SCV for Prevention Controls
Validate, measure and enhance the effectiveness of your network security, endpoint and email controls to block the latest cyber threats.
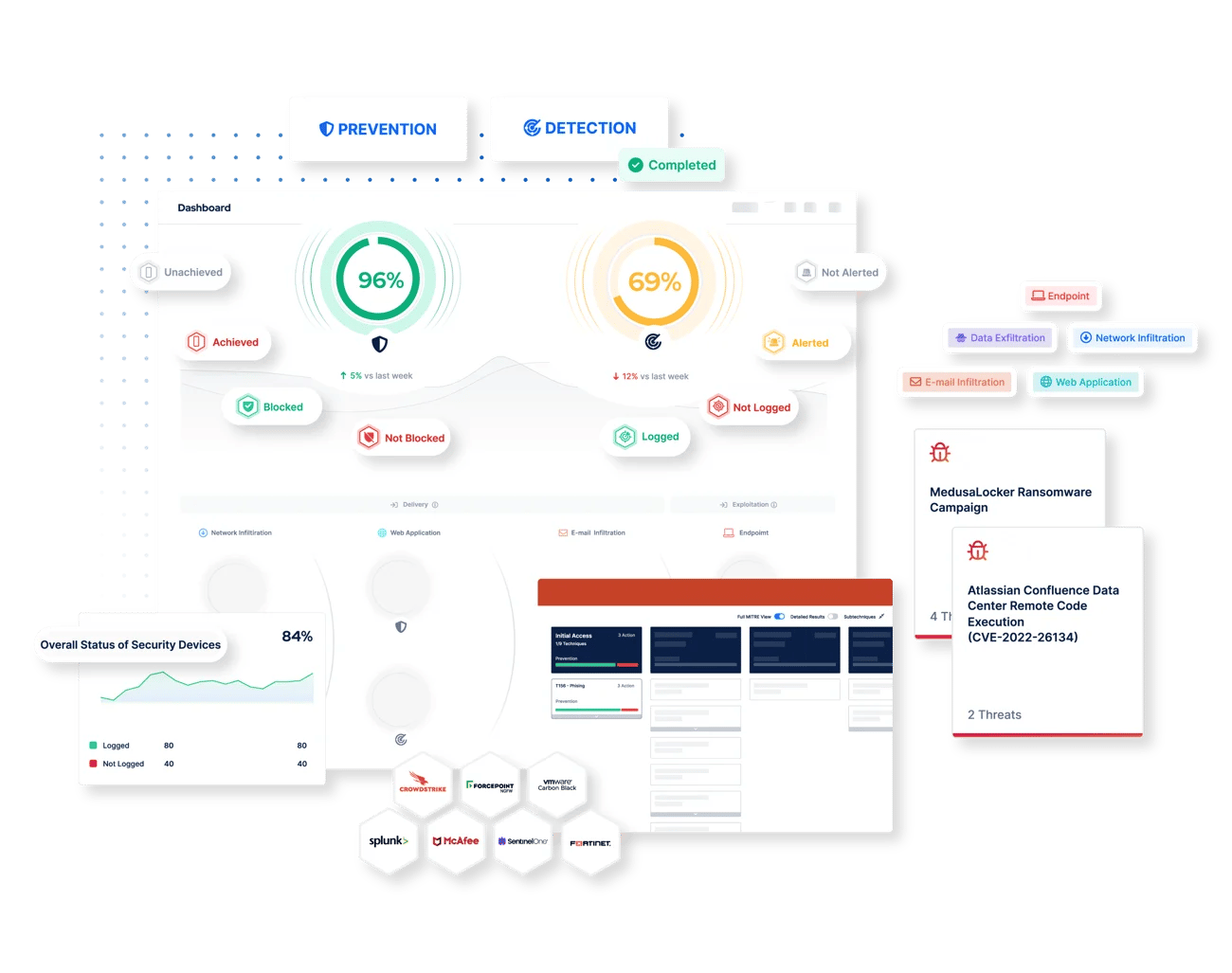
How The Picus Platform Optimizes Threat Prevention
The Types of Threats The Picus Platform Can Simulate Includes
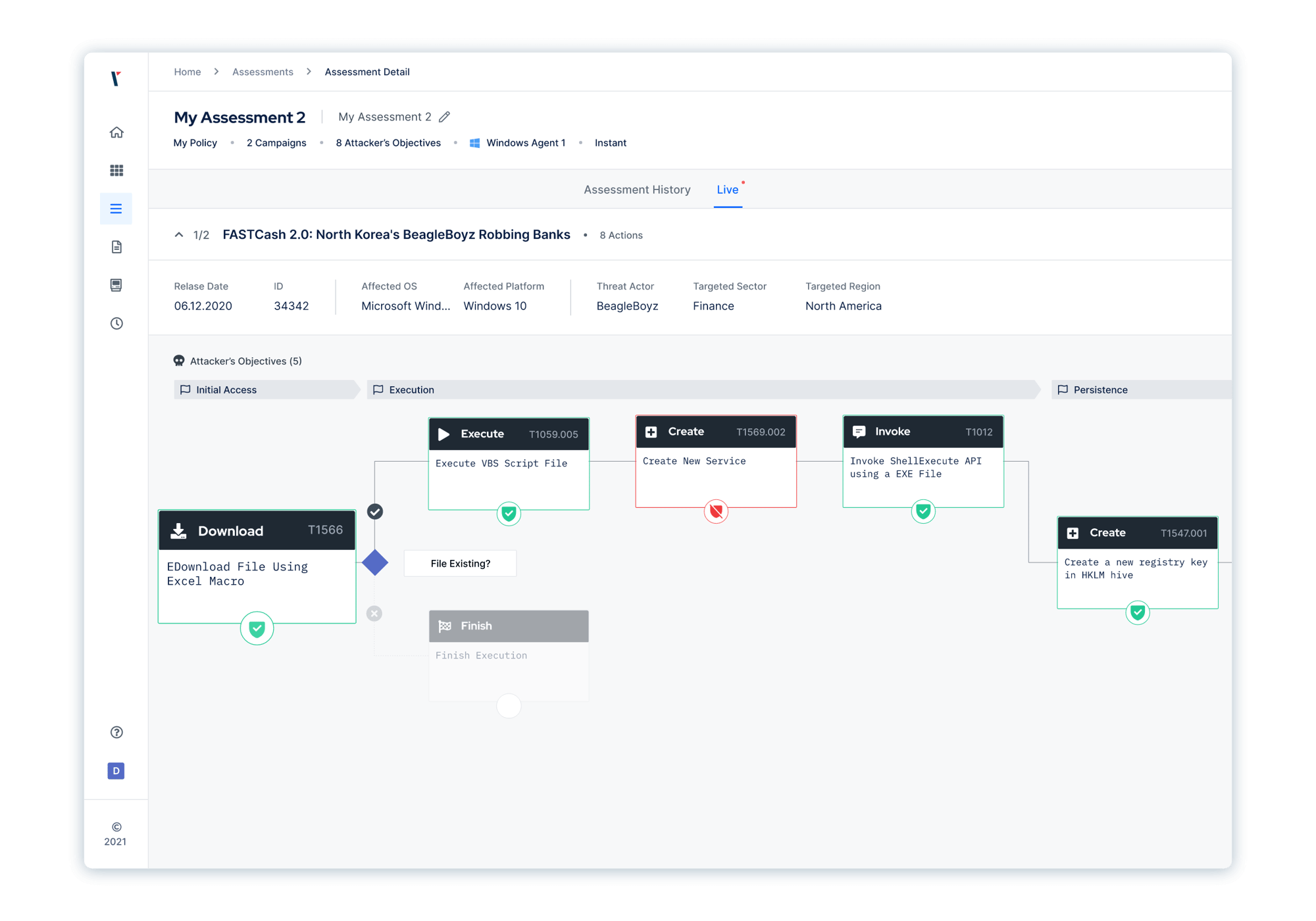
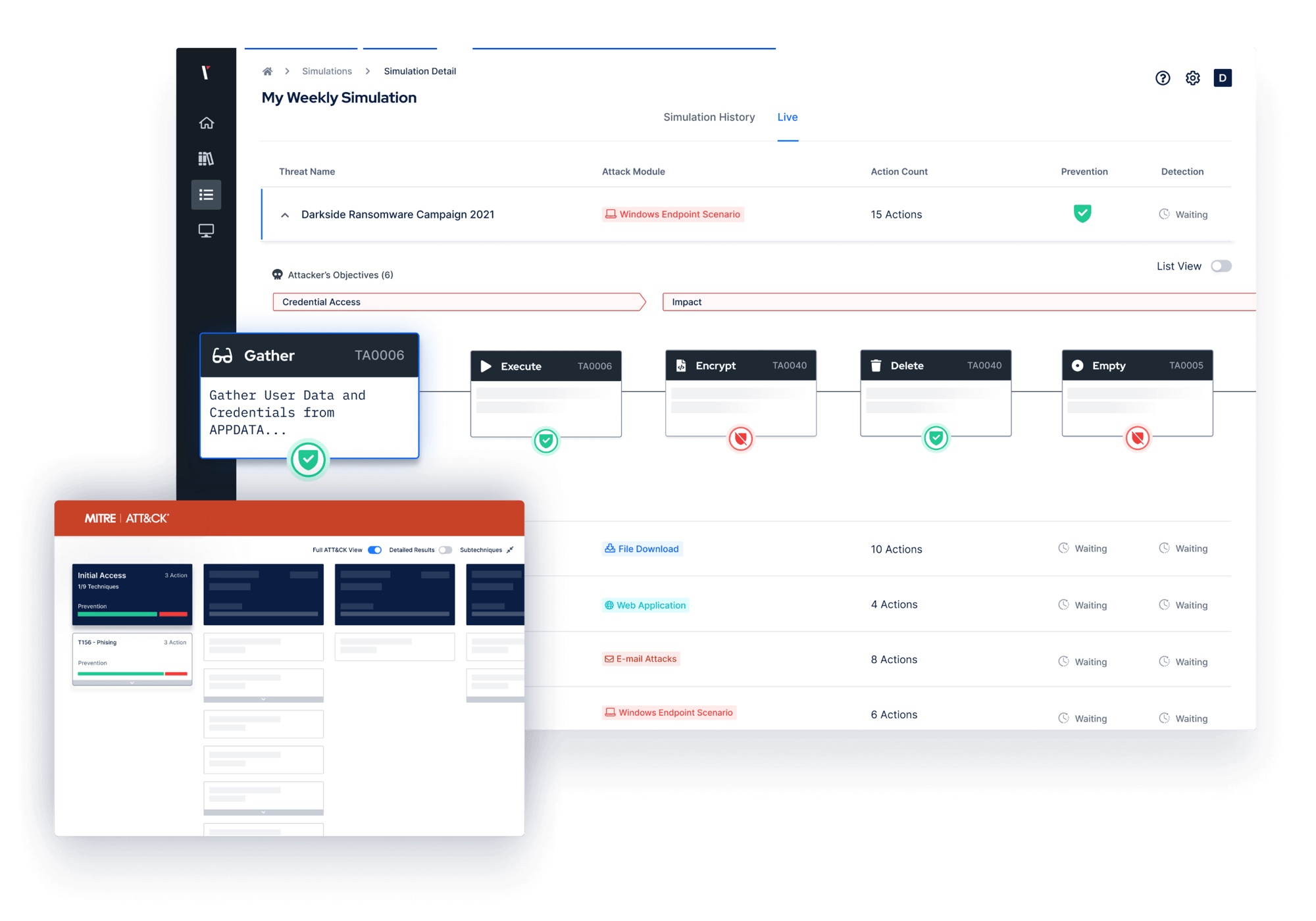
-1.png?width=1559&height=1109&name=Mitre%20(1)-1.png)
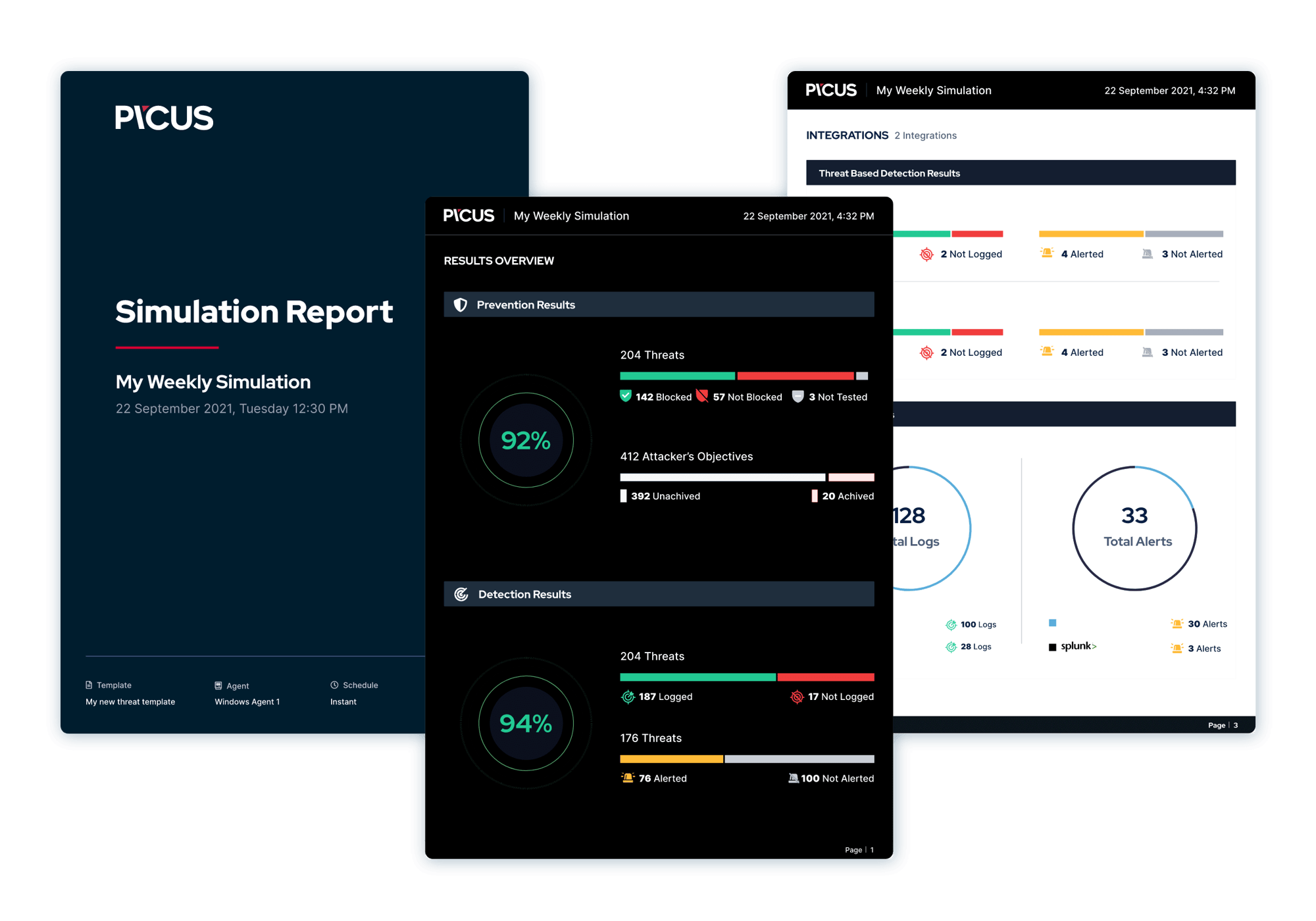
To reduce the time and effort required to tune your security controls, Picus supplies vendor-specific prevention signatures.
To help measure security effectiveness, Picus generates security scores for controls on both an individual and collective basis.
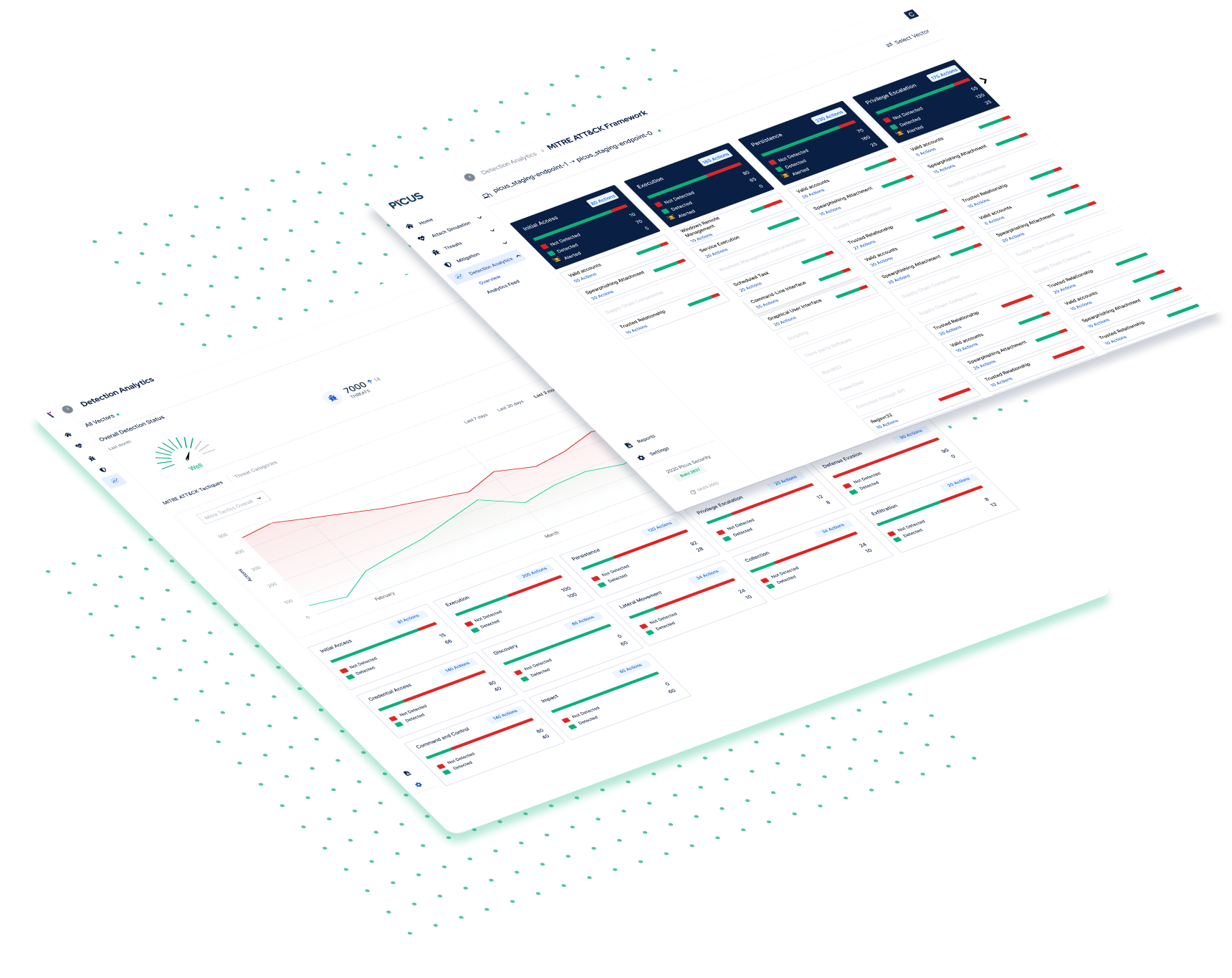
Picus maps assessment results to the MITRE ATT&CK Framework, enabling you to visualize threat coverage and prioritize the mitigation of gaps.
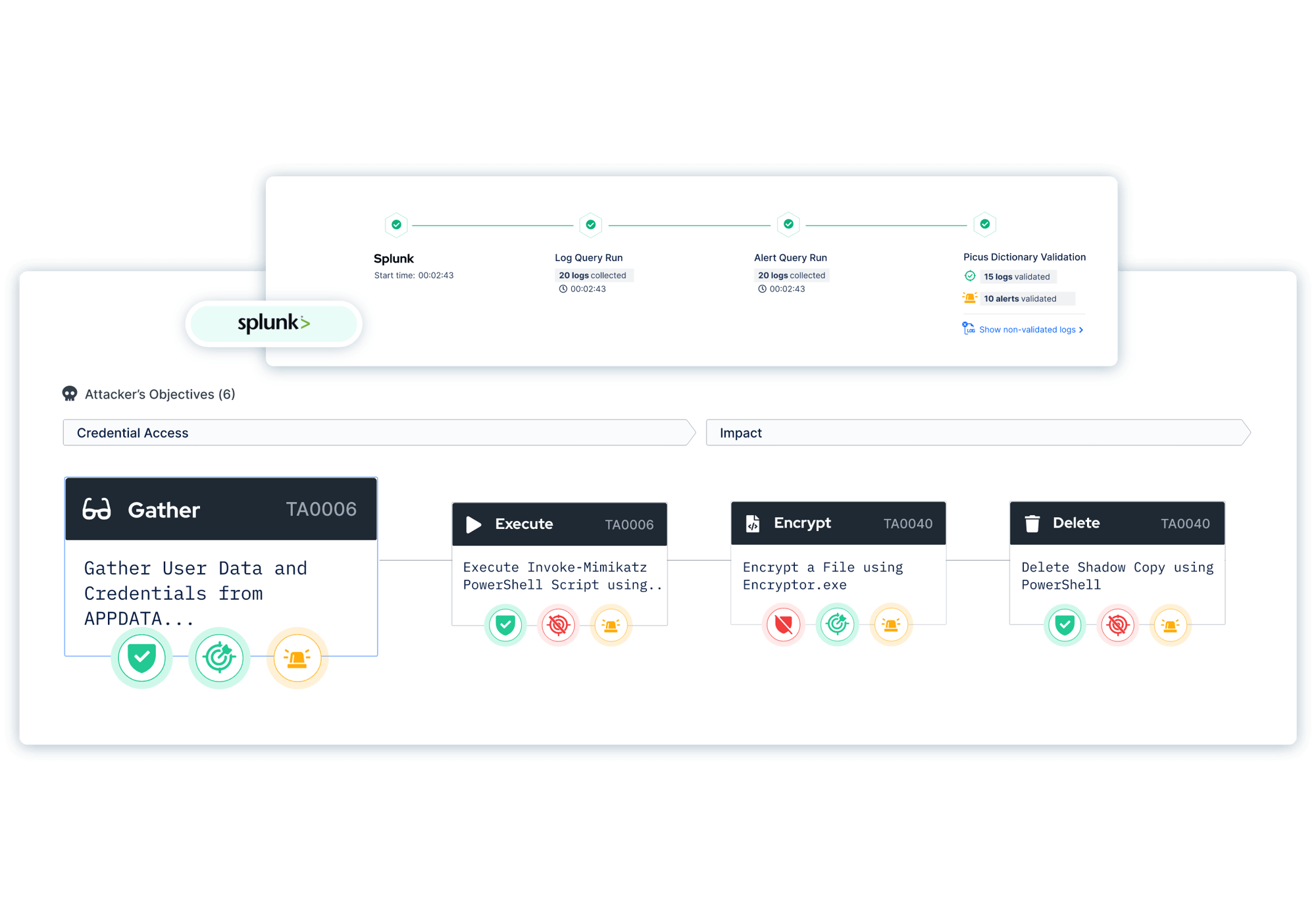
For a deeper level of validation, Picus integrates with the latest toolsets and helps streamline workflows by automating the application of mitigation content.
With The Picus Platform, Validate the Effectiveness of:
- Firewalls and Next-Gen Firewalls (NGFW)
- Secure Web Gateways (SWG)
- Data Loss Prevention (DLP)
- Endpoint Protection Platforms (EPP)
- Email (ES) and Network Sandboxes (NS)
- Web Application Firewalls (WAF)
- Secure Email Gateways (SEG)
- Intrusion Prevention Systems (IPS)
- Antivirus (AV)
- URL Isolation (URL)
.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.
