Picus Threat Library
From Information
Overload to Actionable Threat Intelligence
Information based global threat context is readily accessible in many different ways and forms, but it is hardly actionable. Security analysts try to weather a storm of threat intelligence coming from multiple sources.
Even with a good number of skilled in-house penetration testers or Red Team members, organizations can hardly create a workable and sufficiently broad repository of threat samples in keeping up with the changes in the adversarial context.
" Strong Product to Get a Continuous Security Assessment
Picus is one of the best BAS solution on the market today. The threat database it is constantly updated, in order to simulate the lastest attack campaign and threat, to better understand if the company has an adequate protection against them..."
IT Security and Risk Management,
Transportation Industry
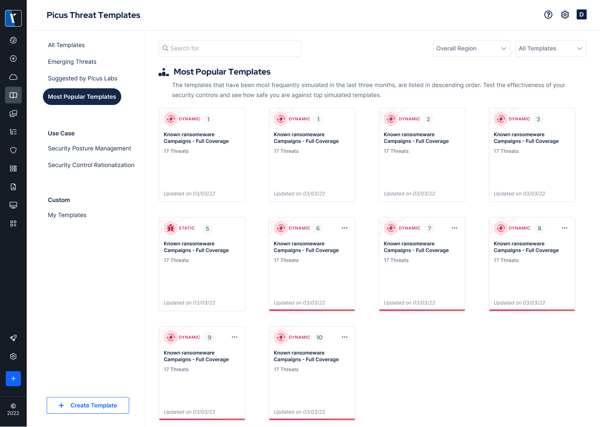
Picus Threat Library
Daily updated Picus Threat Library helps security operations ingest the adversarial changes in relation to their defensive capabilities.
Picus Threat Library offers:
- 30.000+ samples of daily-updated malware, vulnerability exploits, web application attacks, and endpoint attacks.
- Atomic adversarial techniques covering all post-compromise techniques in the MITRE ATT&CK framework.
- Hundreds of Advanced Persistent Threat (APT) driven attack scenarios.
- Picus Threat Library content is mapped to the frameworks of MITRE ATT&CK, Unified Kill Chain, and OWASP, targeted applications, targeted operating systems, and Common Vulnerabilities and Exposures/Common Weakness Enumeration (CVE/CWE) references.

Elevate Your Security Validation with Picus Threat Library
The Picus Threat Library is trusted by security vendors and organizations worldwide, providing the insights and tools needed to proactively validate and improve defenses.
With advanced search and filter options, users can quickly find threats by category, region, or severity. Custom templates can also be created to address specific organizational needs.
Every threat is aligned with industry-standard frameworks like MITRE ATT&CK and Unified Kill Chain, making it easier to connect real-world tactics with security validation efforts.
for Emerging
Threats
Picus Labs continuously adds new and high-impact threats, ensuring that the library stays up to date with the latest attack campaigns and vulnerabilities.
Threats are categorized into Web Application, Vulnerability Exploitation, Endpoint, Malicious Code, and Data Exfiltration, enabling tailored simulations for different security requirements.
Ready-to-use templates, such as Ransomware Readiness or APT Readiness, enable focused testing for specific attack types or adversaries, saving time and effort for security teams.
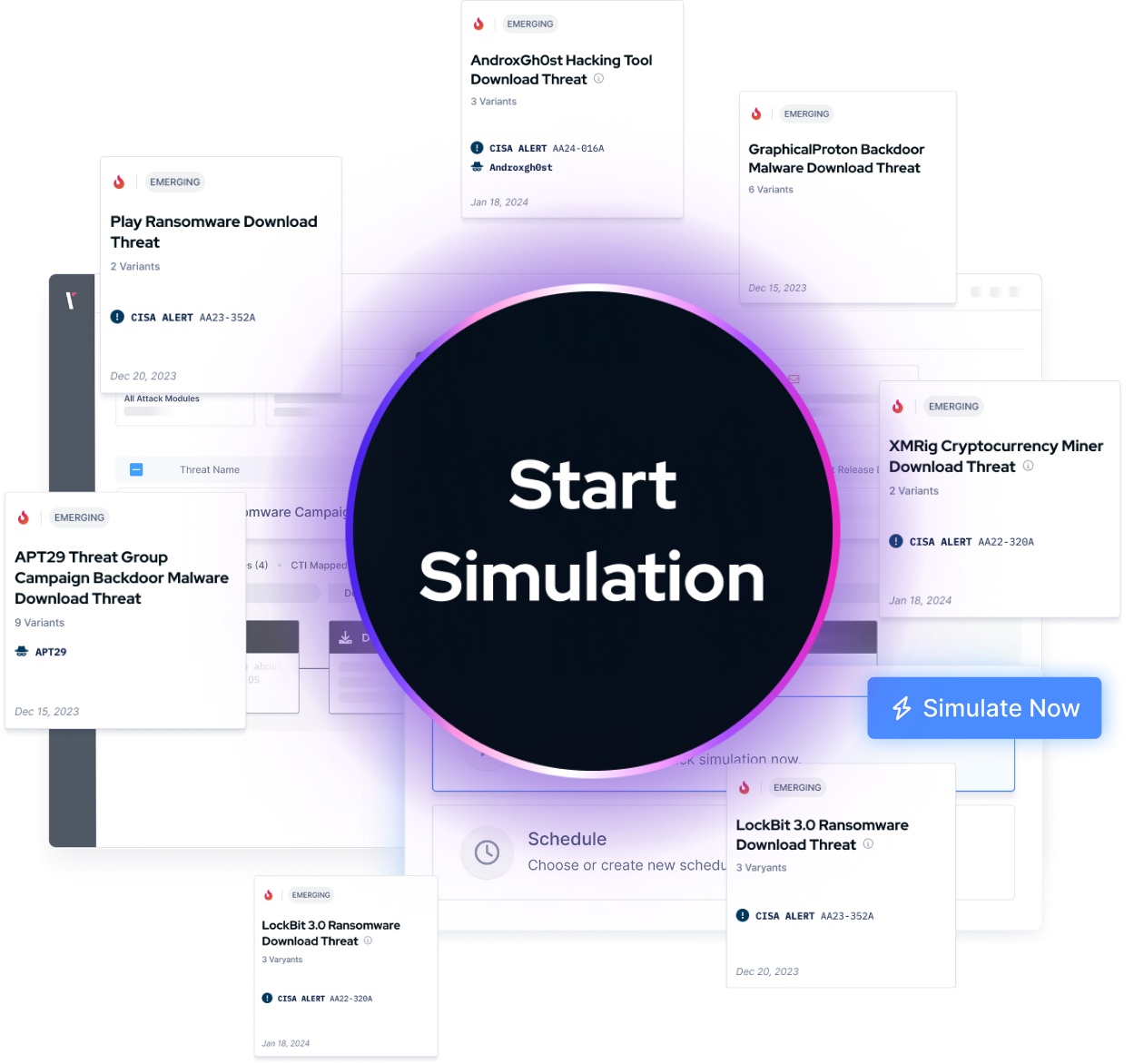
The Most Recent Adversarial Context at Your Fingertips
Thanks to the Global Watch, Commonality Analysis, and Imminent Threat Research processes of Picus Threat Library, Picus customers find the samples of most recent adversarial techniques conveniently at their fingertips. Cybersecurity stakeholders such as SOC analysts, threat hunters, incident responders, security operations teams, the red team, and pen-test members can utilize the granular content of Threat Library for different scenarios they carry out or test.
.png?width=1200&height=152&name=Group%20427319044%20(1).png)
Simulate & Mitigate the Latest Cyber Threats
Improving and maintaining a strong security posture begins with knowing what you're up against. Picus Threat Library enables security teams to simulate real-world cyber attacks and validate their defenses against the latest threats. Once you've identified your security gaps, Picus Mitigation Library provides actionable fixes to strengthen your protection.

Discover Real-World Threat Simulations for Emerging Attacks









.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.
