Picus Labs
Picus Labs is dedicated to advancing cyber threat intelligence, providing tools and knowledge to defend against evolving cyber threats.
Who is Picus Labs?
Picus Labs is the research and development division of Picus. We stay ahead of cyber threats and equip organizations with the knowledge and tools to defend against them.
Picus Labs focuses on:
- Researching emerging threats and adversary techniques
- Updating the Picus Security Validation Platform
- Developing advanced cybersecurity solutions
Our findings integrate into the Picus platform, enhancing its effectiveness and reliability. We also share our expertise through publications and collaborations, raising cybersecurity awareness and preparedness.
Meet the Team
Picus Labs consists of three specialized teams: Red, Blue, and Purple, each playing a crucial role in cybersecurity.
.png?width=55&height=55&name=Group%20427319017%20(1).png)
Red Team
The Picus Red Team simulates real-world cyberattacks to:
- Research the latest adversary techniques
- Improve our threat simulation capabilities
- Update the Picus Threat Library
Our Red Team members are experts in offensive cybersecurity, constantly evolving their methods to stay ahead of threats.
.png?width=55&height=55&name=Group%20427319017%20(2).png)
Purple Team
The Picus Purple Team bridges the Red and Blue Teams, enhancing overall security by:
- Leveraging expertise from both teams
- Fostering collaboration and communication
- Creating and implementing comprehensive security strategies
.png?width=55&height=55&name=Group%20427319017%20(3).png)
Blue Team
The Picus Blue Team focuses on defensive security operations, responsible for:
- Researching prevention and detection techniques
- Engineering prevention signatures and detection content
- Enhancing the Picus Mitigation Library
Our Blue Team members specialize in defensive measures like intrusion detection and malware analysis, ensuring robust security against the latest threats.
.png?width=55&height=58&name=Layer_1%20(4).png)
Picus Threat Library
The Picus Threat Library is a dynamic repository of cyber threats and attack techniques maintained by Picus Labs. It helps clients validate their security posture against the latest threats.
The library includes Network Infiltration Attacks, Endpoint Attacks, Web Application Attacks, E-mail Infiltration Attacks, Data Exfiltration Attacks, and URL Filtering Attacks.
We continuously update the library with the latest threat intelligence.
.png?width=55&height=54&name=Layer_1%20(3).png)
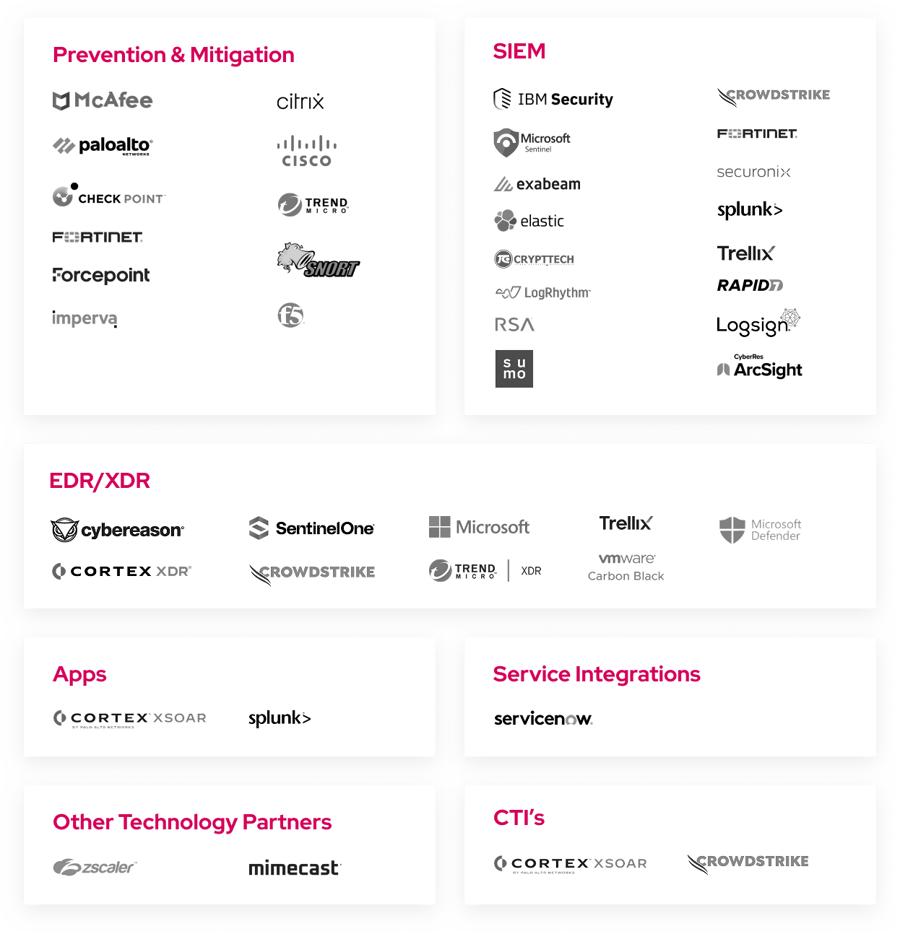
Picus Mitigation Library
The Picus Mitigation Library offers practical strategies to counter various cyber threats. It translates threat intelligence into effective defensive measures.
The library provides:
- Generic and vendor-specific mitigations for security products
- Prevention Mitigation: NGFW, IPS, WAF
- Detection Content: SIEM, EDR, XDR
We regularly update the library to reflect new developments in the threat landscape.
Picus Labs is dedicated to advancing cybersecurity through rigorous research and development. Our teams continuously work to stay ahead of emerging threats, ensuring our clients have the most effective tools and knowledge. By leveraging the comprehensive resources of the Picus Threat Library and the Picus Mitigation Library, we empower organizations to strengthen their defenses and protect against sophisticated cyber threats.
Contact us today for more detailed information and to see how Picus Labs can help your organization.
EMERGING THREATS
Discover Our Latest News and Content









See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.