WHAT ARE THE CHALLENGES OF SIEM MANAGEMENT?
Log Collection
SIEM Log agents and collection software can malfunction due to configuration errors, software bugs, expired licenses, old APIs, and other factors. Also, the complexity, size, and load of the networks can strain the flow of data.
Blind Spots
If security controls technologies have not been made ready against new adversarial techniques, they will be blind to attacks that contain them. As security controls will not detect such attacks, they will not generate logs.
Level of Logging
Decisions on data sources, types, and granularity requires significant elaboration on alternative costs. Each new log adds complexity, takes disk space, puts a load on the correlation engine, and consumes the “events per second” license pool. As a trade of, missing logs may result in some malicious events not being detected.
Keeping up with the Changes
SOC teams must be aware of architectural changes, new deployments, new applications and retiring technologies to keep log management aligned with these changes that are handled by network operations, IT security, devops and other.

Log Validation with Attack Simulation
Picus Security Control Validation Platform with the extensive library of threats, can easily integrate to your infrastructure and help you automatically identify logging gaps and areas of improvement.
HOW PICUS IS SOLVING THESE CHALLENGES?
Picus improves log coverage and detection rules based on actual defensive capabilities and enhances SIEM efficacy proactively. Integrations with major platforms contain extensive vendor-specific and sigma-based detection content.
SIEM ALERT MANAGEMENT WITH PICUS
Adapting the detection rule base on the changing adversarial context is a difficult task. This difficulty results in detection gaps, false positives, alert noise, and alert fatigue.
Challenging SIEM detection rules with an extensive attack simulation and using an automated platform addresses some key challenges. The Picus platform offers security insights that combine detection gaps and detection content, empowers red and blue team practices, and makes purple teaming an integrated capability whereby cyber defense teams can improve security posture.
WHAT ARE YOUR BENEFITS
AS A CUSTOMER?
Uncover if you are collecting right logs at right verbose level.
Assess and see if your SIEM is properly parsing and storing logs.
Identify time gaps between log sources with the attacker timestamping.
Take immediate action by implementing provided detection playbooks.
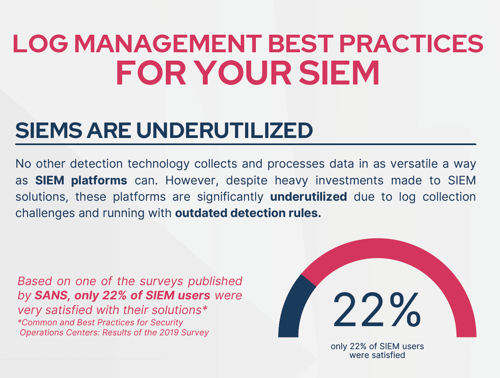
Do you want to learn more about Log Management Best Practices?
👉 Click here to download the full infographic
FIND YOUR
SIEM TECHNOLOGY
Learn more about how The Picus Platform is integrating with your technologies.

Sigma
Security Information and Event Management
Schedule a 30-minute demo with Breach and Attack Simulation Specialist.

















/LogRhythm.png)







.png)


