T1021 Remote Services of the MITRE ATT&CK Framework
LAST UPDATED ON OCTOBER 23, 2024
The impact and scale of cyber attack campaigns have grown enormously in recent years. Adversaries cause significant damage to organizations by compromising multiple systems and networks in a single attack campaign. Pivoting other systems within a network often requires attackers to utilize lateral movement techniques. In this blog, we explain the most used lateral movement technique, T1021 Remote Services.
 |
The Red Report 2023
|
What is a Remote Service?
In an enterprise environment, servers and workstations are often organized into domains, which provide centralized identity management and allow users to log in with a single set of credentials across the entire network. If an adversary can obtain valid domain credentials, they can log in to multiple systems using remote services.
Remote Services are specifically designed to accept connections from remote systems, allowing users to interact remotely with and manage those systems. Some common examples of Remote Services include:
1. Telnet: Telnet is a remote login protocol that allows users to remotely connect to a server and issue commands as if they were physically present at the server's console. Telnet uses a plaintext communication channel, which makes it vulnerable to man-in-the-middle attacks and other types of interception.
2. Secure Shell (SSH): SSH is a network protocol that allows users to securely connect to a remote system and execute commands as if they were physically present at the system's console. SSH uses encryption to secure the communication channel, making it more secure than Telnet.
3. Remote Desktop Protocol (RDP): RDP is a proprietary protocol developed by Microsoft that allows users to remotely connect to and control a remote system using a graphical interface. RDP is commonly used to access Windows systems remotely and uses encryption to secure the communication channel.
4. Virtual Network Computing (VNC): VNC is a remote access protocol that allows users to remotely connect to and control a remote system using a graphical interface. VNC is available for many platforms and uses encryption to secure the communication channel.
5. Remote Procedure Call (RPC): VNC is a protocol that allows a computer program to cause a subroutine or procedure to execute on a different computer in a network. RPC enables the execution of functions or methods on a remote system as if they were local, allowing other systems to communicate and exchange data.
6. Server Message Block (SMB): SMB is a network protocol that enables sharing of resources such as files, printers, and serial ports between computers. It is primarily used in Windows environments and allows client systems to access resources on a server as if they were local. While SMB is not a traditional "remote service" like SSH and RDP, it can facilitate remote access to resources on a server.
7. Distributed Component Object Model (DCOM): DCOM is a technology that enables the communication between software components on different computers in a network. It allows a client object on one computer to call methods of a server object on another computer, using remote procedure call (RPC) technology. This enables the execution of functions or methods on a remote system as if they were local, allowing different systems to communicate and exchange data. While DCOM is not a "remote service," it enables communication between software components on various systems. It can be used in conjunction with other remote services or as part of a larger system.
8. Apple Remote Desktop (ARD): ARD is a remote management software developed by Apple Inc. for macOS. ARD allows administrators to access and control other macOS systems on a network remotely and includes a range of tools and features for managing and maintaining those systems. ARD uses a blend of protocols to provide remote access, including VNC for sending the screen and control buffers and SSH for secure file transfer. It can remotely execute commands and scripts, manage software updates and installations, and perform other tasks on remote systems. In this way, ARD functions as a remote service, enabling administrators to access and manage other systems on a network remotely.
MITRE ATT&CK T1021 Remote Services
T1021 Remote Services technique refers to the exploitation of remote services for malicious activities. Adversaries may use a variety of remote services to gain access to and control over systems in a network during an attack campaign. Adversaries can abuse these services to perform actions as logged-on users, move laterally within a network, and execute arbitrary code on remote systems.
For example, an adversary may use valid credentials to log into a system using Telnet, SSH, RDP, or VNC and then execute commands or scripts on that system to gather information, install malware, or perform other malicious actions. Adversaries may also use ARD or similar remote management tools to remotely access and control network systems to perform actions such as executing commands, transferring files, or installing software.
In addition to using these services directly, adversaries may also abuse other protocols and technologies, such as Remote Procedure Call (RPC) and Distributed Component Object Model (DCOM), to facilitate remote communication and the execution of functions or methods on a remote system.
The MITRE ATT&CK framework categorizes the T1021 Remote Service technique under Lateral Movement tactics, and this technique has seven sub-techniques.
- T1021.001 Remote Desktop Protocol
- T1021.002 SMB/Windows Admin Shares
- T1021.003 Distributed Component Object Model
- T1021.004 SSH
- T1021.005 VNC
- T1021.006 Windows Remote Management
- T1021.007 Cloud Services
T1021.001 Remote Desktop Protocol
Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft that allows users to access and control a system over a network connection remotely. RDP is commonly used in corporate environments to enable employees to access and work on their workstations from any location remotely. However, if RDP is not properly secured, it can also be exploited by cyber attackers to gain unauthorized access to a victim's system.
Adversary Use of Remote Desktop Protocol
While RDP is a useful tool for legitimate remote access, cyber attackers can also abuse it in their attack campaigns. Adversaries may use valid accounts to log into a computer via RDP and perform actions as an authenticated user. There are several ways that attackers can use valid accounts and RDP to their advantage:
- Credential Access techniques (e.g., OS Credential Dumping [T1003] technique)
- Brute-force attacks [T1110] (e.g., dictionary attacks)
- Phishing attacks [T1566]
Once an attacker has gained access to a victim's system through RDP, they can execute commands and manipulate the system as if they were physically present at the keyboard. Here are some ways in which adversaries have been known to abuse RDP:
1. Initial Access: Adversaries may use RDP to gain initial access to a target system or network if the service allows access to accounts with known credentials. They may use Credential Access techniques to obtain these credentials through brute-force attacks or by stealing them from other sources.
2. Lateral Movement: Once an adversary has gained initial access to a system, they may use RDP to move laterally within the environment and access other systems. This can be done by connecting to other systems and using the RDP session to browse and copy files or by using RDP to execute code on the remote system.
3. Persistence: Adversaries may use RDP to maintain a persistent presence on a system by configuring the system to accept RDP connections or leaving an RDP session open and active.
4. Execution: Adversaries may use RDP to remotely execute code or commands on a system by interacting with the system directly through the RDP session or by using RDP to launch a command prompt or other program remotely.
5. Privilege Escalation: Adversaries may use RDP to gain higher levels of access or privilege on a system by authenticating to the RDP server with a privileged account or exploiting vulnerabilities in RDP to gain access to more elevated privileges.
6. Defense Evasion: Adversaries may use RDP to evade security controls and avoid detection by communicating over an encrypted RDP connection or by using RDP to launch programs or execute commands that bypass security controls.
7. Exfiltration: Adversaries may use RDP to exfiltrate data from a target system or network. They may do this by connecting to the system and transferring files over the RDP connection or by using RDP to remotely access other systems that contain the data they want to steal.
8. Command and Control: Adversaries may use RDP to establish a command and control (C2) channel with their malware or other tools. This can be done by using RDP to execute code remotely or tunneling other protocols, such as HTTP or HTTPS, through the RDP connection.
9. Malware distribution: Adversaries may use RDP to distribute malware within a target environment. They may do this by connecting to systems and installing the malware directly or using RDP to execute code that downloads and installs the malware from a remote location.
T1021.002 SMB/Windows Admin Shares
This sub-technique refers to using Server Message Block (SMB) and Windows Admin Shares to gain access to and control a victim's system. SMB is a network protocol that shares resources, such as files and printers, on a network. Windows Admin Shares are hidden shares created by default on Windows systems and used for administrative purposes. While SMB and admin shares are useful tools for legitimate resource sharing, they can also be abused by adversaries in their attack campaigns.
Server Message Block (SMB): SMB is a network protocol that is used to share resources, such as files and printers, between computers on a network. SMB is a client-server protocol, which means that a client computer can access resources on a server by sending requests to the server using the SMB protocol.
SMB can be used as a remote service in the sense that it allows remote systems to access resources on a network. For example, a user on a remote system may connect to a file server using SMB, and access shared files on that server. SMB can also be used to remotely execute commands and scripts and to remotely manage services and other resources on a system.
Since SMB is a protocol rather than a service that accepts connections from remote systems, it is not typically considered a traditional "remote service" like Telnet, SSH, RDP, or VNC. It is generally used in conjunction with other services or protocols, such as NetBIOS or CIFS, to provide remote access to resources on a network.
Samba: Samba is an open-source implementation of the SMB protocol that allows non-Windows systems, such as Linux and macOS, to access and share resources with Windows systems. Samba uses the SMB protocol to provide compatibility with Windows, and it allows non-Windows systems to act as file and print servers in a Windows environment.
Samba can be a remote service because it allows remote systems to access shared resources on a network. For example, a user on a remote system may connect to a file server running Samba, and access shared files on that server. It can also be used to execute commands and scripts remotely and manage services and other resources remotely.
Samba is similar to SMB in terms of its functionality but is implemented as a separate software package that runs on top of other operating systems. Like SMB, Samba is generally used with other services or protocols, such as NetBIOS or CIFS, to provide remote access to resources on a network.
Admin Shares: In Windows, an admin share is a hidden network share that is created automatically by the system on every computer. These shares allow administrators to remotely access and manage a computer over the network.
There are several types of admin shares, including:
-
C$: This share allows an administrator to access the root of the C drive on the computer. This share is often used to install software or remotely access files on the C drive.
-
ADMIN$: This share allows an administrator to access the system root folder on the computer, which contains system files and other resources that are required for the operation of the computer.
-
IPC$: This share allows an administrator to access named pipes and other Interprocess Communication (IPC) resources on the computer.
These shares are hidden by default and are not accessible to users who do not have the necessary permissions. Note that an administrator must specify the share name and provide valid credentials to access an admin share.
Adversary Use of SMB/Windows Admin Shares
One way that attackers can abuse SMB is by using valid administrator-level accounts to remotely access a networked system over the network. This allows them to interact with the system using Remote Procedure Calls (RPCs), which are a way for a program on one computer to request services from a program on another computer.
Using SMB and RPCs, adversaries can transfer files to and from the system and execute transferred binaries. This can be done through authenticated sessions over SMB/RPC, which means that the attacker must provide valid credentials to access the system.
There are several techniques that adversaries may use to execute code on the system once they have gained access through SMB/RPC. These include creating Scheduled Tasks or Services, which are automatically executed at a specified time or when certain events occur, or using Windows Management Instrumentation (WMI), which is a framework for managing and automating system and network administration tasks.
Another way that attackers can abuse SMB is by exploiting vulnerabilities in the protocol. There have been several high-profile vulnerabilities in SMB that have been exploited by attackers in the past, such as CVE-2020-1206 (SMBleed), CVE-2020-0796 (SMBGhost), and MS17-010 (EternalBlue).
Adversaries may also use NTLM hashes to access administrator shares on systems with certain configurations and patch levels. NTLM (NT LAN Manager) is an authentication protocol that is used to authenticate users on a network. When a user logs into a system, their password is hashed using the NTLM algorithm, and the resulting hash is used to verify their identity. The Pass the Hash technique allows an attacker to use a stolen NTLM hash to access a system without knowing the original password. This can be done on systems with certain patch levels and configurations that are vulnerable to this type of attack.
Adversaries have been known to abuse SMB and Windows admin shares in order to move laterally within victim networks and gain access to additional systems. This is often done by obtaining valid credentials and using tools such as Net [2], PsExec [3], and Impacket's smbexec.py [4] to interact with these shares and execute commands on remote systems.
One common tactic is for adversaries to brute force SMB in order to gain access to these shares and move laterally, as in the case of Lucifer [5].
SMB and Windows admin shares have also been used for lateral movement by a number of APT groups, including APT3 [6] and APT32 [7]. In some cases, these groups have also used these shares to transfer implant files and enable remote execution, as seen in the case of APT41 [8].
Other groups, such as Conti [9] and Shamoon [10], have used these shares to spread malware throughout victim networks, potentially compromising an entire network. In the case of Kwampirs and Orangeworm [11], the malware was even copied across multiple Windows admin shares in order to move laterally.
Some adversaries, such as Deep Panda [12] and Duqu [13], have used valid accounts to access SMB shares and move laterally. In other cases, such as HermeticWizard [13], [14], the adversaries have used hardcoded credentials to authenticate via NTLM to SMB shares on remote systems.
As a recent example, the Prestige ransomware group copied the ransomware payload to the ADMIN$ share of a remote system in October 2022. Then, Impacket is utilized to execute the payload by creating a Scheduled Task or remotely executing an encoded PowerShell command on target systems [15].
In February 2022, BlackByte ransomware created SMB shares to distribute AnyDesk, a remote desktop application, to other assets in the victim's network using Cobalt Strike [1].
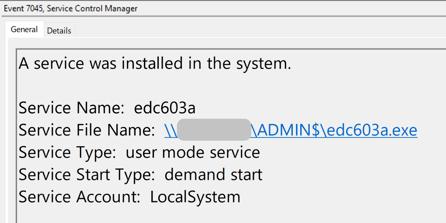
Figure 1: BumbleBee malware creating remote service
As an example from April 2022, the BumbleBee malware loader used by the EXOTIC LILY initial access broker (IAB) has abused SMB shares to move laterally to a domain controller by creating a remote service, as shown in the figure above [16].
T1021.003 Distributed Component Object Model
Distributed Component Object Model (DCOM) is a Microsoft technology that enables the communication between software components distributed across networked computers using Remote Procedure Calls (RPCs). It allows a client object on one computer to call methods on a server object on another computer, regardless of the programming languages used to implement the objects.
DCOM allows a client object on one computer to call methods of a server object on another computer using RPC. It enables software components to communicate with each other over a network, regardless of the programming languages or operating systems they are running on.
DCOM is used in a variety of applications, such as distributed applications, web services, and system management. It is an important part of the Windows operating system and is widely used in enterprise environments.
Permissions to interact with local and remote server COM objects are specified by access control lists (ACL) in the registry. By default, only Administrators may remotely activate and launch COM objects through DCOM. It is important to secure DCOM and properly configure access control to prevent unauthorized access or abuse.
Adversary Use of Distributed Component Object Model
One way adversaries may use DCOM is by taking advantage of valid accounts to interact with remote machines. DCOM uses access control lists (ACLs) in the registry to specify permissions for interacting with local and remote server COM objects. By default, only administrators have the privilege to activate and launch COM objects remotely through DCOM. If an adversary is able to compromise an account with sufficient privileges, they can use DCOM to perform actions as the logged-on user.
DCOM can also be used as a method of remotely interacting with WMI, which is a powerful system management tool that provides information about the hardware and software configuration of a computer. Adversaries can use DCOM to execute arbitrary code through WMI or to manipulate WMI data to achieve their goals.
For example, the attacker may use WMI to create a DCOM object and modify the registry on the remote system:
|
$dcom = New-Object -ComObject WbemScripting.SWbemLocator |
An attacker may use DCOM to execute code remotely on a system by creating a DCOM object and using it to launch a script or program. For example, the attacker may use PowerShell to create a DCOM object and execute a script on the remote system:
|
$dcom = New-Object -ComObject WScript.Shell |
Another way that adversaries may abuse DCOM is by executing macros in existing documents or invoking Dynamic Data Exchange (DDE) execution through a COM-created instance of a Microsoft Office application. This allows them to bypass the need for a malicious document and can be used to deliver payloads or execute code on the target system.
For example, the MuddyWater APT group has used DCOM to execute a malicious PowerShell payload [17], as seen in the following code:
|
$e = [System.Activator]::CreateInstance ([type]::GetTypeFromCLSID("9BA05972-F6A8- |
T1021.004 SSH
Secure Shell (SSH) is a network protocol used for secure remote login and other secure network services over an unsecured network. It is often used to access servers remotely and provides a secure channel for transmitting data between computers. Adversaries may abuse SSH for lateral movement, remote code execution, and remote access.
SSH can be used as a remote service in the sense that it allows users to log into a system and access its resources remotely. Users can connect to a system running an SSH server using an SSH client and authenticate with a username and password or a public key. Once authenticated, they can execute commands and access files on the system as if they were physically present.
SSH is commonly used to remotely manage servers, configure network devices, and automate tasks. It is an important tool for system administrators and IT professionals and is widely used in enterprise environments.
Adversary Use of SSH
Adversaries may abuse SSH for a variety of purposes in their attack campaigns. Some examples of adversary use of SSH include:
1. Lateral Movement
Adversaries may use SSH to move laterally within a network by logging into other systems and accessing their resources. This could be done using a tool such as SSH with a command similar to the following:
|
ssh <username>@<remote_system> |
This command connects to the specified remote system using the specified username, allowing the adversary to access the system and potentially move on to other systems.
In March 2022, Akamai security researchers discovered Panchan, a new peer-to-peer botnet, and SSH worm breaching Linux servers [18]. Panchan introduces a unique technique for lateral movement by reading the id_rsa and known_hosts files to harvest existing credentials and using them to move laterally across the network. Unlike most botnets, it does not rely solely on brute force or dictionary attacks on randomized IP addresses.
2. Remote Access and Command Execution
Adversaries may use SSH to remotely log into a system and execute commands or scripts, either directly or through a reverse shell.
|
ssh <username>@<remote_system> <command> |
This command connects to the specified remote system using the specified username and executes the specified command. Adversaries may use this method to access systems and perform actions as logged-on users remotely.
In an ongoing attack campaign since June 2022, RapperBot botnet malware is used in exclusive brute-force attacks on SSH servers configured to accept password authentication [19].
3. Persistence
In order to maintain remote access into the brute-forced SSH servers, RapperBot executes the following shell command to replace the remote victims' /.ssh/authorized_keys file with one that contains the threat actors' SSH public key [19]. Thus, SSH is also utilized by attackers for persistence.
4. Malware distribution
Adversaries may use SSH to distribute malware within a target environment. As an example, according to the joint advisory published by CISA [20], the Daixin Team ransomware and data extortion group move laterally via SSH and RDP after obtaining access to the victim's VPN server. Daixin actors have attempted to gain access to privileged accounts by dumping credentials [T1003] and Pass-the-Hash [T1550.002]. The actors used these privileged accounts to gain access to VMware vCenter Server and reset account passwords [T1098] for ESXi servers within the environment. The actors then used SSH to connect to accessible ESXi servers, where they deployed ransomware.
T1021.005 VNC
Virtual Network Computing (VNC) is a graphical desktop-sharing system allowing a user to control another computer remotely. It consists of a client and server component, where the server component is installed on the remote system, and the client component is installed on the local system. The client allows the user to see the remote system's desktop and interact with it as if they were physically present, while the server transmits the input and output between the two systems.
VNC can be used as a remote service because it allows users to access and control a system's desktop remotely. This can be useful for remote support, remote administration, and other remote tasks. It is supported on various platforms, including Windows, Mac, Linux, and other operating systems.
Adversary Use of VNC
Adversaries may abuse VNC for a variety of purposes in their attack campaigns. Some examples of adversary use of VNC include:
1. Remote Access and Command Execution
Adversaries may use VNC to remotely log into a system and execute commands or scripts directly or through a reverse shell. This could be done using a VNC client by connecting to the IP address and port of the VNC server on the remote system and authenticating with a valid username and password. Once connected, the adversary can interact with the remote system's desktop and execute commands.
2. Lateral Movement
Adversaries may use VNC to move laterally within a network by logging into other systems and accessing their resources. This could be done using a VNC client by connecting to the IP address and port of the VNC server on the remote system and authenticating with a valid username and password. Once connected, the adversary can interact with the remote system's desktop and potentially move on to other systems.
TrickBot, a modular botnet and banking Trojan, uses a VNC module for remote control and an SMB module for lateral movement in a compromised network [21]. TrickBot also uses VNC to steal credentials by searching for the .vnc.lnk affix [22].
3. Data Exfiltration
Adversaries also use VNC to exfiltrate sensitive data. Mandiant researchers revealed a new URSNIF malware variant dubbed LDR4, a generic backdoor designed to facilitate operations such as data exfiltration [23]. As an essential change from the previous variants of URSNIF, LDR4 includes a VNC module (VncDLL.dll) to connect to a remote C2 server.
4. Malware distribution
Another adversary use case of VNC is malware distribution. In August 2022, Cyble researchers discovered a new malware called MikuBot, which is a malicious bot launching hidden VNC sessions that allow the attacker to remotely access the victim's machine, spread via USB, and download and execute additional malware [24].
T1021.006 Windows Remote Management
Windows Remote Management (WinRM) is a service and protocol that allows users to interact with a remote system, such as running executables, modifying the registry, and modifying services. It can be called using the winrm command or by programs such as PowerShell and is often used as a method of remotely interacting with Windows Management Instrumentation (WMI). While WinRM is a useful tool for remote management, adversaries can abuse WinRM for lateral movement and remote code execution.
Windows Remote Management (WinRM) is a command-line tool and management protocol in Windows that allows administrators to execute commands remotely on other systems using the WS-Management protocol. WinRM uses HTTP or HTTPS to transport and can be configured to use Kerberos authentication for added security.
WinRM is designed to be extensible and can be used with various management technologies, including Windows Management Instrumentation (WMI) and PowerShell. It allows administrators to perform tasks remotely, such as managing services, configuring firewall rules, and modifying the registry.
WinRM can remotely manage systems within an organization, either over a local network or the internet. It is an effective tool for managing large numbers of systems, allowing administrators to perform tasks remotely without physically visiting each system.
WinRM is enabled by default on Windows Server 2008 and later but not on client versions of Windows by default. It can be enabled and configured using the WinRM command-line tool or through Group Policy.
Adversary Use of Windows Remote Management
Windows Remote Management (WinRM) enables administrators to execute commands and manage systems and applications using the WS-Management protocol. WinRM is used to establish communication between a local and a remote system and uses ports 5985 (HTTP transport) and 5986 (HTTPS transport) for communication.
WinRM is a powerful tool that can be used for various tasks, such as running executables, modifying the registry, and modifying services. It can be called using the winrm command or by programs such as PowerShell and is often used as a method of remotely interacting with Windows Management Instrumentation (WMI).
On server and client versions of the Windows operating system, the Enable-PSRemoting cmdlet allows administrators to access the remote shell using PowerShell for private and domain networks through the WinRM service. This allows administrators to remotely execute PowerShell commands and scripts and remotely manage and monitor the system using WMI.
Using WinRM, attackers can use valid accounts to execute commands remotely on multiple systems across the network, allowing them to move laterally within an organization. For example, they could use the following command to execute a script on a target system remotely:
|
winrm -r:<remote_system> -u:<username> -p:<password> "powershell.exe -File C:\path\to\script.ps1" |
Attackers can use WinRM to execute arbitrary code on a target system remotely. For example, they could use the following command to execute a payload on a remote system:
|
winrm -r:<remote_system> -u:<username> -p:<password> "powershell.exe -EncodedCommand <base64_encoded_payload>" |
Attackers can also use WinRM to remotely modify the registry on a target system, allowing them to make changes that persist even after a reboot. For example, they could use the following command to add a new value to the registry:
|
winrm -r:<remote_system> -u:<username> -p:<password> "reg add HKLM\Software\Example /v Key /t REG_SZ /d Value" |
T1021.007 Cloud Services
Cloud services become integral to many organizations' daily operations for managing identities, sharing files, and cooperating with other departments. Popular cloud services such as Azure, AWS, and Google Cloud provide single-sign-on service to many resources in the network allowing users to access them. While these services ease identity management, adversaries may abuse them to access remote resources for malicious operations.
Adversary Use of Cloud Services
As enterprise networks grew, many organizations started using cloud services to manage identities and privileges. While using cloud services for identity management simplified accessing remote resources for users, it also opened up a new attack vector for attackers. Adversaries may access remote services using the compromised hosts' valid accounts and synchronized on-premise identities. After gaining initial access to a host in an enterprise network, adversaries can:
- pivot to cloud environments using compromised users' privileges.
- authenticate to other remote services using cloud services such as single-sign-on.
- execute the malicious payload in a remote system via cloud services.
Adversaries can also access cloud services through the web console or the cloud command line interface (CLI) via compromised users. Accessing cloud services does not require a username and password necessarily; attackers may use Application Access Token [T1550.001] to authenticate to cloud and remote services.
References
[1] H. C. Yuceel, "TTPs used by BlackByte Ransomware Targeting Critical Infrastructure," Feb. 21, 2022. [Online]. Available: https://www.picussecurity.com/resource/ttps-used-by-blackbyte-ransomware-targeting-critical-infrastructure. [Accessed: Dec. 27, 2022]
[2] "Net - Services, File/Print shares, Permissions - Windows CMD - SS64.com." [Online]. Available: https://ss64.com/nt/net.html. [Accessed: Jan. 04, 2023]
[3] "PsExec - Sysinternals." [Online]. Available: https://learn.microsoft.com/en-us/sysinternals/downloads/psexec. [Accessed: Jan. 04, 2023]
[4] "impacket/smbexec.py at master · fortra/impacket," GitHub. [Online]. Available: https://github.com/fortra/impacket. [Accessed: Jan. 04, 2023]
[5] K. Hsu, D. Sangvikar, Z. Zhang, and C. Navarrete, "Lucifer: New Cryptojacking and DDoS Hybrid Malware Exploiting High and Critical Vulnerabilities to Infect Windows Devices," Unit 42, Jun. 24, 2020. [Online]. Available: https://unit42.paloaltonetworks.com/lucifer-new-cryptojacking-and-ddos-hybrid-malware/. [Accessed: Jan. 04, 2023]
[6] "Endpoint Protection." [Online]. Available: http://www.symantec.com/connect/blogs/buckeye-cyberespionage-group-shifts-gaze-us-hong-kong. [Accessed: Jan. 04, 2023]
[7] "[No title]." [Online]. Available: https://cdn2.hubspot.net/hubfs/3354902/Cybereason%20Labs%20Analysis%20Operation%20Cobalt%20Kitty.pdf. [Accessed: Jan. 04, 2023]
[8] "[No title]." [Online]. Available: https://go.crowdstrike.com/rs/281-OBQ-266/images/Report2020CrowdStrikeGlobalThreatReport.pdf. [Accessed: Jan. 04, 2023]
[9] C. Nocturnus, "Cybereason vs. Conti Ransomware." [Online]. Available: https://www.cybereason.com/blog/research/cybereason-vs.-conti-ransomware. [Accessed: Jan. 04, 2023]
[10] "Website." [Online]. Available: https://www.fireeye.com/blog/threat-research/2016/11/fireeye_respondsto.html
[11] "New Orangeworm attack group targets the healthcare sector in the U.S., Europe, and Asia." [Online]. Available: https://www.symantec.com/blogs/threat-intelligence/orangeworm-targets-healthcare-us-europe-asia. [Accessed: Jan. 04, 2023]
[12] D. Alperovitch, "Deep in Thought: Chinese Targeting of National Security Think Tanks," Jul. 07, 2014. [Online]. Available: https://web.archive.org/web/20200424075623/https://www.crowdstrike.com/blog/deep-thought-chinese-targeting-national-security-think-tanks/. [Accessed: Jan. 04, 2023]
[13] "Website." [Online]. Available: https://www.symantec.com/content/en/us/enterprise/media/security_response/whitepapers/w32_duqu_the_precursor_to_the_next_stuxnet.pdf
[14] ESET Research, "IsaacWiper and HermeticWizard: New wiper and worm targeting Ukraine," WeLiveSecurity, Mar. 01, 2022. [Online]. Available: https://www.welivesecurity.com/2022/03/01/isaacwiper-hermeticwizard-wiper-worm-targeting-ukraine/. [Accessed: Jan. 04, 2023]
[15] Microsoft Security Threat Intelligence, "New 'Prestige' ransomware impacts organizations in Ukraine and Poland," Microsoft Security Blog, Oct. 14, 2022. [Online]. Available: https://www.microsoft.com/en-us/security/blog/2022/10/14/new-prestige-ransomware-impacts-organizations-in-ukraine-and-poland/. [Accessed: Jan. 03, 2023]
[16] "BumbleBee Roasts Its Way to Domain Admin," The DFIR Report, Aug. 08, 2022. [Online]. Available: https://thedfirreport.com/2022/08/08/bumblebee-roasts-its-way-to-domain-admin/. [Accessed: Jan. 03, 2023]
[17] "Iranian Government-Sponsored Actors Conduct Cyber Operations Against Global Government and Commercial Networks." [Online]. Available: https://www.cisa.gov/uscert/ncas/alerts/aa22-055a. [Accessed: Jan. 03, 2023]
[18] "Website." [Online]. Available: https://www.akamai.com/blog/security-research/new-p2p-botnet-panchan
[19] J. Salvio and R. Tay, "So RapperBot, What Ya Bruting For?," Fortinet Blog, Aug. 03, 2022. [Online]. Available: https://www.fortinet.com/blog/threat-research/rapperbot-malware-discovery. [Accessed: Jan. 05, 2023]
[20] "#StopRansomware: Daixin Team." [Online]. Available: https://www.cisa.gov/uscert/ncas/alerts/aa22-294a. [Accessed: Jan. 05, 2023]
[21] R. Morris-Reade, "Trickbot overtakes Formbook as most prevalent malware," SecurityBrief New Zealand, Jan. 14, 2022. [Online]. Available: https://securitybrief.co.nz/story/trickbot-overtakes-formbook-as-most-prevalent-malware. [Accessed: Jan. 04, 2023]
[22] C. Stewart, "Trickbot Malware Review," Chris Stewart - Cybersecurity News, Mar. 25, 2022. [Online]. Available: https://www.chrisstewart.ca/1655-2/. [Accessed: Jan. 04, 2023]
[23] "From RM3 to LDR4: URSNIF Leaves Banking Fraud Behind," Mandiant, Oct. 03, 2021. [Online]. Available: https://www.mandiant.com/resources/blog/rm3-ldr4-ursnif-banking-fraud. [Accessed: Jan. 04, 2023]
[24] "MikuBot Spotted In The Wild," Cyble, Aug. 11, 2022. [Online]. Available: https://blog.cyble.com/2022/08/11/mikubot-spotted-in-the-wild/. [Accessed: Jan. 04, 2023]


.png?width=353&height=200&name=Ni8mare-ET-preview-oct25%20(1).png)







