Automated Penetration Testing
Scale your manual penetration testing program with automated security validation.

Automated Penetration Testing
for Continuous Security
Traditional penetration testing is slow and resource-intensive. Picus Security’s automated penetration testing continuously identifies vulnerabilities, validates security controls, and uncovers high-risk attack paths without requiring offensive security expertise. Get faster, scalable, and real-world attack simulations to stay ahead of threats.
Automate Penetration Testing to:
-
Uncover high-risk vulnerabilities
-
Minimize manual efforts
-
Achieve complete attack surface visibility
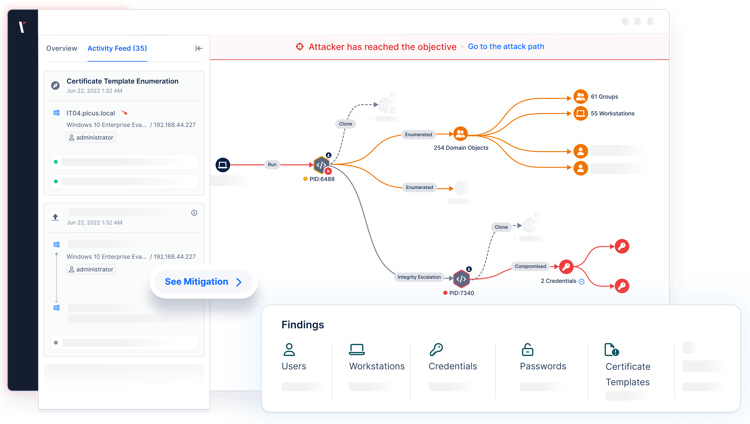
Automated Penetration Testing Meets Precision
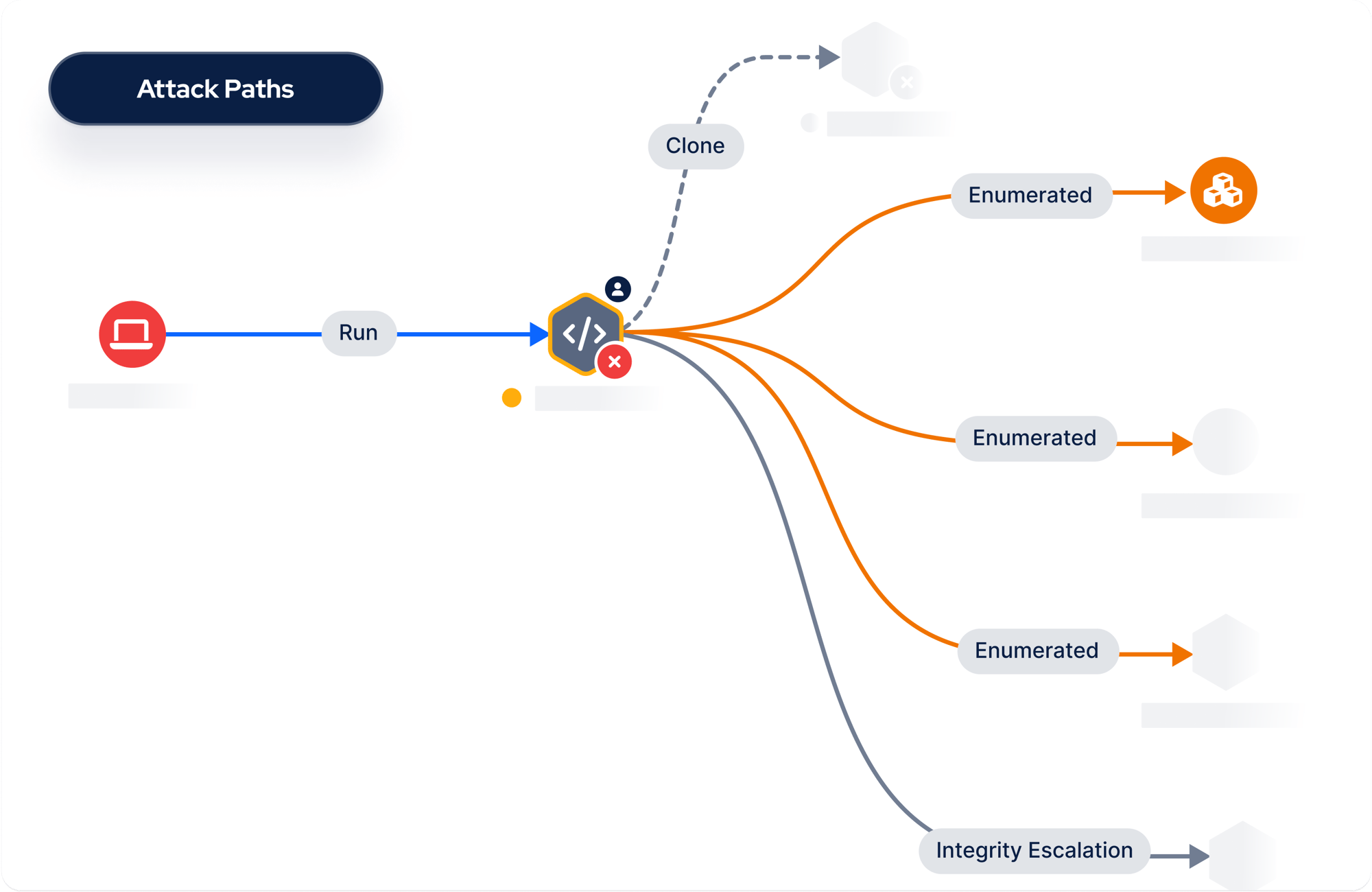
Picus Security combines automated penetration testing with attack path mapping to determine which vulnerabilities are exploitable and shortlist the attack paths.
Automated Penetration Testing provides comprehensive coverage, uncovering a wide range of vulnerabilities and exposures across systems. Attack Path Mapping visualizes the most critical chokepoints that lead to domain admin compromise, disruptive ransomware attacks, and more.
With a unique combination of the two, security teams gain comprehensive visibility and targeted precision.
Full-Spectrum Validation
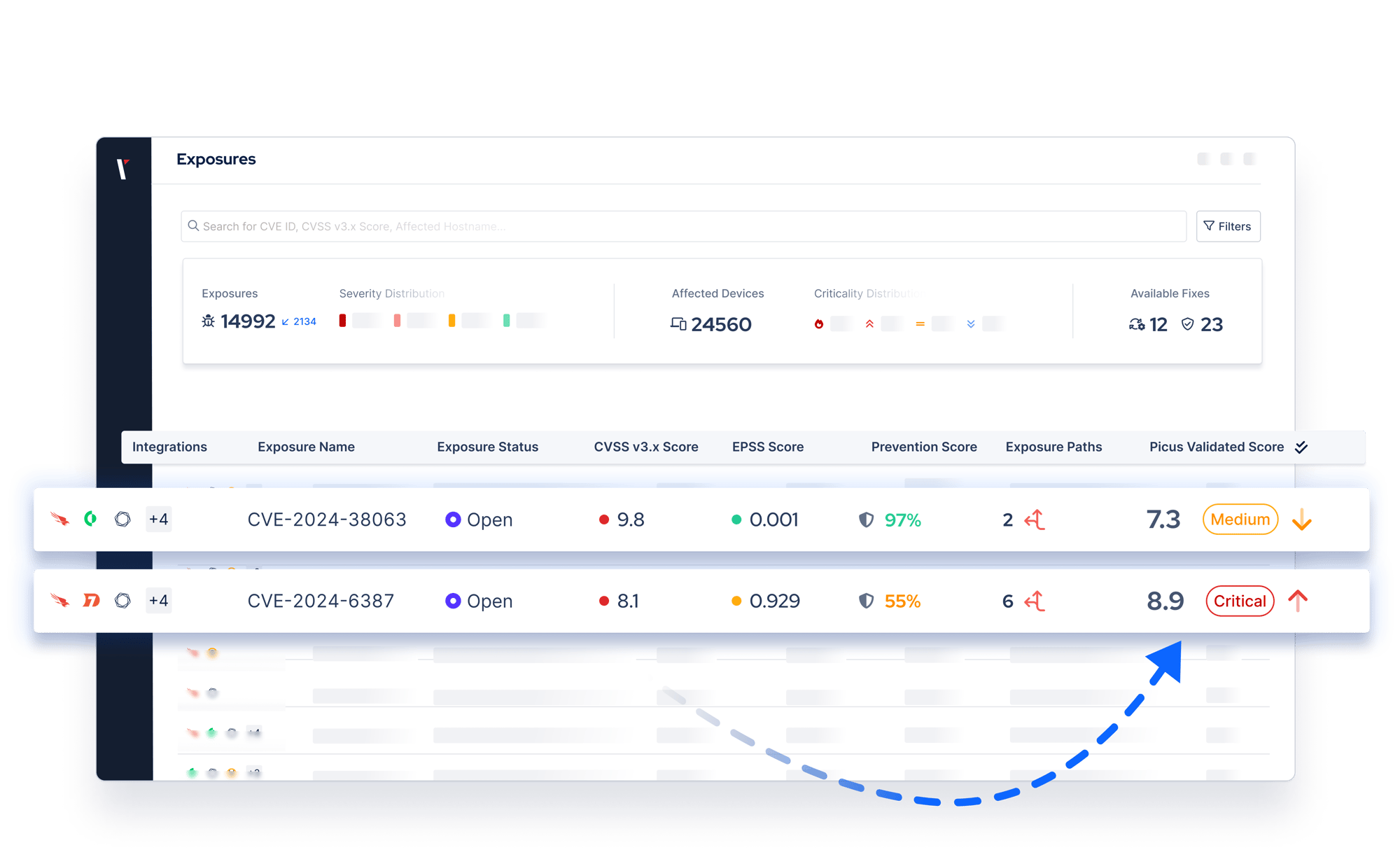
By combining Automated Penetration Testing and BAS, organizations don’t just detect vulnerabilities; they validate which security gaps can be chained from the start to full domain compromise. This integrated approach uncovers whether an attacker can bypass firewalls, exploit misconfigurations, escalate privileges, and execute ransomware, while also testing if security controls can detect and stop these actions.
This unique combination drives Exposure Validation, enabling security teams to have end-to-end visibility, prioritize and remediate the exposures posing the greatest risk.

Andrea Licciardi
Senior Cyber Security Manager
customer
Picus APV has been instrumental in elevating our proactive defense capabilities, particularly through its automated pentesting features.
Its capabilities allow us to identify gaps swiftly and enhance our cybersecurity posture in real time.
KEY FEATURES OF
Picus Automated Penetration Testing
Address vulnerabilities and misconfigurations at ‘choke pointsʼ to ensure you achieve the best security impact.
Discover attack paths by using the latest attack techniques, all mapped to the Unified Kill Chains.
Emulate ransomware behavior by determining which files an attacker can locate and exfiltrate.
Choose attack techniques based on the attack pathʼs value.
User-friendly and non-intrusive assessments.
Schedule or initiate emulations on-demand, not requiring user intervention.
Benefits of Automated Penetration Testing
Awarded By The Industry
Customer's Choice
2024 Gartner® Peer Insights™ Voice of the Customer for Breach and Attack Simulation
Cyber Security Excellence Awards
2024 Cybersecurity Excellence Awards – Most Innovative Cybersecurity Company
Customer Reviews
Picus is very good attack simulation tool in overall. It shows all security vulnerabilities and guides..
Sr. Information Security & Risk Officer
The implementation was very fast, the platform is easy to integrate and results quite intuitive to be analyzed.
CIO
It is easy to use and implement the product. It is a really useful tool to find out your security tool vulnerabilities..
Cyber Security Manage
A very successful platform where we can test the accuracy of our security investments and see their scores.
Manager, IT Security and Risk Management
Picus is one of the best BAS solution on the market today. The threat database it is constantly updated..
ICT Security Engineer
Picus completes the task it is required to do near perfect as a BAS solution. Threat database is up to date & updated frequently after a new malware or campaign, also the database is large..
Consultant Security Engineer
There is a very nice team from which I can get quick support. The application provides us with great convenience and confidence in our work.
Information Security Specialist
To test our systems with the real-time attack product is helping us to improve our security maturity. At the same time, the real time attacks are updating with the zero-day vulnerabilities..
Senior Vulnerability Management Engineer
With the help of this product we can perform continuosly endpoint attack via latest tactics and techniques which are used by threat actors..
Manager, IT Security and Risk Management
.. It is possible to customise the campaign or schedule the assessment periodically, to test protection measure implemented on network, endpoint and email.
ICT Security Engineer
Picus is such a great product for organizations that are looking to have constant checks and validation on their security posture in the organization.
Cybersecuirty Pre-sales Engineer.
Picus is a real safety measurement tool. Ever since we took Picus into our inventory, Security has helped significantly to increase our maturity level.
Cyber Defense Senior Specialist
It strengthened our security perspective and allowed us to follow trend attacks. We can test zeroday malicious threats very early because Picus could add them their attack database quickly.
Security Specialist
INTEGRATIONS
Unlock Your Security Stack’s Full Power
Picus integrates with your SIEM, EDR, NGFW, WAF, and the rest of security controls to:
- Safely simulate real-world attacks in production
- Reveal gaps each tool misses
-
Fine-tune each control for maximum efficacy

Explore Other Use Cases
How the Picus Platform helps you address your cybersecurity challenges.
Attack
Simulation
Simulate attacks to measure and optimize security controls.
Validation
Improve decision making with a holistic view of your security posture.
Latest Resources on
Automated Penetration Testing









.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.
Frequently Asked Questions
Automated penetration testing describes the identification of security exposures, such as vulnerabilities and misconfigurations, using an automated tool. Manual penetration testing performed by an ethical hacker can be slow and is often narrow in scope. Automated penetration testing is faster to perform and widens the scope of testing programs.
Manual penetration testing is performed by human ethical hackers. Automated penetration testing complements manual assessments by broadening the scope and scale of testing programs. The outcomes of manual penetration testing can vary depending on the skills of a tester. Automated tests provide consistent validation and metrics that can be used to track changes to an organization’s security posture more reliably.
No. The Picus platform automates security validation, meaning specialist ethical hacking skills are not required to simulate threats. This makes Picus an ideal choice for security teams that want consistent offensive security insights. For professionals with offensive security skills, the platform offers advanced features, such as threat customization, which help scale testing programs.
Automated Penetration Testing and Breach and Attack Simulation are terms used interchangeably to describe solutions that simulate threats. The main difference between tools is that some are specialized in addressing specific use cases such as
vulnerability management, security control validation, and attack path management. The Picus Platform has capabilities to address an extensive range of validation requirements.
Due to constant changes in the threat landscape and within IT environments, it is recommended that penetration testing should be performed on at least a weekly basis and after infrastructure changes. Annual or quarterly penetration testing might satisfy some compliance requirements but is not enough to ensure swift identification and mitigation of exposures.
Yes. Penetration testing can be performed safely in production environments if it is appropriately scoped to minimize any risks.
Picus performs attack simulations using agents and does not target production systems. Any changes made to an environment are rolled back to their original state once an assessment is completed.

