Picus Mitigation Library

Explore Prevention & Detection Content
in Picus Mitigation Library
Prevention Content
-
Vendor-Based Mitigation: Picus Mitigation Library provides validated prevention signatures tailor-made for security controls, such as NGFW, IPS, and WAF.
-
Generic Mitigation: Picus provides security best practices and mitigation suggestions that remediate gaps in the security posture.
Detection Content
- Picus Mitigation Library provides vendor-specific detection rules and vendor-neutral SIGMA rules for major SIEM and EDR technologies to detect endpoint attacks.
- Picus also provides log source recommendations to enhance log visibility and SIEM efficiency.
Picus Prevention Content
Picus Prevention Content provides mitigation recommendations to proactively reduce security risks. It includes Generic Mitigation Suggestions for broad applicability and Vendor-Based Mitigation Suggestions tailored to specific security products.
Vendor-based mitigation provides mitigation suggestions for threats that are not blocked by security devices. These suggestions include custom signatures tailored to specific devices. For example, if you have ForcePoint NGFW in your security stack, Picus Mitigation Library will provide custom prevention signatures designed for that device. The mitigation suggestions also include details like action count, block rate, and security score for each device.
Additionally, antivirus signatures related to file download attacks can be toggled on or off, depending on whether they are relevant to the security setup.
.png?width=5779&height=3226&name=vendorbasedmit%20(1).png)
Generic mitigation provides security best practices to remediate gaps identified by Picus Platform's attack modules, such as Windows Endpoint Attacks or Email Infiltration Attacks. Picus Mitigation Library displays mitigation suggestions designed to improve defenses against threats that were not blocked by the security controls.
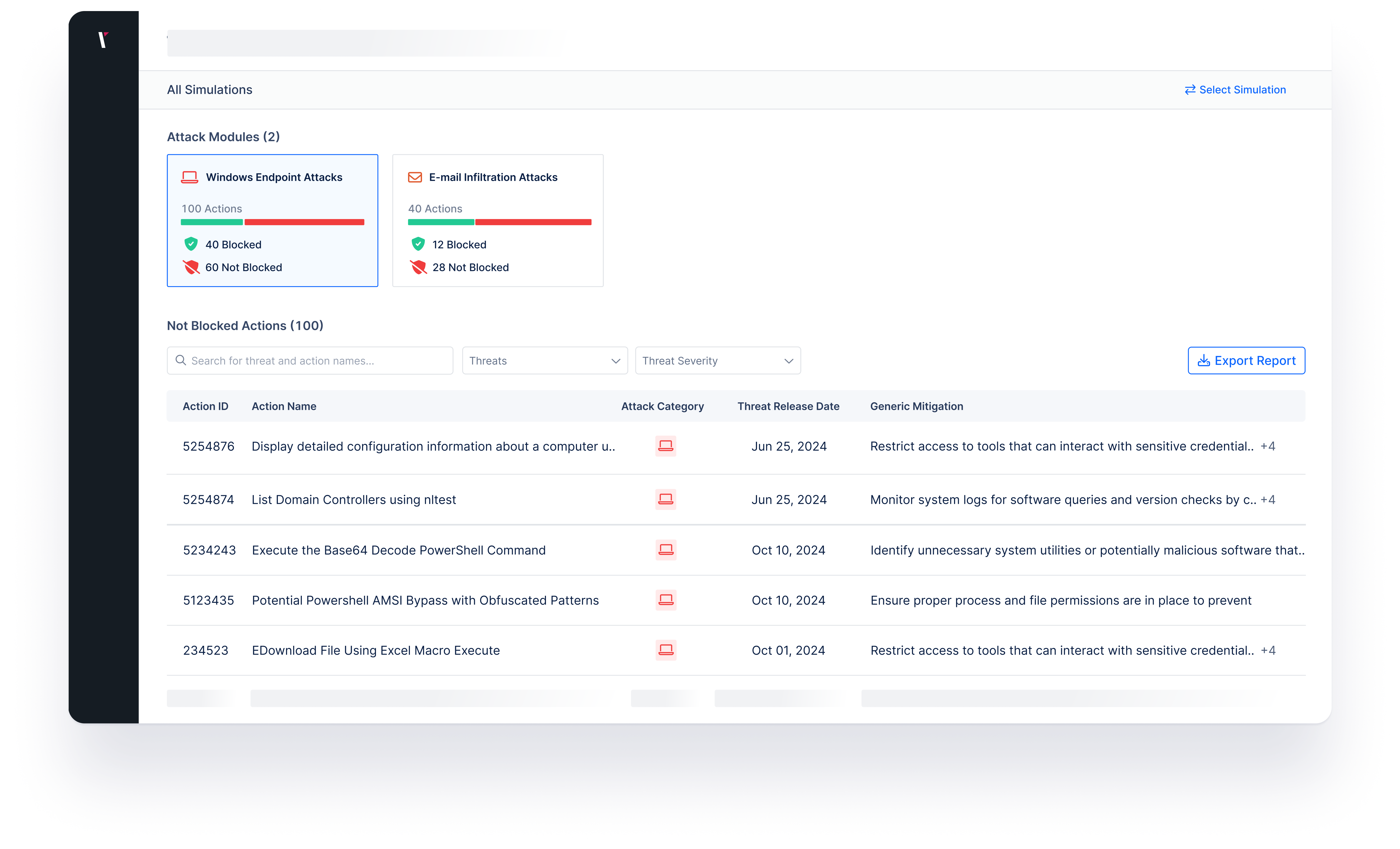
Picus Detection Content
Detection content enables security teams to detect malicious endpoint actions via their SIEM and EDR with little to no expertise in detection engineering. Picus Mitigation Library provides custom detection rules designed to identify endpoint actions efficiently in vendor-specific formats and open-source SIGMA rules.
Each rule provides essential details such as log source, severity, related MITRE ATT&CK techniques, and the actions required for detection, helping organizations monitor and respond to security threats more effectively.
.png?width=600&height=350&name=DetContent_beyza%20(2).png)
Features and Capabilities of Mitigation Library
The Picus Mitigation Library offers several key features and capabilities to enhance the security measures of organizations:
Picus Mitigation Library uses diverse log sources to provide easy-to-apply detection content in vendor-specific and SIGMA formats for SIEM and EDR tools.
Detection
Process
Picus Mitigation Library simplifies the detection engineering process, allowing security teams to directly apply detection content rather than developing it from scratch, saving time and resources.
Picus Mitigation Library provides ready-to-use prevention signatures designed to work for your specific security controls.
Picus Platform runs attack simulations to identify gaps in the security controls. Based on the simulation results, Picus Mitigation Library provides ready-to-use prevention signatures and detection rules that remediate identified gaps.
Reduce Risk Faster with Security Alliance Partners
The extensive technology alliance ecosystem formed by Picus represents the potential of the Mitigation Library in helping customers to eliminate identified security gaps in minutes.
How Picus Planner Works?

Simulate & Mitigate the Latest Cyber Threats
Improving and maintaining a strong security posture begins with knowing what you're up against. Picus Threat Library enables security teams to simulate real-world cyber attacks and validate their defenses against the latest threats. Once you've identified your security gaps, Picus Mitigation Library provides actionable fixes to strengthen your protection.
.png?width=600&height=432&name=templates%20(1).png)
Discover Actionable Mitigations for Emerging Threats









.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.