Huseyin Can YUCEEL
April 11, 2022
Nowadays, it is a common practice to involve red and blue teams in the cyber security operations of organizations. Although these teams approach cyber threats from different angles, they share the common goal of securing the organization and can learn from each other to achieve this goal. In this blog post, we explained purple teaming and why organizations need purple teaming.
What Are Red and Blue Teams?
Before explaining Purple Teaming, we need to understand the Red and Blue teams and what they represent in security operations.
Red Team
Red team is a team of security professionals that think and act like cyber threat actors to test the effectiveness of the defensive capabilities of their organizations. Although they often use similar methodologies, red teamers and penetration testers should not be confused with each other. Red team operations are not limited to penetration testing and have a more comprehensive role in their organizations. An ideal red team should have the following characteristics [1].
1. Organizational Independence: Red teams should not be restricted so that they cannot test a real-life scenario. Organizations might want to limit the scope of the test scenarios performed by the red team; however, an actual attacker would not care about those limitations.
2. Defensive Coordination: There should be a feedback mechanism that feeds the findings of the red team to the defense teams. Without regular defensive coordination between teams, the work done by the red team does not benefit the organization.
3. Continuous Operation: Cyber threat actors do not rest, and neither should red teams. Unlike short and limited-scope penetration tests, red team operations should be in the form of long campaigns that span weeks or months with various attack techniques.
4. Adversary Emulation: Red teams should keep their tools and techniques up-to-date to real-world threats and expand their adversary emulation capabilities. Simulating actual attackers help organizations identify gaps in their defenses. Technically inadequate adversary emulations would lead to faulty risk assessment and management.
5. Efficacy Measurement: Any security team’s main objective is to reduce or eliminate risks that threaten their organization, and the red team is no different. Red teams should be able to show how they improve the security posture of their organization in a tangible way.
Blue Team
Blue team is a team of security professionals that focus on managing and improving the defensive capabilities of their organization. They often work as members of the Security Operations Center (SOC). Some of the responsibilities of blue teamers are [2]:
-
Responding to security incidents
-
noticing suspicious network activity
-
identifying indicators of compromise (IOCs)
-
blocking malicious activity/traffic
-
Forensic analysis of security incidents
-
reviewing and analyzing log data
-
Managing security-related technologies
-
Applying security controls
-
proactive defense against threats
-
utilizing SIEM platform
-
prioritizing actions using threat intelligence data
Beneficial cooperation and communication between blue and red teams improve the security posture of the organizations immensely.
What Is Purple Teaming?
Purple Teaming is a mindset that incorporates the perspective of attackers and defenders. The red and blue teams should adopt this concept to improve the organization's defensive capabilities against real-world cyber threats. Therefore, it should be considered an operational strategy, not an additional team called “Purple Team”.
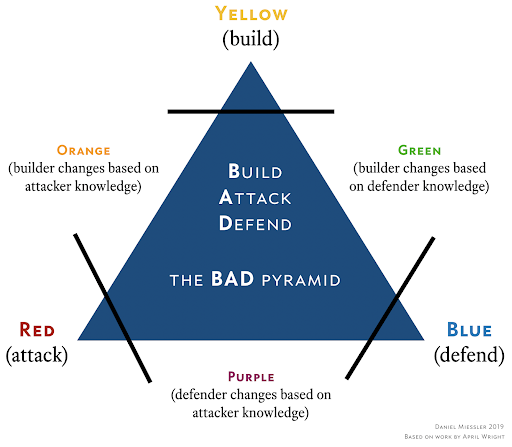 Figure 1: The Build, Attack, Defend Pyramid [3]
Figure 1: The Build, Attack, Defend Pyramid [3]
The purple teaming mindset can improve and optimize the red and blue team operations to continuously improve the organization's overall security. Let's explain purple teaming and the "Assessment-Mitigation Cycle" with an example.
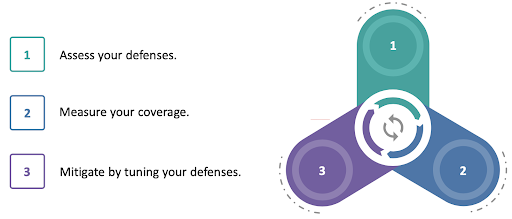 Figure 2: Purple Teaming - Assessment and Mitigation Cycle [4]
Figure 2: Purple Teaming - Assessment and Mitigation Cycle [4]
-
The red team designs an adversary emulation that simulates real-world cyber-attack campaigns or techniques. The adversary emulation can be:
-
atomic tests that emulate a single ATT&CK TTP at a time
-
Advanced Persistent Threat (APT) scenarios
-
malware scenarios
-
The adversary emulation identifies the gaps in the organization's defenses and measures its coverage.
-
The red team documents their findings in a detailed report.
-
Using the red team's report, the blue team makes a risk assessment and decides on which gaps they should focus on.
-
Cyber risk cannot be completely eliminated. Therefore, organizations tolerate risks to some level. It is called residual risk.
-
The blue team checks the log data generated by the security controls to see evidence of successful adversary activity.
-
If the adversary's actions were not recorded in the logs, the blue teamers configure the security controls to gather appropriate log data for detection.
-
If the log data indicates adversary activity, the blue teamers configure security controls to prevent or detect the attack.
-
After the blue team completes its risk assessment and mitigation processes, the red team re-runs its adversary emulation to measure the coverage of the updated defenses.
The back and forth between blue teams running detection and analytics and red teams trying to evade them is beneficial to keep them up-to-date against the ever-evolving threat landscape. The purple teaming allows security teams to build and maintain the best possible defense for their organizations.
References
[1] “Five Attributes of an Effective Corporate Red Team,” Daniel Miessler, Jul. 06, 2016. [Online]. Available: https://danielmiessler.com/blog/five-attributes-effective-corporate-red-team/.
[2] A. Hargreaves and J. Chamberlain, “The Roles of Red, Blue and Purple Teams.” [Online]. Available: https://www.itlab.com/blog/understanding-the-roles-of-red-blue-and-purple-security-teams.
[3] “The Difference Between Red, Blue, and Purple Teams,” Daniel Miessler, Feb. 08, 2016. [Online]. Available: https://danielmiessler.com/study/red-blue-purple-teams/.
[4] Purple Academy by Picus, “Purple Academy,” Purple Academy by Picus. [Online]. Available: https://academy.picussecurity.com/course/cyber-threat-intelligence.




