Automated, Smart,
Safe and Continuously Improving
Designed to help organizations assess, test, and optimize their defenses by emulating the tactics, techniques, and procedures of adversaries.
.png)
.png)

10,000+ Threat
in one platform
Malicious Code Attacks,
Web Application Attacks, Vulnerability Exploitation Attacks, Scenario Attacks,Data Exfiltration Attacks.
Campaign
Builder
Build your own custom red team assessments/campaigns from scratch or leveraging the TTP’s available in Picus Threat Library.
Risk-free
Attack Simulation
Continuously measure the effectiveness of your security defenses by using emerging threat samples in production environments.
THREAT LIBRARY
THE MOST COMPREHENSIVE AND UP TO DATE
Over 10K threats including malicious code, web app attacks, vulnerability exploitation.
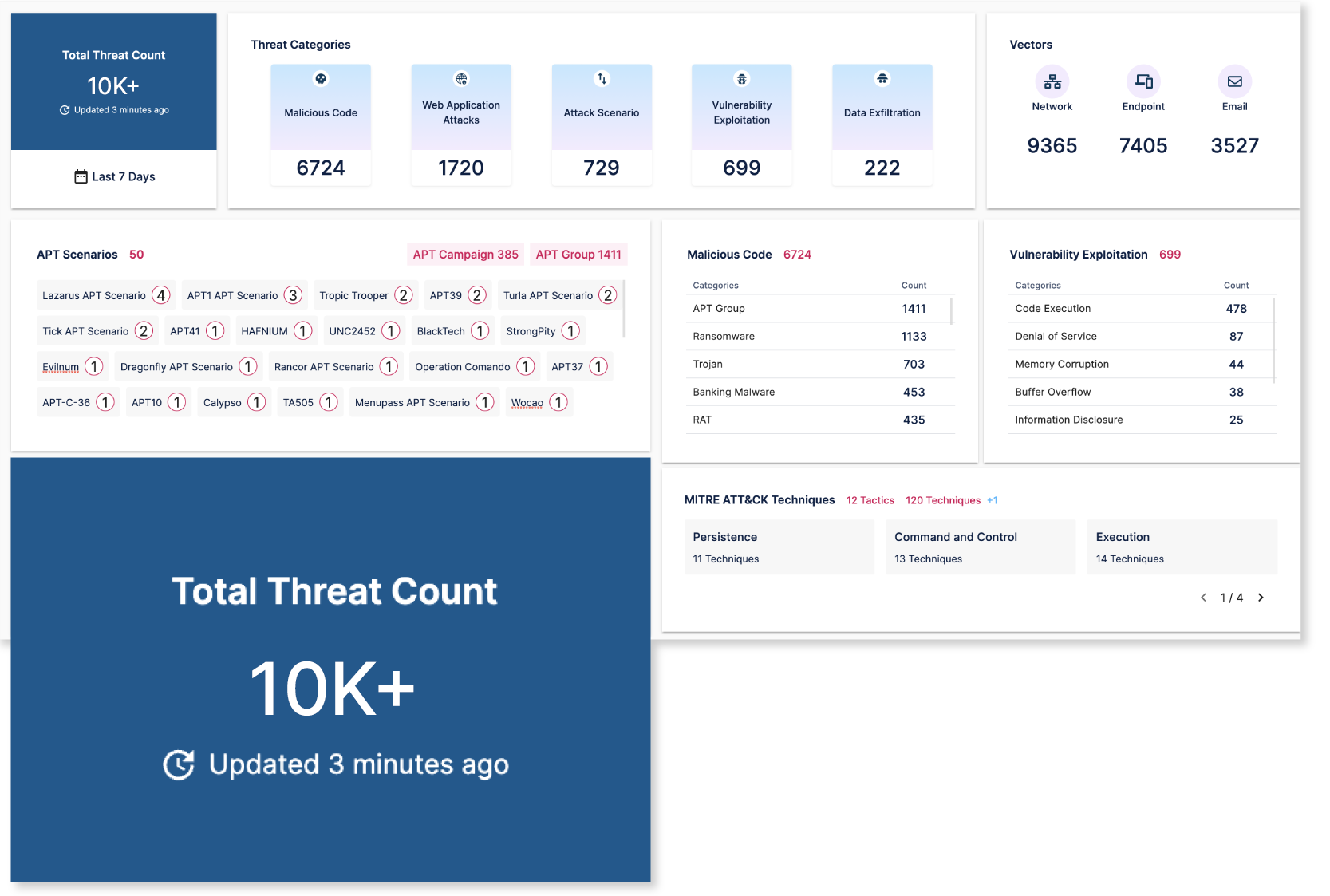
10K+
Threats
150+
APT Group
150+
ATT&CK Techniques
ADVANCED
FILTERING
Ability to search by affected operating system and products, Kill Chain Phases, vertical, geography, release date and more.
.gif)
SUPPORTED BY FRAMEWORKS
Visibility over Cyber Kill-Chain and MITRE ATT&CK frameworks.
150+ APTs
Most comprehensive APT Scenario coverage, over 150+ APTs, can be filtered by geography, industry and campaign

CAMPAIGN BUILDER
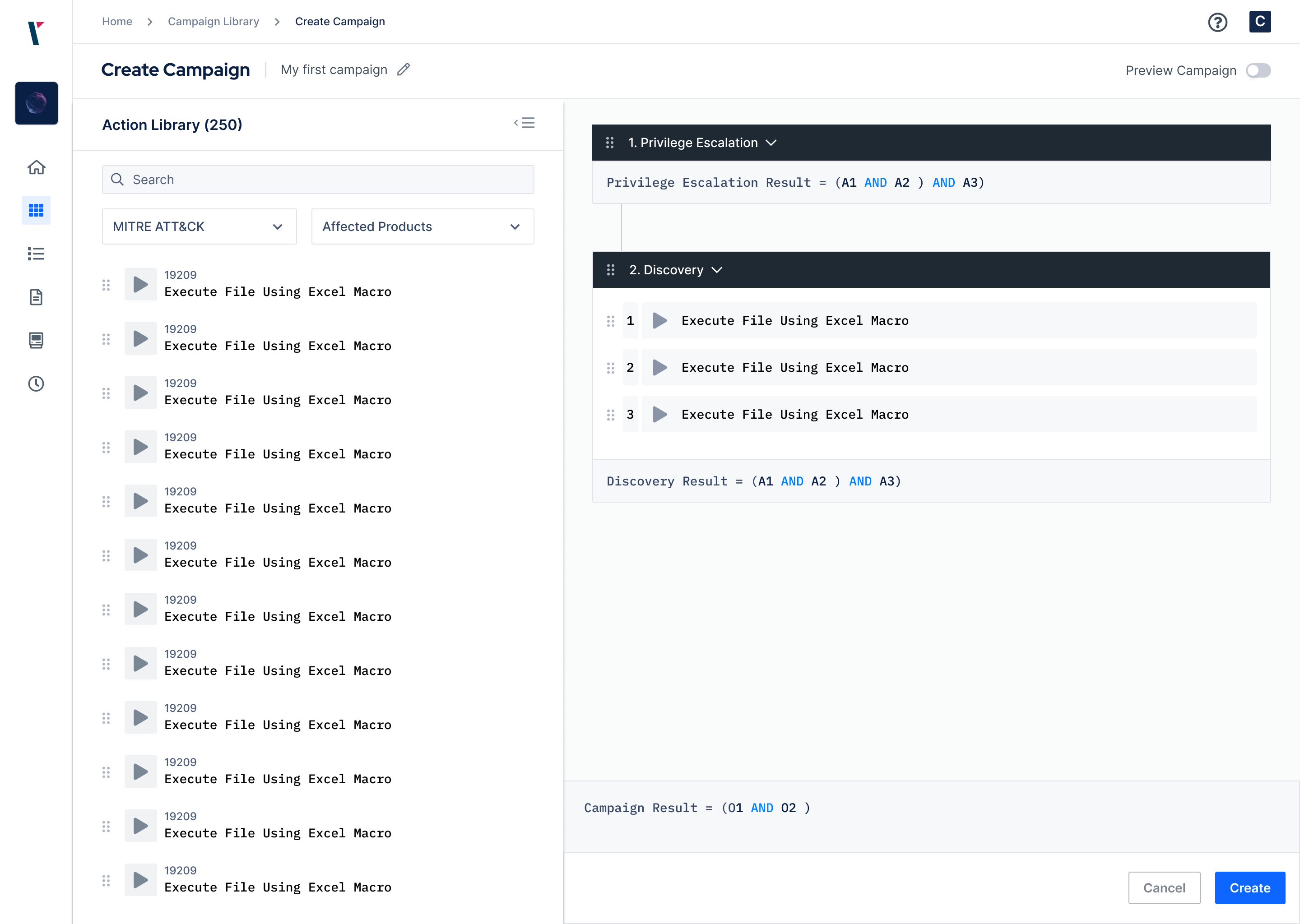
IDEAS TO ACTIONABLE SECURITY INSIGHTS WITHIN MINUTES.
Predefined real-world adversary campaigns, that unlock your ability to mimic attacker mindset to evade security controls.
Build your campaigns from scratch using atomic attacker actions which are mapped to MITRE ATT&CK.
Customize existing campaigns from Threat Library to tailor them for your needs.
ATTACK SIMULATION
DEPLOYED WITHIN AN HOUR
Risk-free technology that does not allow spillovers

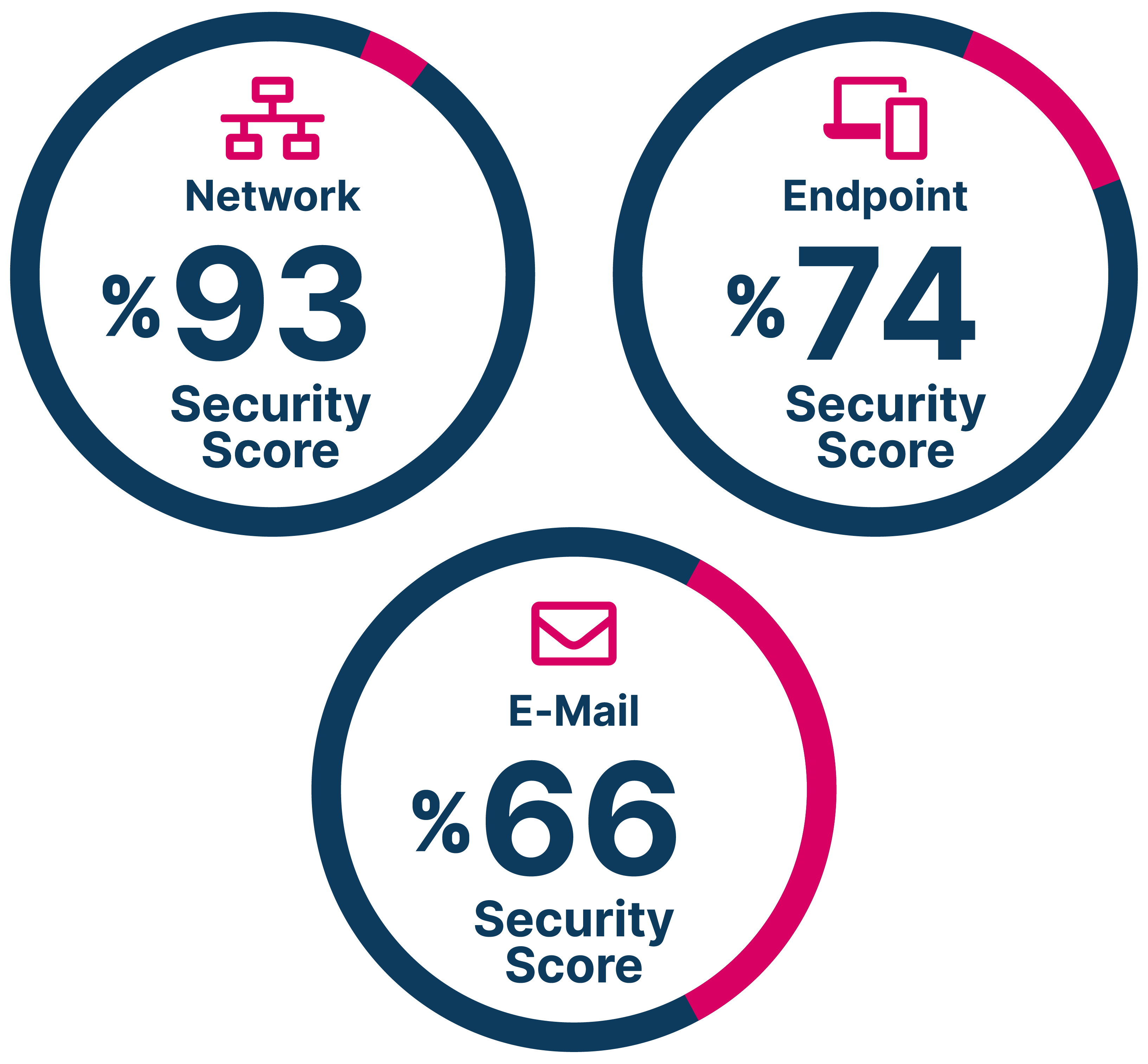
Full coverage over attack vectors from
NETWORK, ENDPOINT, EMAIL SECURITY
ADVANCED ATTACK METHODS
Lateral Movement, Data Exfiltration, Phishing, Malicious Attachment and URL

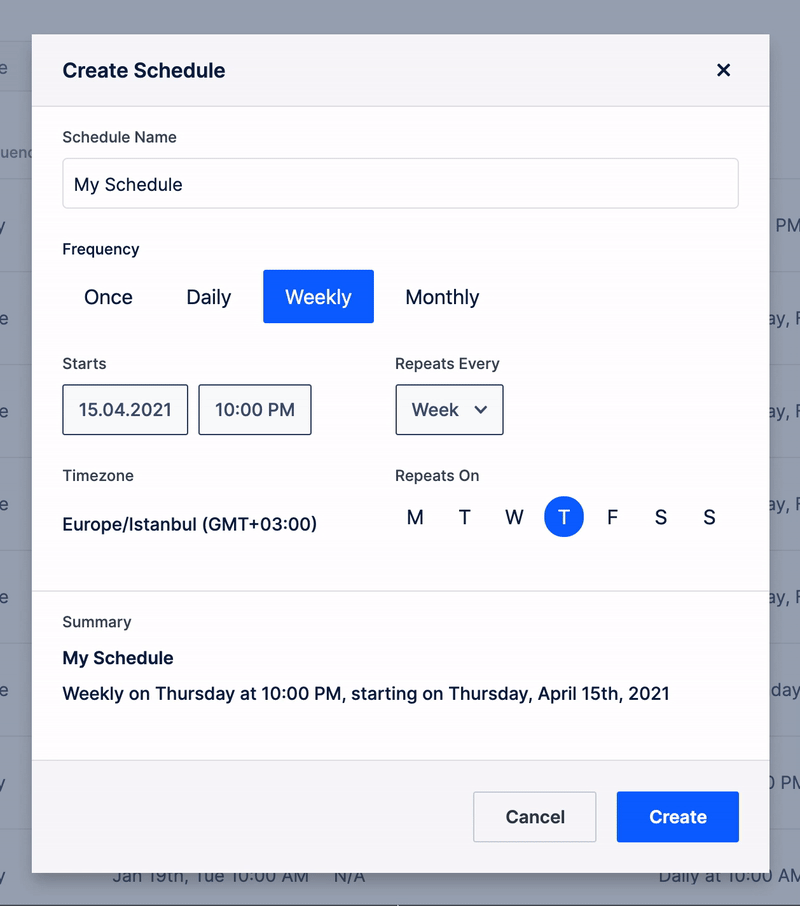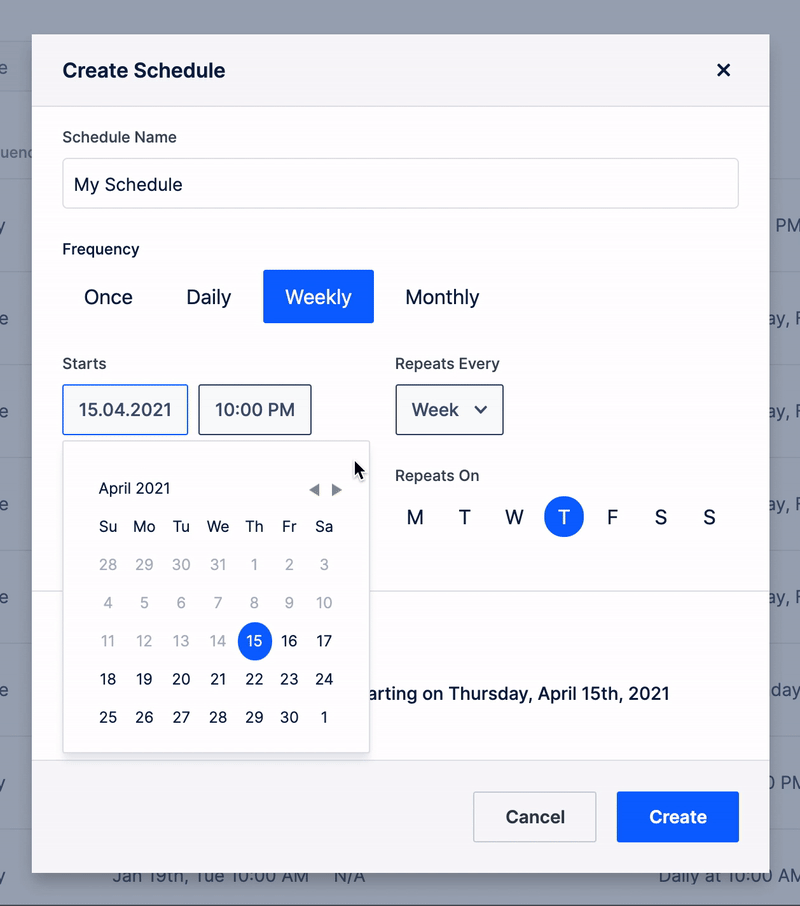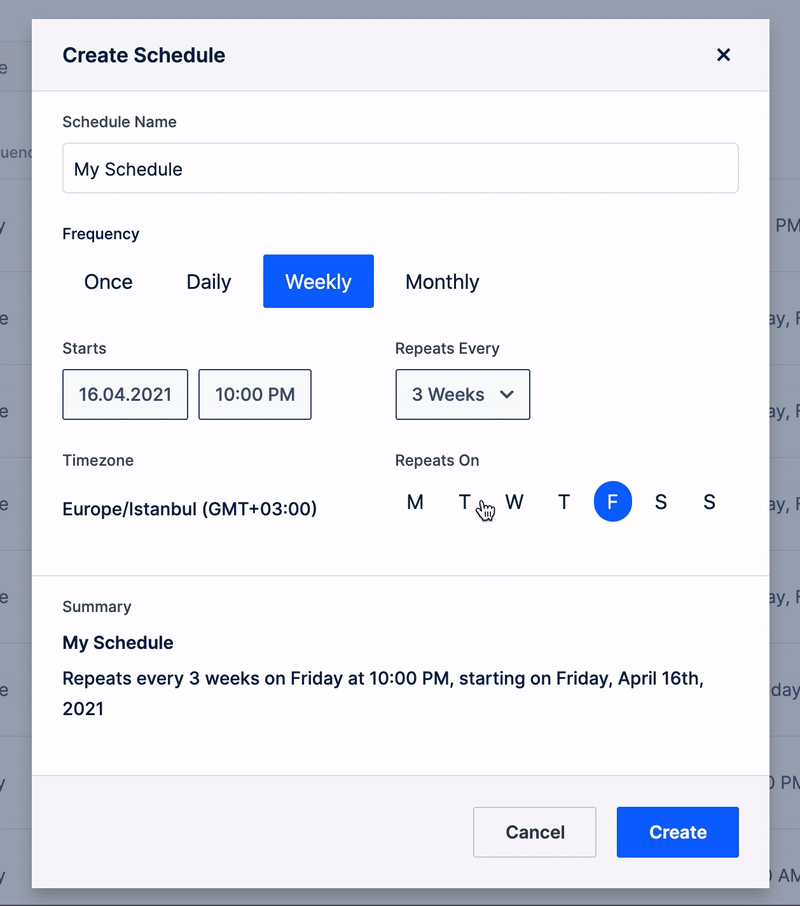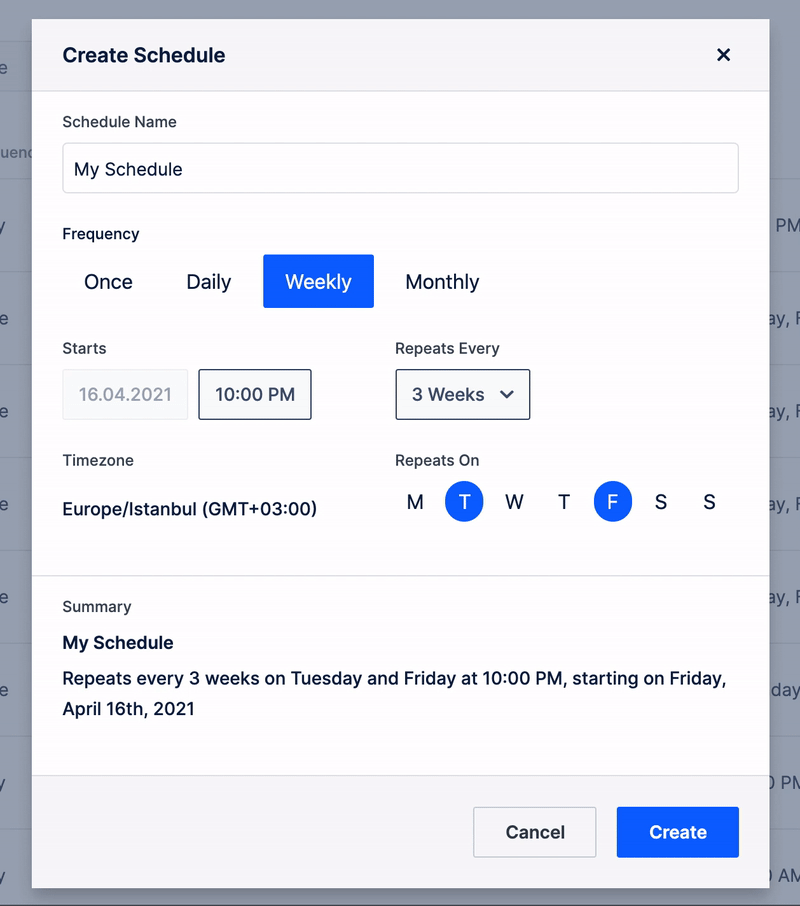
SMART SCHEDULES
Create schedules to run risk-free simulations while securing the organization with 7x24 coverage.
ACTIONABLE
THREAT INTELLIGENCE
Adversary Emulation for #proactive threat readiness
-
No black Magic! All adversary tactics are auditable, provable and served with rich context.
-
Gain real-time visibility across missed or blocked attack actions
-
Assessment results presented in birds-eye view mapped to adversary objectives
-
All objectives are broken down into techniques and sub-techniques mapped to MITRE ATT&CK
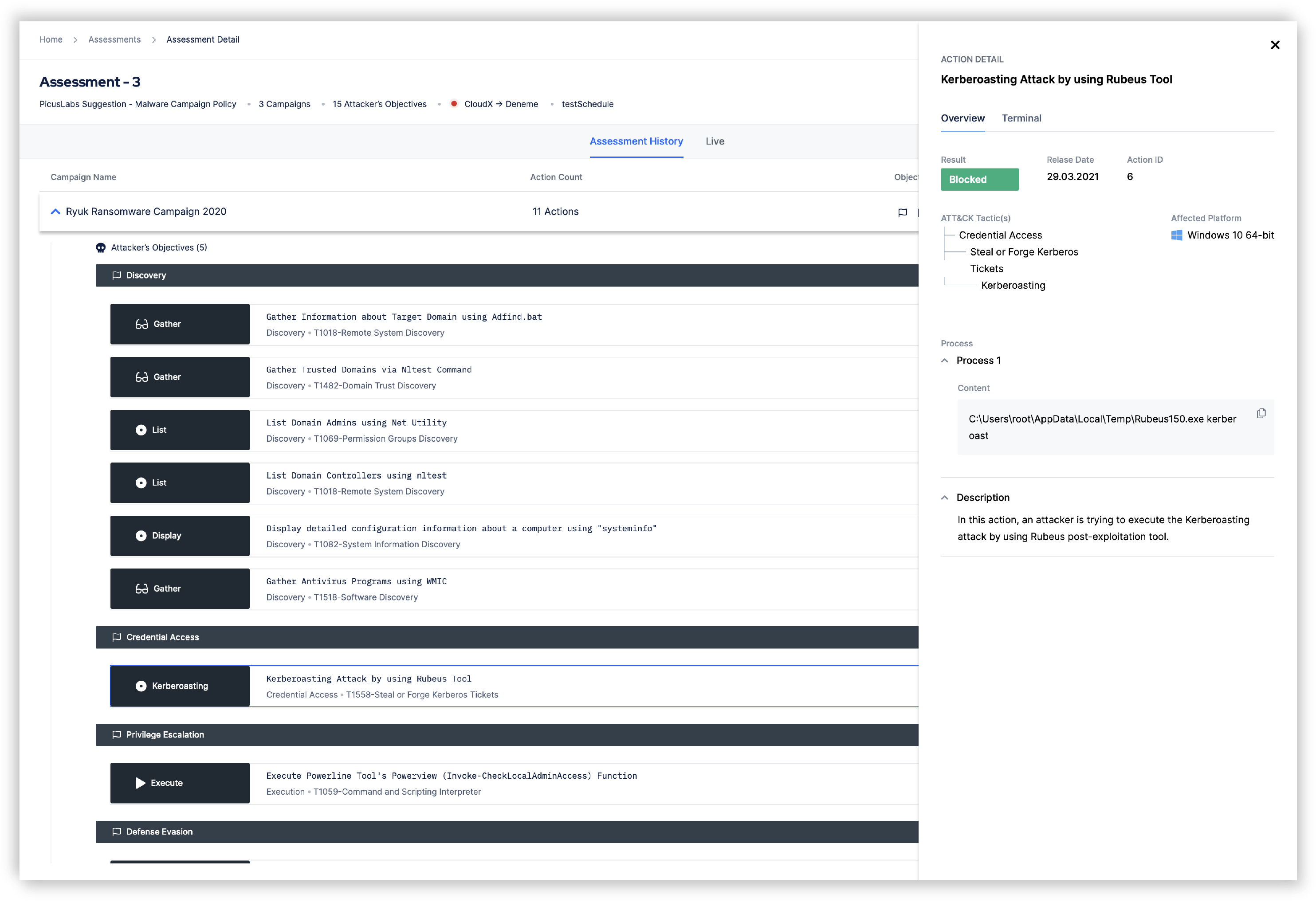
MITRE ATT&CK
Picus trusts industry frameworks and continuously contributes to community efforts. We are a direct contributor and also a supporter of the MITRE ATT&CK framework, which is a free, open, and globally available framework of established adversarial methods, policies,and procedures (TTPs).



