All Roads Lead to Rome – So Do Attacks. Validate Your Security Controls From Multiple Attack Points
Given the ever-evolving nature of the cybersecurity industry, security companies are no longer pondering if a security breach will take place, but rather waiting to see when it will happen. This is reinforced by the latest IBM Data Breach Report, which reveals that an alarming 83% of organizations experienced more than one data breach during 2022. As a result, it's imperative for security teams to proactively prepare and fortify their security systems and processes, which can certainly be achieved by performing stress tests continuously.
This blog introduces a new approach that takes security control validation to the next level by simulating cyber attacks from custom initial attack points. Let's delve into why this capability is critical in today's rapidly evolving threat landscape.
Closing the Gap with Breach & Attack Simulation (BAS)
Traditional penetration tests and red teaming exercises have long been utilized to evaluate security postures. While effective, these methods have limitations as they merely provide point-in-time snapshots and come at a significant cost. In contrast, Breach and Attack Simulation (BAS) tools have emerged as more comprehensive solutions,offering increased effectiveness by automating otherwise manual and repetitive tests while enabling continuous security monitoring
For instance, one of the most important use cases of any BAS solution is to validate the effectiveness of existing security controls, such as NG Firewalls, Secure Web or Email Gateways, Endpoint Protection Solutions and Web Application Firewalls (WAF). Traditionally, these controls were put in place to provide a secure perimeter around the “protected customer environment”. As long as an attacker could not penetrate from the outside-in, we felt secure within our “own walls”. However, with organizations moving to the cloud, people working remotely, and IoT devices spreading out everywhere, this perimeter has now dissolved so we can no longer rely on attackers only living and breeding outside of our network.
Moreover, today’s BAS solutions are typically SaaS platforms. By the nature of their architecture, they initiate the simulated attacks from the manager in the cloud, usually terminating on a specific agent deployed in the customer environment. This approach is most effective in simulating how a malicious attacker could infiltrate a corporate environment and identifying the gaps in the security controls along the path. Nonetheless, it clearly lacks the ability to validate the performance of security controls along alternative paths.
This is where Custom Initial Attack Points come in handy!
Introducing Attack Simulations with Custom Initial Attack Points
With the latest release by Picus, organizations are no longer constrained by predefined “outside-in” attack scenarios. The new capability empowers users to deploy custom attack agents within their own environments - be it on-premises or in the cloud - facilitating the execution of more advanced simulation scenarios from any initial attack point.
Let's explore some examples of how this flexibility revolutionizes cyber attack simulations and the ability to further enhance the ROI of existing security controls.
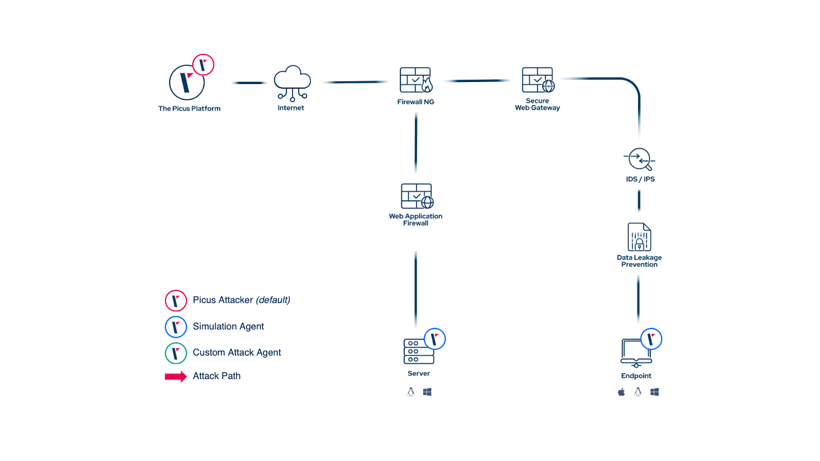
As discussed earlier, a cloud-based SaaS solution is the standard deployment scenario of all BAS solutions, including Picus.
Side note: The Picus Complete Security Validation Platform also supports on-prem deployments, tailored to organizations that are strictly regulated to keep data on premises.
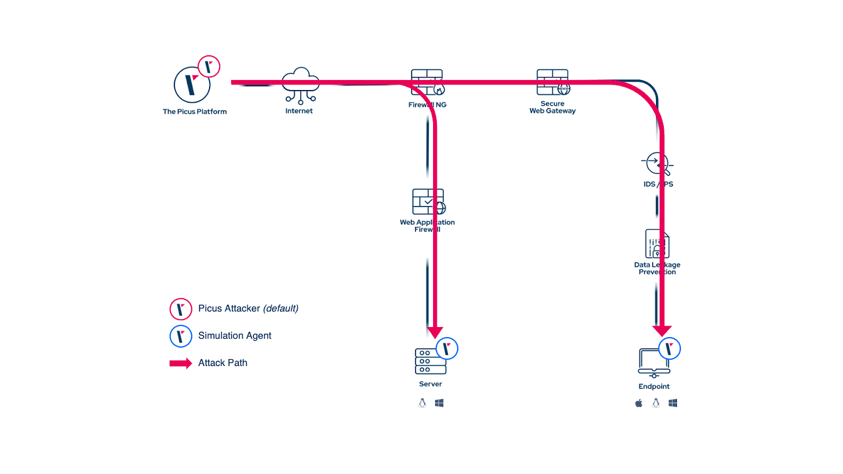
As it can be seen, all security controls in path are being validated for their ability to prevent and detect this particular threat.
But what if a particular “trusted” endpoint is compromised? This may be a user in a remote office or even a remote worker using their own device. It’s high likely that they are considered a “trusted user” and with that, their path and encountered security controls to access certain systems are different.
To simulate such use cases, The Picus Platform now supports the deployment of specific attacker agents on any machine they like:
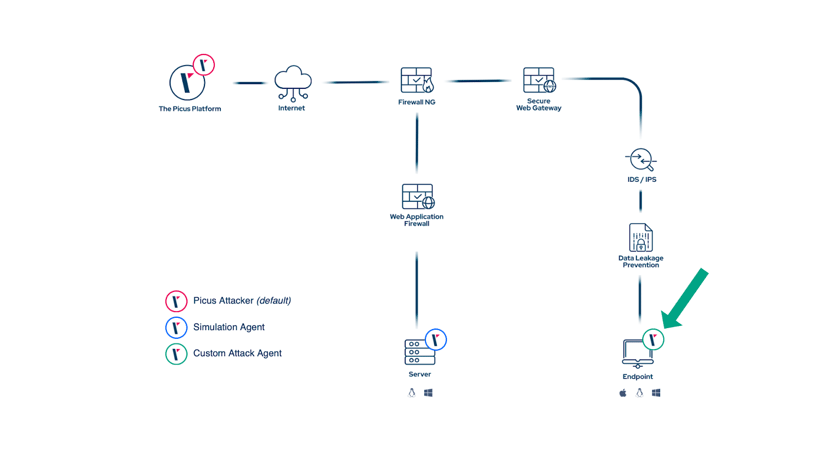
By doing so, customers can now simulate all relevant infiltration scenarios (mostly network infiltration and web application attacks) using this newly deployed attacker agent as initial attack point:
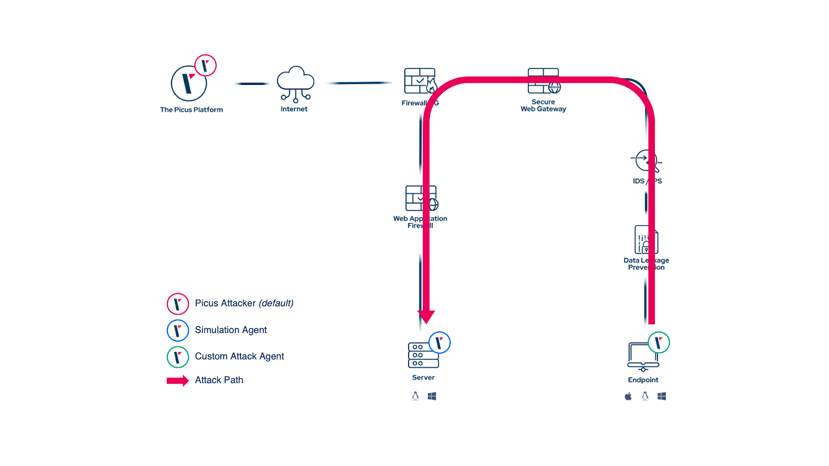
There are other relevant use cases where this approach can come in handy:
-
Simulating web application attacks targeting the backends systems
Organizations can gain a deeper understanding of their vulnerabilities and bolster their protection strategies by simulating web application attacks from front end servers to backends without web application firewalls (WAFs) in between. This is because front end servers often act as gateways to critical backend systems.
Traditionally, web application attack simulation validates the path from a user to the front end, passing a WAF in between. This way, any firewall or other controls in between the frontend and backend server are not validated. Assuming that the front end server can be compromised, we may want to get a better understanding of how the backend could be infiltrated.
-
Simulating Malware Attacks in Segmented Environments
Simulating malware attacks from a server subnet to a backup zone allows security teams to evaluate the efficacy of their segmentation measures and identify potential weaknesses. Many organizations maintain segmented networks and backup zones to minimize the impact of malware attacks, so custom initial attack points enable organizations to tailor these simulations to their specific network architecture.
Conclusion
As the cyber threat landscape continues to evolve, organizations must stay ahead of potential breaches. To achieve this goal, security teams must adapt their validation approaches to evolve at the same time as attackers gain new ways to infiltrate and compromise enterprise environments. As challenging as this may sound, a proper way to address this issue is by continuously performing stress tests and validating security controls from multiple attack points.
So far, this article has focused on how we can simulate attackers who try to infiltrate an environment from various entry points and how we can validate the effectiveness of the security controls in place to prevent such malicious behavior. Naturally, security leaders must not forget to also incorporate validation approaches going beyond these initial stages:
-
How can attackers leverage vulnerabilities and misconfigurations of critical systems (such as Active Directory) to move laterally within an environment and ultimately compromise your organization’s crown jewels?
Check out how Attack Path Validation can help to identify such critical attack paths.
-
It’s great to know how well security controls can prevent an attack. But what if something goes through? How strong are your detection capabilities?
Read more on how Detection Rule Validation can help you to assess and validate your detection rules before a breach happens.
With the introduction of custom attackers in Picus’ Security Control Validation solution combined with the full suite of validation capabilities of The Picus Platform, we empower organizations to simulate sophisticated attack scenarios tailored to their unique environments, enabling them to identify vulnerabilities, fortify their defenses, and enhance their overall security posture.
By embracing this new capability, your organization can proactively address security gaps, gain confidence in their existing measures, and ultimately be better prepared to mitigate cyber threats.
Are you interested in deploying your custom attacker in your own environment?








