Challenges of AWS Cloud Security
If your organization has workloads in Amazon Web Services (AWS), it’s vital to ensure that they are secured properly. AWS cloud attacks often occur because organizations fail to follow AWS’s Shared Responsibility Model and identify cloud misconfigurations.
Common AWS misconfigurations that can lead to cloud security data breaches include:
Open S3 Buckets Misconfigured IAM policies Unrestricted access to resources
How Picus Help You to Secure AWS
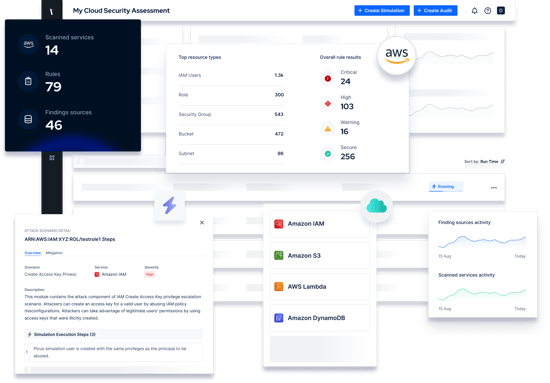
Picus Cloud Security Validation (CSV) helps you secure your workloads in AWS by identifying cloud misconfigurations and overly permissive IAM policies - the two primary causes of AWS cloud data breaches.
AWS cloud auditing
Scanning core AWS services, Picus CSV identifies critical cloud misconfigurations that attackers could exploit. These include excessive privileges, exposed S3 buckets, and cryptographic failures.
AWS attack simulation
By simulating cloud attacks in AWS, Picus CSV identifies overly permissive identity and access management (IAM) policies that could enable attackers to compromise cloud services and steal data.
Want to learn more about Cloud Security Validation for AWS?
Be Cloud Confident With Security Validation for AWS
The complexity and ever-evolving nature of AWS cloud environments means misconfigurations can easily occur.
Picus Cloud Security Validation not only helps to stay on top of cloud security risks by automating cloud security posture management. With AWS attack simulation, it also provides additional assurance that your cloud-native controls are configured optimally.
.png)
One Complete Platform for Security Validation
Validate security effectiveness across your organization’s attack surface
Looking to Validate and Maximize Your
Cyber Defenses?
Let’s link up! Our experts will be more than happy to help. We look forward to getting to know your organization, your priority challenges, pressing questions about breach and attack simulation, and more.

CONTACT A PICUS SECURITY EXPERT
Frequently Asked Questions
|
Why is AWS security? |

|
AWS cloud security is the protection of AWS cloud infrastructure, services and data against cyber attacks.
|
Are AWS attack simulations safe to perform? |

|
Picus Cloud Security Validation simulates attacks in a local policy simulator to ensure that attack scenarios won’t impact cloud operations.
|
How regularly should AWS cloud audits be performed? |

|
Due to constant changes within AWS environments, such as the deployment of new users, services and assets, Picus recommends that organizations should perform cloud audits on at least a weekly basis.
Leave your contact details and a product specialist will contact you to schedule a 30-minute demo.