-1.png?width=262&height=47&name=Website-Vendor-Page-Logos%20(15)-1.png)
Boost Your Fortinet Infrastructure
and Keep a Solid Security Baseline
The integration between Picus and Fortinet empowers security teams to stay ahead of cyber threats by identifying and mitigating gaps in their readiness. The Picus Adversary Emulation module integrates with Fortinet technologies, offering tailored mitigation actions in line with Fortinet policy settings and signatures.
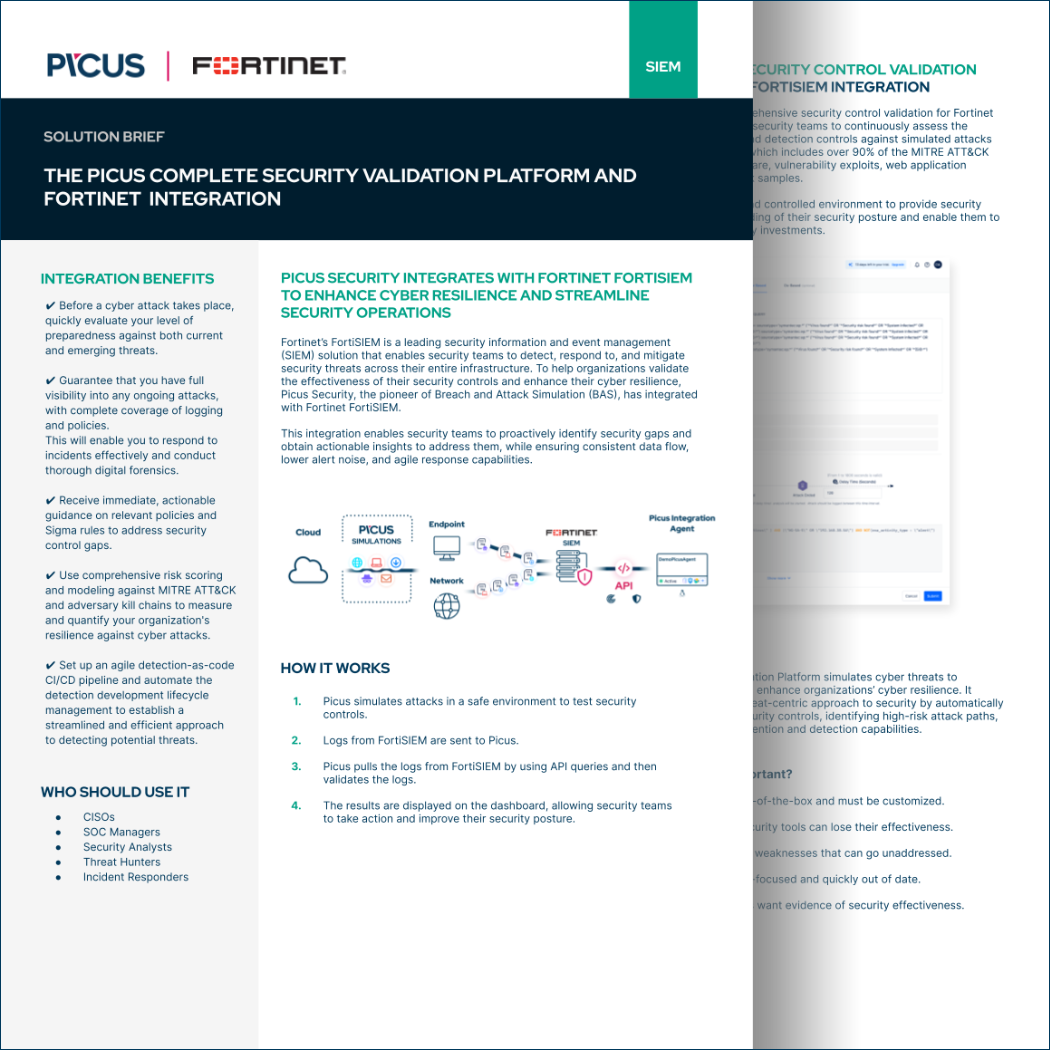
Additionally, the Picus Platform provides comprehensive security control validation for Fortinet FortiSIEM, enabling continuous assessment of prevention and detection controls against simulated attacks. With Picus, organizations can gain a real-world understanding of their security posture and optimize their security investments.
INTEGRATED PRODUCTS
-
FortiGate WAF, IPS, AV, NGW, and FortiWeb
- FortiSIEM
WHO IS IT FOR?
-
Security Architects
-
IT SecOps Teams
-
NGFW, IPS, WAF Admins
-
SOC Teams
- Keep your Fortinet technologies ready against real hackers by operationalizing thousands of real threats such as APT Campaigns, Exploit Kits, Vulnerability Exploitation, Web, and Endpoint threats that exist in the Picus Threat Library.
- Maximize your security posture with prioritized mitigation actions.
- Gain time and efficiency in managing your Fortinet infrastructure.

- Before a cyber attack takes place, quickly evaluate your level of preparedness against both current and emerging threats.
- Guarantee that you have full visibility into any ongoing attacks, with complete coverage of logging and policies.
This will enable you to respond to incidents effectively and conduct thorough digital forensics. - Receive immediate, actionable guidance on relevant policies and Sigma rules to address security control gaps.
- Use comprehensive risk scoring and modeling against MITRE ATT&CK and adversary kill chains to measure and quantify your organization's resilience against cyber attacks.
- Set up an agile detection-as-code CI/CD pipeline and automate the detection development lifecycle management to establish a streamlined and efficient approachto detect potential threats.