Continuous Security Validation
The joint solution between Picus Security and Trend Micro™ TippingPoint™ provides better visibility, improved utilization, and boosted resilience against real threats. Picus Adversary Emulation replicates the activities of malicious actors on Trend Micro™ TippingPoint™ by using real threat samples and putting security control and monitoring technologies under continuous tests. These tests reveal gaps in defenses, log collection, and alerting capabilities. The Picus platform presents findings with content that shows how these gaps can be addressed so that defense capabilities can be improved continuously.
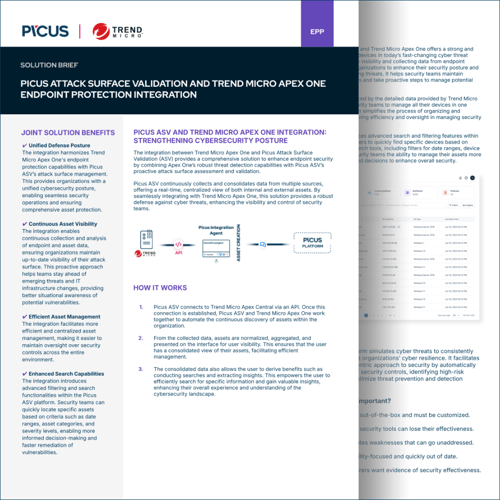
To further expand on our partnership, Picus has integrated with Trend Micro Vision One XDR and Trend Micro Apex One. Picus's integration with Trend Micro Vision One XDR extracts highly valuable data from Trend Micro Vision One and pulls it into the Picus Complete Security Control Validation platform, where our validation technology identifies if XDR logging policies are set correctly, in addition to ensuring detection rules have the right scale and quality.
The integration between Trend Micro Apex One and Picus Attack Surface Validation (ASV) provides a comprehensive solution to enhance endpoint security by combining Apex One’s robust threat detection capabilities with Picus ASV’s proactive attack surface assessment and validation.
The combination of these technologies helps security teams detect attacks more accurately and efficiently while minimizing the number of false positives.
INTEGRATED PRODUCTS
- Trend Micro Vision One XDR
- Trend Micro™ TippingPoint™
- Trend Micro Apex One
WHO IS IT FOR?
- Security Architects
- IT SecOps Teams
- NGFW, IPS, WAF Admins
- SOC Teams
Increase the Effectiveness of Your Trend Micro Vision One XDR Against Real-world Threats
-
Validate the alerts from siloed security solutions that are being captured and analyzed.
-
Identify missing, redundant, and obsolete rulesets and watchlists from all of the valuable telemetry from all security solutions.
-
Measure the time between security events and alert generation.
-
Uncover if you are collecting the right logs at the right verbosity levels.
-
Highlight behaviors that are detected but not blocked by prevention control.
-
Ensure that logs contain the requisite level of data granularity.
Eliminate imminent threats proactively by threat visibility and a rich mitigation library, specifically crafted for Trend Micro™ TippingPoint™.
-
Allowing security teams to move from simple security research analysis to dynamic, adaptive defenses against the full attacker life cycle.
-
Enhanced Trend Micro™ TippingPoint™ effectiveness through continuous validation and mitigation guidance and threat visibility.
-
Shorter detection and response times to imminent threats and false positives reduction using the adversary's perspective to understand advanced TTPs.
-
The capability of making informed decisions by the insights provided by Picus Mitigation Library and efficient utilization of Trend Micro™ TippingPoint™ advanced features and latest signatures.

Strengthen Endpoint Protection with Picus Attack Surface Validation and Trend Micro Apex One
-
Proactively eliminate cyber threats by combining Picus Attack Surface Validation’s real-time visibility and comprehensive asset management with Trend Micro Apex One’s advanced endpoint protection capabilities.
-
Enhance the effectiveness of Trend Micro Apex One through ongoing asset visibility and threat intelligence provided by Picus, allowing security teams to stay ahead of emerging threats and vulnerabilities.
-
Reduce response times and minimize false positives by leveraging the insights from Picus Mitigation Library, enabling informed decisions and maximizing the advanced features of Trend Micro™ Apex One’s latest security signatures.
.png?width=300&height=62&name=Website-Vendor-Page-Logos%20(9).png)
