Securing macOS: A Closer Look At Built-In macOS Application Security
In an increasingly connected world, the security of our digital lives has become more critical than ever. As users rely heavily on their computers for work, personal communication, and handling sensitive information, the need for a secure operating system is paramount.
While macOS is widely regarded for its user-friendly nature, it's important to acknowledge that no operating system is immune to security threats. From malware and phishing attacks to data breaches and unauthorized access, macOS users must be vigilant and proactive in safeguarding their systems and personal information.
In this research, we'll take a closer look at the world of macOS security. We will shed light on the various layers of protection offered by Apple.
Simulate macOS Endpoint Attacks with Picus Platform
Built-In macOS Application Security
When it comes to protecting macOS-powered devices, Apple has implemented a range of robust security measures that often go unnoticed.
macOS takes a multi-faceted approach to safeguarding its system against potential threats from Internet-downloaded applications. It integrates a variety of protective measures to ensure that such apps are free from known malware. By leveraging advanced technologies, macOS not only detects and eliminates malware but also establishes additional barriers to prevent untrusted apps from compromising user data.
Transparency, Consent, and Control - TCC
Transparency, Consent, and Control (TCC) is a fundamental aspect of privacy and security in modern digital ecosystems. It refers to a set of mechanisms and practices designed to provide users with clear visibility and control over the permissions and access rights granted to applications and services on their devices.
In macOS, TCC serves as a crucial component of privacy protection by offering users the ability to manage which applications have access to sensitive data and system resources. This includes permissions for accessing location data, contacts, calendars, microphones, cameras, and more. By allowing users to review and modify these permissions, macOS ensures that individuals have granular control over their personal information.
The transparency aspect of TCC ensures that users are fully informed about the data an application requests and the specific purpose for which it is required. When an application attempts to access sensitive data for the first time, macOS displays a consent prompt, clearly stating the information being requested and the purpose it will serve. This transparency empowers users to make informed decisions about granting or denying access.
Figure 1: TCC Warning
Under System Preferences > Privacy & Security, users can see which applications have permissions to which services.
Figure 2: Giving Full Disk Access to Terminal
TCC Database
TCC is an SQLite database, and this database is located in /Library/Application\ Support/com.apple.TCC/TCC.db. The following command allows users to view the System TCC database.
|
sqlite3 /Library/Application\ Support/com.apple.TCC/TCC.db |
The TCC database includes the following tables.
- access
- access_overrides
- active_policy admin
- expired
- policies
|
➜ ~ sqlite3 /Library/Application\ Support/com.apple.TCC/TCC.db SQLite version 3.37.0 2021-12-09 01:34:53 Enter ".help" for usage hints. sqlite> .tables access active_policy expired access_overrides admin policies |
Example 1: TCC.db tables
The database also allows users to view System applications and TCC permissions.
|
sqlite> select client, auth_reason, auth_value, service from access; us.zoom.xos|5|0|kTCCServiceSystemPolicyAllFiles com.logitech.Logi-Options|4|2|kTCCServiceAccessibility com.logitech.manager.daemon|4|2|kTCCServiceAccessibility com.logitech.manager.daemon|4|2|kTCCServiceListenEvent us.zoom.xos|4|0|kTCCServiceAccessibility us.zoom.xos|4|2|kTCCServiceScreenCapture /usr/libexec/sshd-keygen-wrapper|4|0|kTCCServiceSystemPolicyAllFiles com.apple.screensharing.agent|4|0|kTCCServicePostEvent com.apple.screensharing.agent|4|0|kTCCServiceScreenCapture /System/Library/Frameworks/CoreServices.framework/Versions/A/Frameworks/AE.framework/Versions/A/Support/AEServer|4|0|kTCCServiceAccessibility com.apple.Terminal|4|2|kTCCServiceSystemPolicyAllFiles |
Example 2: TCC system app accesses
File Quarantine
File Quarantine is the predecessor of Gatekeeper and was introduced with OS X Leopard (10.5). With the File Quarantine feature, the extended attribute-(XA) com.apple.quarantine attribute is added to the files downloaded from the Internet.
File Quarantine is designed to notify users when an application downloaded from the Internet is run for the first time.
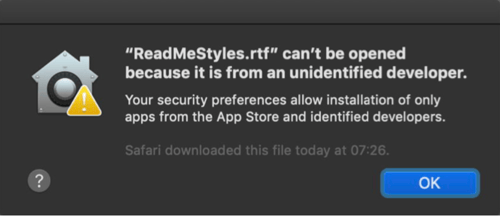
Figure 3: File Quarantine Warning
The warning above is triggered when trying to open files with the com.apple.quarantine extended attribute. Files that have @ at the end of their permissions flags have extended attributes.
|
➜ tools ls -l
total 1632 |
The xattr utility allows users to view a file's extended attributes.
|
xattr CleanMyMacX.dmg com.apple.macl com.apple.metadata:kMDItemWhereFroms com.apple.quarantine |
Example 3: Extended attributes of a downloaded file
The xattr -p command is used to display extended attribute values.
|
xattr -p com.apple.quarantine CleanMyMacX.dmg 0081;64c3bf9d;Firefox;01EB78B6-2EB3-48BF-808B-B8D50B4AEE8C |
Example 4: com.apple.quarantine extended attributes of a downloaded file
Extended Attribute - com.apple.quarantine
The structure of the values in com.apple.quarantine is given in Figure 4.
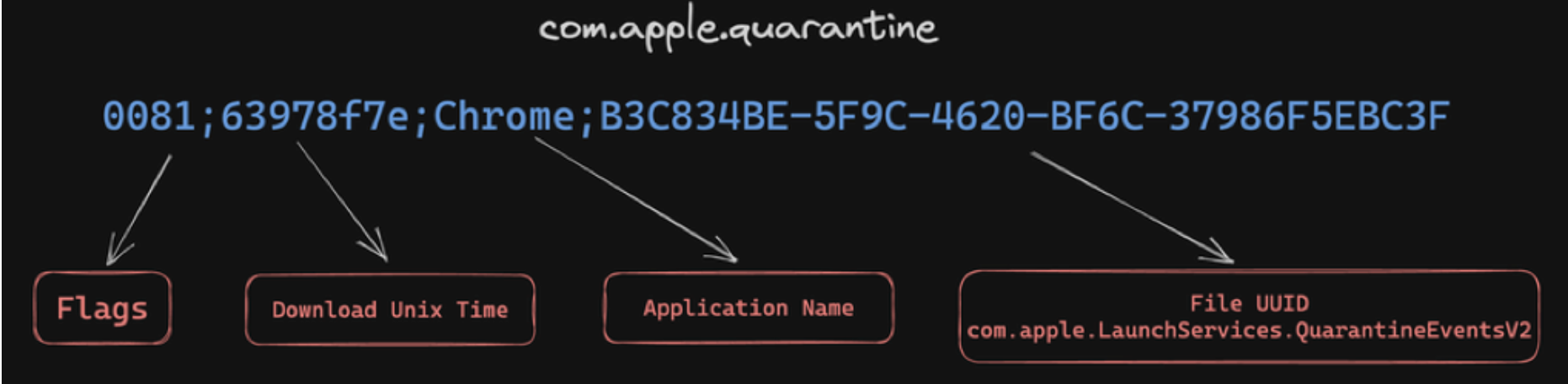
Figure 4: The structure of com.apple.quarantine extended attributes
QuarantineEventsV2 Database - com.apple.quarantine
All flag information of the com.apple.quarantine attribute is available in the com.apple.LaunchServices.QuarantineEventsV2 SQLite database. The database is located at ~/Library/Preferences/com.apple.LaunchServices.QuarantineEventsV2.
|
➜ ~ sqlite3 ~/Library/Preferences/com.apple.LaunchServices.QuarantineEventsV2 SQLite version 3.37.0 2021-12-09 01:34:53 Enter ".help" for usage hints.
sqlite> .schema CREATE TABLE LSQuarantineEvent ( LSQuarantineEventIdentifier TEXT PRIMARY KEY NOT NULL, LSQuarantineTimeStamp REAL, LSQuarantineAgentBundleIdentifier TEXT, LSQuarantineAgentName TEXT, LSQuarantineDataURLString TEXT, LSQuarantineSenderName TEXT, LSQuarantineSenderAddress TEXT, LSQuarantineTypeNumber INTEGER, LSQuarantineOriginTitle TEXT, LSQuarantineOriginURLString TEXT, LSQuarantineOriginAlias BLOB ); CREATE INDEX LSQuarantineEventIndex ON LSQuarantineEvent ( LSQuarantineEventIdentifier ); CREATE INDEX LSQuarantineTimeStampIndex ON LSQuarantineEvent ( LSQuarantineTimeStamp );
sqlite> .tables LSQuarantineEvent |
Example 5: QuarantineEventsV2 database
The following SQL command can be used to display the values in the LSQuarantineEvent.
|
sqlite> select * from LSQuarantineEvent; 87A946DE-B399-4050-A8D0-AA8B367CA73F|712139861.371294|com.apple.Safari|Safari||||0||| 71BA058F-EE40-4E4A-8F1F-1024F431D0F1|712140006.612305|com.apple.Safari|Safari||||0||| F208738B-7B2B-43D5-B899-D8ABCC2D9A4D|712150977.27626|com.apple.Safari|Safari||||0||| 47EB09C4-930B-4855-BD97-D2F5C959F99B|712151493.15678|com.apple.Safari|Safari||||0||| 1BE1FD13-B935-45C6-89E4-B7C4BDC9A02E|712167224.613103|com.apple.Safari|Safari||||0||| 98E55B99-2A5B-4F21-953F-E9B3AE82034C|712171029.575085|com.apple.Safari|Safari||||0||| 8652C19B-A44B-4A3D-AE4D-42099459743A|712171234.319902|com.apple.Safari|Safari||||0||| 01EB78B6-2EB3-48BF-808B-B8D50B4AEE8C|712242961.0|org.mozilla.firefox|Firefox||||0||| |
Example 6: Contents of LSQuarantineEvent
LSQuarantineEvent Table
The LSQuarantineEvent table includes the following columns. The structure of the values in the table is given in Figure 5.
- LSQuarantineEventIdentifier
- LSQuarantineTimeStamp
- LSQuarantineAgentBundleIdentifier
- LSQuarantineAgentName
- LSQuarantineDataURLString
- LSQuarantineSenderName
- LSQuarantineSenderAddress
- LSQuarantineTypeNumber
- LSQuarantineOriginTitle
- LSQuarantineOriginURLString
- LSQuarantineOriginAlias
Figure 5: LSQuarantineEvent table analysis
Gatekeeper
Gatekeeper is a built-in security technology designed to run trusted software on macOS. When downloading an application from the Internet outside the AppStore and opening that application, Gatekeeper confirms that the application comes from the identified developer and is known to Apple (notarization).
Figure 6: Gatekeeper Warning
The operations of the Gatekeeper service are performed at the system level by spctl - SecAssessment system policy security macOS binary.
The spctl command is used to check whether an application is signed and notarized. The command returns either "accepted" or "rejected", depending on the Gatekeeper's evaluation.
|
➜ ~ spctl --verbose=4 --assess --type execute /Applications/Hopper\ Disassembler\ v4.app /Applications/Hopper\ Disassembler\ v4.app: accepted source=Notarized Developer ID |
Example 7: spctl - notarization and signed information
|
|
The main difference between Gatekeeper and File Quarantine is the signature check. File Quarantine does not perform signature checks. |
Figure 7: Gatekeeper Warning
Gatekeeper Database
Gatekeeper performs the controls from its own database, and it keeps a blocklist for applications. The Gatekeeper's database is in SQLite format and is located at /Library/Apple/System/Library/CoreServices/XProtect.bundle/Contents/Resources/gk.db.
|
➜ ~ sqlite3 /Library/Apple/System/Library/CoreServices/XProtect.bundle/Contents/Resources/gk.db SQLite version 3.37.0 2021-12-09 01:34:53 Enter ".help" for usage hints.
sqlite> .schema CREATE TABLE settings (name TEXT, value TEXT, PRIMARY KEY (name)); CREATE TABLE blocked_hashes (hash BLOB, hash_type INTEGER, flags INTEGER, PRIMARY KEY (hash, hash_type)); CREATE TABLE blocked_teams (team_id TEXT, flags INTEGER, PRIMARY KEY (team_id));
sqlite> .table blocked_hashes blocked_teams settings |
Example 8: Gatekeeper's database - gk.db
The following SQL command can be used to display the IDs in blocked_teams table.
|
sqlite> select * from blocked_teams LIMIT 10; F9X83Q5222|1 SS3YFP6RJ7|0 QC8B2PF82S|0 UQ5TUCT7AL|0 NZD5N78GXM|0 Q6XAB4776L|0 GQ65ME5KV3|0 8CHL2NLV6W|0 7698FPNAVX|0 DB6GMRL6AQ|0 |
Example 9: blocked team IDs in gk.db
Malware Detection - XProtect.bundle
macOS has a built-in security tool called XProtect that provides signature-based detection. XProtect performs malware detection using YARA signatures. YARA rules are regularly updated by Apple.
XProtect performs a continuous security scan of the macOS system, including in the following cases.
- Launch a downloaded app for the first time
- Change an app in the file system
- XProtect signatures are updated
|
|
XProtect is included in File Quarantine technology. |
When an application downloaded from the Internet using an application sensitive to File Quarantine technology is opened, A warning appears in front of the user that the application is downloaded from the Internet (Gatekeeper).
When this application downloaded from the Internet is run, File Quarantine technology checks whether the relevant application matches any of the signatures in XProtect. If there is a match, another warning is displayed saying that running the application may harm the system (File Quarantine).
XProtect checks application files and file hashes against these signatures when the application is first launched or whenever it changes. When XProtect detects a matching signature, it prevents the relevant code from running, and the user is informed of the option to delete the relevant application (Gatekeeper).
Figure 8: XProtect Warning
XProtect Files
XProtect is included in macOS in .bundle format. XProtect files are located at /Library/Apple/System/Library/CoreServices/XProtect.bundle.
|
➜ ~ tree XProtect.bundle XProtect.bundle └── Contents ├── Info.plist ├── Resources │ ├── LegacyEntitlementAllowlist.plist │ ├── XProtect.meta.plist │ ├── XProtect.plist │ ├── XProtect.yara │ └── gk.db ├── _CodeSignature │ ├── CodeDirectory │ ├── CodeRequirements │ ├── CodeRequirements-1 │ ├── CodeResources │ └── CodeSignature └── version.plist 4 directories, 12 files |
Example 10: Contents of XProtect.bundle folder
XProtect.yara: This file contains Apple's built-in YARA rules.
|
import "hash" …redacted… |
Example 11: Contents of XProtect.yara
XProtect.meta.plist: This .plist file contains information about malicious application plugins (Java, Flash, etc.) and harmful Safari extensions. Extension block definitions are made according to the bundle identifier and related Developer ID information.
|
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>ExtensionBlacklist</key> <dict> <key>Extensions</key> <array> <dict> <key>CFBundleIdentifier</key> <string>com.searchnt.safari</string> <key>Developer Identifier</key> <string>6ERPEMNB65</string> </dict> <dict> <key>CFBundleIdentifier</key> <string>com.shelfsick.safari</string> <key>Developer Identifier</key> <string>33HGJH7H8P</string> </dict> <dict> <key>CFBundleIdentifier</key> <string>com.searchnt.safari</string> <key>Developer Identifier</key> <string>LUZSN84HYP</string> </dict> …redacted… |
Example 12: Contents of XProtect.meta.plist
XProtect.plist: This .plist file contains information about the application bundle and the harmful content in it. As an example, the content of the OSX.28a9883 signature name in XProtect.plist is given below.
|
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <array> <dict> <key>Description</key> <string>OSX.28a9883</string> <key>LaunchServices</key> <dict> <key>LSItemContentType</key> <string>com.apple.application-bundle</string> </dict> <key>Matches</key> <array> <dict> <key>MatchFile</key> <dict> <key>NSURLTypeIdentifierKey</key> <string>public.unix-executable</string> </dict> <key>MatchType</key> <string>Match</string> <key>Pattern</key> <string>3A6C6162656C3A706C697374506174683A</string> </dict> <dict> <key>MatchFile</key> <dict> <key>NSURLTypeIdentifierKey</key> <string>public.unix-executable</string> </dict> <key>MatchType</key> <string>Match</string> <key>Pattern</key> <string>3A62696E3A706C6973743A</string> </dict> <dict> <key>MatchFile</key> <dict> <key>NSURLTypeIdentifierKey</key> <string>public.unix-executable</string> </dict> <key>MatchType</key> <string>Match</string> <key>Pattern</key> <string>214023247E5E262A28295B5D7B7D3A3B3C3E2C2E31713277336534723574367937753869396F3070415A5358444346564742484E4A4D4B4C5157455254595549</string> </dict> </array> </dict> …redacted… |
Example 13: Contents ofXProtect.plist
The "string" values in the "pattern" keys can be analyzed by converting them to ASCII format as follows. These patterns are searched by XProtect for each signature in the plist file.
|
Hex Value Stored in the Pattern Key |
Converted to ASCII |
|
3A6C6162656C3A706C697374506174683A |
:label:plistPath: |
|
3A62696E3A706C6973743A |
:bin:plist: |
|
214023247E5E262A28295B5D7B7D3A3B3C3E2C2E31713277336534723574367937753869396F3070415A5358444346564742484E4A4D4B4C5157455254595549 |
!@#$~^&*()[]{}:;<>,.1q2w3e4r5t6y7u8i9o0pAZSXDCFVGBHNJMKLQWERTYUI |
LegacyEntitlementAllowlist.plist: This plist file is undocumented by Apple.
It is seen that only cdhash information is included in the plist. Detailed information about cdhash can be found in Apple documentation.
cdhash: The code directory hash identifies a specific version of a program. This allows the system to verify that the contents of a binary have not changed since being code-signed.
|
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>cdhashes</key> <array> <data> AAFd7LJtQHNzgvxZ5kOMf5kNDVo= </data> <data> AAQCJMThA3BGcNrYDj3cGpx+i3U= </data> …redacted… |
Example 14: Contents of LegacyEntitlementAllowlist.plist
XProtect Unified Logs: An example of unified logs of XProtect Remediator events are given below.
|
➜ ~ log show -info -backtrace -debug -loss -signpost -predicate 'subsystem == "com.apple.xprotect"' Filtering the log data using "subsystem == "com.apple.xprotect"" Timestamp Thread Type Activity PID TTL 2023-07-24 10:03:23.070580+0300 0x3f1a Default 0x0 1387 0 XprotectService: [com.apple.xprotect:xprotect] Using meta-plist from: /Library/Apple/System/Library/CoreServices/XProtect.bundle/Contents/Resources/XProtect.meta.plist 2023-07-25 19:19:22.509786+0300 0x52629 Default 0x0 4602 0 XprotectService: [com.apple.xprotect:xprotect] Using meta-plist from: /Library/Apple/System/Library/CoreServices/XProtect.bundle/Contents/Resources/XProtect.meta.plist …redacted… |
Example 15: XProtect unified logs
Malware Removal Tool - MRT
MRT is another built-in anti-malware tool for macOS which is available on macOS 10.8.3 and higher versions. When it is infected with malware, the macOS system is cleaned with MRT. MRT checks the malware database regularly updated by Apple and removes infections. Similar to XProtect, MRT is activated automatically at system startup. MRT is located at /Library/Apple/System/Library/CoreServices/MRT.app.
|
➜ ~ tree MRT.app MRT.app └── Contents ├── Frameworks │ ├── libswiftAppKit.dylib │ ├── libswiftCore.dylib │ ├── libswiftCoreData.dylib │ ├── libswiftCoreFoundation.dylib │ ├── libswiftCoreGraphics.dylib │ ├── libswiftCoreImage.dylib │ ├── libswiftDarwin.dylib │ ├── libswiftDispatch.dylib │ ├── libswiftFoundation.dylib │ ├── libswiftIOKit.dylib │ ├── libswiftMetal.dylib │ ├── libswiftObjectiveC.dylib │ ├── libswiftQuartzCore.dylib │ ├── libswiftXPC.dylib │ └── libswiftos.dylib ├── Info.plist ├── MacOS │ ├── MRT │ └── mrt-helper ├── PkgInfo ├── Resources │ ├── Info.plist │ ├── ar.lproj …redacted… 42 directories, 95 files |
Example 16: Contents of MRT.app folder
When the MRT binary is analyzed, data related to different malware types are seen.
Figure 9: MRT binary
For example, when the data of the Mughtesec malware is examined, it is understood that the MRT application keeps behavioral patterns of the malicious software and detects the malware by comparing the activities in the system with these patterns.
Figure 10: Mughtesec malware family
|
|
MRT is retired from macOS and is being replaced by XProtect Remediator. |
XProtect Remediator - XProtect.app
With the release of macOS 12.3, Apple also released a new macOS tool called XProtect Remediator (XPR). XProtect Remediator is reminiscent of MRT in the sense that it is an application package, but it contains different binaries for different malware.
|
➜ ~ tree XProtect.app XProtect.app └── Contents ├── Info.plist ├── MacOS │ ├── XProtect │ ├── XProtectRemediatorAdload │ ├── XProtectRemediatorBadGacha │ ├── XProtectRemediatorColdSnap │ ├── XProtectRemediatorDubRobber │ ├── XProtectRemediatorEicar │ ├── XProtectRemediatorFloppyFlipper │ ├── XProtectRemediatorGenieo │ ├── XProtectRemediatorGreenAcre │ ├── XProtectRemediatorKeySteal │ ├── XProtectRemediatorMRTv3 │ ├── XProtectRemediatorPirrit │ ├── XProtectRemediatorRankStank │ ├── XProtectRemediatorRoachFlight │ ├── XProtectRemediatorSheepSwap │ ├── XProtectRemediatorSnowBeagle │ ├── XProtectRemediatorSnowDrift │ ├── XProtectRemediatorToyDrop │ ├── XProtectRemediatorTrovi │ └── XProtectRemediatorWaterNet ├── PkgInfo ├── Resources │ ├── com.apple.XProtect.agent.scan.plist │ ├── com.apple.XProtect.agent.scan.startup.plist │ ├── com.apple.XProtect.daemon.scan.plist │ ├── com.apple.XProtect.daemon.scan.startup.plist │ ├── com.apple.XprotectFramework.PluginService.plist │ └── libXProtectPayloads.dylib ├── XPCServices │ └── XProtectPluginService.xpc │ └── Contents │ ├── Info.plist │ ├── MacOS │ │ └── XProtectPluginService │ ├── _CodeSignature │ │ └── CodeResources │ └── version.plist ├── _CodeSignature │ └── CodeResources └── version.plist 10 directories, 34 files |
Example 17: Contents of XProtect.app folder
Different binaries for different malware are in XProtectRemediator<FAMILY_NAME> format. The main differences between MRT and XProtect Remediator are as follows.
- MRT only works during the reboot and login phases.
- XProtect Remediator scans at regular intervals.
Unified logs of XProtect Remediator events can be examined as follows.
When the logs are examined, it is seen that the binaries in XProtect Remediator are scanned regularly.
|
➜ ~ log show -info -backtrace -debug -loss -signpost -predicate 'subsystem == "com.apple.XProtectFramework.PluginAPI" && category == "XPEvent. Structured"' Filtering the log data using "subsystem == "com.apple.XProtectFramework.PluginAPI" AND category == "XPEvent.structured"" 2023-07-25 12:09:44.806791+0300 0xaafd07 Default 0x0 24150 0 XProtectRemediatorTrovi: [com.apple.XProtectFramework.PluginAPI:XPEvent.structured] {"caused_by":[],"status_message":"NoThreatDetected","status_code":20,"execution_duration":9.1910362243652344e-05} …redacted… |
Example 18: XProtect Remediator unified logs
Malware Response in Apple
When new malware is discovered, the following steps are taken.
- Any associated Developer ID certificates are revoked.
- Notarization revocation tickets are issued for all files (apps and associated files).
- XProtect signatures are developed and released.
Behavioral Detection - BastionRules
Apple has released a new XProtect module with macOS Ventura. With this module, it is seen that XProtect has a behavioral detection feature. The SQLite database file of this module is located at /var/protected/xprotect/XPdb.
Figure 11: XPdb
An example rule structure and information in the events table is as follows.
Figure 12: XPdb BastionRules
XPdb and XProtect activities, in general, are handled by the System Configuration Policy Daemon - syspolicyd.
When the syspolicyd binary is analyzed, the registerBastionProfile function is seen in the SandboxManager class. The retain array draws attention to this function.
Figure 13: XPdb - retain
When the offset is analyzed, the following data can be seen.
Figure 14: syspolicyd - retain array
The edited version of the data in aNversion3nnall is as follows.
|
(version 3) (allow default job-creation file-write-setugid) (define (system-binary signing-id) (require-all (process-attribute is-platform-binary))) (define bastion-usual-offenders (system-binary \"com.apple.fseventsd\") (system-binary \"com.apple.MRT\") (system-binary \"com.apple.mdworker_shared\") (system-binary \"com.apple.jetsam_priority\") (system-binary \"com.apple.diskarbitrationd\") (system-binary \"com.apple.StorageManagement.Service\") (system-binary \"com.apple.dt.IDECacheDeleteAppExtension\") (system-binary \"com.apple.STMExtension.Applications\") (system-binary \"com.apple.StorageManagement.Service\") (system-binary \"com.apple.coreservices.uiagent\") (system-binary \"com.apple.imdpersistence.IMDPersistenceAgent\"))) (define rule-one-offenders (require-any (system-binary \"com.apple.Safari.PasswordBreachAgent\") (system-binary \"com.apple.Safari.History\") (system-binary \"com.apple.Safari.CacheDeleteExtension\") (system-binary \"com.apple.Finder\") (system-binary \"com.apple.SafariBookmarksSyncAgent\") (system-binary \"com.apple.UserEventAgent\") (system-binary \"com.apple.appkit.xpc.openAndSavePanelService\") (system-binary \"com.apple.SafariNotificationAgent\") (system-binary \"com.apple.dt.SKAgent\") (system-binary \"com.apple.backupd\") (system-binary \"com.apple.STMExtension.Developer\") (system-binary \"com.apple.STMExtension.Mail\") (system-binary \"com.apple.Safari\"))) (define rule-two-offenders (require-any (system-binary \"com.apple.suggestd\") (system-binary \"com.apple.IMAutomaticHistoryDeletionAgent\") (system-binary \"com.apple.MobileSMS\") (system-binary \"com.apple.MobileSMS.spotlight\") (system-binary \"com.apple.photolibraryd\") (system-binary \"com.apple.Spotlight\") (system-binary \"com.apple.coreduetd\") (system-binary \"com.apple.filecoordinationd\") (system-binary \"com.apple.Safari.SandboxBroker\") (system-binary \"com.apple.quicklook.ThumbnailsAgent\") (system-binary \"com.apple.messages.StorageManagementExtension\") (system-binary \"com.apple.corespotlightd\") (system-binary \"com.apple.mdwrite\"))) (define rule-three-offenders (require-any (system-binary \"com.apple.Safari\") (system-binary \"com.apple.cfprefsd\") (system-binary \"com.apple.mail\") (system-binary \"com.apple.lsd\") (system-binary \"com.apple.sharingd\") (system-binary \"com.apple.dataaccess.dataaccessd\") (system-binary \"com.apple.defaults\"))) (with-filter (require-not (require-any bastion-usual-offenders rule-one-offenders)) (allow (with user-approval \"BastionRule-1\") file* (subpath \"${ANY_USER_HOME}/Library/Application Support/Google/Chrome/Default/\")) (allow (with user-approval \"BastionRule-1\") file* (subpath \"${ANY_USER_HOME}/Library/Application Support/Firefox/Profiles/\")) (allow (with user-approval \"BastionRule-1\") file* (subpath \"${ANY_USER_HOME}/Library/Safari/\"))) (with-filter (require-not (require-any bastion-usual-offenders rule-two-offenders)) (allow (with user-approval \"BastionRule-2\") file* (subpath \"${ANY_USER_HOME}/Library/Messages/\")) (allow (with user-approval \"BastionRule-2\") file* (subpath \"${ANY_USER_HOME}/Library/Application Support/Microsoft/Teams/\")) (allow (with user-approval \"BastionRule-2\") file* (subpath \"${ANY_USER_HOME}/Library/Application Support/Slack/\")) (allow (with user-approval \"BastionRule-2\") file* (subpath \"${ANY_USER_HOME}/Library/Application Support/WhatsApp/\"))) (with-filter (require-not (require-any bastion-usual-offenders rule-three-offenders)) (allow (with user-approval \"BastionRule-3\") file* (literal \"${ANY_USER_HOME}/Library/Preferences/com.apple.LaunchServices.QuarantineEventsV2\"))) (with-filter (require-not (process-attribute is-platform-binary)) (allow (with user-approval \"BastionRule-4\") socket-ioctl (ioctl-command SIOCIFCREATE SIOCGIFDESC))) |
When these data are analyzed, it is understood that Bastion rules are the working mechanism.
It sets up four filters using the with-filter construct to control access permissions based on specific conditions:
-
The first filter, BastionRule-1, restricts file access to specific subpaths within Chrome, Firefox, and Safari application support directories, but only if the accessed binary is not part of either bastion-usual-offenders or rule-one-offenders.
-
The second filter, BastionRule-2, allows access to subpaths within Messages, Microsoft Teams, Slack, and WhatsApp application support directories, but only if the accessed binary is not part of either bastion-usual-offenders or rule-two-offenders.
-
The third filter, BastionRule-3, grants access to a specific file ( com.apple.LaunchServices.QuarantineEventsV2 ) in the user's preferences directory ( Library/Preferences/ ) but only if the accessed binary is not part of either bastion-usual-offenders or rule-three-offenders.
-
The fourth filter, BastionRule-4, allows access to a specific socket ioctl command ( SIOCIFCREATE and SIOCGIFDESC ), but only if the process attribute is-platform-binary is not satisfied.
There are four types of Bastion rules. For example, with the BastionRule-1 type rule, it is understood that the application movements in the ~/Library/Application Support/ directory are followed.
|
|
In macOS Ventura, these behaviors are not blocked; they are saved in the XPdb database. |
Conclusion
macOS has many built-in security features that provide good security for the average user. With regular updates and responsible user practices, macOS is a great option for everyday use.
For those who are looking for a more secure, safe, and reliable computing experience, learning the details of Apple's security utilities is a great way to safeguard user data and privacy. Understanding long-standing applications such as File Quarantine and Gatekeeper and new features such as XProtect Remediator would help users and security professionals attain a higher level of security.








