Purple Team Automation with Breach and Attack Simulation (BAS)
Learn how Breach and Attack Simulation (BAS) platforms enable red teams and blue teams to automate purple teaming with four use cases.
Learn how Breach and Attack Simulation (BAS) platforms enable red teams and blue teams to automate purple teaming with four use cases.
Dr. Suleyman Ozarslan
May 9, 2022
Purple Teaming practices have become more popular and widely adopted among security teams. The improved efficiency and effectiveness of red and blue teams and enhanced security posture justify this trend. Although it benefits organizations' cyber defense capabilities, most organizations may not have the required resources for purple teaming. As a solution for many problems in the modern age, automation helps security teams with limited resources to adopt purple teaming with much less effort. This blog explains how Breach and Attack Simulation (BAS) helps automate purple teaming for four different use cases.
On-Demand Webinar: How to Empower Purple Teaming with the MITRE ATT&CK® Framework
In our previous blog, we explain four use cases that require a high level of cooperation and collaboration between red and blue teams - the purple teaming approach. These use cases are:
1) Threat Intelligence: Security teams must track the cyber threat landscape and prepare for potential cyber threats.
2) Adversary Emulation: Red teams must test their organization’s security controls using adversary techniques. The goals of these emulations are assessing the organization’s security posture and identifying gaps in the organization’s defenses. Adversary emulation results are shared with the blue team for purple teaming.
3) Gap Analysis: Blue teams utilize threat intelligence and adversary emulation results to analyze prevention and detection coverage of their defenses for adversary techniques. This assessment is called security gap analysis, and it helps both red and blue teams decide where they should focus their efforts.
4) Detection & Mitigation: The primary goal of purple teaming is improving the organization’s security posture and cyber resilience by detecting and preventing cyberattacks.
Implementing the above use cases for purple teaming is challenging for security teams because of the following reasons:
Limited Time and Resources: Simulating hundreds of adversary TTPs by red teams is a time-consuming and resource-intensive process. On top of that, the cyber threat landscape changes constantly and requires a fast response from threat intelligence (TI), red, and blue teams. These limitations pose challenges to organizations that need trained and skilled individuals to manage continuous improvement-based processes and a high level of coordination between multiple teams such as red, blue, and TI teams.
Prioritizing Gaps and Adversary TTPs: Complete coverage of adversary TTPs or MITRE ATT&CK techniques is not realistic or pragmatic for security teams. Therefore, red and blue teams need to prioritize TTPs and gaps found in preventing and detecting these TTPs.
Developing Actionable Mitigation and Detection Strategies: Although some resources provide generic mitigation and detection recommendations, they cannot be directly implemented in security controls most of the time.
Free Course: The Beginner's Guide to Breach and Attack Simulation Course
Breach and Attack Simulation (BAS) provides automated security posture assessment through continuous and consistent simulation of real-world threats. BAS analyzes, assesses, and reports the performance of security controls round the clock and on-demand. As a result, BAS creates a common platform for both red and blue teams to use for purple teaming.
Let’s see how Breach and Attack Simulation helps security teams to automate purple teaming in all four use cases.
Breach and Attack Simulation provides extensive, actionable threat intelligence for security teams. A BAS solution enables threat profiling to provide relevant threats to your organization's industry and location. Security teams can use this information to decide which threats they should focus on during a purple teaming exercise.
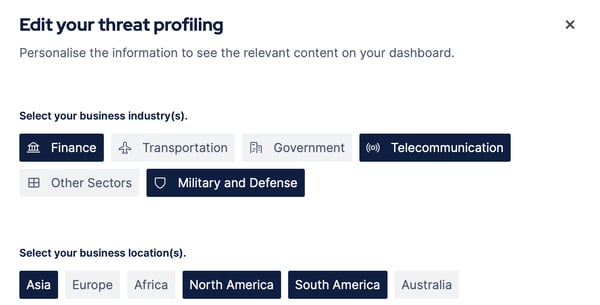
Figure 1: Threat profiling
Breach and Attack Simulation tools also keep track of emerging threats and inform security teams swiftly.
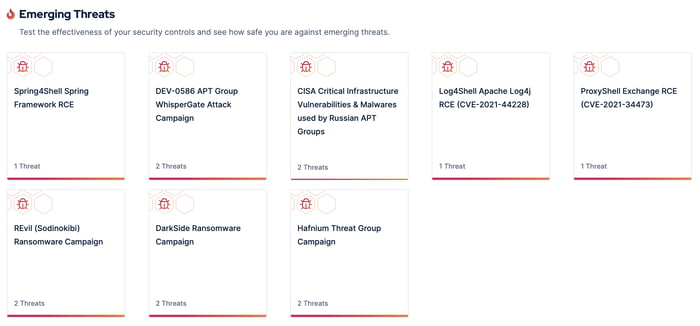
Figure 2: Threat intelligence on emerging threats
Since the threat intelligence provided by a BAS tool also includes actionable mitigation recommendations, security teams can utilize the intel quickly. Therefore, Breach and Attack Simulation provides prioritized and actionable threat intelligence for your organization.
Breach and Attack Simulation provides automated, end-to-end, and ready-to-use adversary emulations for purple teaming. These emulations can test the entire defense infrastructure, including endpoint, network, and email security controls. Since adversary emulations are automated, security teams can focus on the results of the emulations instead of developing and running them.
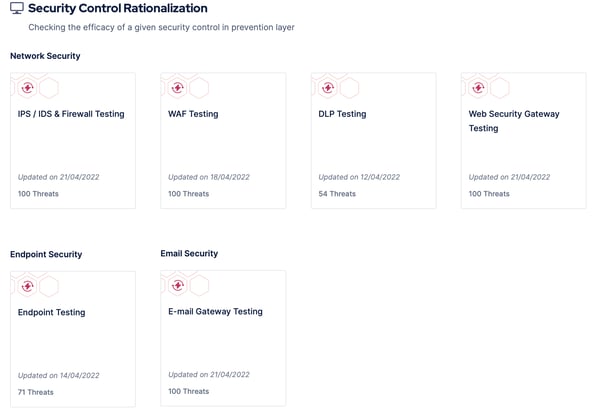
Figure 3: Adversary emulation for security control devices
BAS platforms provide predefined adversary scenarios to test their security posture, as shown in the below figure:
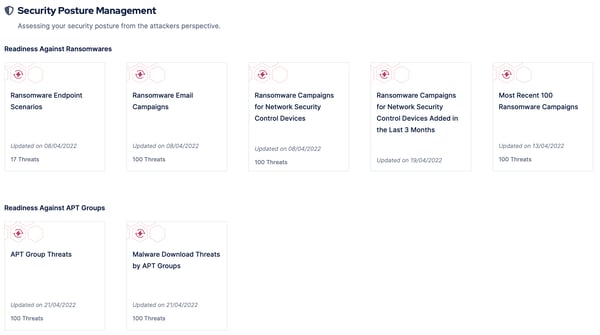
Figure 4: Predefined adversary scenarios
Breach and Attack Simulation platforms also allow security teams to create custom scenarios:
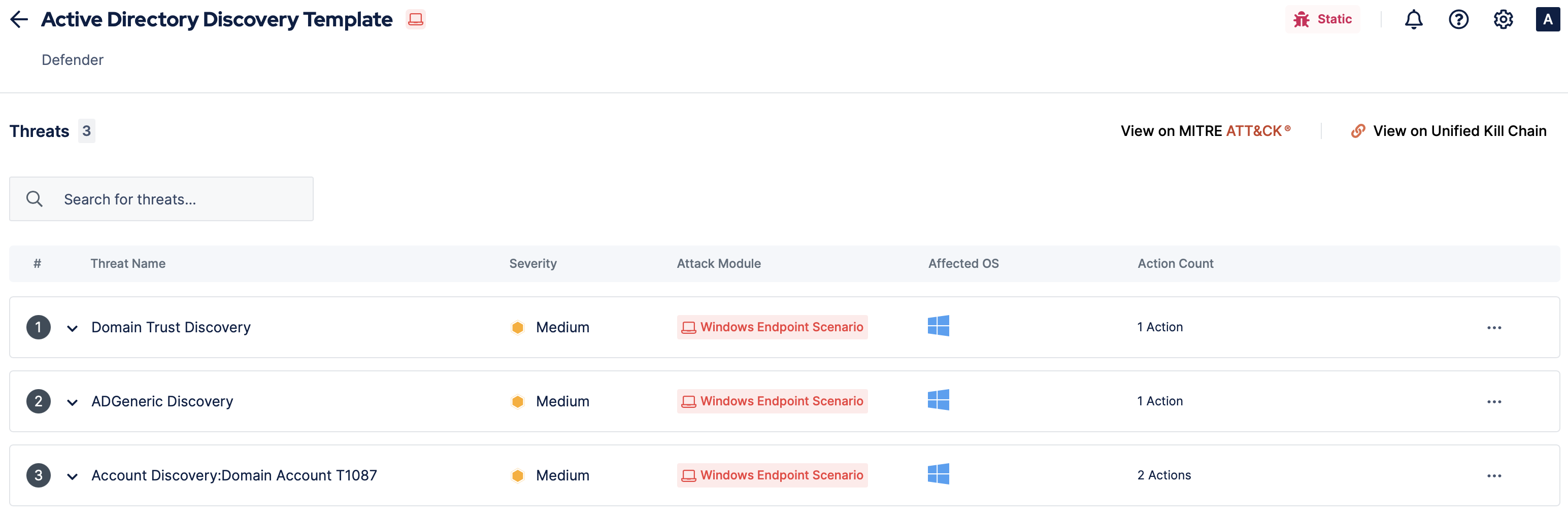
Figure 5: Custom adversary emulation template
A BAS tool enables security teams to run adversary emulations either on-demand or continuously:
When used in the on-demand mode, BAS prioritizes the selected adversary attacks and simulates them within minutes.
When used in the continuous mode, Breach and Attack Simulation can consistently and continuously simulate thousands of attacks in hours.
Finally, Breach and Attack Simulation ensure that adversary emulations in the library are up-to-date and relevant to the ever-changing threat landscape. New adversary emulations are continually added to the library and executed without interruption.
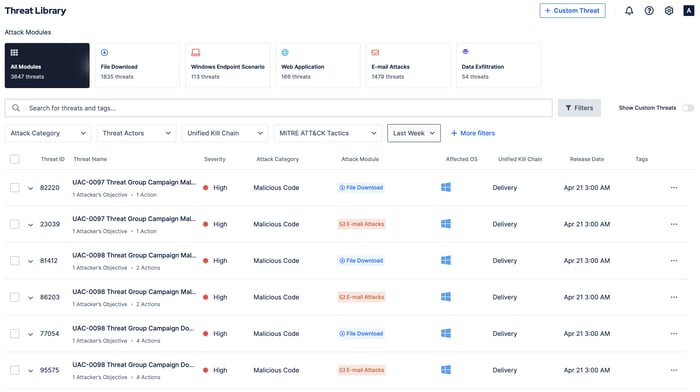
Figure 6: Threat Library updated recent adversary emulations
Continuous adversary emulation and security posture validation capabilities of comprehensive Breach and Attack Simulation platforms allow security teams to conduct gap analysis in their security controls. BAS software aggregates results of adversary emulations and reports the gaps in the tested defense infrastructure to the security team. By automating adversary emulations, Breach and Attack Simulation performs gap analysis continuously and in the background without interruption to daily operations. The heat map resulting from the gap analysis informs the security team which kind of gaps are in their defenses and gives them a clear picture of their security posture.
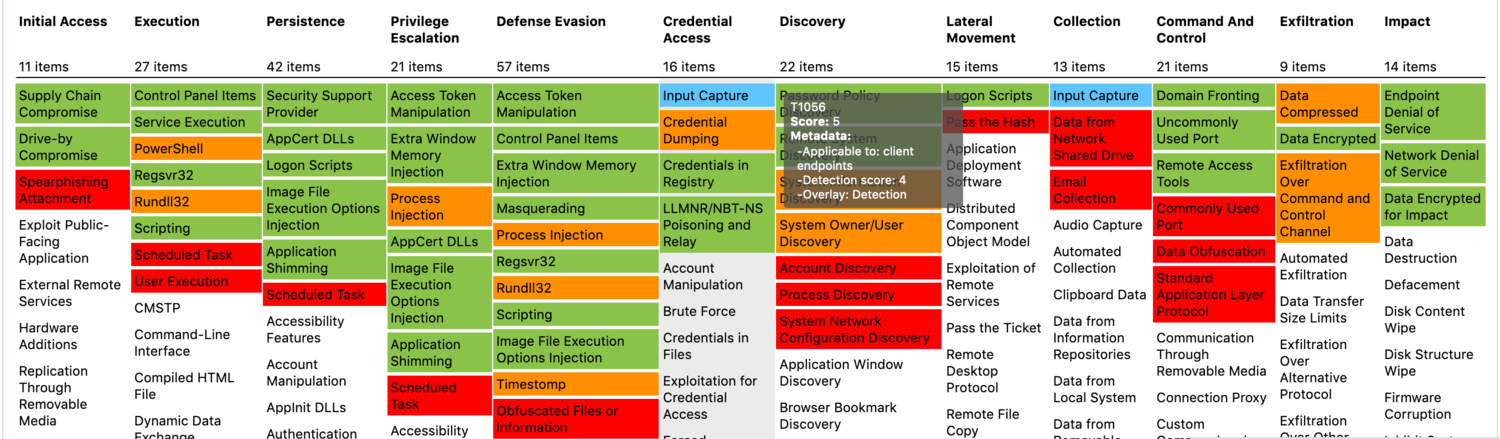
Figure 7: Example heatmap after gap analysis
Techniques used in adversary emulations are colored to indicate the performance of the security controls.
White: Assessment gap - Technique is not tested yet
Red: Logging gap - Relevant log data was not collected to detect the technique.
Orange: Detection gap - Relevant log data was collected, but the detection mechanism was inadequate.
Green: No gap - Adversary activity is successfully detected.
Security teams aim to remediate the gap in their security controls swiftly. After listing the gaps in the security controls, Breach and Attack Simulation gives mitigation recommendations specific to each adversary technique that security controls failed to detect and prevent.
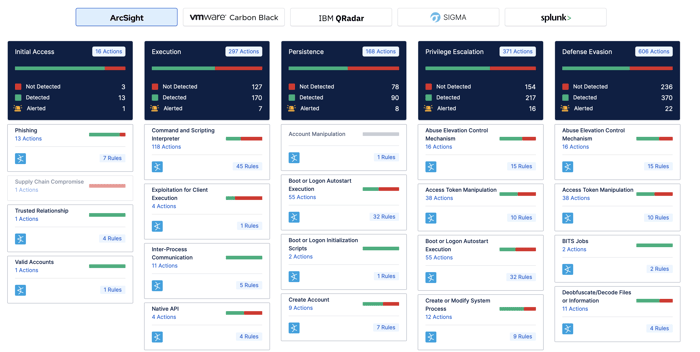
Figure 8: Detection Rules Provided by BAS
These recommendations are both generic and vendor-specific mitigations. Security teams can use generic mitigation recommendations to create custom detection rules and tailor them to their needs. In order to respond to cyberattacks rapidly, vendor-specific mitigation recommendations can be applied to security controls with minimum effort.
A capable BAS platform must provide vendor-specific prevention signatures for prevention security controls such as Next-Generation Firewalls (NGFW), Web Application Firewalls (WAF), and Intrusion Prevention Systems (IPS), and detection rules for Endpoint Detection and Response (EDR) and Security Information and Event Management (SIEM) products.
After mitigation, Breach and Attack Simulation re-assess the security posture to verify that the gap is remediated.
Breach and Attack Simulation platforms can immensely help security teams in their purple teaming activities by automating:
the collection and analysis of threat intelligence
extensive adversary emulation
measuring MITRE ATT&CK coverage
prevention and detection gap analysis
developing and validating prevention signatures and detection rules.
Of course, most Breach and Attack Simulation tools don't have all these purple teaming capabilities. Only BAS platforms with both red team (e.g., extensive adversary emulation) and blue team (e.g., actionable mitigation insights) features can offer these capabilities and enable security teams to adopt purple teaming swiftly and effortlessly. Try the most comprehensive BAS platform on the market free for 14 days and start purple teaming.