Data Exfiltration Module
The Picus Data Exfiltration Module simulates the exfiltration of PII, PCI, source code, critical OS data, and more—across file formats like PDF, XLSX, DOCX and country-specific scenarios to validate your DLP controls.
.png?width=2000&name=DataExfill%20(2).png)
Why Validate Your Data Loss Prevention (DLP) Controls?
Data Loss Prevention (DLP) technologies play a critical role in stopping the unauthorized transfer of sensitive information. However, without regular validation, even the most advanced DLP solutions can fail to detect modern data exfiltration attempts.
-
DLP configurations weaken over time: Policy changes, misconfigurations, and overlooked exceptions can reduce detection accuracy.
-
Attackers use advanced evasion techniques: Data can be exfiltrated via obfuscated or hidden methods across formats like PDF, DOCX, CSV, or even images and executables.
-
Sensitive data is always at risk: Personally identifiable information (PII), payment data (PCI), source code, and critical OS files are high-value targets for cybercriminals.
-
Compliance standards demand proof: Frameworks like GDPR, HIPAA, and PCI-DSS require organizations to test and demonstrate the effectiveness of their data protection controls.
-
One-time tests aren’t enough: Frequent, scenario-based simulations—like country-specific and protocol-aware exfiltration attempts—are key to maintaining a strong security posture.
Strengthen DLP Effectiveness
with Realistic Exfiltration Simulations
Picus Data Exfiltration Module enables organizations to test their host and network-level Data Loss Prevention (DLP) solutions by simulating sophisticated and stealthy data exfiltration attacks. With automated, continuous testing and a comprehensive threat library, security teams can detect misconfigurations, assess coverage, and improve their data protection posture efficiently.
Uncover DLP misconfigurations that are often missed by manual testing to improve data protection before threats strike.
and Effort
Save valuable time and effort with fast deployment and simple management, enabling teams to focus on high-priority tasks.
Visibility
Gain a comprehensive view of your posture against the most critical phase of attacks—data exfiltration.
Run continuous, automated simulations to identify and fix security gaps faster—without draining team resources.
Catch evasive exfiltration attempts—like encrypted or hidden data transfers—that traditional tools often miss.
to Your
Environment
Ensure DLP policies are effective across your specific environment with fully customizable threat scenarios.
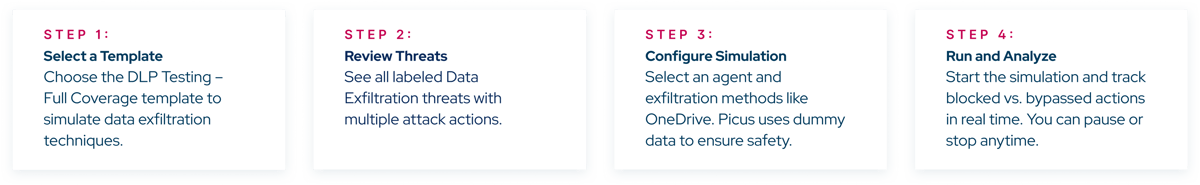
Improve Data Loss Prevention
with Practical Testing Resources









.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.