High-Risk Cryptolocker Ransomware Disguised as Turkcell Invoice
A recent trend observed by our PicusLabs team shows that Cryptolocker Ransomware virus is becoming a high-risk threat for enterprises from a variety of sectors. That said, this post is written to inform the readers about a new cyber-attack wave which started on June 30th.
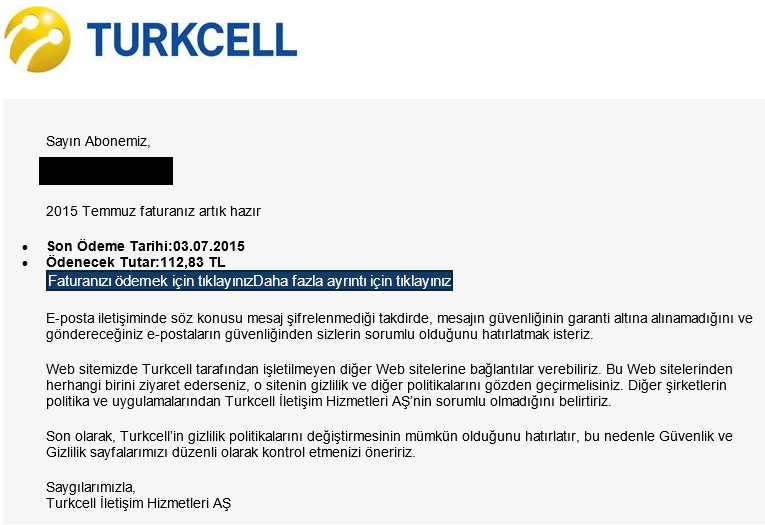
This particular cyber-attack disguises itself in Turkcell's invoice information email format (Turkcell is the largest GSM operator in Turkey). The primary aim of this attack is to catch the user by surprise due to the very high invoice balance that needs to be paid as shown in the email. Instantly, the content hooks the user and urges him/her to click the fake payment link embedded in the email.
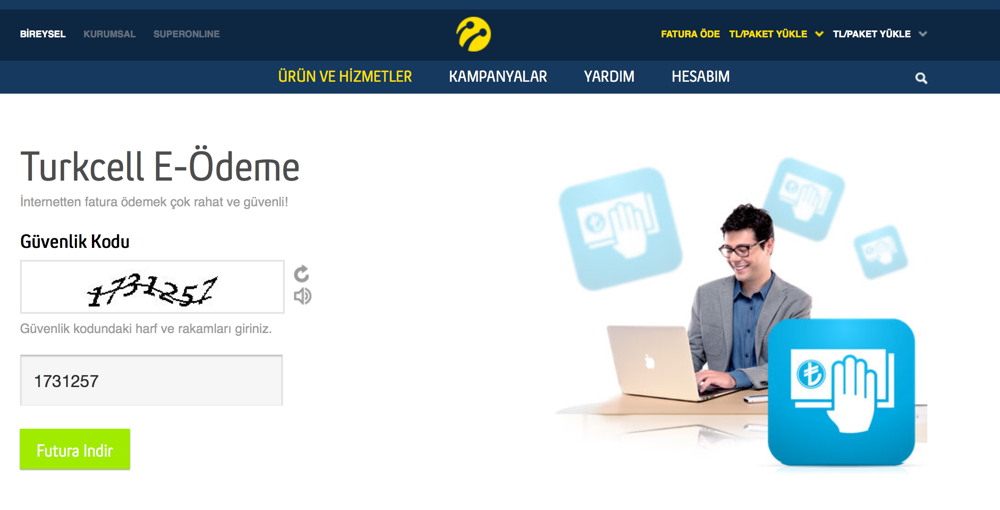
Victims who end up clicking the fake invoice payment link are being redirected to iturkcell.net and turkcell-efatura.com domains. These fake domains have user interfaces very similar to Turkcell's website and they request a security code input from everyone with an aim of reaching the invoice file. Obviously, downloaded invoice zip contains the Cryptolocker Ransomware infected file.
On July 2nd, 2015, we updated our Picus Cyber-Attack database with related attack vectors to assess Picus customers’ readiness against this particular threat. The threat comes with 4 domains containing the viral content and 2 variants of the Cryptolocker virus in ZIP and EXE.file formats.
At the moment, the installed Picus software on your security control systems contains the most up-to-date Cyber-Attack Database. What this means is that you can easily test your network security system's readiness to see whether they are immune to the most popular, high-risk cyber-threats including Cryptolocker. If you have not tried the Picus Platform yet, feel free to contact us to request a live Picus Demo. It takes only 2 hours before you see your network security system’s resilience in the face of Cryptolocker & 1000+ similar cyber-threats!








