Detection Rule Validation
Proactively identify issues related to the performance and hygiene of SIEM rules and obtain insights to accelerate threat detection and response.
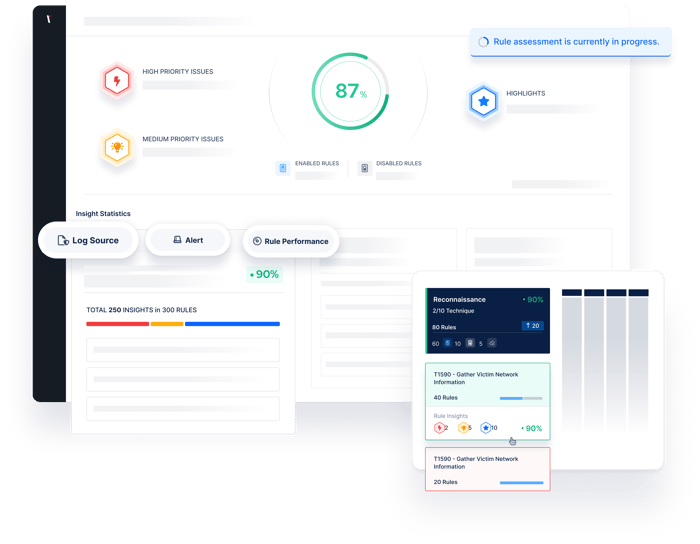
.webp?width=700&height=553&name=detection-rule-3%20(1).webp)
Continuously Validate and Optimize your Detection Rules
In recent years, the volume of alerts, and logs, that security teams have to deal with has increased exponentially. Organizations are collecting more data than ever, and new and more sophisticated threats are constantly emerging. In this cycle, developing new detection rules becomes increasingly difficult.
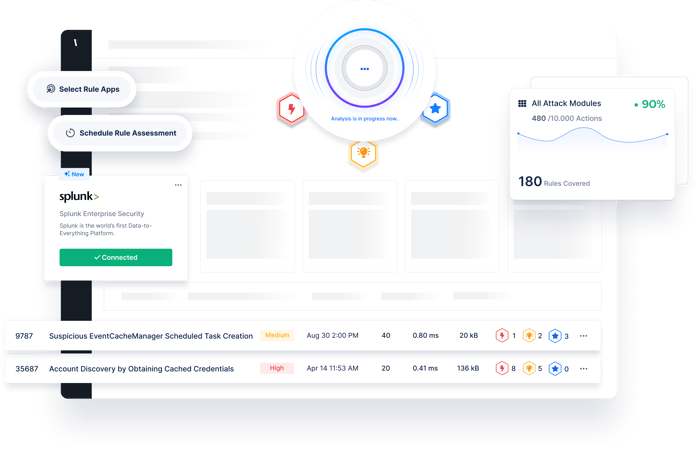
Picus Detection Rule Validation (DRV) enables security teams to stay on top of the detection rule baseline and automate manual detection engineering processes in order to achieve continuous and proactive detection rule validation.
Picus Detection Rule Validation Technology Integrations
Integrations with leading security vendors help to improve the detection engineering process to building, testing, and updating detections for both new and existing rules.

Why Detection Rule Validation?
Reasons to Choose The Picus Platform to Validate Detection Rules
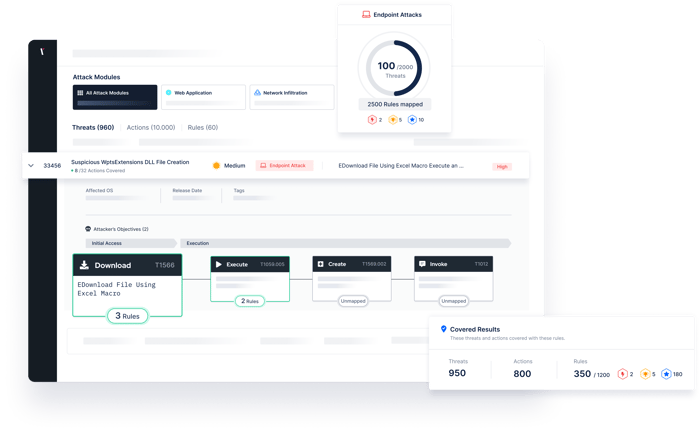
Reveal threat gaps by measuring the threat coverage of your rules and analyze deficiencies.
Test the performance of your detection rules against thousand of real-world threats, updated daily.
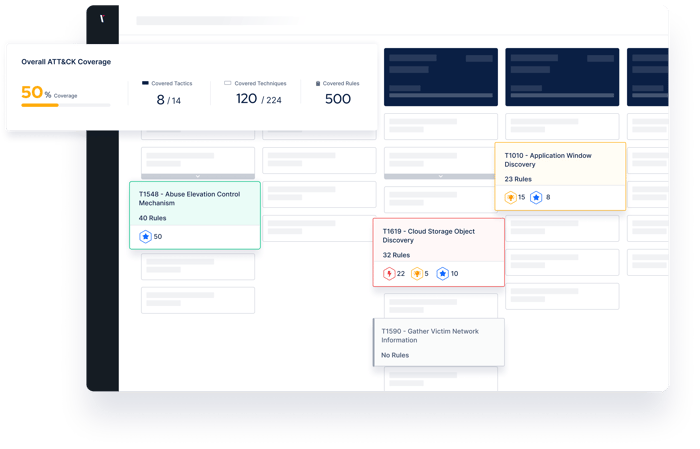
To help visualize threat coverage and visibility, The Picus Platform automatically maps simulation results against The MITRE ATT&CK Framework.
With extensive reports and dashboards, stay on top of the detection rule baseline and automate manual detection engineering processes.
.png?width=700&height=544&name=Small_image_5%20(1).png)
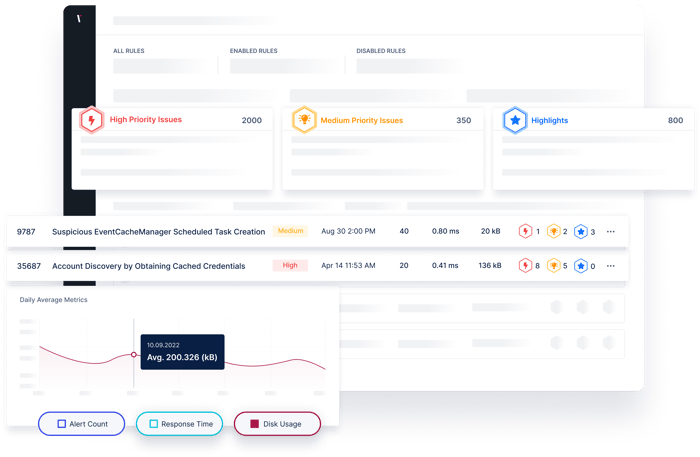
Assess The Quality of Your Detection Rules
-
Identify broken, missing, and inconsistent rules and any issues that need immediate attention by assessing the rule baseline quality.
-
Flag a missing or broken rule to help drive corrective action and prevent future problems.
-
Find unknown risks and create a plan to address them before they have a chance to become a larger problem.
-
Create a risk prioritization process to help address issues sooner.
USE CASES
Address Challenges with Security Validation
See and prioritize exposures across your security operations.
Attack
Simulation
Simulate attacks to measure and optimize security controls.
Testing
Stay on top of exposures while alleviating manual testing requirements.
Exposure Validation
Improve decision making with a holistic view of your security posture.
Awarded By The Industry
Customer's Choice
2024 Gartner® Peer Insights™ Voice of the Customer for Breach and Attack Simulation
Cyber Security Excellence Awards
2024 Cybersecurity Excellence Awards – Most Innovative Cybersecurity Company
Customer Reviews
Picus is very good attack simulation tool in overall. It shows all security vulnerabilities and guides..
Sr. Information Security & Risk Officer
The implementation was very fast, the platform is easy to integrate and results quite intuitive to be analyzed.
CIO
It is easy to use and implement the product. It is a really useful tool to find out your security tool vulnerabilities..
Cyber Security Manage
A very successful platform where we can test the accuracy of our security investments and see their scores.
Manager, IT Security and Risk Management
Picus is one of the best BAS solution on the market today. The threat database it is constantly updated..
ICT Security Engineer
Picus completes the task it is required to do near perfect as a BAS solution. Threat database is up to date & updated frequently after a new malware or campaign, also the database is large..
Consultant Security Engineer
There is a very nice team from which I can get quick support. The application provides us with great convenience and confidence in our work.
Information Security Specialist
To test our systems with the real-time attack product is helping us to improve our security maturity. At the same time, the real time attacks are updating with the zero-day vulnerabilities..
Senior Vulnerability Management Engineer
With the help of this product we can perform continuosly endpoint attack via latest tactics and techniques which are used by threat actors..
Manager, IT Security and Risk Management
.. It is possible to customise the campaign or schedule the assessment periodically, to test protection measure implemented on network, endpoint and email.
ICT Security Engineer
Picus is such a great product for organizations that are looking to have constant checks and validation on their security posture in the organization.
Cybersecuirty Pre-sales Engineer.
Picus is a real safety measurement tool. Ever since we took Picus into our inventory, Security has helped significantly to increase our maturity level.
Cyber Defense Senior Specialist
It strengthened our security perspective and allowed us to follow trend attacks. We can test zeroday malicious threats very early because Picus could add them their attack database quickly.
Security Specialist
Validate Effectiveness Across Your Security Program
Validation
Enhance visibility of internal and external cyber assets and the security risks they pose.
Validation
Identify cloud misconfigurations and overly permissive identity and access management policies.
Validation
Measure and optimize the effectiveness of security controls with consistent and accurate attack simulations.
Validation
Eliminate high-risk attack paths that attackers could exploit to compromise users and assets.
Validation
.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.
Frequently Asked Questions
Detection Rule Validation is a standalone application that analyses rules to identify quality and performance issues and provides strong benefits to SOC teams such as process automation, rule development, and correct log resource management.
Detection Rule Validation integrates with Splunk SIEM. More integrations will be added regularly. Please inquire for more information.
Due to a lack of adequate resources and qualified personnel, a SOC team typically only performs only one manual assessment once over a six-month period. SOC teams find it difficult to remain current on a large number of rules, and new rules cannot be adequately tested.
After starting the first of the continuous assessments, the best practice is to examine the results of the assessment and prioritize the improvement insights in the rules according to the insight categories, improve the rules, see the improvements made in the next assessment and repeat the cycle.

