Validate and Optimize the Efectiveness of Your Microsoft Sentinel and Defender for Endpoint Deployments
The Picus Platform increases the effectiveness of Microsoft Sentinel SIEM and Defender for Endpoint EDR by proactively improving log and detection coverage.
The Picus Complete Security Validation Platform seamlessly integrates with Microsoft Sentinel SIEM, Microsoft Defender for Endpoint EDR, Microsoft Active Directory, and Microsoft Endpoint Configuration Manager(MECM) to bring unparalleled advantages to our joint customers, offering a consolidated and proactive cybersecurity approach by elevating defenses, gaining continuous visibility, and confidently managing their attack surface with a comprehensive solution designed for the dynamic cyber threat landscape.
INTEGRATED PRODUCTS
- Microsoft Defender for Endpoint EDR
- Microsoft Sentinel SIEM Microsoft
- Endpoint Configuration Manager
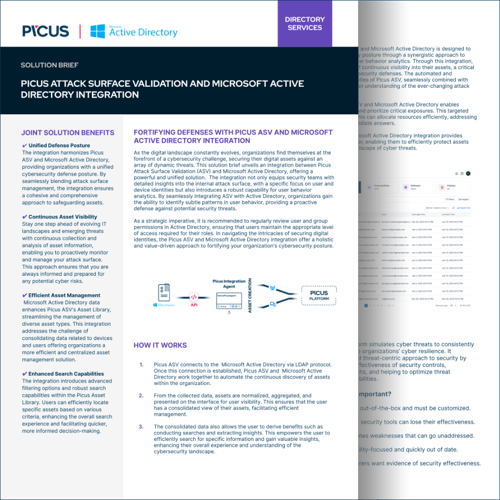
- Microsoft Active Directory Integration
- Microsoft Entra ID
- Microsoft Intune
WHO IS IT FOR?
- Security Analysts
- Detection Engineers
- Threat Hunters
- Incident Responders
- Security Engineers
- CISOs
- Reveal detection gaps before real attacks take place.
- Build and sustain an efficient detection baseline.
- Lower false positives, reduce alert noise, and shorten "time to detect".
- Develop actionable metrics by mapping the results of the hundreds of advanced attack scenario emulations to MITRE ATT&CK Framework.
- Enable agile threat hunting.
- Save time with advanced useability, filtering, and reporting features.
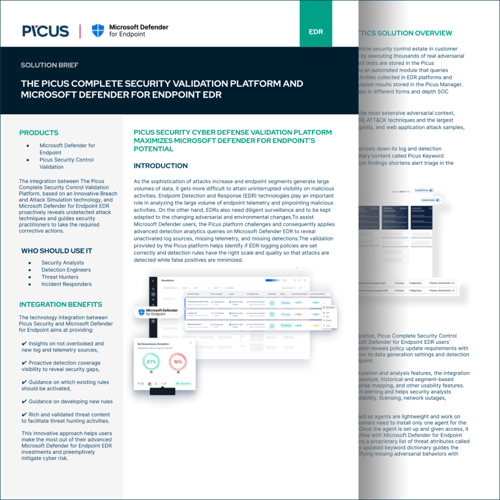
- Ensure a cohesive and comprehensive approach to safeguarding assets by seamlessly blending attack surface management.
- Achieve perpetual oversight of your IT landscape and preemptively address threats with ongoing collection and analysis of asset data.
- Streamline decision-making processes, enabling quicker and more informed actions by the sophisticated search capabilities within the Picus Asset Library, allowing for efficient identification of specific assets.
- Equip your organization with the tools to proactively identify and address vulnerabilities.

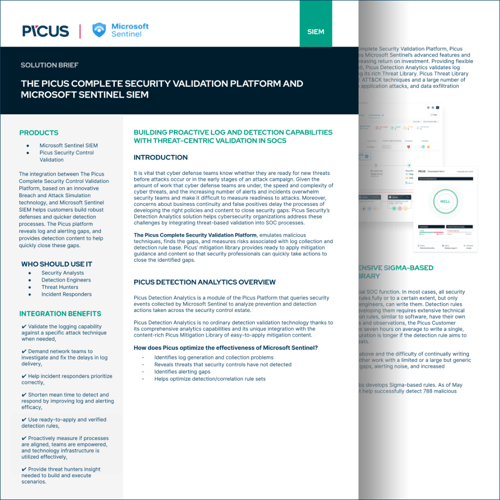
Stress test your Microsoft Sentinel SIEM and improve your detection efficacy
With The Picus Complete Security Validation Platform, you can validate the effectiveness of your Microsoft Sentinel instance in two powerful ways:
Static analysis of your detection rule base:
- Assessment of your existing rule base to support regular maintenance (“spring cleaning”)
- Identifying issues related to the performance and hygiene of your detection rules
- Uncover log source gaps and log ingestion issues
- Remediate query syntax mismatches and bottlenecks to improve your MTTD (mean time to detect)
- Leverage AI to map existing detection rules to MITRE ATT&CK to visualize your detection coverage
Dynamic validation of your detection rules:
- Use real-world attack simulations to validate that your rules perform as expected
- Validate log ingestion and alert creation in your real environment
- Identify logging and detection gaps based on threats that matter to your organization
- Detection engineers can use curated Sigma detection rules developed by Picus Labs to fix the identified gaps quickly
- SOC teams can measure their level of readiness based on MITRE ATT&CK heatmaps.
- SOC teams can build and sustain an efficient detection baseline, lower false positives, eliminate alert noise, and shorten "time to detect".
- Threat hunters can build and strengthen their hypotheses and search capabilities using the rich threat and detection content of the Picus Platform.
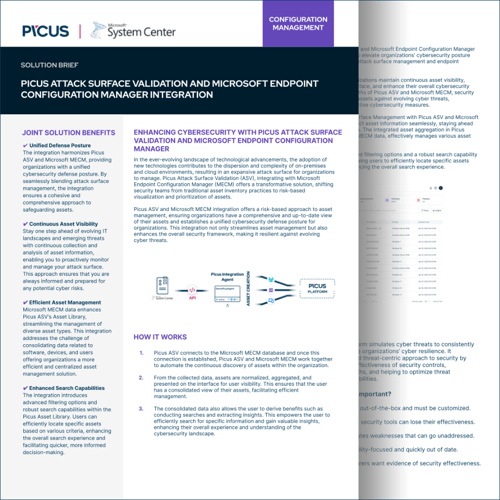
- Stay one step ahead of evolving IT landscapes and emerging threats with continuous collection and analysis of asset information, enabling you to proactively monitor and manage your attack surface.
- Get a more efficient and centralized asset management solution by streamlining the management of diverse asset types and addressing the challenge of consolidating data related to software, devices, and users.
- Efficiently locate specific assets based on various criteria, enhancing the overall search experience and facilitating quicker, more informed decision-making.
- Ensure a cohesive and comprehensive approach to safeguarding your assets.
- Get a more efficient and centralized asset management solution by streamlining the management of diverse asset types and addressing the challenge of consolidating data related to devices, and users.
- Efficiently locate specific assets based on various criteria, enhancing the overall search experience and facilitating quicker, more informed decision-making.
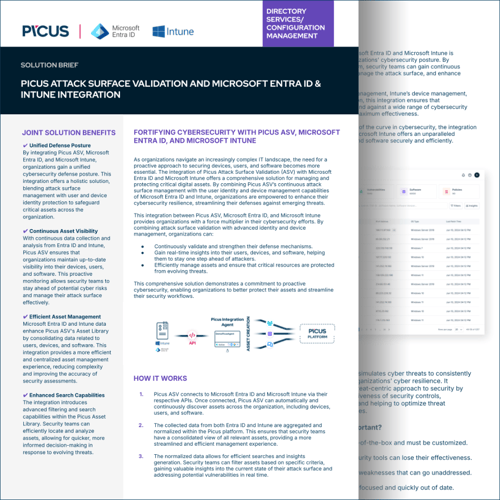
- Create a comprehensive security framework by seamlessly integrating Picus ASV with Microsoft Entra ID and Intune, enabling streamlined management of digital assets and advanced protection against cyber threats.
- Maintain continuous visibility into your organization’s devices, users, and software through real-time monitoring provided by Picus ASV, enhanced by the data insights from Entra ID and Intune, keeping you ahead of emerging risks.
- Simplify asset management by consolidating information from Entra ID and Intune, reducing complexity and improving the precision of security evaluations across all critical assets.
- Leverage enhanced search and filtering capabilities to quickly identify and assess assets, ensuring faster and more informed decision-making to effectively mitigate potential vulnerabilities.