever-increasing threat landscape, Gartner introduced the CTEM process, which aims to consistently monitor, evaluate, and mitigate security risks through strategic improvement plans and actionable security posture remediation.
Unlike vendor-specific technologies or tools, CTEM offers a systematic approach that empowers organizations to effectively prioritize potential threats and corresponding remediation efforts, particularly in the face of a rapidly expanding attack surface.
By embracing the CTEM program, organizations can proactively address their security risks, staying ahead of evolving threats. Continuous Threat Exposure Management (CTEM) approach goes beyond traditional, reactive vulnerability management by providing a practical and pragmatic strategy to prioritize and tackle the most critical risks.
What Are the Benefits of Implementing a CTEM Program in an Organization?
There are six key benefits of implementing a CTEM program in an organization.
-
Proactive Risk Management
-
Prioritization of Threats
-
Enhanced Cyber Resilience
-
Actionable Insights
-
Alignment with Business Objectives
-
Adaptability
Each key benefit is provided with a brief description below.
1. Proactive Risk Management
CTEM programs help organizations proactively address vulnerabilities and threats by continuously scanning and monitoring their digital infrastructure. This holistic approach to cybersecurity shifts the focus from reactive to proactive, leading to a more robust defense against cyber threats.
2. Prioritization of Threats
CTEM programs help organizations prioritize threats based on their potential impact to their business and likelihood of occurrence. By evaluating the severity and potential damage of each threat, organizations can effectively allocate resources towards the most significant risks. This strategic approach to threat management results in more efficient use of resources and a quicker response to the most harmful threats.
3. Enhanced Cyber Resilience
The CTEM approach is iterative, encouraging organizations to continuously reassess and improve their defenses. This ongoing refinement leads to enhanced cyber resilience over time, as organizations learn from each assessment and adapt their defenses accordingly. Hence, CTEM ensures that defenses remain up-to-date and effective against evolving threats.
4. Actionable Insights
CTEM programs generate actionable insights from real-time threat data. These insights can help organizations implement effective remediation measures. CTEM's data-driven approach ensures that decisions are made based on the latest threat intelligence, leading to more effective and targeted remediation efforts.
5. Alignment with Business Objectives
A CTEM program enables organizations to align their cybersecurity strategies with broader business objectives. By understanding and incorporating the business's strategic goals into the CTEM program, organizations can ensure that their security efforts support, rather than hinder, their organizational goals. This alignment increases the value of cybersecurity efforts and ensures that they contribute to the overall success of the organization.
6. Adaptability
As technology and cyber threats evolve, a CTEM program can adapt to these changes, ensuring continuous and relevant protection. This adaptability is crucial in today's fast-paced digital landscape, where new threats can emerge rapidly.
What Are the Five Stages of a CTEM Program?
The five stages of a Continuous Threat Exposure Management (CTEM) program provide a cyclical and comprehensive approach to managing cybersecurity risks. Each stage of the program contributes to an organization's overall cyber resilience.
-
Scoping
-
Discovery
-
Prioritization
-
Validation
-
Mobilization
Below, we provided a brief overview of each step.
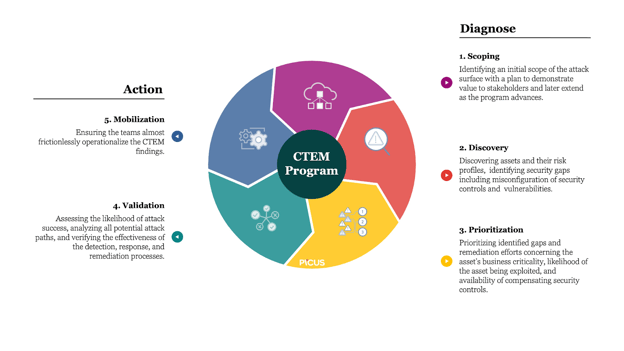
Figure. Five Phases of a CTEM Program.
1. Scoping
In CTEM, scoping is the initial phase where security teams identify the infrastructure segments to be included in the program. A thorough analysis of the organization's cyber resilience is conducted, encompassing both internal and external attack surfaces as well as cloud infrastructures. As part of this step, organizations need to determine what matters most to their business and accordingly define the scope of the CTEM program.
2. Discovery
The discovery phase of the Cyber Threat Exposure Management (CTEM) process is an in-depth exploration into the infrastructure defined during scoping. Here, security teams meticulously identify all assets, including the hidden ones, and evaluate their risk profiles. This process involves not only finding explicit vulnerabilities but also detecting subtle weaknesses such as misconfigurations and counterfeit assets. It's crucial to note that the success of the discovery phase isn't about the quantity of vulnerabilities found, but rather their potential impact on business operations. The extensive data gathered in this phase sets the foundation for the next crucial step: prioritizing risks based on their severity.
3. Prioritization
The prioritization phase of a CTEM process helps organizations to identify gaps in the security infrastructure, such as unprevented/undetected attacks, logging gaps, detection gaps, and missing, broken, and noisy detection rules. This phase is crucial in deciding where to focus remediation efforts and resources for maximum impact.
4. Validation
The validation phase of a CTEM process is crucial as it verifies the cybersecurity posture of an organization following the prioritization of threats, weak points, and remediation efforts. To ensure a thorough validation, the process should involve launching a controlled attack simulation or adversary emulation in a production environment.
It is crucial to underscore that the validation phase should not be solely dependent on traditional security assessment techniques such as red teaming and internal penetration testing. Rather, it should integrate automated and continuous security validation solutions like Breach and Attack Simulation (BAS), with Security Control Validation (SCV) serving as a prime use case for BAS.
These methods offer a more comprehensive view of an organization's security posture by considering not just the commonly leveraged and relevant threat vectors, but also the possibility of pivoting and lateral movement between internal hosts.
5. Mobilization
The mobilization phase in the CTEM process is a crucial step where security leaders drive the message that remediation cannot be entirely automated. While automated solutions can address common issues like patching or basic threat detection, they often fall short in addressing complex and nuanced vulnerabilities. Thus, security teams need to understand that automated remediation is an initial step and not a complete solution.
The mobilization phase involves rallying all stakeholders to appreciate this reality and to gear up for a more hands-on and nuanced approach towards cybersecurity risk management, tackling challenges that often prove problematic for security teams.
How Does CTEM Differ From Traditional Vulnerability Management Programs?
CTEM differentiates from traditional vulnerability management programs by being proactive rather than reactive, focusing on a wide range of threats instead of only known vulnerabilities, incorporating existing security measures, and utilizing advanced simulation tools for validation.
A CTEM process differs from traditional vulnerability management programs for six main characteristics.
-
Proactive and Reactive Approach
-
Broader Scope
-
Business-Aligned Prioritization
-
Continuous Improvement
-
Integration with Security Controls
-
Emphasis on Validation
Each characteristic is provided with a brief explanation.
1. Proactive vs. Reactive Approach
Traditional vulnerability management programs are typically reactive, focusing on identifying and patching known vulnerabilities after they have been discovered. On the other hand, CTEM takes a proactive approach by continuously monitoring the threat landscape and prioritizing the remediation of the identified threats and vulnerabilities before they can be exploited.
2. Broader Scope
Traditional vulnerability management programs typically focus solely on technical vulnerabilities. However, CTEM takes a more holistic view, acknowledging that threat exposure can come from various sources such as configuration errors, misused credentials, and insider threats.
3. Business-Aligned Prioritization
Traditional vulnerability management can struggle with effective prioritization of remediation efforts, often resulting in patching all vulnerabilities, regardless of their severity. Conversely, CTEM aligns its prioritization with business objectives, focusing on the most critical threats and vulnerabilities that could potentially impact the organization's most valuable assets.
4. Continuous Improvement
Traditional vulnerability management programs often take a point-in-time approach, performing periodic scans and then moving on. CTEM, on the other hand, promotes a cycle of continuous improvement, constantly monitoring, evaluating, and enhancing the organization's security posture.
5. Integration with Security Controls
Traditional vulnerability management is often conducted separately from other security measures. In contrast, CTEM integrates with existing security controls, fostering a more holistic and effective approach to managing threat exposure.
6. Emphasis on Validation
Traditional programs often rely on theoretical assessments of vulnerabilities. CTEM, however, places significant emphasis on validation, using tools like Breach and Attack Simulation (BAS) and Security Control Validation to test the organization's actual defenses against simulated attacks.
Can CTEM Be Applied to Different Industries and Business Sizes?
Continuous Threat Exposure Management (CTEM) can be applied to businesses of all sizes and across various industries. The principles of CTEM, such as proactive threat monitoring, business-aligned prioritization, and continuous improvement, are universal and can be beneficial to any organization, regardless of its size or sector.
Whether it's a small business with a growing digital footprint or a large corporation with an extensive digital infrastructure, all organizations can benefit from implementing a CTEM program. The flexible and scalable nature of CTEM ensures that it can be adapted to suit the specific needs and resources of any organization.
Moreover, CTEM is highly relevant to industries that handle sensitive data, including but not limited to, finance, healthcare, IT, and e-commerce. These sectors face an array of cybersecurity threats and would greatly benefit from a proactive and continuously improving approach to managing these threats. The same holds true for businesses operating in regulated industries. CTEM not only helps to improve the security posture but also aids in compliance with various industry-specific cybersecurity regulations.
In conclusion, CTEM's broad applicability and scalability make it an effective cybersecurity strategy for businesses of all sizes and across all sectors.
What Role Does Automation Play in the CTEM Process?
Automation plays a crucial role in the CTEM process, enhancing efficiency, reducing manual effort, and enabling organizations to adapt quickly to the evolving threat landscape. It contributes to various stages in the following ways:
Discovery
Automated scanning tools and vulnerability management solutions can quickly identify vulnerabilities, misconfigurations, and weak points within an organization's infrastructure, offering comprehensive insights.
Prioritization
Automation helps process large volumes of data to prioritize threats and vulnerabilities based on factors such as potential impact, exploitability, and likelihood. Machine learning algorithms can be used to analyze historical and real-time threat intelligence data, effectively prioritizing remediation efforts. An example is the integration of threat intelligence feeds with vulnerability management solutions to provide a more informed prioritization process.
Validation
Automated technical assessments like Breach and Attack Simulation (BAS) platforms, Security Control Validation, and Attack Path Validation enable organizations to validate their security posture and controls continuously and cost-effectively. For instance, solutions like Security Control Validation (SCV) as the foremost use case of Breach and Attack Simulation (BAS) offer simulation of real-world attack scenarios and evaluate the effectiveness of security controls.
Mobilization
Automation can aid in the implementation of remediation efforts by streamlining communication, collaboration, and workflows across teams. Automated ticketing systems can be integrated with vulnerability management solutions to create and assign remediation tasks to the appropriate teams. Additionally, security orchestration, automation, and response (SOAR) platforms can help automate incident response and remediation processes, minimizing human intervention and reducing the time needed to address identified vulnerabilities and threats.
In summary, automation plays an essential role in the CTEM process by enabling organizations to identify, prioritize, validate, and address vulnerabilities and threats more efficiently and effectively. This approach helps organizations stay ahead of the evolving threat landscape and continuously improve their security posture.
What Are the Best Practices for Scoping in a CTEM Program?
Best practice for scoping in the Continuous Threat Exposure Management (CTEM) cycle involves a detailed analysis of the infrastructure segments that should be included in the process. It requires security teams to deeply understand the business aspects of their organization in order to define a suitable scope for the CTEM initiative. An optimal scope for a pilot CTEM program could include an examination of the external attack surface and SaaS security posture.
The process begins with a comprehensive discovery phase, where the cyber resilience of an organization is analyzed, documented, and quantified. This involves an assessment of the entire attack surface - externally, internally, and in the cloud.
As the CTEM cycle progresses, refinement of the scope becomes necessary. This is where precise metrics come into play. These metrics, derived from the initial scoping phase, should include network segment details, security control data, identified threat types, threat tactics/techniques, quantified risk, and overall cyber resilience metrics. These data points provide a foundation for aligning the refined scope with the organization's strategic cybersecurity goals.
Following these best practices ensures a thorough and effective scoping phase for a CTEM program, setting a solid foundation for the remaining steps in the cycle.
It is worth noting that platforms like Picus are ideally suited to aid in this process. By providing detailed metrics and thorough analyses of an organization's cyber resilience, Picus can greatly assist in both the initial scoping phase and subsequent refinements, helping to align the CTEM initiative with the organization's strategic cybersecurity goals.
How Can Organizations Measure the Success of Their CTEM Program?
The success of a Continuous Threat Exposure Management (CTEM) program can be measured by observing a substantial decrease in security risks, noticeable improvements in threat detection abilities, and a quicker response time for remediation. In addition, an effective CTEM program will show improved security control performance, compliance with regulatory standards, and alignment with key business priorities. Lastly, valuable insights can be gleaned from positive stakeholder feedback, further signaling a successful CTEM program.
-
Risk Reduction
-
Improved Threat Detection
-
Time to Remediate
-
Security Control Effectiveness
-
Compliance Metrics
-
Business Alignment
Each of these success measures are provided with a brief explanation.
1. Risk Reduction
The most direct way to measure the success of a CTEM program is by assessing the reduction in security risks. This can be quantified by tracking the number of identified vulnerabilities, the time taken to remediate them, and the decrease in successful attacks or breaches over time.
2. Improved Threat Detection
An effective CTEM program should lead to enhanced threat detection capabilities, demonstrated by an increase in both the number and complexity of threats detected. Integrating a framework like MITRE ATT&CK can further improve this process by providing a comprehensive view of prevention and detection coverage. This aids in identifying potential gaps in the system's defenses and enables more targeted and effective responses to threats, thereby bolstering overall cybersecurity resilience.
3. Time to Remediate
The speed at which identified threats and vulnerabilities are addressed is a crucial metric. A successful CTEM program should help reduce the time between detection and remediation.
4. Security Control Effectiveness
Using tools like Security Control Validation and Breach and Attack Simulation can provide quantitative data on how well security controls are performing and how their performance improves over time.
5. Compliance Metrics
For industries with regulatory requirements, achieving and maintaining compliance is a key success indicator. A decrease in compliance violations or issues can signal a successful CTEM program.
6. Business Alignment
A successful CTEM program aligns with business priorities. This can be measured qualitatively by assessing whether remediation efforts focus on protecting the most critical business assets and processes.
What Tools and Technologies Can Be Used to Support a CTEM Program?
Implementing a successful Continuous Threat Exposure Management (CTEM) program isn't merely about adopting a set of tools, as emphasized by Gartner when they stated, "CTEM is not a tool, it’s a program".
However, a successful CTEM program does necessitate the deployment of a suite of tools and technologies that can support the iterative nature of the process. These tools should aid in the discovery, assessment, prioritization, validation, and mobilization stages of the threat management cycle, facilitating more robust mitigation efforts.
Firstly, robust discovery tools are essential. They should be capable of identifying and analyzing the entirety of an organization's attack surface, which includes external, internal, and cloud environments. Tools that provide visibility into network segments, security controls, threat types, and tactics/techniques are crucial.
Once discovery is complete, assessment tools that offer quantified risk and cyber resilience metrics are required. They allow for an understanding of the organization's current security posture and inform the prioritization phase.
In the prioritization phase, tools that can assess the business criticality of assets, likelihood of exploitation of identified weak points, and the availability of compensating security controls are essential.
Validation is a critical step in the CTEM program, and it requires a suite of testing and validation tools. Breach and Attack Simulation (BAS) tools are a key part of this phase. They allow for the launching of controlled attack simulations or adversary emulation in a production environment, providing a clear picture of how the organization's defenses would fare against a real-world attack.
Finally, for the mobilization phase, tools that facilitate effective collaboration and communication are needed. They should enable teams to operationalize the CTEM findings and implement necessary remediation measures efficiently.
A comprehensive platform like Picus offers these capabilities under one roof. Picus' Security Control Validation (SCV) platform, for instance, serves as the foremost use case of the Breach and Attack Simulation (BAS) tool, providing a comprehensive security validation capability. By using Picus, organizations can effectively validate their cyber security posture, providing actionable insights and helping improve overall cyber resilience.
Frequently Asked Questions (FAQs)
How does CTEM help organizations stay ahead of emerging threats?
How does CTEM prioritize threats and remediation efforts?
How does CTEM deal with zero-day vulnerabilities?
How often should a CTEM cycle be repeated?
[1] “Predicts 2023: Enterprises Must Expand From Threat to Exposure Management.” [Online]. Available: https://www.gartner.com/guest/purchase/registration?resId=4021605. [Accessed: May 12, 2023]








