Attack Path Validation
Discover and prioritize high-risk exposures with automated penetration testing and attack path mapping.
.gif?width=1920&height=1080&name=apv-hero-1920x1080px%20(1).gif)
Visualize and Remediate Exploitable High-risk Attack Paths in Your Environment
Attack Path Management is the continuous process of discovering, visualizing, validating, and eliminating the paths attackers could use to reach critical assets. It helps security teams disrupt the stealthiest routes adversaries will take to achieve their objectives, such as domain admin access or ransomware deployment.
Picus Attack Path Validation (APV) supports this effort by identifying security misconfigurations and validating their exploitability under real-world conditions. It reveals how attackers can chain together weaknesses to compromise endpoints, such as servers, workstations, users, and other critical assets in the organization's directory environment, such as Windows Active Directory.
By validating attack paths through automated penetration testing, Picus APV reveals where vulnerabilities intersect across multiple paths, highlighting critical choke points. This enables security teams to execute precise, risk-based remediation that cuts through noise, minimizes downtime, and strengthens defenses where it matters most.
See How an Attacker Can Reach
Domain Admin in 7 Steps
Picus Attack Path Validation mimics real attacker behavior to uncover your most critical paths to crown-jewel assets like Domain Admin accounts. This red team emulation shows how credentials are stolen, cracked, and used to escalate privileges—step by step. In just minutes, security teams gain actionable visibility into where attackers could succeed and where to focus their defenses.
Find Potential Attack Paths with Automated Penetration Testing
Picus APV identifies how attackers chain misconfigurations and weaknesses to move laterally and reach your crown jewels. Through automated penetration testing, it emulates and simulates real attack techniques to validate paths that scanners inherently miss, proving what is truly exploitable in your environment.
.png?width=2000&name=Group%20427319521%20(1).png)
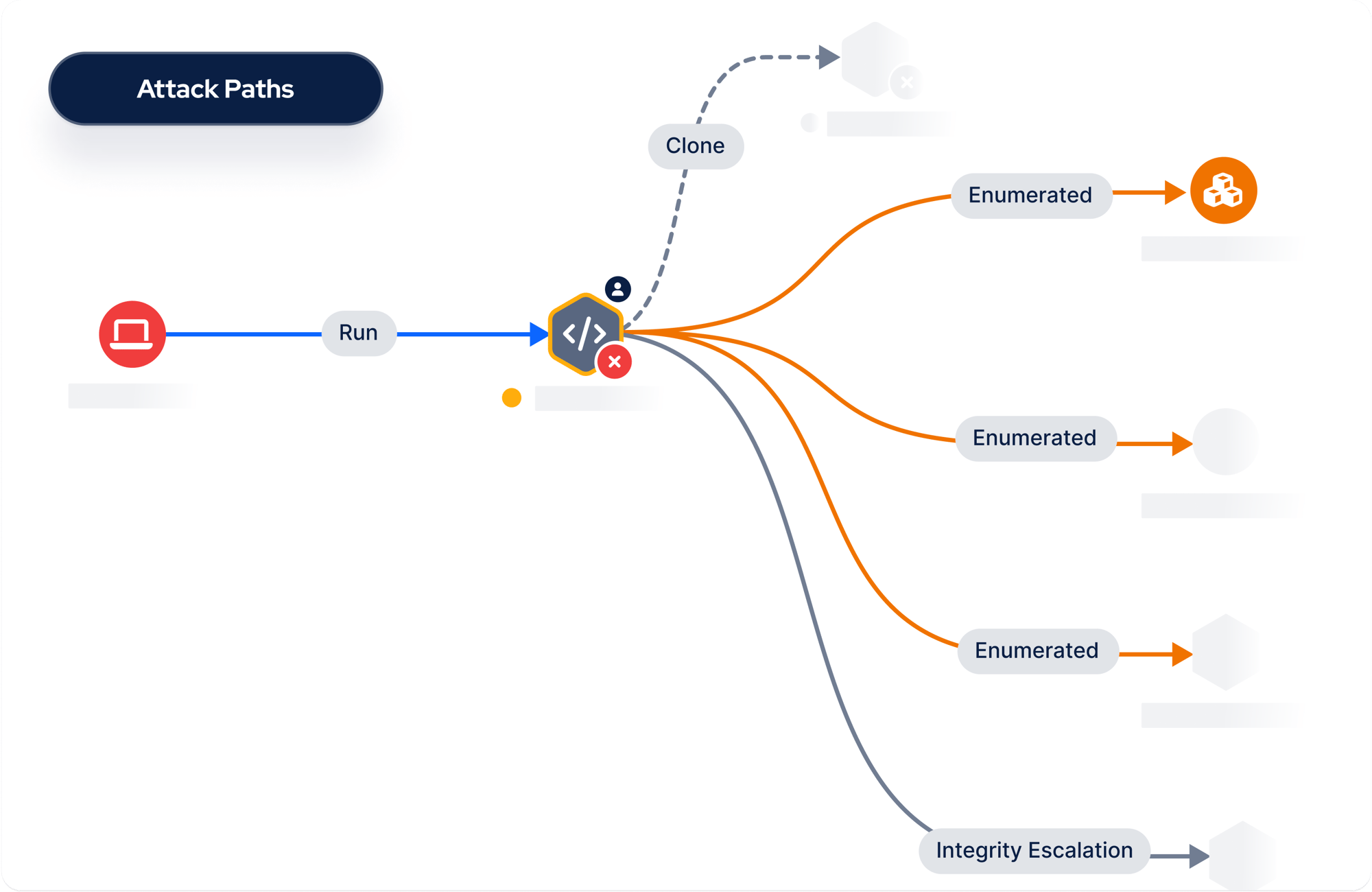
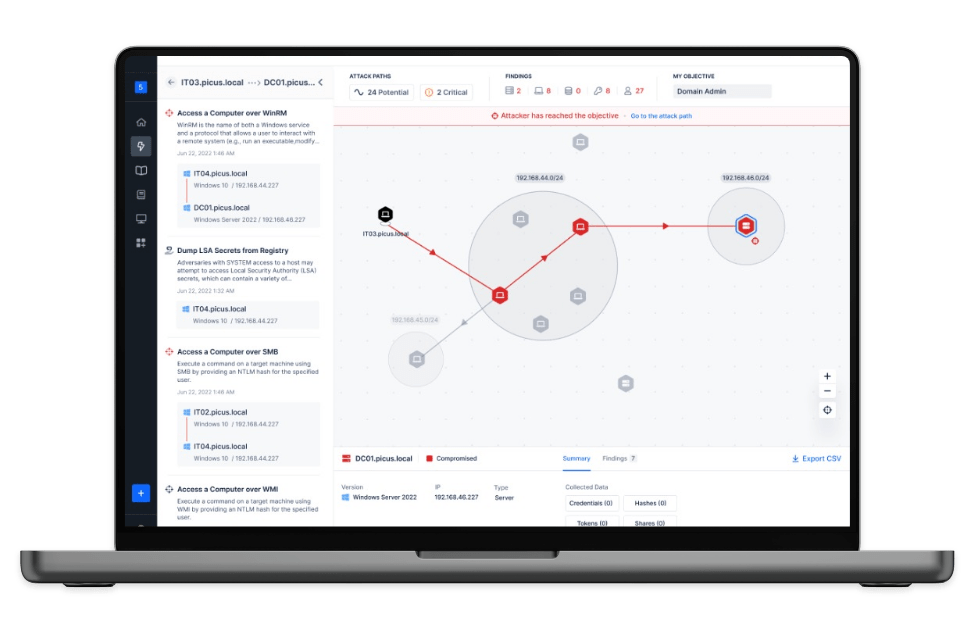
Attack Path Mapping
Discover and visualize high-risk attack paths to understand how attackers could achieve their ultimate objective. Simulate ransomware or identify lateral movement leading to domain admin privileges to stop adversaries.
Why Attack Path Validation?
Reasons to Choose the Picus Platform for
Attack Path Validation
-1.png?width=2000&name=1%20(1)-1.png)
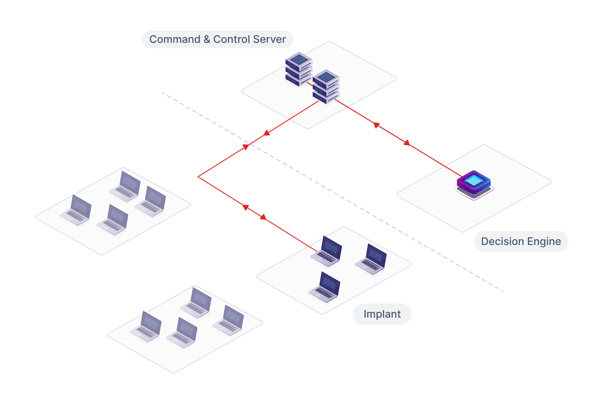
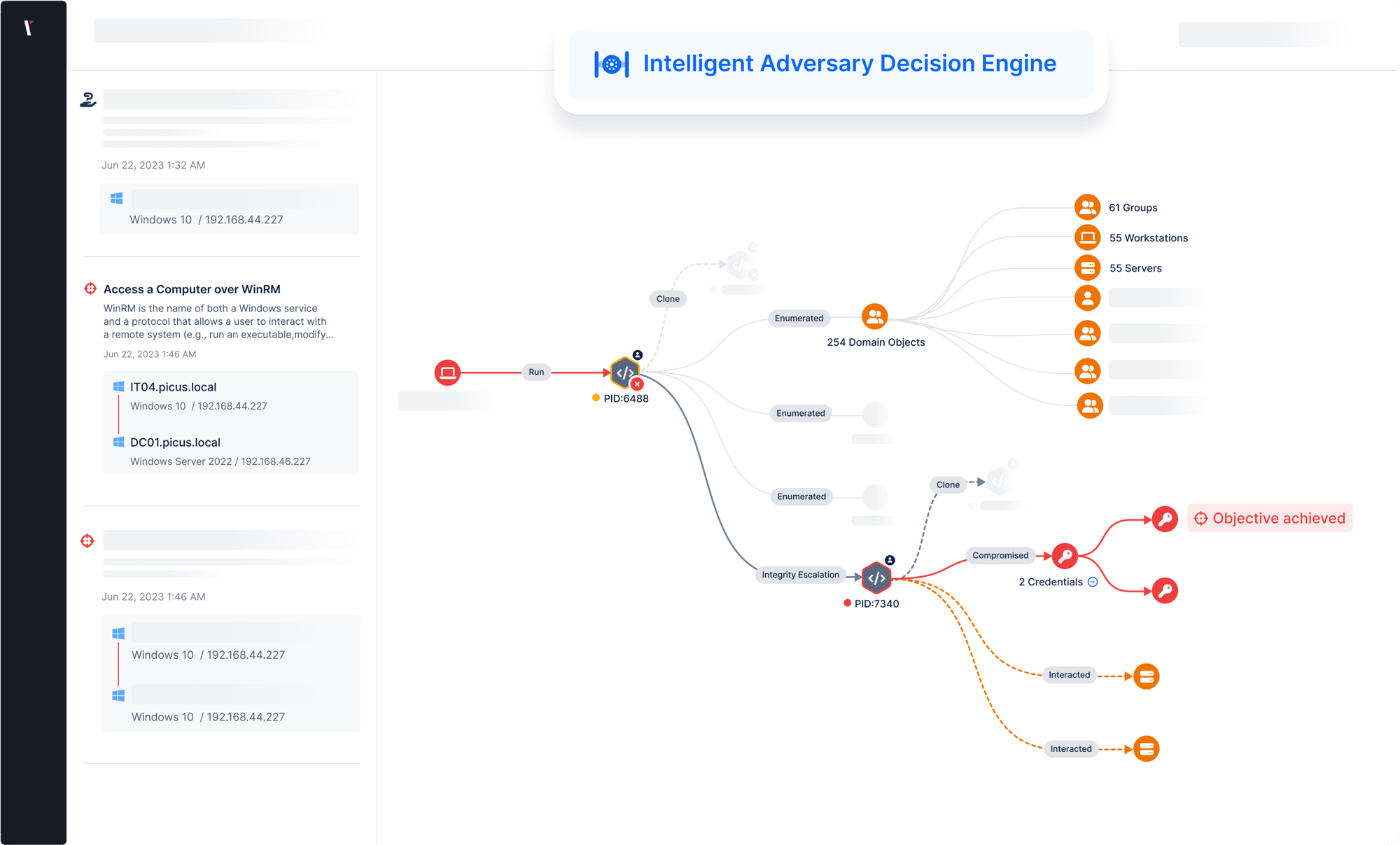


Picus APV goes beyond discovery by validating attack paths through the exploitation of real misconfigurations and weaknesses. It chains attack vectors such as credential harvesting, Kerberoasting, and lateral movement to confirm which paths pose a true risk to your security posture. In doing so, it highlights your most critical exposure points and reveals the potential impact of each validated attack path.
Picus APV is driven by the Intelligent Decision Engine that mirrors the decision-making of a real attacker. It dynamically selects and chains techniques such as reconnaissance, privilege escalation, and credential access to reach defined objectives in the stealthiest and most evasive way possible, with minimal noise.
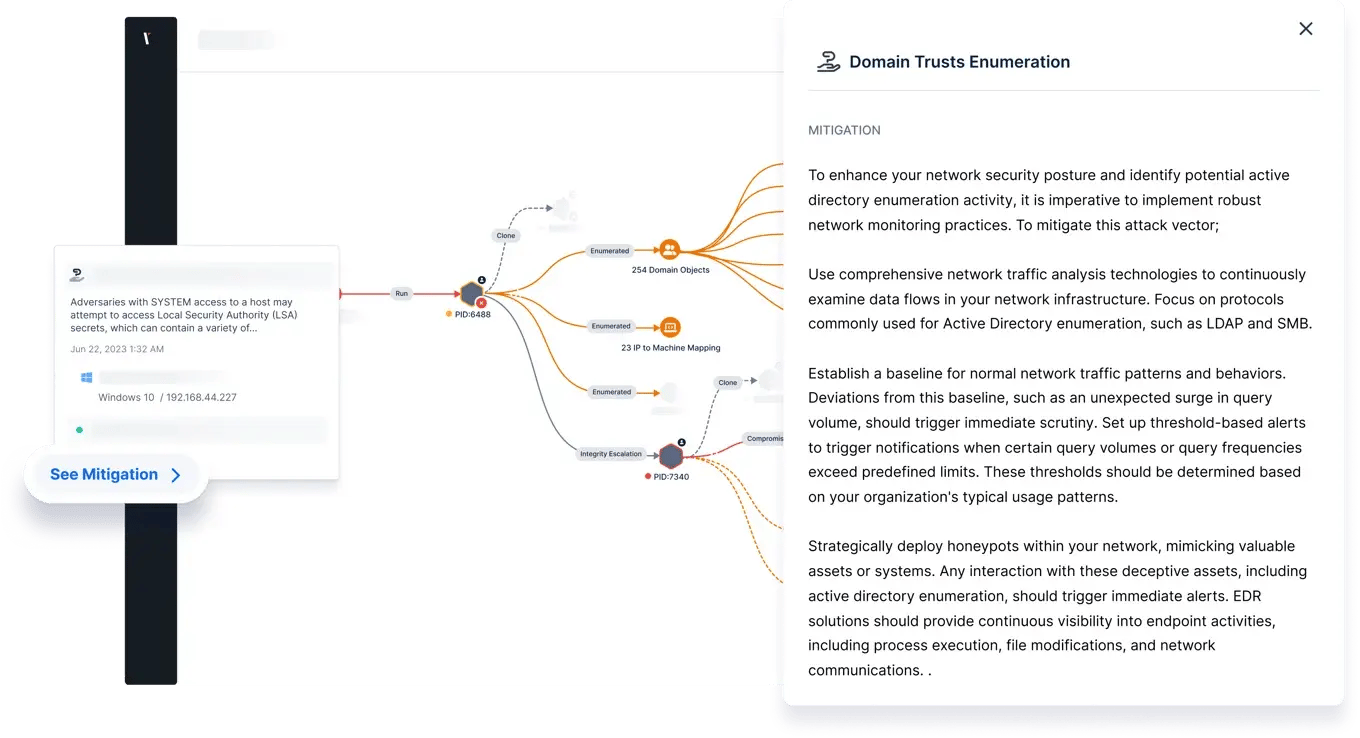
So you can harden your network security and eliminate attack paths, APV supplies helpful insights to mitigate the impact of any actions it is able to perform during an assessment.
Tailor simulations to your requirements by defining a scope and by selecting the type of harvesting and access actions that can be leveraged by the product's decision engine to achieve an objective.
With no agents to install and configure in your environment, it’s easy to get started with Picus Attack Path Validation. After scoping an assessment, all you need to do is execute a binary on an initial access point.
Harden Active Directory
Continuous assessment of Active Directory security is vital since an attacker that has gained domain admin privileges can access all of an organization’s systems, users, and data.
Picus Attack Path Validation enhances internal attack surface validation by identifying and addressing the shortest attack paths within an organization. This ensures that, even after an attacker gains initial access, opportunities for privilege escalation, lateral movement, and exploitation of critical systems are proactively mitigated, reducing the likelihood of a breach causing major business-impacting incidents.
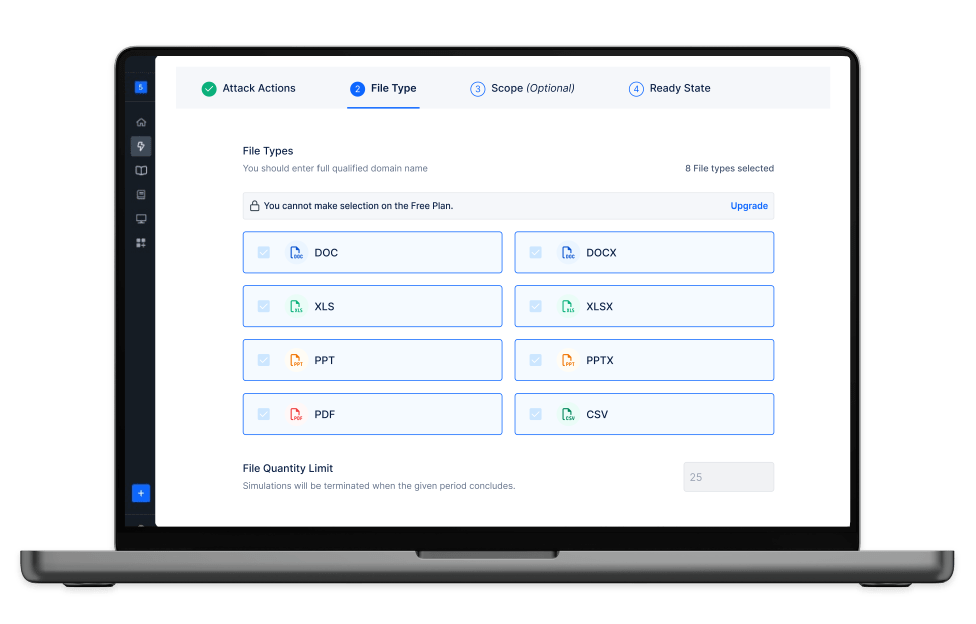
Simulate Ransomware Indicators
Replicate the impact of potential ransomware attacks by simulating the encryption and exfiltration of sensitive files.
Determine common or custom file types to include in your simulation and test the risk post by unauthorized access. Quickly take next steps with key findings, simulation summaries and recommendations.
USE CASES
Address Challenges with Security Validation
See and prioritize exposures across your security operations.
Testing
Stay on top of exposures while alleviating manual testing requirements.
Validation
Improve decision making with a holistic view of your security posture.
Attack
Simulation
Simulate attacks to measure and optimize security controls.
Awarded By The Industry
Customer's Choice
2024 Gartner® Peer Insights™ Voice of the Customer for Breach and Attack Simulation
Cyber Security Excellence Awards
2024 Cybersecurity Excellence Awards – Most Innovative Cybersecurity Company
Customer Reviews
Picus is very good attack simulation tool in overall. It shows all security vulnerabilities and guides..
Sr. Information Security & Risk Officer
The implementation was very fast, the platform is easy to integrate and results quite intuitive to be analyzed.
CIO
It is easy to use and implement the product. It is a really useful tool to find out your security tool vulnerabilities..
Cyber Security Manage
A very successful platform where we can test the accuracy of our security investments and see their scores.
Manager, IT Security and Risk Management
Picus is one of the best BAS solution on the market today. The threat database it is constantly updated..
ICT Security Engineer
Picus completes the task it is required to do near perfect as a BAS solution. Threat database is up to date & updated frequently after a new malware or campaign, also the database is large..
Consultant Security Engineer
There is a very nice team from which I can get quick support. The application provides us with great convenience and confidence in our work.
Information Security Specialist
To test our systems with the real-time attack product is helping us to improve our security maturity. At the same time, the real time attacks are updating with the zero-day vulnerabilities..
Senior Vulnerability Management Engineer
With the help of this product we can perform continuosly endpoint attack via latest tactics and techniques which are used by threat actors..
Manager, IT Security and Risk Management
.. It is possible to customise the campaign or schedule the assessment periodically, to test protection measure implemented on network, endpoint and email.
ICT Security Engineer
Picus is such a great product for organizations that are looking to have constant checks and validation on their security posture in the organization.
Cybersecuirty Pre-sales Engineer.
Picus is a real safety measurement tool. Ever since we took Picus into our inventory, Security has helped significantly to increase our maturity level.
Cyber Defense Senior Specialist
It strengthened our security perspective and allowed us to follow trend attacks. We can test zeroday malicious threats very early because Picus could add them their attack database quickly.
Security Specialist
RESOURCES
Latest Attack Path Validation Resources









.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.
Frequently Asked Questions
An attack path is a route an attacker, that breached a network, could take to achieve an objective. Due to the size of IT environments and the rate at which they grow, most organizations have thousands of potential attack paths. Left undiscovered and unmanaged, high-risk attack paths could enable attackers to compromise critical users and assets quickly and easily.
Attack Path Management is a term used in cyber security to describe the discovery, visualization and elimination of attack paths. By remediating vulnerabilities and addressing misconfigurations inside a network, security teams are able to reduce the number of available paths to critical assets as well as increase the effort required by attackers to reach them.
By automatically discovering and visualizing attack paths inside a network, attack path mapping tools help security teams to understand how attackers could compromise critical users and assets. In doing so, attack path mapping tools reveal vulnerabilities and misconfigurations and provide insights to remediate them.
Examples of common exposures that attackers can exploit once inside a network include excessive user privileges, inadequate network partitioning and unpatched vulnerabilities in systems.
Yes. In order to aid the successful completion of an objective, Picus APV can simulate lateral movement actions. Lateral movement actions that can be simulated include pass-the-hash and pass-the-ticket.
Like red teaming exercises, Picus Attack Path Validation is designed to achieve a certain objective. However, whereas manual red team assessments can take months to perform and deliver results, Picus APV can provide insights in minutes.
By automating attack path mapping, Picus APV enables security teams to run simulations from multiple initial access points quickly and easily. The result is a more holistic view and greater insights to help prioritize the remediation of vulnerabilities and misconfigurations.

