Endpoint Attacks Module
Picus Endpoint Security Testing Module simulates real-world endpoint attacks to evaluate your defenses, identify security gaps, validate the effectiveness of your EDR, AV, and SIEM solutions, and strengthen overall endpoint protection.
![]()
.png?width=2000&name=Endpoint%20(1).png)
Why Validate Your Endpoint Security?
Endpoint attacks are among the most critical cybersecurity threats, targeting individual devices to gain unauthorized access, execute malware, and evade detection. Unlike traditional network threats, endpoint attacks directly exploit endpoint vulnerabilities, making endpoint security validation essential for modern cybersecurity strategies.
-
Endpoints Are the Primary Attack Surface: Cybercriminals frequently target endpoints with sophisticated attacks, often initiating them through user interactions like malicious downloads. These multi-stage attacks slip through security gaps in endpoint defenses to infiltrate systems and move laterally.
-
Dynamic Gaps in Endpoint Security Controls: Traditional antivirus (AV), endpoint detection and response (EDR), and SIEM solutions can detect threats but may fail to effectively prevent or remediate them due to misconfigurations or security gaps.
-
Advanced Attack Techniques Bypass Defenses: Advanced attack techniques, such as the use of fileless malware, DLL injection, and infostealers, are designed to exfiltrate data and evade traditional security defenses. This highlights the need for continuous testing and proactive security hardening.
-
Comprehensive Validation Enhances Security Posture: Simulating real-world endpoint attacks covering the full kill chain of malware, threat actors, and APT campaigns helps organizations identify security gaps and optimize their defenses.
Enhance Your Endpoint Security
with Real-World Simulations
Picus Endpoint Security Testing Module helps organizations strengthen their endpoint defenses by simulating real-world MITRE ATT&CK® aligned threats. Test your EDR, AV, and SIEM solutions against sophisticated multi-stage attacks, uncover security gaps, and gain actionable mitigation suggestions to improve your security posture.
Simulate real-world endpoint attacks to uncover security gaps before attackers exploit them.
Leverage an extensive and regularly updated attack library or customize your own attack scenarios.
Assess your security stack against MITRE ATT&CK aligned threats and ensure threats are detected, blocked, and remediated.
Test against multi-stage APT scenarios, including fileless malware, DLL injections, PowerShell attacks, and more.
Cross-Version Compatibility
Simulate attacks across multiple Windows versions to verify consistent security coverage.
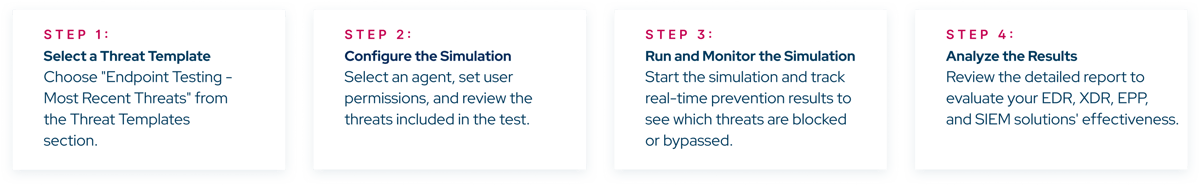
Improve Your Endpoint Security Testing
with Actionable Insights









.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.